IT Security and Software Development A Deep Dive
IT security and software development are intrinsically linked. This blog post explores the crucial relationship between securing software and building robust applications. From foundational principles to emerging trends, we’ll delve into the importance of integrating security throughout the entire software development lifecycle (SDLC). We’ll cover common vulnerabilities, security threats, and practical tools and techniques to build more secure software.
Understanding the interplay between security and software development is vital in today’s digital landscape. We’ll examine various methodologies, from secure coding practices to advanced security testing. We’ll also analyze the impact of compliance standards, emerging technologies like AI and cloud security, and how they shape the future of secure software development.
Introduction to IT Security and Software Development

IT security and software development are intertwined disciplines, each crucial for creating and maintaining secure digital systems. Understanding their relationship is vital in today’s interconnected world, where software applications power everything from critical infrastructure to personal devices. A robust understanding of both domains is essential for mitigating risks and building resilient systems.Software development focuses on building applications, while IT security focuses on protecting them.
The fundamental relationship between these two fields lies in the need for security to be integrated into every stage of the software development process. Failing to do so can lead to significant vulnerabilities and breaches.
Defining IT Security and Software Development
IT security encompasses the practices and technologies designed to protect information systems and data from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes measures like access controls, encryption, intrusion detection systems, and vulnerability management. Software development, on the other hand, is the process of designing, coding, testing, and deploying software applications. This encompasses various methodologies and approaches, from traditional waterfall to agile methodologies.
The Fundamental Relationship Between IT Security and Software Development
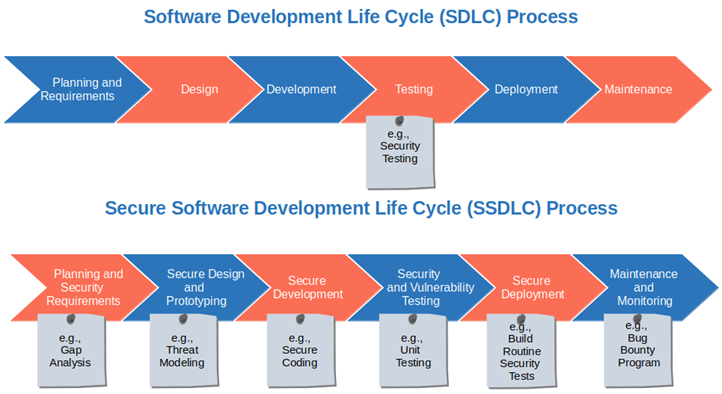
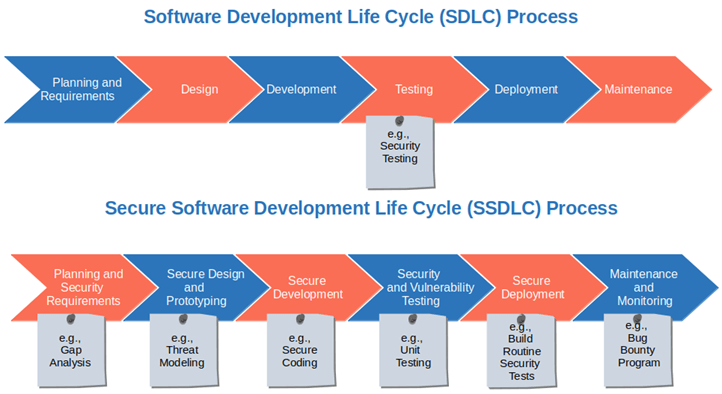
Security is not an afterthought; it’s an integral part of the software development lifecycle (SDLC). Security considerations should be addressed throughout the entire process, from initial design to final deployment. This proactive approach minimizes the risk of vulnerabilities emerging later. This means incorporating security best practices into every phase, from design and coding to testing and deployment.
Importance of Integrating Security Practices Throughout the SDLC, It security and software development
Integrating security throughout the SDLC is crucial for building secure applications. Security should be baked into the application’s architecture, design, and code from the very beginning. This reduces the likelihood of security flaws emerging later in the process, making it more cost-effective and efficient to address them early.
