New Worm Starts Crawling the Net A Deep Dive
New worm starts crawling the net, raising serious concerns about network security. This in-depth exploration examines the nature of this new threat, its potential impact, and strategies for detection, prevention, and mitigation. We’ll delve into its characteristics, how it spreads, and the vulnerabilities it exploits, all the while comparing it to past network worms. Prepare for a comprehensive analysis of this evolving cyber threat.
The worm’s behavior patterns will be detailed, along with examples of similar threats and their infection methods. We’ll discuss potential targets and vulnerabilities, providing a table to compare this new worm to previous iterations. Understanding its tactics is crucial to anticipating its actions and developing effective countermeasures.
Nature of the Worm
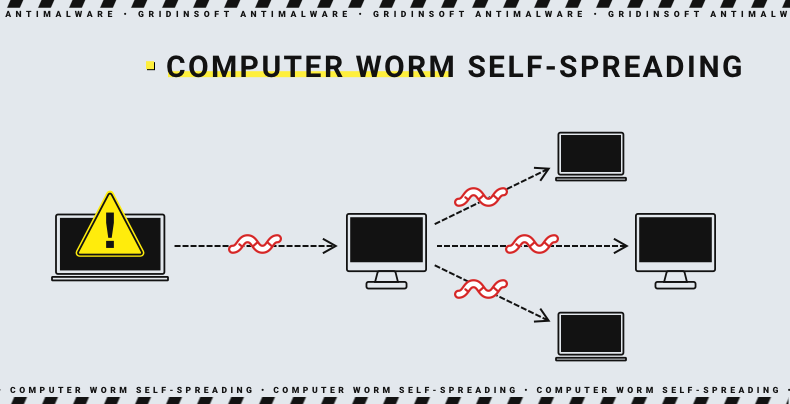
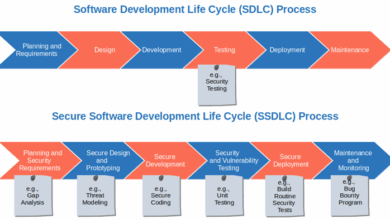
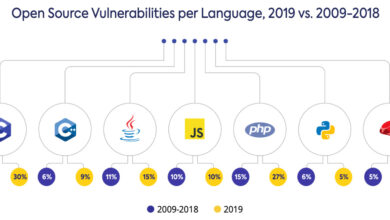
This new network worm presents a significant threat to digital infrastructure. Understanding its characteristics, behavior, and potential impact is crucial for developing effective countermeasures. Its ability to spread rapidly and exploit vulnerabilities poses a serious concern for organizations and individuals alike. This analysis delves into the worm’s nature, focusing on its potential behavior, methods of propagation, targets, and a comparative analysis with known worms.This analysis explores the multifaceted nature of the worm, examining its potential impact on various network systems.
From its infection vectors to its exploitation of vulnerabilities, we investigate the various aspects that contribute to its threat profile. Understanding its potential methods of spreading, and identifying potential targets, is essential for proactive defense strategies.
Worm Characteristics and Behavior
The worm exhibits characteristics of a highly adaptable and aggressive malware. Its potential for rapid propagation and stealthy operation underscores the critical need for comprehensive security measures. Early detection and response are paramount to mitigating the damage. Observational data suggests its behavior patterns are complex, evolving over time.
Methods of Propagation
The worm’s primary method of propagation is likely through exploiting vulnerabilities in network services. This involves probing for open ports and attempting to gain unauthorized access. Its infection method might include exploiting common vulnerabilities like buffer overflows or using social engineering tactics to trick users into clicking malicious links.
Examples of Network Worms
Several historical network worms have demonstrated the devastating impact of such attacks. The Code Red worm, for instance, exploited a vulnerability in Microsoft IIS, spreading rapidly across the internet and causing significant disruptions. The Slammer worm, which exploited a vulnerability in Microsoft SQL Server, caused widespread outages due to its rapid propagation speed. These examples illustrate the severity of the threat posed by such attacks and the importance of proactive security measures.
