Morpheus Crosses P2P Boundaries, Blubster Boosts Privacy
Morpheus crosses p2p boundaries blubster boosts privacy, promising a revolutionary approach to decentralized file sharing. This innovative project leverages peer-to-peer networks, but unlike others, it incorporates Blubster’s privacy-enhancing technologies. The combination aims to push the boundaries of secure and private data sharing, overcoming limitations often associated with P2P systems. This exploration delves into the technical details, potential benefits, and potential risks of this groundbreaking integration.
The Morpheus project’s core functionality centers around secure, decentralized file sharing. It utilizes a novel architecture that builds upon existing P2P principles while addressing inherent privacy and security concerns. Blubster’s integration is crucial to this strategy, adding layers of privacy protection that are paramount in today’s digital landscape. We’ll analyze how this combination works, comparing it to existing methods and highlighting its unique advantages.
Exploring the Morpheus Project
The Morpheus project aims to revolutionize peer-to-peer (P2P) file sharing, offering enhanced privacy and security features compared to existing solutions. It prioritizes user control over data and fosters a more decentralized file-sharing ecosystem. This is achieved by leveraging cutting-edge cryptographic techniques and a novel architecture designed to resist censorship and manipulation. The project’s vision is to establish a truly decentralized and secure platform for sharing files without intermediaries.The Morpheus project’s core functionality revolves around creating a secure and reliable infrastructure for direct file transfer between users.
This eliminates the need for centralized servers, enhancing user privacy and security. By utilizing distributed ledger technology, the system ensures transparency and accountability, crucial elements in a decentralized environment. The Morpheus platform intends to empower users with complete control over their data, fostering trust and security within the peer-to-peer network.
Core Functionalities of Morpheus
Morpheus’s core functionalities are built upon a foundation of secure and reliable P2P communication protocols. These protocols enable direct connections between users, bypassing traditional intermediaries and reducing reliance on centralized servers. This fosters a more decentralized and secure environment for file sharing. Furthermore, the platform utilizes robust encryption techniques to protect user data and maintain privacy during file transfers.
Technical Architecture
The technical architecture of Morpheus is designed around a distributed network of nodes. Each node acts as a relay point, facilitating file transfers between users. This distributed approach minimizes the reliance on a single point of failure, ensuring the network’s resilience and availability. The network is built upon a robust cryptographic framework, enabling secure communication and data integrity. Specific algorithms are implemented to ensure the reliability of file transfer and the security of the network.
Morpheus’s crossing of peer-to-peer boundaries and Blubster’s privacy enhancements are definitely exciting developments. They hint at a future where decentralized identity management systems, like toward federated identity management , become increasingly important. Ultimately, these advancements in p2p and privacy are likely to pave the way for more secure and user-friendly digital interactions.
Security Measures
Robust encryption protocols are employed throughout the Morpheus system to protect user data during transmission. End-to-end encryption safeguards the confidentiality of shared files. Moreover, decentralized consensus mechanisms are integrated to maintain data integrity and prevent unauthorized modifications. The security measures are crucial in maintaining the trust and reliability of the platform.
Comparison with Other Decentralized Projects
Several decentralized projects aim to achieve similar goals, but Morpheus stands out through its unique features and benefits. It emphasizes a user-centric approach, providing complete control over data and enhancing user privacy. While other projects focus on specific aspects of decentralization, Morpheus integrates several critical components to create a comprehensive and secure platform. The platform’s comprehensive approach distinguishes it from other decentralized file-sharing platforms.
