Virus Writers Battle War of Worms
Virus writers battle in war of worms, a relentless digital conflict where malicious code wages war on computer systems. This ongoing struggle involves sophisticated tactics, motivated actors, and significant consequences. From the historical precedents of digital conflicts to the emerging threat of AI-powered viruses, the narrative explores the intricacies of this digital battlefield.
This conflict is waged through viruses that infect files and worms that self-replicate, spreading across networks. Cybercriminals, hacktivists, and even state-sponsored actors participate, each driven by their own motivations, from financial gain to political agendas and espionage. The resulting impact ranges from minor inconveniences to catastrophic network disruptions, highlighting the vulnerability of modern digital infrastructure.
Introduction to the Conflict
The “War of Worms” is a protracted, often unseen, struggle waged in the digital realm. Virus writers, individuals or groups skilled in creating malicious software, employ sophisticated techniques to infiltrate and disrupt computer systems and networks. Their methods range from exploiting vulnerabilities in software to crafting intricate algorithms capable of replicating and spreading rapidly. This conflict transcends mere technical expertise; it embodies a battle of wills, where attackers aim to cause damage and disruption, and defenders strive to maintain security.This ongoing conflict mirrors historical conflicts in the digital space, where individuals and groups have sought to gain advantage through manipulation of information and technology.
The war of worms is characterized by the relentless pursuit of vulnerabilities and the constant adaptation of malicious code to evade detection and remediation. This constant evolution underscores the need for continuous vigilance and proactive security measures in the face of this ongoing conflict.
Definition of Virus Writers and Their Methods
