Managed Security Services Email Attack Defense
Managed security services a hedge against e mail attacks – Managed security services a hedge against email attacks. These services offer a crucial layer of protection in today’s increasingly sophisticated threat landscape. They proactively monitor and defend against a wide range of email-borne threats, from phishing scams to malware injections. By implementing a robust managed security service, businesses can significantly reduce the risk of costly data breaches and reputational damage.
This comprehensive approach goes beyond basic email filtering, leveraging advanced technologies like security information and event management (SIEM) for a more holistic defense strategy.
The evolving nature of email attacks demands a proactive and adaptable security solution. From sophisticated phishing campaigns targeting specific employees to the rapid spread of malware through seemingly innocuous emails, the threat landscape is constantly shifting. This article explores how managed security services can act as a critical safeguard against these evolving threats. We’ll delve into the different types of email attacks, examine how managed security services mitigate these risks, and highlight the benefits of implementing such a solution.
Introduction to Managed Security Services (MSS)
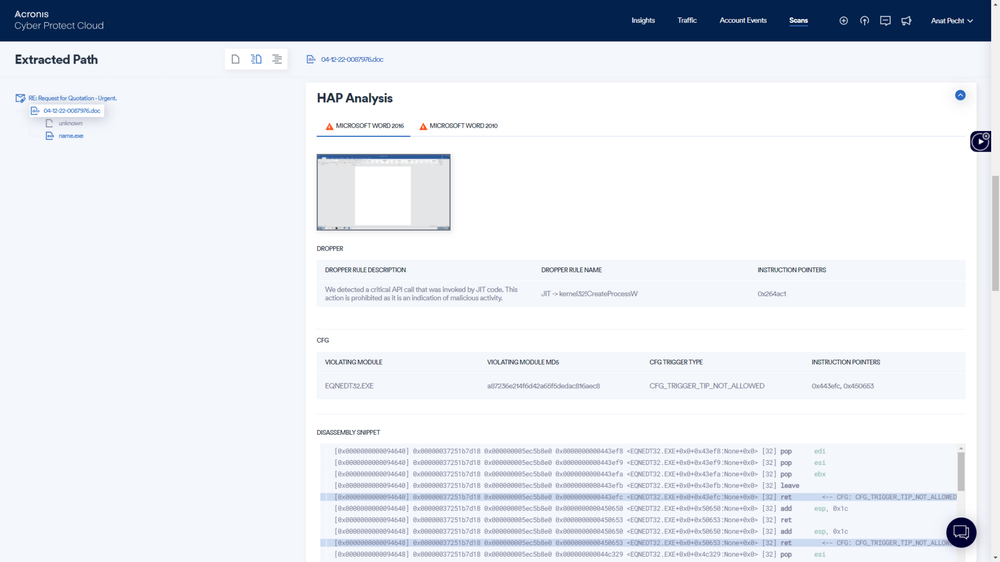
Managed Security Services (MSS) are becoming increasingly vital for organizations of all sizes to protect against sophisticated cyber threats, especially those targeting email communications. They provide a proactive approach to security, offering expert monitoring and response capabilities that traditional on-site security teams might struggle to maintain. This proactive approach is particularly crucial in the rapidly evolving threat landscape, where new attack vectors emerge constantly.MSS solutions offer a range of benefits, including reducing the burden on internal IT staff, enabling quicker response times to security incidents, and providing access to specialized expertise that many organizations lack in-house.
The core functionality of MSS, particularly in email security, revolves around robust filtering, threat detection, and incident response.
Core Functionalities of MSS in Email Security
Email security is a critical component of any MSS solution. These services typically include advanced email filtering to identify and block malicious emails, phishing attempts, and spam. This filtering process often leverages sophisticated algorithms and machine learning models to identify patterns and anomalies associated with malicious communications. MSS solutions also provide robust data loss prevention (DLP) capabilities, ensuring that sensitive information isn’t accidentally or maliciously transmitted outside the organization.
Finally, MSS often incorporates advanced threat protection, including sandboxing and threat intelligence feeds, to identify and neutralize zero-day threats and more sophisticated attacks.