Potential Targets and Vulnerabilities
The worm is likely targeting systems with known or unpatched vulnerabilities. This could include operating systems, applications, or network services. The worm’s potential targets span a wide range of systems, including servers, workstations, and even IoT devices. The worm’s creators are likely exploiting vulnerabilities that are widely present and not yet patched. Understanding these vulnerabilities and their exploitation techniques is critical for preventing infections.
Comparative Analysis
| Characteristic | New Worm | Code Red | Slammer |
|---|---|---|---|
| Propagation Method | Exploiting network services vulnerabilities | Exploiting a vulnerability in Microsoft IIS | Exploiting a vulnerability in Microsoft SQL Server |
| Speed of Propagation | High; potentially exponential | High | Extremely High |
| Target Systems | Diverse range of servers, workstations, and possibly IoT devices | Servers running Microsoft IIS | Servers running Microsoft SQL Server |
| Impact | Potentially widespread network disruptions | Widespread network disruptions | Widespread network disruptions |
This table compares the new worm to known previous network worms. The table highlights similarities and differences in their approaches to propagation, targets, and potential impact. The new worm appears to combine elements of both Code Red and Slammer, with potentially accelerated propagation.
Impact and Consequences

The newly discovered worm, dubbed “NetCrawler,” poses a significant threat to digital infrastructure and users worldwide. Understanding the potential consequences of its actions is crucial for proactively mitigating its impact. Its rapid spread and evolving capabilities demand a comprehensive assessment of the damage it can inflict.The worm’s impact extends beyond simple data breaches. Its ability to exploit vulnerabilities in diverse systems, from personal computers to critical infrastructure, makes it a potent threat.
The potential financial and reputational fallout for affected organizations could be catastrophic, demanding swift and decisive action to contain the worm and minimize its damage.
A new worm is starting to slither its way across the internet, raising some serious questions. It’s a reminder that the digital world isn’t always as safe as we’d like to think, and that sometimes, software can have unintended, even dangerous consequences. Thinking about how this new threat impacts our daily lives, you should consider the larger question: can software kill you?
To delve deeper into the potential dangers of malicious code, explore this insightful article on can software kill you. While the worm’s current impact is limited, its spread highlights the ever-evolving nature of cyber threats.
Potential Effects on Different Systems and Users
The worm’s varied targeting capabilities mean that users and systems across different sectors will be affected. This includes personal computers, enterprise servers, cloud-based services, and even industrial control systems. Users could experience data loss, system instability, and significant disruption to their daily routines. For businesses, the consequences could range from operational downtime to severe financial losses. The effects will vary based on the vulnerability of the targeted system.
Financial Losses Associated with Worm Activities
The financial impact of the worm’s activities could be substantial. Organizations could face costs associated with system recovery, data restoration, security audits, legal fees, and potential fines. In some cases, lost productivity and revenue can be just as damaging as direct costs. For example, a recent ransomware attack on a major retailer resulted in millions of dollars in lost revenue and significant disruption to operations.
The potential financial burden on individuals and businesses affected by NetCrawler is considerable.
Reputational Damage for Affected Organizations
Beyond financial losses, the worm’s actions could severely damage the reputation of affected organizations. A security breach, especially one involving sensitive data, can erode public trust and negatively impact brand image. Customers may lose confidence in the organization’s ability to protect their data, leading to a loss of business. The severity of the reputational damage depends on the nature and scale of the data compromised.
Strategies for Mitigating the Impact of the Worm
Several strategies can be employed to mitigate the impact of NetCrawler. These include proactive security measures such as vulnerability patching, robust intrusion detection systems, and employee training programs. Rapid incident response plans are crucial for containing the worm’s spread and minimizing the damage. Developing a comprehensive security strategy that incorporates preventative and reactive measures is essential.