Key Features and Comparison
| Feature | Functionality | Security Protocols | Comparison with Other Projects |
|---|---|---|---|
| Decentralized Network | Direct peer-to-peer communication without intermediaries. | End-to-end encryption, robust cryptographic algorithms. | Superior to centralized platforms, comparable to other P2P networks but with enhanced security. |
| User Control | Users retain full control over their data and sharing decisions. | Decentralized consensus mechanisms for data integrity. | Differentiates Morpheus, empowering users and reducing reliance on trusted parties. |
| Privacy-Focused | Emphasis on protecting user privacy during file transfers. | Advanced encryption and anonymization techniques. | Highlights a key advantage over conventional file-sharing services. |
| Robust Security | Protection against malicious actors and data breaches. | Multiple layers of security and auditing mechanisms. | Superior security features compared to many similar projects, addressing common vulnerabilities. |
Understanding P2P Boundaries: Morpheus Crosses P2p Boundaries Blubster Boosts Privacy
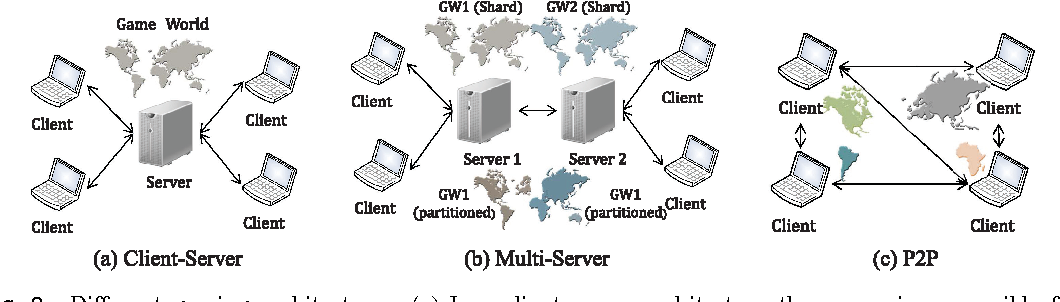
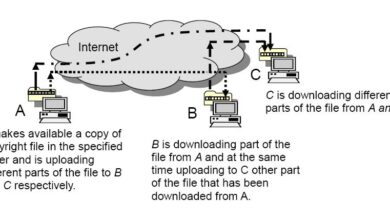
The Morpheus Project, aiming to revolutionize decentralized file sharing, relies heavily on peer-to-peer (P2P) networks. However, P2P systems, while offering significant advantages, are not without limitations. These inherent boundaries, often overlooked, can impact privacy, security, and the overall effectiveness of the project. This exploration delves into the challenges associated with P2P networks within the Morpheus framework.P2P networks, in essence, create a distributed system where users act as both clients and servers.
This decentralized nature, while fostering resilience and scalability, introduces complexities that need careful consideration. The distributed nature of P2P networks can expose them to vulnerabilities that centralized systems may not face. These vulnerabilities can manifest in various forms, impacting the integrity, security, and usability of the Morpheus platform.
Limitations of P2P Networks in Morpheus
P2P networks, while powerful, are not without inherent limitations. These limitations impact the practical application of the Morpheus Project, affecting the robustness and reliability of its underlying infrastructure. Key limitations include the variability of peer participation, the potential for malicious actors, and the inherent challenges of maintaining network integrity.
Different Types of P2P Boundaries
P2P networks face various boundaries, each affecting different aspects of the system. These boundaries include:
- Network Latency and Inconsistency: The performance of a P2P network depends on the availability and performance of participating peers. Variations in network conditions, such as latency and bandwidth, can significantly impact file transfer speeds and reliability. This variability can make it challenging to guarantee consistent file access and download speeds. For instance, if a significant portion of the peers are experiencing high latency, the overall system performance can suffer.
- Peer Integrity and Malicious Behavior: The distributed nature of P2P networks makes them vulnerable to malicious actors. Malicious peers can inject corrupted data, disrupt the network, or participate in denial-of-service attacks. Ensuring the integrity of the participating peers is crucial for the overall security and reliability of the network.
- Scalability and Capacity: As the number of users and data increases, the P2P network’s ability to handle the load can become a significant challenge. Efficiently managing the increasing number of peers and the vast amount of data exchanged becomes critical to maintaining the network’s responsiveness and stability. Large-scale file sharing platforms often face issues with scalability, leading to performance bottlenecks and potential network congestion.