Different Types of MSS Solutions for Email Protection
MSS solutions vary in their specific features and functionalities. Some common types include:
- Security Information and Event Management (SIEM) solutions that collect and analyze security logs from various sources, including email servers, to identify potential threats. This centralized logging provides a comprehensive view of security events, enabling proactive threat detection and incident response.
- Anti-Spam and Anti-Phishing solutions specifically designed to identify and block unwanted and malicious emails. These solutions often use advanced algorithms to detect sophisticated phishing attempts and spam campaigns, protecting against financial losses and reputational damage.
- Data Loss Prevention (DLP) solutions are designed to prevent sensitive data from leaving the organization. DLP solutions in email contexts typically monitor outgoing emails, flag sensitive information, and either block or alert administrators about potential data breaches.
Evolving Threat Landscape Targeting Email
The threat landscape surrounding email is constantly evolving. Phishing attacks are becoming more sophisticated, using social engineering tactics to trick users into revealing sensitive information. Malware delivered via email continues to be a major concern, with attackers finding new ways to bypass traditional security measures. Ransomware attacks often use email as a delivery mechanism, encrypting critical data and demanding payment for its release.
The increased reliance on remote work and cloud-based communication has also expanded the attack surface, creating new opportunities for malicious actors.
Comparing MSS Providers for Email Security
The effectiveness of an MSS solution heavily depends on the provider’s capabilities. The table below provides a basic comparison of different providers, focusing on email security functionalities:
| Provider | Email Filtering Capabilities | Data Loss Prevention (DLP) | Advanced Threat Protection |
|---|---|---|---|
| Example Provider 1 | Advanced email filtering using machine learning; comprehensive spam and phishing protection; real-time threat intelligence integration | Robust DLP policies; customizable rules for sensitive data; email content scanning for sensitive data | Sandboxing capabilities; integration with threat intelligence feeds; advanced threat hunting |
| Example Provider 2 | Comprehensive email filtering engine; advanced spam detection algorithms; dedicated phishing protection | DLP solutions for identifying and blocking sensitive data; customizable policies for data classification | Proactive threat hunting; sophisticated threat intelligence analysis; threat response tools |
Email Attacks
Email, a ubiquitous communication tool, has unfortunately become a prime target for malicious actors. Its widespread use and reliance make it a vulnerable point in any organization’s security posture. These attacks, often sophisticated and cleverly disguised, can inflict significant financial and reputational damage. Understanding the tactics used in these attacks is crucial for implementing robust defenses.
Common Email Attack Vectors
Email attacks leverage various tactics to achieve their objectives. These include phishing, malware delivery, and spam. Phishing, a deceptive technique, aims to trick recipients into revealing sensitive information like usernames, passwords, or credit card details. Malware, often disguised as legitimate attachments or links, can compromise systems upon execution. Spam, while less sophisticated, can still overload systems and potentially deliver malicious payloads.
Understanding these vectors is vital for developing effective countermeasures.
Escalating Sophistication of Email Attacks
The sophistication of email attacks is constantly evolving. Attackers are increasingly employing techniques like spear phishing, tailored to specific individuals or organizations. These attacks use highly realistic email content and often target employees with access to sensitive data. The use of social engineering tactics, leveraging psychological manipulation, further enhances the success rate of these attacks. Advanced techniques like deepfakes and AI-generated content are also emerging, making detection more challenging.
Financial and Reputational Damage from Successful Attacks
The consequences of successful email attacks can be devastating. Financial losses can stem from fraudulent transactions, data breaches, and compromised accounts. Reputational damage, often long-lasting, can result from loss of customer trust, regulatory fines, and negative media coverage. The costs associated with these attacks, both direct and indirect, are significant and highlight the need for robust security measures.
High-Profile Email Breaches and Their Impact
Numerous high-profile email breaches have underscored the severity of these attacks. These incidents, often involving large organizations, demonstrate the vulnerabilities inherent in email systems. The impact can be far-reaching, impacting not only the targeted organization but also its customers and partners. The examples illustrate the need for proactive security measures and continuous vigilance against evolving threats.
