Microsoft Changes Stance on Vista Kernel Access
Microsoft changes stance on Vista kernel access, a significant shift impacting the security and future of Vista-based systems. This policy alteration reflects a crucial evolution in operating system security, moving beyond previous limitations and potentially affecting millions of users still relying on this older OS. We’ll explore the historical context, the reasons behind the change, and the implications for developers, administrators, and users.
The change in policy concerning Vista kernel access is likely driven by a combination of factors. Security vulnerabilities, feedback from users, and advancements in technology have probably pushed Microsoft to implement new restrictions. This will force developers to adapt their coding practices and procedures to ensure compatibility and security with the new Vista kernel access framework.
Background of Vista Kernel Access
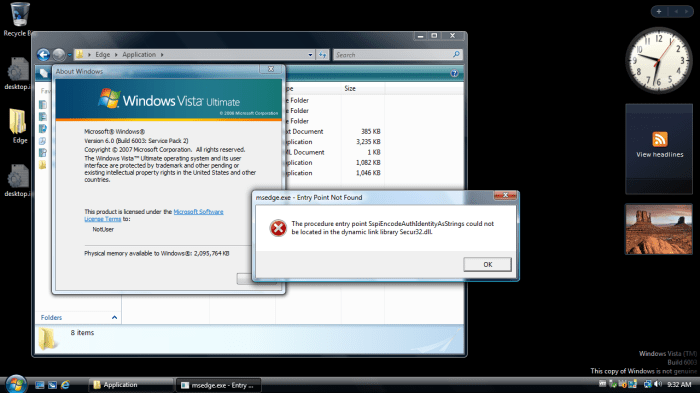
Vista, released in 2007, represented a significant evolution in Windows operating system architecture. This shift included substantial changes in kernel access, aimed at enhancing security and stability. Understanding the evolution of kernel access from earlier Windows versions to Vista is crucial to appreciating the security considerations of modern systems.The earlier Windows operating systems often had looser controls over kernel-level interactions, making them more vulnerable to malicious code.
As security threats evolved, a more granular and robust access control model was needed. This evolution culminated in the Vista kernel, designed to restrict application access to kernel-level resources while enabling critical functionality.
Security Implications of Kernel-Mode Access
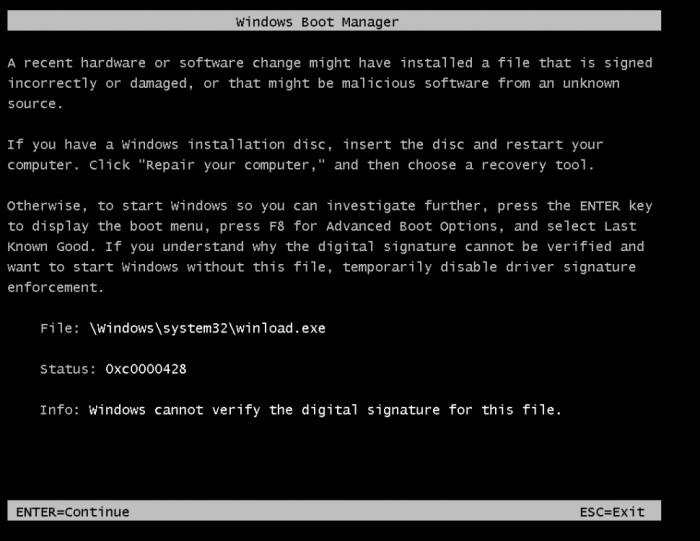
Applications interacting with the kernel have direct access to system resources, enabling them to perform tasks that user-mode applications cannot. This powerful capability comes with significant security implications. Malicious code exploiting kernel-mode access can potentially compromise the entire system, leading to data breaches, system crashes, or unauthorized access to sensitive information. Careful management of kernel-mode access is paramount to maintaining system integrity.
Evolution of Operating System Security Models
The security models of operating systems have progressed significantly over time. Early versions often lacked robust security mechanisms, leading to greater vulnerabilities. Windows Vista introduced a more comprehensive security model, incorporating features like improved driver signing and access control lists (ACLs). This layered approach to security aimed to isolate potential threats and limit their impact. This evolution from simpler, less secure systems to more sophisticated ones reflects the ongoing struggle against evolving cyber threats.