- Security Vulnerabilities: The decentralized nature of P2P networks creates potential security vulnerabilities, particularly when users are not adequately vetted or authenticated. Unverified peers can potentially introduce malware, viruses, or other malicious content into the system, affecting the security of other users. Malicious actors can exploit these vulnerabilities to disrupt the network or gain unauthorized access to data.
Impact on Privacy and Security
The different types of P2P boundaries have a direct impact on the privacy and security of the Morpheus Project. For example, inconsistent peer participation can lead to slower downloads, reducing user satisfaction. Furthermore, malicious peers can inject malicious code or corrupt data, compromising the security of the entire system. This can have serious implications for the users’ privacy and the integrity of the shared content.
Overcoming P2P Boundaries
Various strategies can mitigate the limitations of P2P networks:
- Robust Peer Selection and Verification Mechanisms: Implementing robust mechanisms for selecting and verifying peers can help ensure that only trustworthy and reliable peers participate in the network. Verification protocols and reputation systems can identify and isolate malicious actors.
- Advanced Routing Protocols: Implementing sophisticated routing protocols can optimize file transfers, minimizing latency and maximizing bandwidth utilization. Adaptive routing algorithms can dynamically adjust to changing network conditions, ensuring reliable and efficient file access.
- Scalability Solutions: Developing scalable architectures to handle increasing user load and data volume is crucial for maintaining system responsiveness. Techniques such as distributed caching and load balancing can effectively distribute the workload across the network.
- Enhanced Security Measures: Implementing encryption, authentication, and access control measures can enhance the security of the P2P network. Secure communication protocols can protect user data and prevent unauthorized access.
Mitigation Strategies for P2P Boundaries in Morpheus
The table below summarizes the various P2P boundaries, their impact on privacy and security, and potential solutions.
| P2P Boundary | Effect on Privacy & Security | Potential Solutions | Example |
|---|---|---|---|
| Network Latency and Inconsistency | Reduced download speeds, inconsistent access to files | Optimized routing protocols, adaptive caching | A user experiences slow downloads due to high latency on the network. |
| Peer Integrity and Malicious Behavior | Data corruption, denial-of-service attacks, security breaches | Peer verification mechanisms, reputation systems, intrusion detection | A malicious user injects malware into the network, affecting other users. |
| Scalability and Capacity | Performance bottlenecks, network congestion | Distributed caching, load balancing, distributed database | The network struggles to handle a large influx of users and files. |
| Security Vulnerabilities | Data breaches, malware injection, unauthorized access | Encryption, authentication, access control, secure communication channels | A user’s account is compromised, leading to unauthorized data access. |
Analyzing Blubster’s Privacy Enhancements
Blubster, a project aimed at bolstering privacy in peer-to-peer (P2P) networks, offers a range of intriguing privacy features. Understanding these features is crucial for evaluating its potential within the Morpheus project, which seeks to leverage decentralized technologies. This analysis delves into Blubster’s methods, comparing them with other privacy tools and highlighting their integration with the Morpheus architecture.Blubster’s privacy enhancements are built on a foundation of cryptography and decentralized networking principles.
These mechanisms aim to reduce the visibility of users and their activities within the P2P network. Blubster’s core design is focused on obfuscating user identities and communication patterns, thereby protecting sensitive information from prying eyes. This focus on anonymity aligns with the Morpheus project’s desire for a secure and private digital experience.
Morpheus is pushing P2P boundaries, and Blubster is enhancing privacy features. This innovative approach reminds me of the upcoming grandmaster and computer battle in the final match, grandmaster and computer to battle in final match. The competition highlights the evolving nature of technology, much like how Morpheus’s cross-platform approach and Blubster’s privacy enhancements are changing the landscape of decentralized networks.