Common Security Vulnerabilities in Software Applications
Several common vulnerabilities can compromise software applications. These include injection flaws (SQL injection, command injection), cross-site scripting (XSS), cross-site request forgery (CSRF), insecure direct object references, and insecure design flaws. Understanding these vulnerabilities is critical for developers to write secure code and for security teams to effectively test and secure applications.
Comparison of Software Development Methodologies and Security Implications
| Methodology | Security Implications |
|---|---|
| Waterfall | Security considerations are often addressed late in the development cycle, potentially leading to more complex fixes and higher costs. The sequential nature can lead to vulnerabilities being overlooked if not explicitly addressed at each stage. |
| Agile | Agile methodologies often prioritize rapid development and iterative feedback, which can be beneficial for incorporating security early. However, security practices need to be integrated seamlessly into the sprints and iterations. Security testing needs to be part of the sprint cycles. |
| DevOps | DevOps emphasizes automation and collaboration between development and operations teams, which can enhance security through continuous monitoring and integration of security checks into the pipeline. Automated security scanning and testing is key. |
This table highlights how different methodologies can affect security practices. Choosing the right methodology depends on the project’s specific needs and constraints.
Security Considerations in Software Development
Building secure software is paramount in today’s interconnected world. Vulnerabilities in applications can lead to significant financial losses, reputational damage, and even legal repercussions. Understanding the various threats and implementing robust security practices throughout the development lifecycle is crucial for building trust and protecting users.Security flaws in software are often exploited by malicious actors. These vulnerabilities can range from simple coding errors to sophisticated attacks targeting specific architectural weaknesses.
Preventing these vulnerabilities is more cost-effective and less disruptive than reacting to them after deployment. Therefore, proactive security measures during the design, development, and testing phases are vital for building robust and reliable applications.
Common Security Threats
Security threats targeting software applications are diverse and evolving. These threats exploit weaknesses in the design, implementation, or deployment of the software. Some prevalent threats include:
- Injection attacks (SQL injection, command injection): Exploiting vulnerabilities where untrusted data is inserted into a query or command.
- Cross-site scripting (XSS): Injecting malicious scripts into web pages viewed by other users.
- Cross-site request forgery (CSRF): Forcing a user to perform unwanted actions on a web application they are authenticated to.
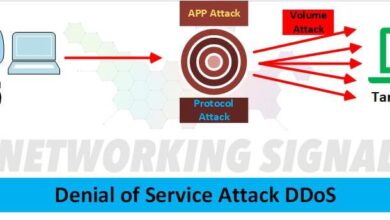
- Denial-of-service (DoS) attacks: Overwhelming a system with traffic, rendering it unavailable to legitimate users.
- Authentication and authorization flaws: Weak or improperly implemented authentication and authorization mechanisms, allowing unauthorized access to sensitive data.
- Malware and viruses: Malicious software that can infect and damage systems.
Secure Coding Practices
Secure coding practices are essential to mitigate security risks at the source code level. Adhering to these practices throughout the development process is vital. They involve adopting a security-conscious approach from the initial design phase to the final deployment.
- Input validation: Carefully validating all inputs to prevent injection attacks and other vulnerabilities.
- Output encoding: Encoding output data to prevent XSS attacks and ensure data integrity.
- Authentication and authorization: Implementing robust authentication and authorization mechanisms to control access to sensitive resources.
- Least privilege principle: Granting users only the necessary permissions to perform their tasks.
- Secure session management: Implementing secure session management to prevent session hijacking.
Secure Coding Techniques and Best Practices
Effective secure coding techniques encompass a variety of strategies. Implementing these strategies early in the development process is essential.
- Using secure libraries and frameworks: Leveraging validated and secure libraries and frameworks can help mitigate vulnerabilities.
- Following coding standards and guidelines: Adhering to established coding standards and guidelines helps ensure consistent and secure code quality.
- Code reviews: Performing thorough code reviews to identify potential vulnerabilities.
- Security testing: Integrating security testing throughout the development process.
Security Testing Methodologies
Security testing methodologies provide structured approaches to evaluate software security. These methodologies encompass various techniques to identify vulnerabilities.
- Penetration testing: Simulating real-world attacks to identify vulnerabilities.