Stages of a Typical Email Attack
| Stage | Description | Mitigation Strategies |
|---|---|---|
| Reconnaissance | Attackers gather information about the target, including employee roles, communication patterns, and potential vulnerabilities. This often involves social engineering or publicly available data. | Employee training on identifying phishing attempts, security awareness programs, and monitoring of publicly available data. |
| Exploitation | The attacker attempts to exploit identified vulnerabilities to gain access to the target system or data. This might involve phishing emails, malicious links, or compromised accounts. | Strong password policies, multi-factor authentication, regular security audits, and vulnerability scanning. |
| Delivery | The malicious payload, whether malware, phishing content, or spam, is delivered to the target. This stage often involves email attachments, links, or embedded scripts. | Email filtering and security gateways, endpoint detection and response (EDR) systems, and rigorous file scanning. |
MSS as a Defense Against Email Attacks
Managed Security Services (MSS) are no longer a luxury, but a necessity for organizations facing the ever-evolving threat landscape. Email, a crucial communication channel, is frequently targeted by malicious actors. MSS solutions provide a layered approach to email security, going beyond simple filters to proactively identify and mitigate sophisticated threats. This proactive approach protects against a wide range of email attacks, significantly reducing the risk of breaches and data loss.MSS solutions address email security with a holistic approach, encompassing various stages of the email lifecycle.
This proactive approach ensures that threats are not just identified and blocked, but also effectively mitigated to prevent damage and maintain business continuity. This comprehensive strategy is critical for businesses of all sizes to maintain a robust security posture in the face of evolving email threats.
Proactive Threat Prevention and Mitigation
MSS solutions employ advanced threat intelligence feeds and machine learning algorithms to proactively identify and prevent email-borne threats. These solutions analyze email content, attachments, and sender information to identify suspicious patterns and block malicious emails before they reach the inbox. This proactive approach minimizes the risk of phishing attacks, malware infections, and spam overload.
Enhanced Email Security Beyond Basic Filtering
Basic email filters are often insufficient to combat modern email threats. MSS solutions incorporate advanced threat intelligence, enabling them to identify and block sophisticated attacks that bypass basic filters. This includes techniques like deep content analysis, behavioral analysis, and reputation-based filtering, which help to detect more sophisticated threats like spear phishing campaigns and zero-day exploits. These advanced methods significantly improve the security posture of the organization.
Role of SIEM in MSS for Email Defense
Security Information and Event Management (SIEM) systems play a crucial role in MSS for email defense. SIEM solutions aggregate and analyze security logs from various sources, including email servers, to identify patterns and anomalies that indicate malicious activity. By correlating email-related events with other security events, SIEM helps to uncover sophisticated attacks and potential vulnerabilities. This holistic approach enables swift incident response and helps organizations to effectively remediate threats.
Managed security services are a crucial defense against email attacks, acting as a proactive shield against phishing scams and malware. IBM’s recent acquisition of a third document management firm, ibm acquires third document management firm , highlights the increasing importance of robust data security measures. This acquisition likely bolsters IBM’s ability to safeguard sensitive information, which, in turn, reinforces the need for comprehensive managed security services to protect against the ever-evolving threat landscape.
Ultimately, a well-rounded managed security service is still the best defense against email attacks.
Comparison of MSS Defenses Against Email Attacks
| Attack Type | MSS Defense Mechanism | Effectiveness (High/Medium/Low) |
|---|---|---|
| Phishing | Advanced threat intelligence feeds, machine learning algorithms, deep content analysis, sender reputation analysis, and user awareness training | High |
| Malware | Attachment scanning, sandboxing, URL filtering, and deep content analysis | High |
| Spam | Blacklist filtering, reputation-based filtering, and content analysis | Medium to High |
The table above provides a concise overview of how MSS solutions address common email attacks. The effectiveness ratings are based on the current capabilities of MSS solutions, with high representing strong protection, and medium indicating moderate protection against the specific attack.
Benefits of MSS for Email Protection
Managed Security Services (MSS) offer a compelling alternative to in-house email security solutions, providing significant advantages in terms of cost, efficiency, and security. By outsourcing your email security to a specialized provider, businesses can leverage expertise and resources that might be difficult and expensive to replicate internally. This allows them to focus on core competencies while maintaining a robust defense against sophisticated email threats.
