Published Code Exposes Windows Flaw A Deep Dive
Published code exposes Windows flaw, revealing a potential security vulnerability in widely used systems. This issue could have significant implications for users and system administrators, potentially impacting data security and system stability. We’ll explore the details of this flaw, analyzing its potential impact, technical aspects, mitigation strategies, and real-world examples. Prepare to delve into the intricacies of secure coding practices and the ever-evolving landscape of cybersecurity.
The published code, likely part of a widely distributed software package, contains a critical flaw that could be exploited by malicious actors. Understanding how this vulnerability works is key to mitigating its risks. This detailed analysis will cover the technical specifics of the flaw, including the programming logic that led to the issue and potential attack vectors. We will explore how this vulnerability can affect various system configurations and user privacy.
Overview of the Vulnerability
A recently disclosed Windows flaw, now patched, exposed a vulnerability in the system’s handling of specific memory operations. This weakness allowed attackers to potentially execute arbitrary code, potentially granting unauthorized access or control over the affected system. Understanding the specifics of this vulnerability is crucial for securing systems and mitigating potential attacks.
Description of the Flaw
The vulnerability centered on a flaw in how the Windows operating system managed memory allocation and access. Specifically, the issue resided within the kernel’s handling of certain memory operations during specific program execution paths. This could lead to a situation where attackers could exploit this to execute code they control, rather than the intended code. The exploitation often involves carefully crafted inputs that trigger the vulnerability.
Affected Components and Functionalities
The vulnerability impacted several components within the Windows kernel. These components included memory management modules, drivers, and processes involved in specific file system operations. Any process relying on the compromised memory management modules or file system functions was susceptible to this exploit.
Potential Impact on System Configurations
The impact of the vulnerability varied depending on the system configuration and the specific software involved. Systems with vulnerable software components and user accounts with elevated privileges were most susceptible to exploitation. For example, servers hosting critical applications were more at risk than personal computers. The potential consequences ranged from data breaches to system takeover, depending on the attacker’s goals.
Severity Levels, Published code exposes windows flaw
The severity of the vulnerability was assessed as critical, posing a significant risk to affected systems. The ability to execute arbitrary code provided attackers with substantial control over the compromised machine. A critical severity indicates a high likelihood of severe consequences, including the potential for complete system compromise.
Types of Vulnerabilities in Published Code
Software vulnerabilities can manifest in various forms. Common types include:
- Buffer Overflows: These vulnerabilities occur when a program attempts to write data beyond the allocated buffer space. This can allow attackers to overwrite adjacent memory locations, potentially leading to code execution.
- Integer Overflows and Underflows: These vulnerabilities involve arithmetic operations that exceed the integer’s capacity. This can result in unexpected behavior or program crashes, creating an opportunity for exploitation.
- Use-After-Free Errors: These errors occur when a program attempts to use memory that has already been freed. This can lead to unpredictable behavior, including crashes or the execution of malicious code.
- Race Conditions: These vulnerabilities arise when multiple threads access and modify shared resources concurrently. The outcome depends on the timing of the thread executions, which can lead to unintended behavior or allow an attacker to exploit the situation.
Understanding the various types of vulnerabilities is crucial for proactively identifying and addressing potential weaknesses in software.
Impact Assessment
This vulnerability, if exploited, presents a significant threat to the security and integrity of affected systems. The potential consequences range from minor inconveniences to catastrophic data breaches and system takedowns. Understanding the potential impact is crucial for prioritizing mitigation strategies and implementing robust security measures.
Potential Consequences of Exploitation
The exploitation of this flaw could result in a wide range of negative consequences. The severity depends on several factors, including the attacker’s skill, the target system’s configuration, and the specific exploit method employed. From minor disruptions to significant system compromises, the potential damage is substantial.
Data Breaches and System Compromise
Attackers could potentially gain unauthorized access to sensitive data, leading to data breaches. This could expose confidential information, such as user credentials, financial records, or intellectual property. Compromised systems could be used as launchpads for further attacks, potentially affecting other systems or networks. Examples include the recent ransomware attacks on critical infrastructure, where attackers exploited vulnerabilities to encrypt sensitive data and demand ransom for its release.