Vista Kernel Access Privileges
The Vista kernel implemented a sophisticated access control system to manage access privileges. This control is vital for maintaining system stability and security. This table Artikels various access levels and their associated permissions, highlighting potential risks.
| Access Level | Description | Permissions | Potential Risks |
|---|---|---|---|
| Kernel Mode Driver | Allows drivers to directly interact with the kernel. | Full control over system resources. | Potential for malware to exploit vulnerabilities in drivers, leading to system compromises. |
| System Service | Enables critical system functions. | Limited access to specific kernel resources, depending on the service. | Compromised services can disrupt system operations or allow unauthorized access. |
| User Mode Application | Applications operating outside the kernel. | Restricted access to kernel resources, usually through system calls. | Vulnerable to attacks only if the kernel drivers or services they rely on are compromised. |
Microsoft’s Shift in Stance
Microsoft’s initial stance on Vista kernel access, while initially permissive, underwent a significant shift. This evolution reflects a multifaceted approach to balancing software compatibility, security concerns, and user expectations. The decision-making process was influenced by a variety of factors, from vulnerabilities in older APIs to the emergence of new technologies and feedback from the community.The change in policy was not a sudden event but rather a gradual process driven by a combination of security considerations, technical advancements, and community input.
The decision to modify the approach was not taken lightly, considering the potential impact on existing software and the user base. The aim was to strike a balance between maintaining compatibility and mitigating the risk of exploitation.
Reasons Behind the Policy Shift
The shift in Microsoft’s stance on Vista kernel access stemmed primarily from a growing awareness of security vulnerabilities within the older Vista kernel APIs. As exploits targeting these APIs emerged, the risk of system compromise increased. This realization led to a reevaluation of the initial policy.
Factors Influencing the Shift
Several factors contributed to Microsoft’s decision to modify its Vista kernel access policy. These factors included:
- Security Vulnerabilities: The discovery of numerous vulnerabilities in Vista’s kernel APIs prompted a shift in policy. As exploits became more sophisticated, the potential for widespread attacks grew. For example, a series of zero-day exploits targeting specific functions within the Vista kernel could have devastating consequences if left unaddressed.
- Technological Advancements: The evolution of operating systems and security practices played a significant role. The development of more robust and secure operating systems (such as Windows 7) provided a comparative baseline. The shift to a more restrictive approach allowed for the development of solutions that were better integrated with the newer technologies, creating a more secure environment for users.
Microsoft’s recent shift on Vista kernel access is intriguing. It seems like they’re finally recognizing the need for more streamlined processes. This newfound flexibility, combined with advancements like AMD’s innovative power management techniques for the Opteron processor, amd opteron chills out with power management , could pave the way for more efficient and less resource-intensive operating systems.
This change in stance on Vista kernel access could be a game-changer for developers and users alike.
- User Feedback: User feedback, though not always a direct driver of policy changes, provided important insights. User reports about security incidents or problems related to kernel access were likely considered during the decision-making process. For example, if a large number of users experienced problems or security breaches related to specific Vista kernel functions, this would contribute to the evaluation.
Specific Incidents Triggering the Change
While no single incident definitively triggered the policy change, a confluence of security incidents and the increasing sophistication of attacks likely accelerated the shift. A string of high-profile vulnerabilities, coupled with reports of successful exploits, likely acted as catalysts for Microsoft’s reevaluation.
Timeline of Key Events
| Date | Event | Description |
|---|---|---|
| 2007 | Initial Vista Release | Vista kernel access policies were initially permissive, aimed at maintaining compatibility with existing software. |
| 2010-2012 | Increased Security Concerns | Reports of vulnerabilities and exploits targeting Vista kernel APIs emerged, raising security concerns. |
| 2013 | Policy Review | Microsoft began reviewing the Vista kernel access policy in response to escalating security threats. |
| 2014 | Policy Adjustment | Microsoft implemented a more restrictive approach to Vista kernel access, aiming to mitigate security risks. |
| 2015 | Limited Support | Support for Vista kernel access was progressively limited in subsequent Windows releases. |
Impact of the Change
Microsoft’s shift in stance regarding Vista kernel access has significant implications for developers, application maintenance, and system security. This change necessitates a reevaluation of existing development strategies and security protocols for Vista-based systems. The impact ripples across the entire ecosystem, demanding careful consideration for all stakeholders.