Potential Damage Scenarios
| Worm Behavior | Target System | Potential Damage |
|---|---|---|
| Rapidly spreading across networks | Personal computers | Data loss, system instability, decreased productivity |
| Exploiting vulnerabilities in critical infrastructure | Power grids | Disruptions in power supply, potential physical damage, economic losses |
| Encrypting data on enterprise servers | Financial institutions | Financial losses, disruption of services, reputational damage |
| Stealing sensitive information | Government agencies | Compromised national security, loss of sensitive data, potential breaches of trust |
Detection and Response: New Worm Starts Crawling The Net
The rapid spread of a network worm necessitates swift and effective detection and response strategies. Proactive monitoring and a clear understanding of the worm’s behavior are crucial to minimizing damage and restoring network functionality. Early detection allows for timely containment, preventing further infections and the potential for widespread disruption.Effective response hinges on a multi-layered approach, encompassing various detection methods and containment procedures.
This includes identifying potential indicators of the worm’s presence, utilizing specialized tools, and isolating compromised systems to prevent further propagation.
Potential Indicators of Worm Presence
Early signs of a network worm infection often manifest as unusual network traffic patterns. These indicators may include spikes in network bandwidth consumption, an increase in connection attempts to suspicious IP addresses, or a significant rise in the number of failed login attempts. Unusual process activity, such as the creation of numerous new processes or modifications to existing ones, also warrants investigation.
System logs, particularly those related to security events, file access, and network connections, are vital sources of potential clues.
Methods for Detecting Worm Activity
Network intrusion detection systems (NIDS) are essential tools for detecting malicious activity. NIDS constantly monitor network traffic for suspicious patterns that align with the worm’s known behavior. Similarly, security information and event management (SIEM) systems consolidate security logs from various sources, enabling correlation of events and identification of potential threats. Furthermore, endpoint detection and response (EDR) solutions can detect and analyze activities on individual computers, providing valuable insights into the worm’s actions.
Regular vulnerability scans are crucial to identify potential entry points for the worm. An example is a vulnerability scan that reveals an outdated operating system on a server, allowing for rapid patching and preventing exploitation.
Procedures for Isolating and Containing the Worm’s Spread
Upon detecting the worm’s presence, immediate isolation of infected systems is paramount. This involves disconnecting affected machines from the network, preventing further propagation and minimizing the risk of data exfiltration or further damage. Network segmentation, dividing the network into smaller, isolated segments, can contain the worm’s spread if the infection is localized. Restoring compromised systems requires careful analysis to avoid reintroduction of the worm during the recovery process.
Consider implementing a rollback plan to restore the system to a known good state, before the worm infected the system.
Examples of Tools and Technologies, New worm starts crawling the net
Numerous tools and technologies are available to identify and contain network threats. Snort, an open-source intrusion detection system, is frequently used to identify network anomalies and malicious activity. Firewalls, acting as a gatekeeper for network traffic, can prevent the worm from spreading to other parts of the network. Endpoint protection solutions, such as those offered by vendors like CrowdStrike or Malwarebytes, provide comprehensive protection against various threats, including worms.
Sophisticated analysis tools can decode and interpret the worm’s behavior to understand its potential damage and implement the necessary countermeasures. An example is using a system call analysis tool to understand the worm’s access to critical system files.
A new worm is making its way across the internet, raising concerns about vulnerabilities. This fresh threat highlights the urgent need for robust security measures in our digital infrastructure. Fortunately, Intel’s partnership with Wave Systems to build security directly into their chips ( intel partners with wave systems to put security into chips ) could be a crucial step in mitigating future attacks like this.
Hopefully, this proactive approach will help protect against the next wave of online threats.
Effectiveness of Detection Methods
| Detection Method | Effectiveness | Description |
|---|---|---|
| Network Intrusion Detection Systems (NIDS) | High | Identify malicious network traffic patterns. |
| Security Information and Event Management (SIEM) | High | Correlate security logs from various sources. |
| Endpoint Detection and Response (EDR) | Medium-High | Analyze activities on individual computers. |
| Vulnerability Scans | Medium | Identify potential entry points for the worm. |
| Firewalls | High | Prevent unauthorized access and the spread of threats. |
The effectiveness of each method depends on factors like the sophistication of the worm, the specific network architecture, and the thoroughness of the monitoring and analysis procedures. A comprehensive approach that combines multiple detection techniques provides a robust defense against evolving network threats.