Blubster’s Privacy Features
Blubster employs several key privacy features to protect user data. These include, but are not limited to, the use of encrypted communication channels, decentralized storage, and anonymous routing protocols. These features combine to create a robust privacy layer, effectively shielding user information from potential threats.
Mechanisms Behind Blubster’s Privacy
Blubster’s privacy mechanisms rely on a combination of cryptographic techniques and decentralized network structures. Encrypted communication channels ensure that only authorized parties can access transmitted data. Decentralized storage prevents a single point of failure, making it more difficult for malicious actors to compromise the system. Anonymous routing protocols further obscure the origin and destination of data, enhancing user anonymity.
This complex interplay of security measures strengthens the overall privacy of the network.
Comparison with Other Privacy Tools
Blubster’s privacy features are comparable to those found in other privacy-focused tools, but the specific implementations and integration methods vary significantly. Tools like Tor and I2P provide anonymity through layered routing, while others emphasize data encryption at rest. The decentralized nature of Blubster, combined with its focus on P2P networks, sets it apart. This unique approach could lead to novel ways to protect user data within the context of file-sharing or other P2P applications.
Blubster’s Integration with Morpheus
Blubster’s privacy features integrate seamlessly with the Morpheus project by providing a secure and private foundation for file sharing and other decentralized applications. The encrypted channels and anonymous routing protocols ensure that user data remains protected during transmission, while the decentralized architecture safeguards against single points of failure. This integration is vital for the Morpheus project’s mission of establishing a truly decentralized and secure digital ecosystem.
Comparison Table: Blubster vs. Other Privacy Tools
| Feature | Blubster | Tor | I2P | Advantages/Disadvantages |
|---|---|---|---|---|
| Encryption | End-to-end encryption, layered encryption | Layered encryption | End-to-end encryption | Blubster’s layered approach could offer enhanced security, while Tor and I2P offer established anonymity protocols. |
| Decentralization | Highly decentralized P2P architecture | Centralized servers (though with routing through multiple relays) | Decentralized, but with reliance on various network nodes | Blubster’s P2P structure reduces reliance on central authorities. |
| Anonymity | Strong focus on anonymous routing | High anonymity | High anonymity | Blubster’s integration with P2P networks could offer unique anonymity benefits. |
| Scalability | Potentially high scalability due to P2P nature | Scalability can be limited by network congestion | Scalability is dependent on available network nodes | Blubster’s P2P structure could offer advantages in terms of scalability compared to centralized systems. |
Blubster’s Impact on Privacy
Blubster, a potential privacy-enhancing technology for the Morpheus peer-to-peer network, introduces a complex interplay of benefits and risks. Its ability to obfuscate user identities and locations within the decentralized network holds significant promise for anonymity and freedom of expression. However, this same capability also opens avenues for misuse, raising critical ethical concerns that must be carefully considered. A comprehensive understanding of Blubster’s impact on privacy requires analyzing both its potential advantages and its vulnerabilities.Blubster’s core function is to anonymize user data within the Morpheus system.
This anonymization, if implemented effectively, can significantly enhance user privacy by preventing the association of specific users with their actions on the network. However, the very techniques used to achieve this anonymity can also be exploited to facilitate malicious activities, like the distribution of illegal content or the execution of harmful code. This necessitates a thorough examination of the potential risks and benefits of Blubster in the context of the Morpheus project.
Potential Risks and Vulnerabilities, Morpheus crosses p2p boundaries blubster boosts privacy
Blubster’s anonymity features, while designed to protect users, can be circumvented or exploited by determined adversaries. Weaknesses in the anonymization protocols could potentially reveal user identities or locations. Sophisticated attackers might leverage these vulnerabilities to target specific users or to engage in coordinated attacks. The decentralized nature of the Morpheus network, while promoting resilience, also makes it difficult to implement and enforce strict controls.