- Vulnerability scanning: Identifying known vulnerabilities in software.
- Static application security testing (SAST): Analyzing source code to identify vulnerabilities.
- Dynamic application security testing (DAST): Analyzing running applications to identify vulnerabilities.
Integrating Security into Design
Security should be integrated into the design phase of software development. This proactive approach reduces the likelihood of introducing vulnerabilities later.
- Security requirements gathering: Defining security requirements early in the project.
- Threat modeling: Identifying potential threats and vulnerabilities.
- Security design patterns: Utilizing established security design patterns to enhance security.
Secure Software Architecture
A secure software architecture plays a critical role in mitigating vulnerabilities. This approach establishes a framework that considers security from the initial design stage.
- Separation of concerns: Isolating different components to limit the impact of vulnerabilities.
- Principle of least privilege: Limiting access to resources.
- Modular design: Designing the system in modules to isolate functionalities.
Security Attacks and Prevention Mechanisms
| Security Attack Type | Description | Prevention Mechanisms |
|---|---|---|
| SQL Injection | Injecting malicious SQL code into database queries. | Input validation, parameterized queries, prepared statements. |
| Cross-Site Scripting (XSS) | Injecting malicious scripts into web pages. | Output encoding, input validation, Content Security Policy (CSP). |
| Cross-Site Request Forgery (CSRF) | Forcing a user to perform unwanted actions on a website. | CSRF tokens, double-submit cookie, HTTP methods. |
Software Development Security Tools and Technologies
Securing software is no longer an afterthought but a crucial aspect of the development lifecycle. Integrating security tools and technologies from the initial design phase fosters a more robust and resilient application. This proactive approach significantly reduces vulnerabilities and improves overall application quality and user trust.Modern software development practices emphasize building security into the codebase, from design to deployment.
This proactive approach significantly minimizes vulnerabilities that attackers could exploit. The selection and implementation of appropriate security testing tools are essential for effective vulnerability identification and remediation.
Static Application Security Testing (SAST) Tools
SAST tools analyze the source code of an application to identify potential security flaws. They are designed to find vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure direct object references before the application is deployed. This early detection enables developers to fix these issues during the development phase, reducing the cost and time associated with patching vulnerabilities later.Implementing SAST tools involves integrating them into the development pipeline.
Tools often come with plugins for popular IDEs, allowing developers to integrate security checks into their daily workflow. Results are displayed within the IDE or as separate reports, highlighting the vulnerabilities found in the code. Thorough understanding of the tool’s output and how to address the identified issues are critical for successful implementation.
Dynamic Application Security Testing (DAST) Tools
DAST tools assess the application’s security posture by simulating real-world attacks. They test the application’s behavior during runtime, probing for vulnerabilities like cross-site request forgery (CSRF), broken authentication, and insecure API endpoints. DAST tools simulate various user interactions, mimicking the actions of malicious actors to identify vulnerabilities that might not be detected by SAST.Using DAST tools involves setting up a testing environment that mimics the production environment as closely as possible.
Configurations should reflect the application’s actual setup to ensure realistic vulnerability detection. Thorough documentation and comprehensive analysis of the testing results are essential for effective remediation of discovered vulnerabilities.
Interactive Application Security Testing (IAST) Tools
IAST tools operate within the application’s runtime environment, monitoring the execution flow and identifying vulnerabilities as they are exploited. This dynamic approach provides valuable insights into the application’s behavior under attack. IAST tools work in tandem with the application’s execution, allowing for immediate feedback and identification of vulnerabilities. This real-time feedback allows for rapid identification and resolution of security issues.
It security and software development are intrinsically linked, especially when considering new platforms. For example, the upcoming Napster beta, ready to rock n roll, here’s the beta announcement , presents exciting challenges and opportunities for developers to implement robust security measures. Strong encryption and secure authentication protocols are crucial for protecting user data, regardless of the platform’s underlying technology.
Effective security protocols are essential to the success of any new software launch.
Examples include tools that hook into the application’s runtime environment to observe code execution, identifying potentially risky behavior.