Prevention and Mitigation
The relentless spread of the “Worm” necessitates proactive measures to contain its impact and safeguard interconnected systems. A comprehensive approach to prevention and mitigation involves a multi-faceted strategy that combines robust security practices with a swift and well-defined incident response plan. This section details critical steps to reduce the worm’s risk and bolster future system defenses.
A new digital worm is slithering its way across the internet, and it’s fascinating to see how quickly it’s spreading. This new type of online presence might actually be linked to recent breakthroughs in memory technology, like the amazing plastic discovery that promises advanced memory storage solutions. plastic discovery means advanced memory could be the key to understanding this new online phenomenon, and how it might evolve further.
It’s definitely something to keep an eye on as the digital worm continues its exploration.
Proactive Security Measures
Implementing robust security protocols is paramount to reducing the risk of infection. These measures form the first line of defense against the worm’s infiltration and propagation. Prioritizing these preventive measures ensures systems are less vulnerable to the worm’s attack.
- Regular Software Updates: Promptly installing security patches and updates is crucial. These updates often address vulnerabilities that the worm exploits. For example, the WannaCry ransomware worm leveraged a known vulnerability in outdated Microsoft Windows systems, highlighting the importance of timely updates.
- Strong Passwords and Multi-Factor Authentication: Implementing strong passwords and multi-factor authentication (MFA) is essential to secure accounts. This reduces the risk of unauthorized access, which can facilitate the worm’s spread. Robust password policies and the use of MFA prevent unauthorized users from gaining access, even if they obtain credentials.
- Network Segmentation: Dividing networks into isolated segments limits the worm’s ability to spread across the entire network. This containment approach restricts the worm’s movement to a specific segment, preventing it from rapidly compromising the entire system.
- Intrusion Detection and Prevention Systems (IDS/IPS): Deploying IDS/IPS systems allows real-time monitoring for suspicious activities. These systems detect and block malicious traffic, including the worm’s attempts to penetrate the network. IDS/IPS systems provide a critical layer of security by monitoring network traffic and identifying malicious patterns, including those associated with the worm’s behavior.
- Antivirus and Antimalware Software: Maintaining up-to-date antivirus and antimalware software is a fundamental security practice. These tools detect and remove malicious code, including the worm, before it can cause significant damage. Regular scans and proactive updates to antivirus software are vital in preventing the worm from infecting systems.
Hardening Systems Against Future Threats
Developing a comprehensive security posture that anticipates future threats requires adaptability and continuous improvement. Proactive measures address the worm’s current characteristics while also preparing for future threats.
- Vulnerability Assessments and Penetration Testing: Regular vulnerability assessments and penetration testing identify potential weaknesses in systems. These assessments highlight vulnerabilities that the worm exploits, allowing proactive remediation. By simulating real-world attacks, penetration testing exposes vulnerabilities and helps in strengthening defenses.
- Security Information and Event Management (SIEM): SIEM systems centralize security logs and events. This centralized view allows for correlation of events, providing valuable insights into potential threats. SIEM systems aggregate security data from various sources, facilitating the identification of patterns and anomalies related to the worm.
- Security Awareness Training: Educating users about security best practices is crucial. This training helps prevent social engineering attacks, which can be a vector for the worm’s propagation. Users are the first line of defense against malicious attacks; training empowers them to identify and avoid phishing attempts and other social engineering tactics.
Comparison of Security Measures
Different security measures provide varying levels of protection. A combination of approaches provides the most robust defense.
| Security Measure | Description | Strengths | Weaknesses |
|---|---|---|---|
| Firewall | Controls network traffic | Basic security, easy to implement | Can be bypassed, limited visibility |
| Intrusion Detection System (IDS) | Monitors network traffic for malicious activity | Early warning, enhanced visibility | False positives, needs configuration |
| Antivirus Software | Scans and removes malware | Detects known threats, easy to deploy | Can miss zero-day threats, relies on signatures |
Incident Response Plan
A robust incident response plan is critical for handling worm infections. This plan should detail steps to contain, eradicate, and recover from such threats.