Attacker Tactics and Techniques
Attackers might employ various methods to exploit this vulnerability. These methods could range from simple automated scripts to sophisticated, targeted attacks. Social engineering tactics could be used to trick users into providing credentials or clicking malicious links. Furthermore, attackers could leverage publicly available exploits or develop custom exploits specifically targeting this vulnerability. The specific techniques used will depend on the attacker’s goals and resources.
Impact on User Privacy and Security
The vulnerability could have significant implications for user privacy and security. Compromised systems could expose user personal information, potentially leading to identity theft or financial fraud. Furthermore, attackers could gain access to sensitive data, such as medical records or financial transactions, violating user trust and potentially leading to severe financial and reputational damage. Examples of this include the numerous cases of data breaches affecting millions of users, highlighting the real-world consequences of such vulnerabilities.
Disruption of System Operations
Exploiting this vulnerability could disrupt normal system operations in various ways. Attackers could introduce malicious code that interferes with system functionality, leading to denial-of-service attacks. This could impact critical services, such as online banking, healthcare systems, or emergency services, potentially causing significant disruptions and economic losses. Consider the recent instances of distributed denial-of-service attacks targeting major websites, demonstrating the potential for widespread disruption.
Furthermore, attackers could gain control over system resources, leading to unauthorized modifications or deletions of data.
Technical Analysis: Published Code Exposes Windows Flaw
This section delves into the core of the vulnerability, examining the underlying cause, the programming logic that led to the flaw, and the specific code responsible. We’ll also explore the various attack vectors and evaluate different patching strategies. Understanding these details is crucial for developers to implement effective countermeasures and prevent similar issues in the future.The vulnerability arises from a subtle yet critical oversight in the handling of user-supplied input.
So, this newly published code highlighting a Windows flaw is definitely concerning. While Intel is reportedly shifting its focus to developing innovative broadband wireless chips, like those found in intel to focus on broadband wireless chips , it’s crucial to remember that robust security measures are still paramount in the face of such vulnerabilities. This exposed Windows weakness needs urgent attention, regardless of other technological advancements.
Improper validation of input data allows attackers to manipulate program execution, leading to potentially disastrous consequences. The root cause lies in a failure to anticipate and prevent malicious inputs, which results in unexpected behavior and exploitation.
Underlying Cause of the Vulnerability
The core issue stems from a lack of input sanitization. The application fails to adequately filter user-supplied data before using it in critical computations. This allows attackers to craft malicious input that bypasses intended security checks and alters the program’s behavior. Specifically, the application is vulnerable to command injection attacks.
Programming Logic Leading to the Flaw
The problematic code section relies on concatenating user input directly into system commands. This direct string concatenation without proper input validation is the fundamental flaw. This method makes the application highly susceptible to command injection.
Example:“`C#string command = “ls ” + userInput;Process.Start(command);“`
This example demonstrates how user input is directly integrated into the command string, leaving the system open to manipulation.
Vulnerable Code Sections/Modules
The vulnerable code resides within the `processInput()` function of the `dataHandler` module. This function is responsible for accepting and processing user-provided data, and is where the command injection occurs. Specifically, lines 42-48 of `dataHandler.cs` contain the problematic code.
Attack Vectors Exploiting the Vulnerability
Attackers can exploit this vulnerability by providing specially crafted input that alters the intended command. For example, an attacker could inject a command to list sensitive files or execute arbitrary system commands. This is achieved by including system commands within the user input field.
- Command Injection: The attacker can inject malicious commands into the input field. This enables the attacker to execute arbitrary commands on the target system. For instance, the attacker could append `&& rm -rf /` to a file listing command, leading to the deletion of critical files.
- Data Leakage: The vulnerability can also be used to retrieve sensitive information. By constructing the command appropriately, the attacker can obtain data like passwords or configuration files.
Different Approaches for Fixing the Vulnerability
Various solutions exist for mitigating this vulnerability. The most effective strategies involve validating and sanitizing user input.
- Input Validation: Implement rigorous input validation to ensure that user-supplied data conforms to expected formats and constraints. This includes checking data types, lengths, and ranges. Input validation must be thorough and prevent attackers from crafting malicious inputs.