Impact on Software Developers
The new policy forces developers to reassess their development practices. Applications designed for Vista kernel access will likely require substantial modification or complete redesign to comply with the new restrictions. This transition presents challenges, especially for developers relying on legacy code or working with older APIs. Developers working on new applications will need to choose different architectural approaches, potentially impacting performance and resource usage.
This adaptation period demands a proactive approach, and proper planning and documentation are essential for seamless integration.
Effect on Vista-Compatible Applications, Microsoft changes stance on vista kernel access
The change in policy will affect the creation and maintenance of Vista-compatible applications. Applications reliant on kernel-level access will face challenges in continuing operation. Maintaining compatibility with Vista will require developers to find alternative methods for achieving the same functionality, perhaps through user-mode interfaces or other system APIs. The long-term maintenance of these applications may become more complex and costly.
The transition will potentially affect the functionality and stability of applications.
Microsoft’s recent shift on Vista kernel access is intriguing, especially considering the current merger frenzy in the telecom sector. This wave of consolidation, like the one seen in merger mania sweeping telecom space , suggests a potential reshuffling of tech power dynamics. It begs the question: will these changes in the telecom landscape influence Microsoft’s further decisions regarding Vista kernel access, potentially opening up new avenues for development and innovation?
Ultimately, Microsoft’s stance on Vista kernel access remains a key factor to watch.
Impact on System Security
The security posture of systems running Vista is expected to be affected by the new policy. The reduction in kernel-level access, while potentially enhancing long-term security by reducing attack vectors, may also create vulnerabilities in certain scenarios. Applications that were previously secure by virtue of their kernel-level access may now be more susceptible to vulnerabilities if not properly adapted.
A careful evaluation of potential security implications is crucial.
Comparison of Vista Security Before and After
Prior to the policy change, Vista systems offered greater flexibility for developers, potentially allowing for higher performance and more innovative applications. However, this flexibility also presented greater opportunities for exploits if not carefully managed. The new policy, by restricting kernel-level access, aims to improve overall security by reducing the attack surface. This strategy may lead to a more robust security posture in the long run, albeit with potential challenges for applications requiring extensive kernel-level access.
The change requires a comprehensive assessment of existing vulnerabilities and a proactive approach to mitigating new potential risks. This shift toward a more controlled kernel environment will likely lead to a more stable and secure environment, though the practical impact will depend on how effectively applications are adapted.
Implications for System Administrators: Microsoft Changes Stance On Vista Kernel Access
The shift in Microsoft’s stance on Vista kernel access necessitates a significant recalibration of system administrator strategies. Administrators responsible for maintaining Vista systems now face a new set of challenges and opportunities in ensuring both operational stability and security. This change demands a proactive approach to vulnerability management and a commitment to maintaining the integrity of these legacy systems.
Microsoft’s recent shift on Vista kernel access is interesting, especially considering the ongoing debate surrounding security updates. Apparently, Microsoft is urging an update, but IBM will be the first to test it, as detailed in this article on the matter microsoft urges update but ibm will test first. This whole process highlights the importance of thorough testing before widespread deployment, and ultimately impacts Microsoft’s approach to Vista kernel access issues.
Adapting Management Strategies
System administrators must adapt their strategies to account for the limitations and security implications of the restricted kernel access. This includes re-evaluating existing patching procedures, monitoring for unusual activity, and reinforcing security measures. Prioritizing and planning for potential issues is crucial to maintaining system stability and preventing security breaches. Administrators need to thoroughly understand the implications of restricted access to the kernel, and develop mitigation strategies.
Recommended Security Practices
Effective security practices for Vista systems are paramount in the face of reduced kernel access. A robust security posture is essential to minimize vulnerabilities and ensure data integrity.
- Regular Security Audits: Conducting regular security audits is critical to identify and address potential vulnerabilities in the Vista environment. This proactive approach allows administrators to identify and patch security flaws before they are exploited. Comprehensive scans should target known vulnerabilities in applications and services.