Virus writers are individuals or groups with advanced programming skills who design and release malicious software, commonly known as computer viruses and worms. Their methods involve exploiting vulnerabilities in software, often crafting intricate code to target specific systems or networks. This process includes creating self-replicating programs capable of infecting and spreading across systems without user interaction, as well as developing sophisticated camouflage to evade detection.
They employ diverse tactics, including social engineering, to gain access to systems and propagate their malicious code.
The “War of Worms” Metaphor
The “War of Worms” metaphor effectively captures the dynamic and evolving nature of the conflict. Just as worms burrow through soil, these malicious programs infiltrate and spread through computer systems and networks, causing damage and disruption. The implication is that the struggle is ongoing, and defenders must constantly adapt to new threats. The metaphor also highlights the need for a coordinated and comprehensive defense strategy to combat the pervasive nature of these attacks.
Historical Context of Similar Conflicts
The digital realm has witnessed numerous conflicts with parallels to the “War of Worms”. Early internet worms like Morris Worm demonstrated the potential for widespread disruption. Later, the emergence of sophisticated malware families like Stuxnet, exemplified the escalating sophistication and destructive potential of these attacks. These historical precedents underscore the enduring nature of the struggle between those seeking to exploit vulnerabilities and those working to protect systems.
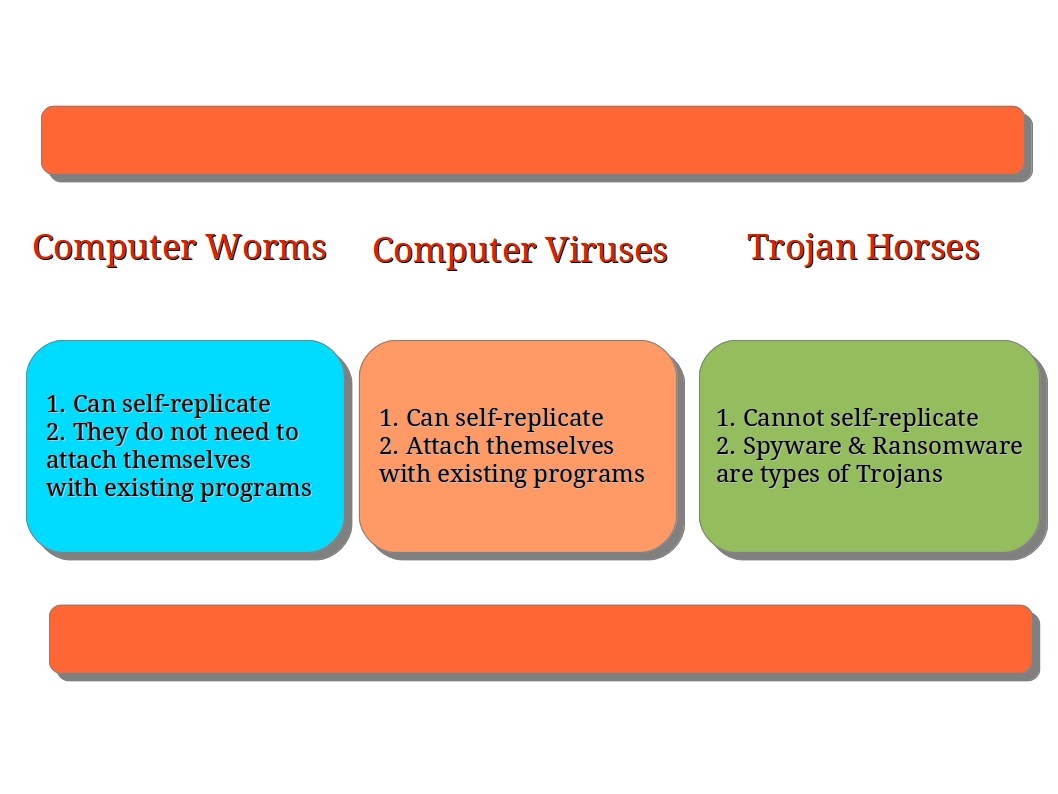
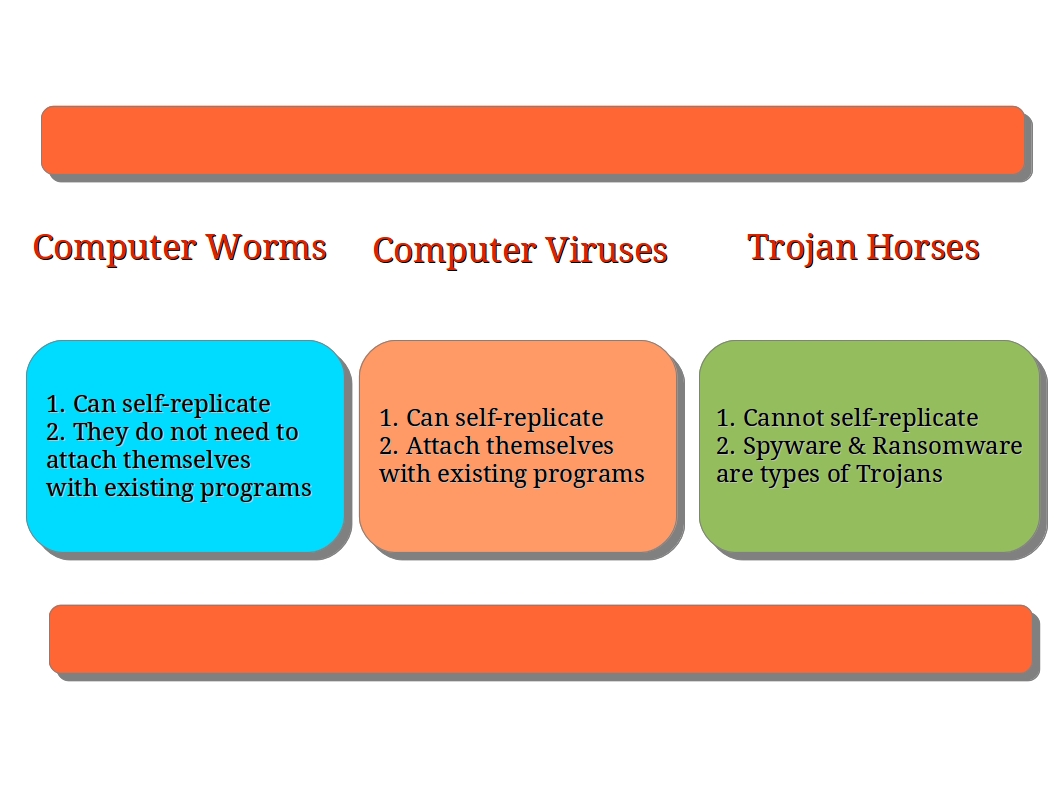
Types of Viruses and Worms Involved in the Conflict, Virus writers battle in war of worms
A variety of malicious software programs, including viruses and worms, are involved in the “War of Worms”. These malicious programs employ diverse techniques and exhibit different behaviors.