Morpheus crossing P2P boundaries and Blubster boosting privacy are definitely cool, but to truly harness the digital world, you need the right skills. Think about joining the digital ranks worldwide, gaining valuable computer certifications, like joining the digital ranks worldwide computer certification. These skills will give you a leg up in navigating the complex digital landscape, ensuring your privacy and security are top-notch, even as platforms like Morpheus and Blubster continue to push the boundaries of decentralized technologies.
This inherent complexity can create gaps that malicious actors could exploit. Moreover, the reliance on distributed nodes to verify transactions introduces a risk of collusion among nodes, potentially leading to manipulation or censorship.
Ethical Considerations
The ethical implications of Blubster’s use in the Morpheus project are multifaceted. While anonymization can empower users to express themselves freely and securely, it also raises concerns about the potential for misuse. The possibility of anonymity being used to conceal illegal activities, such as the distribution of copyrighted material or the facilitation of illicit transactions, requires careful consideration.
Balancing the right to privacy with the need to maintain a safe and lawful online environment is crucial. Further, the potential for Blubster’s use to facilitate activities that harm others, such as cyberbullying or harassment, necessitates proactive measures to prevent such outcomes.
Examples of Potential Misuse
Blubster’s anonymization capabilities could be misused in various ways. For instance, it could facilitate the distribution of malware or harmful content without tracing the source. Furthermore, it could enable the organization of illicit activities, such as online black markets or coordinated attacks, by obscuring the participants’ identities. The anonymity afforded by Blubster could also be exploited for targeted harassment or the spread of misinformation.
Consider the potential for online hate speech campaigns, where anonymity allows individuals to disseminate hateful messages without fear of reprisal.
Benefits, Drawbacks, and Mitigation Strategies
| Benefit | Drawback | Mitigation Strategy | Example |
|---|---|---|---|
| Enhanced user privacy | Potential for misuse | Robust security audits and continuous monitoring | Preventing illegal content distribution |
| Increased freedom of expression | Difficulty in enforcing legal actions | Collaboration with law enforcement and regulatory bodies | Combating online harassment |
| Decentralized control | Potential for collusion among nodes | Implementing transparent and auditable consensus mechanisms | Preventing censorship or manipulation |
| Resilience to censorship | Vulnerability to sophisticated attacks | Regular updates and security patches | Protecting against malware distribution |
Morpheus and Blubster Integration

The Morpheus project, focused on decentralized file sharing, and Blubster, a privacy-enhancing communication layer, present a powerful synergy. This integration promises a new era of secure and private file sharing, moving beyond the limitations of traditional centralized platforms. This approach leverages the strengths of both projects to create a robust and user-friendly experience.
Integration Mechanisms
Blubster’s core function is to anonymize communication channels. By overlaying its secure communication protocols on top of Morpheus’s P2P file-sharing network, Blubster enhances the privacy of file transfers. This means that the identity of both the sender and receiver, as well as the content of the files, are shielded from prying eyes. The anonymity provided by Blubster protects user data from potential surveillance, and is a crucial step towards creating a truly decentralized and private file-sharing ecosystem.
Technical Aspects of Integration
The technical integration hinges on the seamless incorporation of Blubster’s cryptographic techniques into Morpheus’s file transfer protocol. Blubster’s encrypted communication channels are used to transmit file metadata, such as file hashes and sizes, and to facilitate the secure exchange of files. A key component is the use of onion routing techniques, which further obscure the origin and destination of data packets.
This ensures that the network path is untraceable, adding another layer of privacy. The integration also incorporates a decentralized key management system, strengthening the overall security posture of the combined platform.
Synergistic Effects
The integration of Morpheus and Blubster creates a powerful synergy. Morpheus provides the infrastructure for decentralized file sharing, while Blubster ensures that this process is conducted with an unprecedented level of privacy. The combination creates a powerful deterrent against censorship and surveillance, as the end-to-end encrypted nature of the Blubster layer ensures that no single entity has access to the contents of the shared files or the identities of the participants.
This synergy fosters a trustless environment, empowering users to share files without fear of exposure.