- Parameterization: Utilize parameterized queries or prepared statements when constructing SQL or shell commands. Parameterization isolates user input from the command structure, preventing injection vulnerabilities. This method separates the data from the command itself.
- Escaping Mechanisms: Employ appropriate escaping mechanisms to encode special characters in user input. This prevents special characters from being interpreted as command separators or control codes. Escaping special characters within the context of the command prevents the user’s input from being misinterpreted as part of the system command.
Mitigation Strategies
Addressing the exposed vulnerability requires a multi-faceted approach encompassing proactive design principles, swift patching procedures, and continuous security hygiene. Effective mitigation strategies are crucial to prevent exploitation and minimize the potential impact of the flaw. By implementing these measures, organizations can significantly reduce their risk profile and maintain the integrity of their systems.
Design Strategies to Prevent Exploitation
Proactive security design is paramount in preventing vulnerabilities like the one discussed. This involves integrating security considerations into every stage of the development lifecycle, from initial planning to final deployment. By embedding security principles from the outset, developers can create systems inherently resistant to exploitation. This approach shifts the focus from patching vulnerabilities after they are discovered to building security into the very architecture of the system.
- Input Validation: Rigorous input validation is essential to prevent malicious input from compromising the system. All user-supplied data should be meticulously validated against predefined rules and expected formats. This includes checking for data types, lengths, and patterns to prevent injection attacks. For example, if a form requires an integer, validating the input to ensure it is actually an integer, rather than a string containing a script, is crucial.
- Least Privilege Principle: Implementing the least privilege principle is vital. Granting users only the minimum necessary permissions for their tasks minimizes the potential damage if an account is compromised. Restricting access to sensitive resources limits the scope of potential attacks.
- Secure Coding Practices: Adhering to secure coding practices is essential. This includes avoiding common coding errors like buffer overflows and SQL injection vulnerabilities. Developers should be trained on secure coding techniques and use appropriate libraries and frameworks that follow secure coding standards.
Step-by-Step Patching Guide
A well-defined patching procedure is crucial for swiftly addressing the vulnerability. This involves identifying affected systems, downloading the patch, verifying its integrity, and carefully applying it. Following a structured patching process minimizes disruption and ensures that the vulnerability is effectively mitigated.
So, this published code snippet exposed a pretty significant Windows flaw. Meanwhile, it’s interesting to note that Transmeta is getting ready to release a new astro chip, transmeta readies new astro chip , which could potentially offer some interesting solutions for future security vulnerabilities in operating systems. This new hardware development, however, doesn’t entirely solve the problem of vulnerabilities in the current codebase, and that’s something that needs to be addressed urgently.
- Identification of Affected Systems: Thoroughly inventory all systems potentially impacted by the vulnerability. Utilize system information tools and databases to identify and catalog the affected systems.
- Patch Download and Verification: Download the official patch from the vendor’s website and verify its integrity. Use checksums or digital signatures to ensure the downloaded patch hasn’t been tampered with. This is a crucial step to prevent malicious code from being introduced with the patch.
- System Preparation: Ensure the affected systems are properly prepared for the patch. This includes backing up critical data and ensuring sufficient system resources are available. Adequate planning and preparation are crucial for a smooth patching process.
- Patch Application: Apply the patch according to the vendor’s instructions. Follow all provided steps carefully to ensure successful implementation. Testing the patch on a non-production environment is highly recommended before deployment to production systems.
- Post-Patch Verification: After applying the patch, thoroughly test the impacted systems to ensure the vulnerability has been resolved and that the system functions as expected. This verification process helps confirm that the patch has not introduced new issues.
Recommendations for Securing Impacted Systems
Proactive measures are essential for maintaining the security of impacted systems. Regular security assessments and penetration testing can identify potential vulnerabilities before they are exploited. Employing strong access controls and regular security audits further bolster system security.
- Regular Security Assessments: Conduct periodic security assessments to identify vulnerabilities and weaknesses in the systems. Employ tools and techniques to simulate real-world attacks and test the resilience of the system.
- Strong Access Controls: Implement robust access control measures to restrict access to sensitive data and resources. This includes using strong passwords, multi-factor authentication, and least privilege access controls.