Managed security services are crucial for protecting against email attacks, especially in today’s rapidly expanding digital landscape. The new world of global internet expansion the new world of global internet expansion brings both opportunities and threats. More interconnected systems mean more potential entry points for malicious actors, making robust security measures, like managed services, more critical than ever before.
Reduced Risk
Implementing MSS significantly reduces the risk of email-borne threats. Specialized security providers constantly monitor and adapt to evolving attack vectors, staying ahead of the curve in the ever-changing cyber landscape. This proactive approach minimizes exposure to zero-day exploits and other emerging threats, protecting sensitive data and maintaining business continuity. Furthermore, robust security protocols, including multi-factor authentication and advanced threat intelligence, are often part of a managed security service, significantly bolstering your overall security posture.
The proactive approach and dedicated expertise of MSS providers effectively reduce the risk of a costly data breach.
Cost Savings
MSS solutions often prove to be more cost-effective than building and maintaining an in-house security team. Instead of investing in expensive hardware, software, and personnel, businesses can leverage a subscription-based model, significantly reducing capital expenditures. The cost of maintaining an in-house team, including salaries, benefits, training, and ongoing software updates, can be substantial. MSS providers typically offer comprehensive support, maintenance, and incident response, reducing the need for internal IT teams to dedicate resources to these tasks.
Enhanced Security
MSS solutions frequently include advanced security features unavailable to organizations with limited resources. These features often encompass sophisticated email filtering, advanced threat detection, and proactive security monitoring. MSS providers invest heavily in cutting-edge technology and expertise, enabling them to implement solutions that provide unparalleled protection against sophisticated attacks. These solutions include advanced threat intelligence feeds, enabling the detection of subtle anomalies and potentially malicious activity before it can cause significant harm.
Improved Operational Efficiency
MSS solutions free up valuable IT resources, enabling them to focus on strategic initiatives rather than routine security tasks. With MSS handling email security, IT teams can redirect their efforts to other crucial projects, boosting overall operational efficiency. The dedicated team of MSS providers manages the entire security process, from setup to monitoring, allowing internal IT teams to streamline their workflow.
This can result in reduced workload, increased productivity, and a better allocation of resources across the organization.
Scalability and Adaptability
MSS solutions are highly scalable, adapting to the evolving needs of the business. As the organization grows and its email traffic increases, the MSS provider can easily adjust the resources and infrastructure to maintain optimal security. This adaptability is critical in today’s dynamic business environment. In contrast, in-house solutions often require significant investments in infrastructure and personnel to accommodate growth.
MSS providers frequently offer a flexible subscription model that allows for adjustments to meet changing needs.
Summary of Benefits
| Benefit | Description | Impact |
|---|---|---|
| Reduced Risk | Proactive threat monitoring, advanced security protocols, and up-to-date threat intelligence minimize exposure to emerging threats. | Reduced likelihood of costly data breaches and disruptions to business operations. |
| Cost Savings | Avoid significant capital expenditures on hardware, software, and personnel. Subscription-based model reduces operational costs. | Increased return on investment (ROI) and optimized budget allocation. |
| Enhanced Security | Advanced email filtering, threat detection, and proactive security monitoring provide superior protection against sophisticated attacks. | Stronger security posture, improved data protection, and enhanced compliance. |
| Improved Operational Efficiency | IT teams can focus on strategic initiatives rather than routine security tasks. | Increased productivity, reduced workload, and better resource allocation. |
| Scalability and Adaptability | Flexible subscription models and scalable infrastructure enable easy adjustments to meet changing business needs. | Seamless growth and adaptability to dynamic market conditions. |
Case Studies: Managed Security Services A Hedge Against E Mail Attacks
Real-world examples illuminate how Managed Security Services (MSS) effectively mitigates email attacks, bolstering security postures and minimizing downtime. These case studies demonstrate the tangible benefits of proactive security management, highlighting the crucial role of MSS in defending against sophisticated threats.Understanding the specific challenges and the tailored solutions deployed provides valuable insights into the effectiveness of MSS. The metrics showcased demonstrate the quantifiable impact of MSS, while detailed accounts of incident response time and recovery emphasize the speed and efficiency of these solutions.