Security Information and Event Management (SIEM) Systems
SIEM systems provide a centralized platform for collecting, analyzing, and correlating security events from various sources within the network. These systems help detect and respond to security incidents, providing a comprehensive view of the security posture of the organization. They are crucial for incident response, enabling swift action to contain and mitigate security breaches. A SIEM system often integrates with other security tools to provide a holistic view of security events.
Benefits and Drawbacks of Security Testing Tools
| Tool Type | Benefits | Drawbacks |
|---|---|---|
| SAST | Early vulnerability detection, reduced development costs, improved code quality | False positives, potential for missing complex vulnerabilities, limited real-world context |
| DAST | Real-world attack simulation, identification of vulnerabilities in runtime environment, effective for detecting vulnerabilities in deployed applications | Can be time-consuming, requires a realistic test environment, potential for disruption of production systems |
| IAST | Real-time vulnerability detection, accurate identification of issues during runtime, reduced false positives compared to DAST | Can be more complex to implement, may require specific configurations, potential for impact on application performance |
| SIEM | Centralized security event management, comprehensive security view, improved incident response | Complexity of implementation, high cost of installation and maintenance, potential for data overload |
Security Standards and Compliance: It Security And Software Development
Adherence to security standards and compliance with regulations is crucial for building trustworthy and reliable software. Robust security practices are not just a “nice-to-have” but a necessity in today’s interconnected world. Failure to meet these standards can lead to significant financial losses, reputational damage, and legal repercussions. This section delves into the importance of these standards, outlining key industry benchmarks and regulations.Security standards provide a framework for developing secure software, reducing vulnerabilities and improving overall system resilience.
These standards are based on extensive research and best practices, offering proven methods for mitigating risks and preventing breaches. By adopting and implementing these standards, organizations can significantly reduce the likelihood of security incidents and ensure the confidentiality, integrity, and availability of their systems and data.
Significance of Adherence to Security Standards
Following security standards offers numerous benefits, including reduced vulnerabilities, enhanced system resilience, and increased trust from users and stakeholders. A robust security posture demonstrates a commitment to protecting sensitive information and assets. Organizations that prioritize security standards are often perceived as more trustworthy and reliable, fostering customer loyalty and confidence. Consistently meeting these standards can help mitigate risks and reduce the financial impact of security breaches.
It security and software development are deeply intertwined, especially when considering the growing need for robust systems. Apple’s recent preview of Xgrid clustering technology, which promises enhanced performance and scalability , offers intriguing possibilities for future applications. This advancement could ultimately lead to more secure and reliable software, improving data protection in various sectors.
Relevant Industry Standards for Software Security
Several industry standards play a crucial role in defining secure software development practices. The Open Web Application Security Project (OWASP) is a widely recognized organization that publishes valuable resources and guidelines. The OWASP Top 10, for instance, highlights the most critical web application security risks, providing developers with actionable recommendations for mitigation. Another key standard is the National Institute of Standards and Technology (NIST) Cybersecurity Framework, which provides a comprehensive approach to managing cybersecurity risks across various sectors.
These standards are essential for developers, as they Artikel best practices and address potential vulnerabilities.
Importance of Compliance with Regulations
Compliance with regulations like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) is critical for organizations handling sensitive data. These regulations define specific requirements for data protection and privacy, and non-compliance can result in substantial penalties. Organizations must understand and implement the necessary controls to comply with these regulations, safeguarding the privacy and security of user data.
Failure to adhere to regulations can lead to legal issues and financial penalties.
Examples of Security Audits and Assessments
Security audits and assessments are crucial for identifying and addressing security weaknesses. A penetration test, for example, simulates real-world attacks to assess the security posture of a system. Vulnerability assessments scan for known vulnerabilities in software and systems, helping to prioritize remediation efforts. These assessments help identify potential security gaps and provide actionable steps for improvement.
Comparison of Different Compliance Frameworks and Their Security Implications
Different compliance frameworks, such as ISO 27001, SOC 2, and PCI DSS, offer varying levels of security and compliance requirements. The security implications differ based on the specific framework and the nature of the organization’s data and operations. Understanding the specific requirements of each framework allows organizations to tailor their security policies and practices accordingly.