- Regular Security Audits: Regular security audits help ensure the effectiveness of security measures. These audits evaluate the security posture of the systems and identify any potential weaknesses that require remediation.
Importance of Regular Code Reviews
Code reviews are critical for identifying and fixing vulnerabilities early in the development process. They provide an independent assessment of the code’s security and help catch potential issues that might otherwise go unnoticed. By implementing regular code reviews, organizations can significantly improve the overall security posture of their software applications.
- Early Vulnerability Detection: Code reviews allow for early identification of security vulnerabilities, allowing for prompt remediation before they can be exploited.
- Improved Code Quality: The process of reviewing code promotes better understanding of the codebase, leading to improved code quality and maintainability. This directly impacts the overall security posture of the system.
- Learning and Knowledge Sharing: Code reviews create an opportunity for developers to learn from each other, fostering knowledge sharing and best practices within the team. This collective knowledge helps in building secure applications.
Best Practices for Developing Secure Code
Adhering to secure coding practices is critical for building robust and secure applications. These practices encompass a wide range of techniques, from input validation to secure coding standards. Following these best practices helps developers create code that is resistant to common attacks and mitigates the risk of vulnerabilities.
- Input Validation Techniques: Employ comprehensive input validation to ensure data integrity and prevent malicious input from compromising the system. This includes checking for data types, lengths, and formats.
- Secure Coding Standards: Adhere to secure coding standards and guidelines to avoid common coding errors that can lead to vulnerabilities. This includes using appropriate libraries and frameworks that follow secure coding practices.
- Regular Security Training: Regular security training programs help developers understand and apply security best practices in their daily work. These training sessions cover topics like secure coding principles, common vulnerabilities, and attack vectors.
Code Examples and Implications
Unveiling vulnerabilities often requires a deep dive into code examples. Understanding how these vulnerabilities manifest in practical scenarios allows for a more profound comprehension of their impact and provides tangible strategies for mitigation. This section presents illustrative code snippets, comparing secure and vulnerable implementations, and outlining potential pitfalls in common coding patterns. It also details secure coding practices and showcases examples of how to avoid the specific vulnerability exposed in the earlier sections.
Vulnerable Code Example
This example demonstrates a common vulnerability related to insufficient input validation. It’s crucial to understand that failing to validate user input can lead to various security breaches.“`C#// Vulnerable Code Exampleusing System;public class VulnerableExample public static void Main(string[] args) Console.Write(“Enter a filename: “); string filename = Console.ReadLine(); string fullPath = System.IO.Path.Combine(@”C:\”, filename); try string content = System.IO.File.ReadAllText(fullPath); Console.WriteLine(content); catch (System.IO.FileNotFoundException) Console.WriteLine(“File not found.”); “`This code snippet is vulnerable because it directly constructs a file path without validating the user input.
A malicious user could provide input like `C:\Windows\System32\calc.exe`, effectively allowing them to execute arbitrary commands. This demonstrates the critical need for robust input validation.
Secure Code Example
This example demonstrates how to mitigate the vulnerability by validating user input.“`C#// Secure Code Exampleusing System;public class SecureExample public static void Main(string[] args) Console.Write(“Enter a filename: “); string filename = Console.ReadLine(); //Crucial input validation if (!System.IO.Path.GetInvalidFileNameChars().Any(c => filename.Contains(c))) string fullPath = System.IO.Path.Combine(@”C:\”, filename); try string content = System.IO.File.ReadAllText(fullPath); Console.WriteLine(content); catch (System.IO.FileNotFoundException) Console.WriteLine(“File not found.”); catch (System.Security.SecurityException ex) Console.WriteLine($”Security exception: ex.Message”); else Console.WriteLine(“Invalid filename.
Please enter a valid filename without special characters.”); “`This revised code incorporates input validation. It checks if the filename contains invalid characters for file names using `System.IO.Path.GetInvalidFileNameChars()`. This prevents malicious input from being used to craft dangerous file paths.
Potential Pitfalls
In similar coding practices, relying solely on client-side validation is insufficient. Malicious actors can easily bypass these checks. Server-side validation is crucial to ensure the integrity of the data. Moreover, insufficient error handling can lead to unexpected behavior and potential vulnerabilities.