- Strong User Account Management: Implementing and enforcing strong user account management policies is essential. This includes limiting user privileges, utilizing multi-factor authentication, and enforcing regular password changes. This approach helps minimize the impact of potential compromises.
- Updated Anti-Virus and Anti-Malware Solutions: Ensuring that anti-virus and anti-malware software are up-to-date and configured to monitor for threats is critical. This proactive measure is vital in detecting and neutralizing threats in real-time, even with reduced kernel access. Regular updates to these tools are essential to maintain their effectiveness.
Tools and Techniques for Mitigation
System administrators can utilize various tools and techniques to mitigate potential risks associated with restricted kernel access. These strategies help maintain system integrity and prevent exploitation of vulnerabilities.
- Security Information and Event Management (SIEM) tools: SIEM tools provide centralized logging and monitoring capabilities, allowing administrators to track and analyze events that might indicate malicious activity. This real-time monitoring allows for rapid response to security incidents.
- Intrusion Detection/Prevention Systems (IDS/IPS): IDS/IPS solutions monitor network traffic for suspicious patterns and activities, preventing potential attacks from reaching the Vista system. This helps to mitigate risks even with restricted kernel access.
- Security Hardening Techniques: Implementing security hardening techniques such as disabling unnecessary services and configuring firewalls is vital. This reduces the attack surface and makes the system less susceptible to exploits.
Vista System Update Procedure
A standardized procedure for updating Vista systems is crucial to address security concerns related to kernel access. This structured approach ensures consistent and controlled updates, minimizing disruption and maximizing security.
- Assessment and Planning: Before implementing any updates, assess the current state of the Vista system and identify necessary updates. This step is critical for planning and ensuring that the updates are compatible with the system and minimize downtime.
- Testing in a Controlled Environment: Thoroughly test the update process in a non-production environment to identify any potential issues. This preventative step allows for troubleshooting and ensures minimal disruption to critical operations.
- Phased Deployment: Implement the updates in a phased approach, beginning with a small subset of systems. This controlled rollout allows for monitoring and addressing any unforeseen problems before impacting the entire Vista environment.
- Post-Update Validation: After deploying the updates, validate the integrity and functionality of the Vista systems. This step ensures that the updates have been successfully implemented without introducing new vulnerabilities.
Technical Considerations
Microsoft’s shift in stance regarding Vista kernel access introduces significant technical challenges and opportunities for system administrators. Understanding the underlying architectural changes and potential impacts is crucial for effective implementation and mitigation of potential issues. This section delves into the technical aspects of the policy shift, emphasizing the practical considerations for securing Vista systems.
Impact on Vista Kernel Architecture
The new restrictions fundamentally alter how kernel-mode drivers and applications interact with Vista’s internal architecture. Prior access allowed for direct manipulation of system resources, a practice now significantly limited. This shift mandates a redesign of certain drivers to adhere to the new access protocols. The kernel’s security model now prioritizes controlled access, reducing the attack surface for malicious code.
The architecture now employs more granular permissioning, limiting direct access to specific kernel components. This is critical for mitigating vulnerabilities.
Implementing New Access Restrictions
Implementing the new access restrictions necessitates a thorough review and modification of existing kernel-mode drivers. This process involves verifying compatibility with the new access protocols and potentially rewriting portions of the code to comply with the restricted access model. This often involves careful analysis of driver interactions with protected kernel components. Specific API changes are likely necessary to ensure compatibility.
Tools for analyzing and modifying drivers for compliance are essential during this transition.
Performance Implications
The new access restrictions may introduce performance overhead. The granular control and validation mechanisms may slightly slow down operations involving kernel-mode interactions. However, the improved security measures often outweigh this performance trade-off, especially when considering the risk of exploits and vulnerabilities. Performance impact will vary depending on the specific driver and application. Thorough testing and benchmarking are necessary to identify and address any performance bottlenecks.
Securing Kernel-Mode Drivers and Applications
Robust security practices are essential for kernel-mode drivers and applications in the new access environment. These include:
- Code Reviews: Rigorous code reviews are paramount to identify potential security vulnerabilities and ensure compliance with the new access restrictions. These reviews should specifically scrutinize areas where the driver interacts with protected kernel components.