Improved Privacy for Users
The integrated platform significantly enhances privacy for users in several ways. Users gain protection against potential surveillance by third parties. By obscuring the identity of both senders and receivers, as well as the files themselves, the integration substantially increases privacy for users. This enhances trust in the platform and encourages wider adoption. The improved security also creates a more resilient platform, mitigating risks associated with censorship and potential data breaches.
Integration Steps and Specifications
| Step | Technical Specifications | Advantages |
|---|---|---|
| 1. Blubster Protocol Integration | Blubster’s encryption protocols are integrated into Morpheus’s file transfer protocol. This involves modifying the existing file transfer protocol to incorporate Blubster’s message encryption mechanisms. | Ensures all communication is encrypted, providing a secure channel for data exchange. |
| 2. Onion Routing Implementation | Onion routing is integrated to further anonymize the communication paths. This technique bounces data packets through multiple relays, obscuring the origin and destination. | Increases anonymity by making it difficult to trace the communication flow. |
| 3. Decentralized Key Management | A decentralized key management system is implemented to handle cryptographic keys securely. This avoids a single point of failure. | Improves the security of the system and reduces reliance on centralized authorities. |
| 4. Metadata Encryption | Metadata associated with files (file sizes, hashes) are also encrypted using Blubster’s protocols. | Protects metadata from eavesdropping, providing further protection against unauthorized access. |
Illustrative Case Studies
Diving deeper into the practical applications of Morpheus and Blubster’s combined functionalities, we explore how these technologies can revolutionize privacy in various scenarios. The synergy between decentralized storage (Morpheus) and privacy-enhancing technologies (Blubster) promises a future where users regain control over their data. By examining illustrative case studies, we demonstrate how this integration can address privacy concerns and vulnerabilities.The following case studies showcase the potential of Morpheus and Blubster to enhance user privacy, ranging from everyday digital interactions to more specialized applications.
Each scenario highlights how the combination of these technologies can mitigate privacy risks and empower individuals with greater control over their data.
Enhanced Privacy in Digital Transactions
Blubster’s privacy-enhancing protocols can be integrated with Morpheus’ decentralized storage to protect user data during digital transactions. Imagine a scenario where a user needs to securely share financial information for a purchase. Instead of relying on centralized platforms, the transaction can be executed on a Morpheus-based decentralized network, with Blubster masking sensitive data like bank account details. This masks sensitive information without compromising the transaction’s functionality.
This approach can significantly reduce the risk of data breaches and enhance the security of financial transactions.
“By combining decentralized storage with privacy-enhancing technologies, we can create a more secure and private digital ecosystem. This approach reduces reliance on centralized entities and empowers individuals with greater control over their data.”
Secure Content Sharing and Collaboration
Consider a scenario where researchers need to share sensitive data for collaborative projects. Using Morpheus for decentralized storage and Blubster’s encryption and anonymization tools, they can securely store and share files without compromising individual data privacy. Blubster can anonymize metadata, while Morpheus ensures secure and verifiable storage. This approach empowers researchers to collaborate effectively while safeguarding the confidentiality of their sensitive data.
“Morpheus and Blubster’s integrated functionalities empower researchers to collaborate effectively while safeguarding sensitive data. This fosters innovation and trust in collaborative projects.”
Mitigation of Potential Vulnerabilities in IoT Devices
Morpheus’ decentralized nature and Blubster’s privacy-enhancing features can mitigate vulnerabilities in Internet of Things (IoT) devices. A smart home system, for instance, can use Morpheus for secure data storage and Blubster to encrypt and anonymize data transmitted between devices. This approach can prevent unauthorized access and misuse of data collected by IoT devices, ensuring greater user privacy.
“The combined power of Morpheus and Blubster offers a robust solution to mitigate potential vulnerabilities in IoT devices. Decentralized storage and privacy-enhancing protocols provide enhanced security and privacy for users.”