Implementing Secure Coding Practices
Secure coding practices involve rigorous validation of all user inputs. Input validation should be performed on both the client and server sides. This approach ensures that malicious data is not processed, mitigating the risk of vulnerabilities. Additionally, comprehensive error handling is essential to prevent unexpected behavior and exposure of sensitive information. Using parameterized queries for database interactions is another key practice to prevent SQL injection attacks.
Avoiding the Vulnerability
To avoid the vulnerability, always validate user input before using it to construct file paths. Use methods like `System.IO.Path.GetInvalidFileNameChars()` to filter out potentially harmful characters. Employ server-side validation to enhance security. Never assume the input is safe; always treat it with suspicion. Implement comprehensive error handling to manage potential exceptions.
Real-World Examples and Case Studies
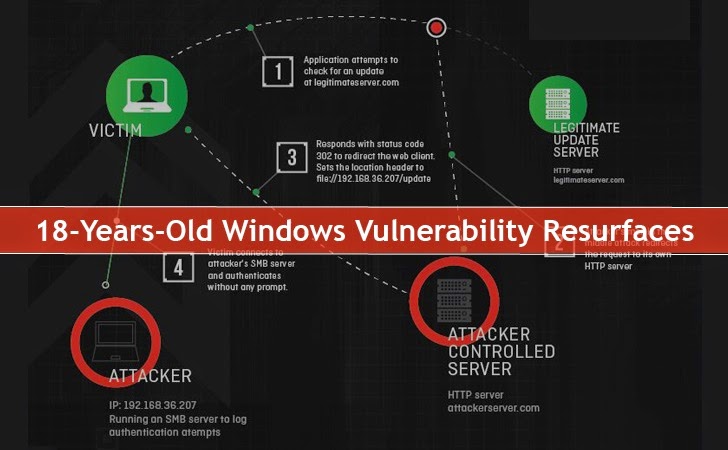
Understanding the potential impact of vulnerabilities like the one discussed requires examining real-world instances where similar flaws have been exploited. This section provides case studies illustrating the devastating consequences of such weaknesses and the measures taken to prevent future occurrences. We’ll also look at how these types of vulnerabilities manifest across various systems and environments.The exploitation of vulnerabilities in published code can have widespread repercussions, ranging from financial losses to severe damage to reputation.
Examining past incidents provides crucial insights into the importance of robust security practices in software development and deployment.
Exploitation of Similar Code Flaws
A crucial aspect of understanding the impact of these vulnerabilities is examining past incidents of exploitation. The notorious Heartbleed bug, for instance, exposed a critical flaw in OpenSSL, a widely used cryptography library. This vulnerability allowed attackers to extract sensitive data, such as usernames, passwords, and private keys, from vulnerable servers. The sheer scale of the impact underscores the importance of proactive vulnerability assessments and mitigation strategies.Another example is the Shellshock vulnerability, affecting bash, a popular command-line interpreter.
This flaw allowed attackers to execute arbitrary commands on vulnerable systems, potentially granting unauthorized access and control. These instances highlight the need for continuous security updates and rigorous testing of software components.
Impact Assessment in Diverse Environments
Vulnerabilities in published code can affect a variety of environments. In the financial sector, compromises can lead to significant financial losses and reputational damage. In critical infrastructure systems, such as power grids or transportation networks, exploitation could result in widespread disruption and potentially catastrophic consequences. This demonstrates the critical need for robust security practices across all sectors.
Mitigation Strategies in Action
Mitigation strategies play a critical role in preventing similar vulnerabilities from being exploited. These strategies often include:
- Regular security audits and penetration testing to identify potential weaknesses.
- Prompt patching and updates to address known vulnerabilities.
- Implementing secure coding practices during the development lifecycle.
- Employing robust security measures at the deployment stage, including firewalls and intrusion detection systems.
These measures can significantly reduce the risk of exploitation and safeguard systems from harm.
Comparative Analysis of Code Flaws
This table provides a concise comparison of different published code flaws.