Malware Types and Targeting Methods
| Malware Type | Targeting Method | Example | Impact |
|---|---|---|---|
| Virus | Infects files | Win32.Mydoom | System slowdown, data loss |
| Worm | Self-replicating | Code Red | Network congestion, system crashes |
| Trojan | Disguises itself as legitimate software | Zeus | Data theft, unauthorized access |
| Ransomware | Encrypts data and demands payment for decryption | WannaCry | Data loss, financial extortion |
Actors and Motivations

The “War of Worms” isn’t a simple conflict between individuals; it’s a complex interplay of motivations driving diverse actors to participate in this digital battlefield. From hacktivists seeking to disrupt systems to state-sponsored entities aiming for strategic advantage, each player brings unique goals and methods to the table. Understanding these actors and their incentives is crucial to comprehending the intricacies of this digital arms race.
Key Players in the Digital Conflict
This digital conflict involves a diverse range of actors, each with their own motivations and methods. These actors range from individuals and small groups to large organizations and nation-states. The motivations behind their actions vary greatly, but the common thread is the pursuit of specific goals through the use of malicious software.
Motivations Behind Virus and Worm Creation
Motivations behind creating and deploying viruses and worms are as varied as the actors themselves. Some seek financial gain, others pursue political or social objectives, and still others aim for strategic advantage on the global stage. The methods used to achieve these goals are equally diverse, reflecting the different approaches of each actor.
Incentives for Participating in the “War of Worms”
The incentives for participating in this “War of Worms” are deeply rooted in the motivations of the actors involved. Hacktivists may gain recognition and influence within their online communities, while cybercriminals seek financial rewards. State-sponsored actors, on the other hand, might leverage these tools for intelligence gathering or disrupting critical infrastructure of adversaries. The perceived value of success, be it political, financial, or strategic, is a primary driver.
Motivations of Various Actors
| Actor | Motivation | Methods |
|---|---|---|
| Hacktivists | Achieving a political or social agenda through disruption and data breaches. This might include exposing corruption, protesting government policies, or promoting a particular ideology. | Disrupting services, defacing websites, or releasing sensitive data to draw attention to their cause. |
| Cybercriminals | Financial gain through ransomware attacks, phishing scams, and other fraudulent activities. The goal is to extract money from individuals or organizations through deception. | Deploying ransomware to encrypt data and demand payment for its release, using phishing emails to steal login credentials, or conducting credit card fraud. |
| State-sponsored actors | Espionage, sabotage, or disrupting critical infrastructure of adversary states. These actors often have a broader geopolitical agenda. | Stealing classified information, disrupting power grids or communication networks, or manipulating election outcomes. |
Impact and Consequences
The “War of Worms” has the potential to unleash catastrophic consequences across various sectors, from the economy to personal lives. The interconnected nature of modern digital infrastructure makes even seemingly contained attacks capable of rippling outwards, causing widespread damage and disruption. The vulnerabilities exposed in these conflicts necessitate careful consideration of preventative measures and robust response strategies.The consequences of this digital conflict extend beyond immediate technical failures.
The economic, social, and political ramifications are substantial and long-lasting, demanding a comprehensive understanding of the potential damage. From individual financial losses to national security breaches, the impact of a sustained worm war can be devastating.
Virus writers are constantly battling in the war of worms, creating ever more sophisticated ways to infiltrate systems. This constant arms race is fascinating, but the recent push for PC-free computing, as seen at CES with Panasonic’s innovative approach panasonic pushes pc free computing at ces , might actually change the game. Ultimately, the virus writers’ efforts might be rendered less effective in a world without the traditional PC target.
It’s a compelling thought as the battle continues.
Economic Impact
The economic repercussions of a prolonged “War of Worms” could be severe. Businesses reliant on online transactions and data storage would suffer significant financial losses due to downtime, data breaches, and lost productivity. Supply chains could be disrupted, leading to shortages and price increases. Furthermore, the cost of repairing damaged systems and implementing security upgrades would add to the financial burden.
Social Impact
The social implications are equally profound. The erosion of trust in online systems could lead to a decline in online activity, affecting e-commerce, social media interactions, and remote work. The potential for misinformation and the spread of malicious content could exacerbate social divisions and distrust. Individuals could experience significant personal losses, from identity theft to the loss of important data.