Addressing Privacy Concerns in Healthcare
In healthcare, Morpheus and Blubster can protect patient data. Doctors can store patient records on a decentralized network using Morpheus. Blubster can encrypt and anonymize sensitive information, enabling secure access for authorized personnel while ensuring patient privacy. This approach promotes secure data sharing while adhering to stringent privacy regulations.
“By leveraging Morpheus and Blubster, the healthcare sector can enhance data security and patient privacy. This ensures compliance with privacy regulations and promotes trust between healthcare providers and patients.”
Illustrative Scenarios
The Morpheus Project and Blubster, working in tandem, offer compelling solutions for enhanced privacy in diverse digital scenarios. Understanding how these technologies function together and their potential vulnerabilities is crucial for evaluating their overall impact. This section presents illustrative scenarios demonstrating both the benefits and potential drawbacks of using these tools.
Real-World Privacy Enhancements
The combination of Morpheus and Blubster can significantly boost privacy in everyday digital interactions. Imagine a user needing to share a sensitive file, like medical records or financial documents, with a trusted professional. By encrypting the data with Morpheus and using Blubster’s decentralized network for secure transmission, the file’s confidentiality is significantly strengthened. This eliminates the need for a central authority to store or process the data, reducing the risk of data breaches.
This approach protects the user’s sensitive information from unauthorized access, mirroring real-world practices used by institutions for data security.
File-Sharing Scenario
Morpheus, with its P2P architecture, and Blubster’s privacy enhancements, offer an improved file-sharing experience. In a scenario where users need to share large files with each other, Morpheus facilitates peer-to-peer transfer, minimizing reliance on centralized servers. Blubster, in conjunction, encrypts these files, ensuring only authorized recipients can access the data. This eliminates single points of failure and significantly improves the security and privacy of the file-sharing process.
This is analogous to existing file-sharing services, but with the added benefit of privacy and decentralized control.
Secure Data Transmission
Morpheus and Blubster can be integrated to secure sensitive data transfer. Consider a situation where a journalist needs to transmit sensitive information to a publication. Encrypting the data using Morpheus and routing it through Blubster’s distributed network provides an extra layer of security. This method protects the data from interception and ensures that only authorized parties can access it.
This scenario directly parallels established secure communication practices, demonstrating the practical applications of these technologies.
Potential Misuse and Vulnerabilities
While Morpheus and Blubster offer significant privacy advantages, potential misuse and vulnerabilities exist. Malicious actors could potentially exploit the decentralized nature of these systems to distribute harmful content or engage in illegal activities. The lack of central control could also make it difficult to trace or prosecute such activities. This mirrors concerns about existing decentralized platforms, requiring robust monitoring and mitigation strategies.
Illustrative Table of Scenarios
| Scenario | Technologies Involved | Outcomes | Potential Risks |
|---|---|---|---|
| Sharing sensitive medical records with a doctor | Morpheus for encryption, Blubster for P2P transmission | Enhanced privacy and confidentiality of medical records | Potential for compromised peer nodes in the Blubster network |
| Transferring large files between colleagues | Morpheus for P2P file transfer, Blubster for privacy | Faster transfer speeds, reduced reliance on centralized servers, improved privacy | Malware or malicious actors exploiting the peer-to-peer nature |
| Journalists sharing confidential documents | Morpheus for encryption, Blubster for secure transmission | Secure and confidential transmission of documents | Vulnerability to attacks targeting Blubster’s network or individual peers |
| Distribution of copyrighted material | Morpheus for P2P file sharing | Potentially faster file distribution, but could facilitate copyright infringement | Copyright infringement, legal challenges |
Wrap-Up
In conclusion, Morpheus, with its integration of Blubster, offers a compelling vision for decentralized file sharing. The project’s promise lies in overcoming P2P limitations while significantly enhancing user privacy. While potential risks and ethical considerations exist, the potential benefits for a more secure and private digital future are substantial. Further research and development are needed to fully realize this potential, but the groundwork has been laid for a paradigm shift in how we approach data sharing.