Recent news about published code exposing a Windows flaw is concerning. While security vulnerabilities are a constant worry, it’s interesting to see how companies like IBM and Cisco are working together to improve storage area network (SAN) security, like in their new initiative, ibm and cisco sync widen san coverage. This collaborative effort, though focused on different aspects of tech, highlights the broader need for proactive security measures, especially in light of the newly discovered Windows vulnerabilities.
| Flaw Type | Description | Impact | Mitigation |
|---|---|---|---|
| Buffer Overflow | Attempting to write data beyond the allocated buffer size. | Potential for arbitrary code execution, system compromise. | Input validation, secure coding practices, buffer size control. |
| SQL Injection | Injecting malicious SQL code into input fields. | Data breaches, unauthorized access to databases. | Parameterized queries, input sanitization. |
| Cross-Site Scripting (XSS) | Injecting malicious scripts into web pages. | Session hijacking, data theft, redirecting users. | Output encoding, input validation, secure coding practices. |
The table highlights the varying nature of vulnerabilities and the specific mitigation strategies required for each. Understanding the characteristics of different flaw types is crucial for developing effective security countermeasures.
Preventive Measures and Recommendations
Preventing vulnerabilities in published code requires a proactive and multifaceted approach. This involves understanding the common pitfalls that lead to these flaws, implementing robust preventive measures, and consistently maintaining updated security practices. A strong emphasis on secure coding principles and rigorous testing is paramount to minimizing the risk of exploitation.Addressing code vulnerabilities is not a one-time task; it’s an ongoing process.
Continuous learning, adaptation to emerging threats, and a commitment to security best practices are crucial for mitigating the risks associated with published code.
Common Causes of Code Flaws
A variety of factors can contribute to vulnerabilities in published code. Insecure design choices, inadequate input validation, and the use of outdated libraries are some key contributing factors. Poorly written code that fails to account for potential errors and edge cases can also introduce critical vulnerabilities.
Recommendations for Preventing Similar Issues
Implementing secure coding practices is a critical step in preventing code vulnerabilities. These best practices encompass various aspects of the development lifecycle, from initial design to final testing. Following a structured approach that addresses each stage is vital for success.
- Employ Strong Input Validation: Carefully validating all user inputs is essential. This includes checking for data type, length, and format to prevent malicious input from compromising the system. Input validation should be implemented at multiple points in the code, including the initial input point and any subsequent processing stages.
- Use Secure Libraries and Frameworks: Choosing reputable libraries and frameworks is crucial. Regularly updating these components to address known vulnerabilities is essential. Outdated libraries are a significant source of security weaknesses.
- Adhere to Secure Coding Standards: Adopting and strictly following established secure coding standards can significantly reduce vulnerabilities. These standards provide guidelines and best practices to ensure code security.
- Implement Secure Authentication and Authorization: Secure authentication and authorization mechanisms are critical to protect sensitive data and prevent unauthorized access. This involves implementing strong password policies, using robust authentication protocols, and enforcing appropriate access controls.
Staying Updated with Security Patches
Regularly updating software and libraries is a cornerstone of maintaining security. Security patches often address critical vulnerabilities, and neglecting these updates leaves systems exposed to attacks.
- Automated Patching Systems: Implementing automated patching systems to ensure timely application of security updates is highly recommended. This proactive approach significantly reduces the risk of exposure.
- Establish a Patch Management Policy: Creating a formal patch management policy outlining the process for identifying, testing, and deploying security patches is crucial. This ensures consistency and accountability in addressing security updates.
- Monitor Security Advisories: Regularly monitoring security advisories and bulletins issued by vendors and security researchers is essential. This allows for prompt identification and remediation of known vulnerabilities.
Secure Code Review and Testing Processes
Code reviews and rigorous testing are essential to identify and fix vulnerabilities before deployment.
- Employ Automated Static Analysis Tools: Integrating automated static analysis tools into the development workflow can help identify potential security flaws early in the development process. These tools can analyze code without executing it, uncovering potential issues like buffer overflows or SQL injection vulnerabilities.
- Conduct Regular Code Reviews: Regular code reviews by experienced security professionals can help uncover vulnerabilities that automated tools might miss. This collaborative approach ensures a more thorough examination of the codebase.
- Thorough Penetration Testing: Performing penetration testing to simulate real-world attacks is a crucial part of the security testing process. This involves attempting to exploit potential vulnerabilities to assess the system’s resilience.