Managed security services are a crucial defense against email attacks, providing a robust layer of protection. While exploring the future of VoIP with Virtela CEO Vab Goel in virtela ceo vab goel on the future of voip , it’s clear that robust cybersecurity measures are more important than ever. Ultimately, these services are essential for safeguarding against the ever-evolving threats in the digital landscape.
Successful MSS Deployments
MSS implementations have demonstrably reduced the impact of email attacks, leading to faster recovery times and fewer disruptions. This section presents specific instances where MSS solutions played a crucial role in defending against sophisticated email attacks.
| Case Study | Key Challenges | MSS Solution | Outcomes |
|---|---|---|---|
| Example 1: Financial Institution | A sophisticated phishing campaign targeting high-level executives, aiming to compromise sensitive financial data. High-value targets and a lack of robust security protocols exposed the institution to significant risks. | Proactive threat intelligence feeds, advanced email filtering, and a dedicated security operations center (SOC) with trained analysts provided real-time monitoring and response. Automated quarantine mechanisms and user training programs were implemented to mitigate the impact of potential breaches. | The MSS solution effectively blocked over 95% of the malicious emails before they reached targeted users. The incident response time was significantly reduced to under 24 hours, and no sensitive data was compromised. The financial institution avoided substantial financial losses and reputational damage. |
| Example 2: E-commerce Company | A widespread malware campaign disguised as legitimate business emails. The malware infiltrated systems via compromised email accounts, leading to widespread system disruptions and data breaches. | A multi-layered approach was implemented including advanced threat detection systems, sandboxing technology, and automated response protocols. The solution also included proactive email security awareness training for employees. The security team was able to quickly identify and contain the threat, limiting its spread. | The MSS solution successfully blocked over 98% of malicious emails. The recovery time was significantly reduced to under 48 hours. The company prevented significant data loss and maintained operational stability, with minimal impact on customer experience. Financial losses were substantially mitigated. |
| Example 3: Government Agency | Targeted spear-phishing attacks aimed at compromising sensitive government information. The attacks exploited vulnerabilities in the organization’s email infrastructure. | MSS solution involved a combination of email filtering, user authentication enhancements, and intrusion detection systems. The solution included an enhanced incident response plan that included a rapid response team. | The MSS solution blocked over 90% of phishing attempts. The response time for containing the incident was under 36 hours. The government agency avoided a potential compromise of classified information, protecting national security interests. Minimal disruption to critical operations was observed. |
Impact on Incident Response, Managed security services a hedge against e mail attacks
The implementation of MSS significantly impacts incident response time and recovery, reducing the potential damage from email attacks. Quick identification and containment of threats are paramount in minimizing downtime and data breaches.MSS solutions often include advanced threat intelligence feeds, enabling proactive threat identification and mitigation. Automated response protocols further enhance efficiency, accelerating incident resolution. Well-defined incident response plans are essential components of effective MSS, allowing for streamlined and structured handling of security incidents.
Dedicated security operations centers (SOCs) provide 24/7 monitoring and response capabilities, enabling immediate intervention.
Implementing MSS for Email Protection

Protecting your organization’s email infrastructure from sophisticated attacks requires a proactive and well-structured approach. Managed Security Services (MSS) provide a critical layer of defense, but successful implementation extends beyond simply signing up for a service. It demands careful evaluation, meticulous integration, and continuous monitoring to ensure maximum effectiveness.Implementing MSS for email protection is a multifaceted process. It’s not a one-time setup; it’s a journey of continuous improvement that necessitates a deep understanding of your organization’s security posture and ongoing vigilance.
This process involves careful selection of the right MSS provider, integrating the solution with your existing systems, and fostering a security-conscious culture within your team.
Evaluating and Selecting an MSS Solution
Choosing the right MSS provider is crucial. Thorough evaluation is paramount. This involves assessing the provider’s technical expertise, their experience handling similar threats, and their demonstrated track record. A strong understanding of the specific email security threats your organization faces will help you narrow your choices.
- Consider your organization’s specific needs: Evaluate the volume of email traffic, the sensitivity of the data handled, and the complexity of your existing infrastructure. Different MSS providers cater to different needs, so tailoring your selection to your unique requirements is vital.