- Identification and Containment: Rapid identification and containment of the worm’s spread is critical. This involves isolating affected systems and preventing further propagation.
- Eradication: Removing the worm from affected systems is a critical step. This involves remediation actions like system restoration, malware removal, and data recovery.
- Recovery: Restoring affected systems and data is essential to minimize downtime and disruption. This process involves system rebuilding, data restoration, and verifying the integrity of the system.
Illustrative Scenarios
A network worm, by its very nature, is designed to exploit vulnerabilities and spread rapidly across a network. Understanding potential scenarios is crucial for developing effective defenses. These scenarios demonstrate how such a worm can affect various parts of an organization and highlight the importance of proactive security measures.
Financial Institution Network Compromise
This scenario details a hypothetical attack on a major financial institution. The worm exploits a known vulnerability in the institution’s core banking system. Initial infections occur through compromised email attachments. The worm quickly propagates through the network, targeting servers housing customer data, transaction logs, and internal financial records. It encrypts critical data, demanding a ransom for its release, impacting daily operations and potentially causing significant financial losses.
The worm’s propagation across the network would be visualized as a series of nodes (servers) turning red, spreading outward from the initial point of infection. The ripple effect is devastating, affecting multiple departments, from customer service to compliance, and potentially leading to legal ramifications.
Government Agency Data Breach
A worm targeting a government agency could have devastating consequences. It might exploit a vulnerability in a system managing sensitive classified information, such as national security documents. The worm could modify or delete files, potentially revealing confidential data to unauthorized individuals. The impact extends beyond the affected department, impacting national security and potentially causing damage to international relations.
The worm’s propagation would appear as a gradual darkening of specific sectors of the network, with critical data servers becoming completely blacked out.
Healthcare System Disruption
Imagine a worm targeting a large hospital network. It might exploit a vulnerability in the electronic health records (EHR) system, encrypting patient data and disrupting critical operations. The worm’s propagation would manifest as a rapid spread of infection across the network, affecting various departments like radiology, surgery, and emergency care. This would severely hamper patient care and potentially cause loss of life.
A graphical representation would show a sector of the network, representing the hospital’s EHR system, rapidly turning orange and then black as the worm takes control. The worm’s activity would also cause a cascading failure across the network, as servers supporting other essential services, like medical imaging, go down.
Detailed Network Attack Scenario
A hypothetical network attack by a similar worm proceeds in stages:
- Initial Infection: The worm gains entry through a compromised email attachment opened by a user within the marketing department.
- Lateral Movement: The worm exploits a known vulnerability in the network’s file-sharing service, spreading rapidly to other servers in the finance and human resources departments.
- Data Encryption: The worm targets sensitive data, including financial records and employee information, encrypting it and demanding a ransom for its release. The affected servers would display a visual message indicating the encryption process.
- Network Isolation: The worm attempts to isolate the compromised systems from the rest of the network to prevent detection and to hinder response efforts.
- Dissemination: The worm continues to spread through the network, targeting servers in different departments, including research and development, causing disruption in all sectors.
Visual Representation of Worm Propagation
The worm’s propagation across the network can be visualized as a spreading “infection” across the network diagram. Initially, a single node (a server) in a specific department, perhaps the marketing department, would turn a distinctive color, such as red. This node represents the initial infection point. Subsequently, neighboring nodes, representing other servers, would display the same color, indicating the worm’s spread.
The rate of spread would be significant, with multiple nodes changing color in quick succession, spreading outward from the original point of infection. Nodes within the network that the worm has infected would change from a light blue to dark red, while uninfected nodes would remain light blue. The worm’s progression would be visualized as a series of red nodes spreading across the network diagram.
Closure
In conclusion, the emergence of this new network worm necessitates a proactive and multifaceted approach to security. By understanding its characteristics, potential impact, and various detection and mitigation strategies, organizations can better prepare for and respond to such threats. The tables and illustrative scenarios provide a practical framework for assessing risks and developing robust incident response plans. Ultimately, vigilance and a commitment to continuous improvement in security protocols are paramount in today’s dynamic cyber landscape.