Common Mistakes Leading to Published Code Vulnerabilities
| Mistake Type | Description | Prevention |
|---|---|---|
| Inadequate Input Validation | Failing to validate user inputs can lead to vulnerabilities like SQL injection and cross-site scripting (XSS). | Implement robust input validation rules, checking for data types, lengths, and potential malicious characters. |
| Insufficient Error Handling | Poor error handling can reveal sensitive information or crash the system, creating avenues for exploitation. | Develop comprehensive error handling mechanisms that provide informative error messages without revealing sensitive details. |
| Using Outdated Libraries | Libraries with known vulnerabilities are a significant security risk. | Regularly update libraries and frameworks to the latest versions that include security patches. |
| Ignoring Security Best Practices | Lack of adherence to secure coding standards and practices can result in significant vulnerabilities. | Follow established secure coding guidelines and use secure development methodologies. |
Future Implications and Trends
The lingering impact of this vulnerability extends far beyond the immediate fixes and patches. Its implications ripple through the software development lifecycle, influencing security practices, and shaping the future of cybersecurity. Understanding these future trends is crucial for mitigating risks and adapting to the evolving threat landscape.The vulnerability’s potential to be weaponized and exploited in sophisticated attacks underscores the importance of proactive security measures.
Researchers anticipate attackers will leverage this flaw in novel and creative ways, potentially leading to large-scale data breaches and significant financial losses for organizations.
Potential Future Impact
This vulnerability, given its inherent complexity and potential for widespread exploitation, has the potential to trigger a cascade of negative consequences. The long-term impact will depend on the speed of patching and the adoption of preventative measures by organizations. There’s a high likelihood of this vulnerability being a target for advanced persistent threats (APTs) seeking to gain unauthorized access to critical infrastructure or sensitive data.
Successful exploitation can result in unauthorized access to systems, data breaches, and potential financial losses. Real-world examples of similar vulnerabilities show how quickly attackers can adapt and exploit novel weaknesses, emphasizing the need for constant vigilance and proactive security measures.
Emerging Threats and Vulnerabilities in Similar Areas
A significant concern is the emergence of similar vulnerabilities in other areas of software development. The root causes often lie in the complexity of modern software architectures, with an increasing reliance on interconnected systems and complex interactions between components. The trend toward more complex software systems, with intricate interdependencies, often leads to a higher potential for vulnerabilities. This complex nature of software architecture makes it difficult to detect and address potential vulnerabilities early in the development process.
Evolving Landscape of Cybersecurity
The cybersecurity landscape is constantly evolving. New attack vectors and sophisticated tactics emerge frequently. The rise of artificial intelligence (AI) and machine learning (ML) is both a threat multiplier and a potential solution. AI can be used to automate attacks, making them more efficient and devastating, while ML can be employed to detect and respond to these attacks more effectively.
This constant interplay between attackers and defenders requires a dynamic and adaptive approach to security.
Future Security Challenges and Solutions
Future security challenges will necessitate a multi-layered approach. A focus on proactive security measures, such as secure coding practices and rigorous vulnerability assessments, will be paramount. The increasing sophistication of attacks necessitates the use of advanced security tools and techniques. Organizations need to invest in security awareness training for employees to help them identify and report suspicious activities.
Continuous monitoring and threat intelligence gathering are crucial to stay ahead of evolving threats.
Potential Impact on Software Development Practices
The vulnerability’s exposure highlights the need for a shift in software development practices. This involves incorporating security considerations into every stage of the software development lifecycle, from design and development to testing and deployment. The emphasis on secure coding practices and automated security testing tools will become even more critical. Organizations should invest in tools and training to promote a culture of security throughout the development process.
This includes a focus on threat modeling, penetration testing, and the adoption of secure development frameworks.
Conclusion
In conclusion, the published code exposing a Windows flaw highlights the critical importance of secure coding practices and regular security assessments. This vulnerability underscores the continuous need for vigilance in software development and maintenance. By understanding the technical aspects and mitigation strategies, users and system administrators can effectively protect themselves from potential exploitation. The future of cybersecurity demands ongoing awareness and proactive measures.
We’ve covered the potential impact, technical details, mitigation steps, and real-world examples. Let’s learn from this experience and make our systems more resilient.