Political Impact
The political landscape could also be dramatically altered. Governments might be forced to implement stricter regulations to mitigate the risks, potentially impacting individual liberties and economic freedoms. The potential for political destabilization or cyber warfare escalations cannot be ignored. International cooperation to develop effective defense mechanisms becomes crucial.
Impact on Individuals
Individuals face direct consequences in a “War of Worms.” Financial losses from online fraud, identity theft, and the inability to access essential services like banking and healthcare are immediate concerns. The emotional distress caused by data breaches and the loss of personal information cannot be underestimated.
Impact on Organizations
Organizations of all sizes would be impacted by the “War of Worms.” Businesses could experience significant losses from operational downtime, data breaches, and reputational damage. The cost of implementing security measures and recovering from attacks would be a significant financial burden. Maintaining customer trust becomes paramount.
Impact on Nations
Nations face potentially devastating consequences from a prolonged “War of Worms.” National security systems, critical infrastructure, and government operations could be severely compromised. The loss of trust in digital systems could impact international relations and economic cooperation. The ability to maintain national security and stability is paramount.
Comparison of Virus/Worm Attacks
| Attack | Severity (Low/Medium/High) | Impact Description |
|---|---|---|
| Worm X | High | Massive network disruption, financial losses, potential for widespread outages |
| Virus Y | Medium | Data breaches, system slowdowns, limited network disruption |
| Trojan Z | High | System compromise, remote access for malicious actors, potential for espionage or sabotage |
Strategies and Countermeasures
The battle between virus writers and security professionals is a constant arms race. Virus writers constantly develop new techniques to bypass defenses, while security researchers and developers work tirelessly to create countermeasures. Understanding these strategies and countermeasures is crucial to protecting systems and data in the ever-evolving digital landscape.
Virus Writer Strategies
Virus writers employ a variety of sophisticated techniques to spread their malicious code. These strategies often exploit vulnerabilities in software, operating systems, and human behavior. A common strategy is the use of social engineering tactics, tricking users into downloading infected files or clicking malicious links. Another prevalent approach involves polymorphic code, which changes its structure to evade detection by antivirus software.
Furthermore, viruses are frequently designed to spread through various channels, including email attachments, malicious websites, and compromised networks.
Virus writers are constantly battling in a digital war of worms, creating new threats daily. This relentless activity, however, is somewhat overshadowed by the recent news of Apple tweaking iTunes for Windows teams with AOL, a fascinating development in the tech world. While the details of this collaboration remain unclear, it likely represents a significant shift in how users interact with digital media, and potentially opens new avenues for attack by those same virus writers who continue their relentless work in the war of worms.
Countermeasures and Defense Mechanisms
Countermeasures against virus attacks are multifaceted and involve a combination of technical and human-centric strategies. Strong security protocols, including regular software updates, are essential. These updates often patch known vulnerabilities that virus writers might exploit. Users also play a critical role in preventing infections by practicing safe computing habits, such as avoiding suspicious emails and downloading files only from trusted sources.
The principle of least privilege, limiting access to only necessary resources, can significantly reduce the impact of a potential compromise.
Role of Security Software and Protocols
Security software and protocols are vital components of a comprehensive defense strategy. Antivirus software, firewalls, and intrusion detection systems actively monitor network traffic and system activity for suspicious patterns, alerting administrators to potential threats. The effective implementation of security protocols, such as strong passwords and multi-factor authentication, can also dramatically reduce the risk of successful attacks.
Virus writers are constantly battling in a digital war of worms, creating ever-evolving threats. Fortunately, companies like IBM are stepping up to help businesses stay safe. IBM recently unveiled content management software for small businesses, helping them manage their online presence and security , which is a welcome relief in the face of these persistent digital threats.
This sophisticated software can potentially bolster defenses against malicious code and improve overall cybersecurity for smaller operations, effectively mitigating some of the damage from the ongoing battle of virus writers.