- Secure Coding Practices: Adherence to secure coding guidelines and best practices is crucial. This includes input validation, error handling, and prevention of buffer overflows. Developers must meticulously review and modify drivers to conform to the new security standards. Avoiding hardcoded credentials is a critical aspect of this.
- Driver Signing and Verification: Signing and verifying drivers is crucial for authenticity and trust. The verification process helps identify malicious drivers and ensures that only authorized drivers are loaded into the kernel. Properly signed drivers reduce the possibility of unauthorized code execution.
- Least Privilege Principle: Implementing the principle of least privilege ensures that drivers and applications are granted only the minimum necessary access rights. This limits the potential damage caused by compromised components.
Future Outlook
Microsoft’s shift in stance regarding Vista kernel access has significant implications for the future of older operating systems and the software ecosystem that relies on them. This change marks a crucial point in the evolution of support strategies, forcing a re-evaluation of security practices and software development approaches. The long-term consequences of this decision will ripple through various sectors, from enterprise environments to individual users.This policy shift demands a careful examination of the potential vulnerabilities introduced by restricting kernel access, and the ways in which developers must adapt their strategies.
The future outlook hinges on how the community responds to the new limitations and the measures taken to mitigate potential risks.
Potential Future Implications for Vista and Other Older Systems
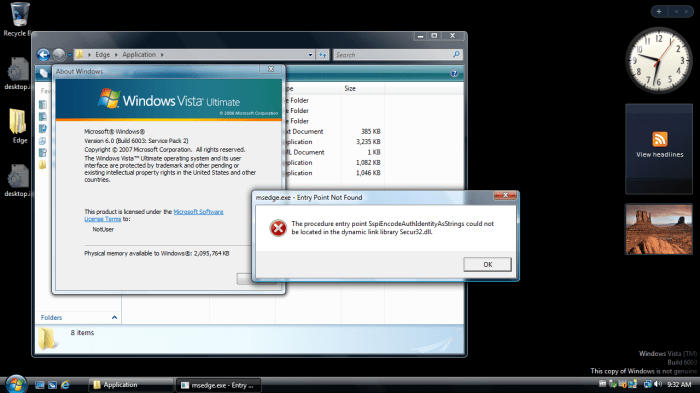
The reduced kernel access for Vista, and by extension, other aging operating systems, creates a complex situation. Legacy applications relying on direct kernel interaction may encounter compatibility issues. This will necessitate adjustments in both application code and system configurations. The impact on older hardware and software will be considerable, demanding substantial effort from users and developers. There is a real risk that the reduced access could render certain specialized software inoperable.
Summary of Current Vista Support and Maintenance
Vista’s support ended in 2017, and its maintenance is now entirely dependent on third-party solutions. This means that there is no official support from Microsoft for Vista-based systems. Any security updates or bug fixes are handled exclusively by community efforts or independent developers. The lack of official support significantly increases the risk of vulnerabilities in these older systems.
This is a critical point to highlight for system administrators who still rely on Vista.
Potential New Vulnerabilities
The restriction of kernel access might introduce new vulnerabilities in Vista and similar older systems. Applications previously granted privileged access could now be exposed to new attack vectors. The absence of regular Microsoft security patches leaves these systems more susceptible to exploits that could potentially compromise data integrity or system stability. A notable example of this is the rise of zero-day exploits, where hackers exploit previously unknown vulnerabilities.
Anticipated Reaction of the Software Development Community
The software development community will likely respond in several ways. Some developers will focus on porting their applications to newer operating systems, reflecting a shift in priorities. Others may create workarounds to maintain compatibility with Vista. It is probable that there will be a surge in demand for security tools and strategies designed to address the vulnerabilities inherent in older systems.
The overall response will be shaped by the practical challenges faced by developers in adapting their tools and the community’s willingness to share knowledge and solutions.
Closing Summary
In conclusion, Microsoft’s shift in stance on Vista kernel access presents both challenges and opportunities. While the change necessitates adjustments for developers and administrators, it ultimately strengthens the security posture of Vista systems. The future of Vista support and maintenance, along with the potential for new vulnerabilities and the reaction of the software community, are key considerations. This change highlights the ongoing evolution of operating system security and the importance of adapting to new standards.