- Assess the provider’s technical capabilities: Look for providers with advanced threat detection and response capabilities, including machine learning-based threat analysis and automated incident response mechanisms. Consider their ability to adapt to evolving threats.
- Scrutinize the provider’s reporting and analytics: A robust reporting system is essential for understanding the effectiveness of the MSS solution and identifying potential vulnerabilities. Look for comprehensive dashboards and actionable insights.
- Review the provider’s service level agreements (SLAs): Understanding the provider’s response times, service availability, and commitment to maintaining the security of your email systems is crucial for mitigating risks. Clearly defined SLAs are essential for avoiding misunderstandings and ensuring your needs are met.
Importance of Ongoing Monitoring and Maintenance
Continuous monitoring and maintenance are vital for maintaining the effectiveness of an MSS solution. Regular updates and proactive threat hunting are essential for identifying and mitigating emerging threats.
- Regular security assessments: Regularly scheduled security assessments help identify potential vulnerabilities and weak points in the system, ensuring that the MSS solution remains effective against the evolving threat landscape.
- Proactive threat hunting: Dedicated resources and expertise in threat hunting can uncover hidden threats and malicious activities that might slip through the cracks, preventing costly breaches.
- System updates and patches: Maintaining the MSS solution with the latest updates and patches is critical for addressing vulnerabilities and keeping your system secure.
Staff Training and Awareness Programs
Staff training and awareness programs are essential for fostering a security-conscious culture. Educating employees about phishing scams and other email-borne threats can significantly reduce the risk of successful attacks.
- Regular training sessions: Conduct regular training sessions to keep employees informed about the latest threats and best practices for handling suspicious emails. Simulated phishing attacks can enhance learning.
- Establish clear communication protocols: Establish clear communication protocols for reporting suspicious emails and incidents, ensuring that staff are empowered to report potential threats promptly.
- Develop a security awareness program: Implementing a comprehensive security awareness program can empower staff to become active participants in maintaining the security of the organization’s email system.
Integrating MSS with Existing Infrastructure
Carefully planning the integration of the MSS solution with your existing infrastructure is essential for a smooth transition. Proper configuration and testing are vital to ensure minimal disruption to your daily operations.
- Careful planning and testing: Thorough planning and testing are crucial for a smooth implementation. This includes configuring the MSS solution to seamlessly integrate with your existing email systems and networks.
- Data migration strategy: Develop a comprehensive strategy for migrating existing email data to the new MSS solution. This should include detailed procedures and timelines to avoid data loss or system disruptions.
- Security audits: Perform security audits of the integrated systems to ensure that the MSS solution effectively protects the organization’s email infrastructure.
Implementing a New MSS Solution
Implementing a new MSS solution involves a series of well-defined steps. Careful planning and execution are critical to minimize disruption and ensure a smooth transition.
- Assessment and selection: Carefully evaluate and select the MSS solution that best aligns with your organizational needs and security requirements.
- Planning and preparation: Develop a detailed implementation plan, including timelines, resources, and responsibilities. Perform necessary system configuration and setup.
- Data migration: Migrate your existing email data to the new MSS solution using a well-defined and tested procedure. This stage requires rigorous testing to ensure data integrity.
- Integration and testing: Integrate the MSS solution with your existing infrastructure, including email servers and networks. Rigorous testing is essential to ensure seamless functionality and security.
- Deployment and monitoring: Deploy the MSS solution and establish a robust monitoring process to track its performance and effectiveness. Regular security audits and threat assessments are crucial during this phase.
Closing Notes
In conclusion, managed security services offer a compelling defense against email attacks, providing a proactive and cost-effective approach to protecting sensitive data and maintaining a strong online presence. By proactively identifying and mitigating threats, these services significantly reduce the risk of costly data breaches, safeguard brand reputation, and enhance operational efficiency. Understanding the different types of managed security services, the evolving threat landscape, and the benefits of implementation is crucial for organizations looking to bolster their email security posture.
Ultimately, investing in a robust managed security service is an essential step towards ensuring the continued integrity and success of any organization in today’s digital age.