Creating a Security Policy for a Software Development Team
A comprehensive security policy for a software development team should Artikel the organization’s security standards and procedures. This policy should define roles and responsibilities, processes for handling vulnerabilities, and guidelines for secure coding practices. It should also include provisions for incident response and continuous improvement of security practices. Clear communication and training on the security policy are essential for its effective implementation.
Security in Specific Software Development Areas
Building secure software is not just about adding security features at the end of the development cycle. It’s a crucial consideration throughout the entire process, from design to deployment. This involves understanding the specific vulnerabilities in different software types and implementing appropriate safeguards. This section dives into the security concerns of web applications, databases, mobile apps, and APIs.
It security and software development are intertwined in today’s digital landscape. Modern music production often relies on complex software, raising interesting questions about data protection and security. For instance, in the interview with composer and singer Paul Korda, technology meets music , we see how tech tools impact creative endeavors. This highlights the crucial role of robust security measures in protecting both digital assets and the creative process itself.
Ultimately, understanding these connections is key to future-proofing both the music industry and the software development world.
Web Application Security Concerns
Web applications are frequently targeted by attackers due to their public accessibility. Security flaws in these applications can lead to data breaches, unauthorized access, and denial-of-service attacks. Understanding the potential vulnerabilities and implementing appropriate mitigation strategies is critical.
- Cross-Site Scripting (XSS): XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. This can steal user data, redirect users to malicious sites, or deface web pages.
- Cross-Site Request Forgery (CSRF): CSRF attacks trick users into performing unwanted actions on a web application. Attackers can manipulate requests to transfer funds, change account settings, or post malicious content without the user’s knowledge or consent.
- SQL Injection: SQL injection attacks exploit vulnerabilities in database interactions to execute malicious SQL queries. This can lead to data breaches, data manipulation, or complete database compromise.
- Session Management Issues: Weak session management practices allow attackers to hijack user sessions, gaining unauthorized access to protected resources.
- Insecure Direct Object References: This vulnerability allows attackers to access resources or functionalities they are not authorized to use.
Secure Database Development Practices
Databases store sensitive information and are crucial to the functionality of many applications. Robust security measures are essential to protect this data.
- Principle of Least Privilege: Grant users only the necessary permissions to access and modify data. This minimizes the impact of a potential security breach.
- Input Validation: Validate all user inputs to prevent SQL injection and other similar attacks.
- Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities.
- Secure Configuration Management: Use strong, regularly updated passwords for database accounts and ensure that the database server is properly configured.
Secure Mobile Application Development Practices
Mobile applications are increasingly used to access sensitive data, making secure development practices crucial.
- Secure Data Storage: Use encryption to protect sensitive data stored on the device.
- Secure Network Communication: Employ secure protocols (e.g., HTTPS) for communication between the application and the server.
- Code Reviews: Thoroughly review the application code to identify potential vulnerabilities.
- Regular Updates: Maintain the application with regular updates to address security vulnerabilities.
- Input Validation: Validate all user inputs to prevent vulnerabilities like SQL injection and XSS.
Secure API Development
APIs are essential for connecting different applications. Secure API development is critical to protect the integrity and confidentiality of data exchanged between systems.
- Authentication and Authorization: Implement robust authentication mechanisms (e.g., OAuth 2.0) to verify the identity of users and authorize their access to specific resources.
- Rate Limiting: Implement rate limiting to prevent abuse and denial-of-service attacks.
- Input Validation: Validate all inputs to prevent injection attacks.
- Output Encoding: Encode all outputs to prevent XSS attacks.
- Secure API Design: Design APIs with security in mind from the beginning. Avoid unnecessary functionalities.