Security Measures Overview
The table below Artikels various security measures and their effectiveness in combating virus attacks.
| Security Measure | Description | Effectiveness |
|---|---|---|
| Firewall | A firewall acts as a gatekeeper for network traffic, blocking unauthorized access from the outside world. It scrutinizes incoming and outgoing data packets, preventing malicious traffic from entering the network and outgoing data from being compromised. | High. Firewalls are effective at preventing unauthorized access, but they are not foolproof. Sophisticated attackers can bypass firewalls using various techniques. |
| Antivirus Software | Antivirus software is designed to detect and remove known viruses and malware from a system. It utilizes signature-based and heuristic analysis to identify malicious code. Signature-based analysis compares the code to known virus signatures, while heuristic analysis looks for suspicious code patterns. | Medium. Antivirus software’s effectiveness depends on its update frequency and the sophistication of the virus. Modern viruses often employ techniques to evade detection by antivirus software. |
| Intrusion Detection System (IDS) | An IDS monitors network traffic for malicious activity and alerts administrators to potential threats. It can identify unusual patterns or known attack signatures. | High. IDSs can detect many types of attacks and provide valuable information to administrators. |
| Regular Software Updates | Regular software updates are crucial for patching security vulnerabilities that virus writers can exploit. These updates often address known exploits and improve overall system security. | High. Regular updates are essential for maintaining a strong security posture. |
Future Trends and Implications: Virus Writers Battle In War Of Worms
The digital conflict known as the War of Worms is rapidly evolving, driven by the relentless innovation in both defensive and offensive technologies. The future of this conflict hinges on the ability of individuals and organizations to anticipate and adapt to emerging threats and vulnerabilities. This necessitates a proactive approach to cybersecurity, embracing predictive modeling and advanced threat intelligence.The landscape is set to become even more complex, with new actors, motivations, and strategies emerging.
The implications extend far beyond the realm of information security, potentially impacting critical infrastructure, economic stability, and societal trust. This section explores the evolving trends, the pivotal role of AI, and the potential impact of quantum computing.
Potential Future Developments in Digital Conflict
The future of the War of Worms will likely see an increase in the sophistication and customization of malware. Cyberattacks will likely become more targeted and tailored to specific vulnerabilities in individual systems or entire networks. This trend emphasizes the need for adaptive security measures capable of responding to highly specialized attacks.
Role of Artificial Intelligence in Malware Evolution
AI is poised to play a transformative role in the evolution of malware. Advanced algorithms can be used to create more sophisticated and effective viruses. Furthermore, AI can analyze vast amounts of data to identify patterns and predict future attack vectors. This predictive capability allows for a proactive defense against emerging threats. For example, AI-driven malware can adapt to changes in security measures, making them increasingly difficult to detect and mitigate.
Potential Scenarios in the Future
Numerous scenarios are possible in the future of this conflict. One scenario involves AI-powered viruses targeting specific vulnerabilities in autonomous systems. These systems are crucial in critical infrastructure, such as power grids, transportation networks, and financial institutions. A successful attack could disrupt these systems, leading to widespread societal consequences. Another scenario involves the use of AI-powered social engineering tools to target individuals and manipulate them into carrying out malicious actions.
These actions could include spreading misinformation, stealing sensitive information, or launching attacks against other systems.
Impact of Emerging Technologies on the Conflict
Emerging technologies like quantum computing could potentially revolutionize both the offensive and defensive strategies in this conflict. Quantum computing’s ability to perform complex calculations could allow for the development of more advanced encryption methods. Conversely, it could also enable the development of more powerful decryption techniques, potentially rendering current security measures obsolete. This necessitates a constant adaptation in both the design and implementation of cybersecurity strategies.
Hypothetical Scenarios Involving AI-Powered Viruses
Imagine a scenario where AI-powered viruses target specific vulnerabilities in autonomous systems, disrupting critical infrastructure. A sophisticated virus, trained on vast datasets of system behaviors and vulnerabilities, could identify and exploit weaknesses in autonomous vehicles, causing collisions or malfunctions. Similarly, such a virus could disrupt power grids, leading to widespread blackouts. These attacks would require a sophisticated and adaptive defense, relying on advanced anomaly detection and real-time threat intelligence.
Another scenario could involve AI-powered viruses targeting financial systems, manipulating market trends and causing significant financial losses. These examples highlight the need for a proactive and preventative approach to cybersecurity in the face of rapidly evolving threats.
Ending Remarks
The “war of worms” is a multifaceted digital struggle with serious implications for individuals, organizations, and nations. From the development and deployment of malware to the critical importance of security measures, this discussion delves into the intricacies of this ongoing conflict. The future of this battle, shaped by evolving technologies like AI and quantum computing, promises to present new and unprecedented challenges and opportunities for both attackers and defenders.