Top 10 Web Application Security Vulnerabilities
| Rank | Vulnerability | Description |
|---|---|---|
| 1 | Injection | Allows attackers to inject malicious code into the application. |
| 2 | Broken Authentication | Weak or broken authentication mechanisms allow unauthorized access. |
| 3 | Sensitive Data Exposure | Failure to protect sensitive data from unauthorized access. |
| 4 | XML External Entities (XXE) | Vulnerability in XML parsers allowing attackers to access unauthorized data. |
| 5 | Broken Access Control | Improper access controls allow unauthorized access to resources. |
| 6 | Security Misconfiguration | Improperly configured security settings allow vulnerabilities. |
| 7 | Cross-Site Scripting (XSS) | Allows attackers to inject malicious scripts into web pages. |
| 8 | Insecure Deserialization | Vulnerabilities in deserialization can allow attackers to execute arbitrary code. |
| 9 | Using Components with Known Vulnerabilities | Using outdated or vulnerable components can expose the application to attacks. |
| 10 | Insufficient Logging & Monitoring | Lack of logging and monitoring makes it difficult to detect and respond to security incidents. |
Future Trends in IT Security and Software Development
The landscape of IT security and software development is constantly evolving, driven by technological advancements and emerging threats. This evolution necessitates a proactive and adaptable approach to ensure systems remain secure and resilient. The future will demand a deep understanding of emerging trends and a willingness to embrace innovative security solutions.
Emerging Trends in IT Security
The cybersecurity threat landscape is rapidly shifting, with attackers constantly developing new methods to exploit vulnerabilities. Key emerging trends include the increasing sophistication of cyberattacks, the rise of ransomware and other forms of malicious software, the expanding attack surface due to the proliferation of connected devices, and the growing importance of supply chain security. This requires organizations to continuously adapt their security strategies and invest in advanced threat detection and response capabilities.
Impact of Artificial Intelligence and Machine Learning on Software Security
AI and machine learning are revolutionizing software development and security. AI-powered tools can automate tasks like vulnerability detection, code analysis, and threat intelligence gathering. This automation significantly increases efficiency and reduces the time it takes to identify and remediate security issues. Machine learning algorithms can also be trained to detect anomalies and patterns indicative of malicious activity, improving the accuracy and speed of threat detection.
However, the integration of AI and machine learning in security also presents new challenges, such as ensuring the trustworthiness and explainability of AI-driven security systems.
Role of Cloud Security in Software Development
Cloud computing is rapidly transforming how software is developed and deployed. Cloud security plays a crucial role in ensuring the confidentiality, integrity, and availability of data and applications hosted in the cloud. Developers need to be mindful of security considerations from the outset, implementing secure coding practices and utilizing cloud-native security tools. Organizations must establish robust access controls, data encryption, and compliance frameworks to protect sensitive information stored and processed in the cloud.
The increasing adoption of cloud-based services demands a shift in mindset, focusing on building security into the very fabric of software development.
Importance of DevSecOps in Integrating Security
DevSecOps represents a fundamental shift in how security is addressed in the software development lifecycle. It emphasizes integrating security practices into every stage of development, from planning and design to testing and deployment. This approach fosters a culture of shared responsibility for security across development, operations, and security teams. By automating security testing and integrating security tools into the CI/CD pipeline, organizations can identify and address vulnerabilities early in the process, leading to more secure and reliable software.
This proactive approach helps prevent costly security breaches and minimizes the risk of vulnerabilities entering production environments.
Future of Cybersecurity
The future of cybersecurity hinges on proactive measures and a focus on prevention. This includes investing in advanced threat detection and response systems, developing more resilient software, and promoting cybersecurity awareness among all stakeholders. Continuous learning and adaptation are essential for staying ahead of evolving threats. Collaboration between organizations and security researchers is critical to sharing knowledge and best practices, allowing for a collective approach to bolstering overall security posture.
Examples of Emerging Security Tools and Technologies
Several innovative tools and technologies are emerging to address future security challenges. These include AI-powered vulnerability scanners, machine learning-based intrusion detection systems, and advanced encryption techniques. Furthermore, the development of zero-trust security architectures is gaining traction, requiring continuous authentication and authorization for all users and devices. These tools are crucial for maintaining security in the face of increasing sophistication in cyberattacks.
Final Thoughts
In conclusion, IT security and software development are inextricably intertwined. Building secure software requires a holistic approach, integrating security considerations throughout the entire development process. This includes understanding vulnerabilities, employing secure coding practices, utilizing testing tools, adhering to industry standards, and adapting to future trends. By prioritizing security from the start, developers can create more resilient and trustworthy applications.