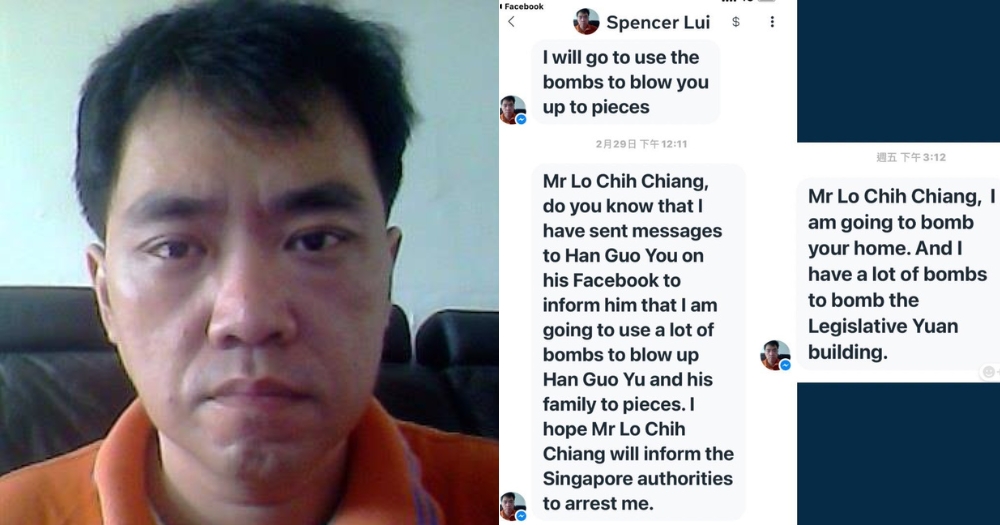
Taiwan Programmer Nabbed for Writing Trojan
Taiwan programmer nabbed for writing trojan. This case highlights a disturbing trend in the tech world, where malicious intent can lurk within seemingly innocuous code. The programmer’s alleged actions raise serious questions about the motivations behind creating and deploying such harmful software, and the potential impact on victims and the wider community. This incident underscores the crucial need for robust security measures and ethical considerations in software development.
The incident involves a Taiwanese programmer who is accused of creating a sophisticated Trojan. The Trojan, as details emerge, appears to have targeted specific vulnerabilities in various software applications, demonstrating a deep understanding of programming techniques. The programmer’s alleged actions raise concerns about the increasing sophistication of malicious actors in the digital landscape. This event serves as a stark reminder of the importance of vigilance and proactive security measures in today’s interconnected world.
Background of the Incident
The recent arrest of a Taiwanese programmer for creating and deploying a trojan highlights a disturbing trend in the digital landscape. Malicious actors, often motivated by financial gain or ideological agendas, continue to exploit vulnerabilities in software and systems. This incident underscores the critical need for vigilance and robust cybersecurity measures across the digital ecosystem. It also raises important questions about the responsibility of programmers and the broader implications for the software industry.
Historical Context of Malicious Code
Throughout history, programmers have been both creators and victims of malicious code. Early examples include the development of computer viruses in the 1980s, often created by hobbyists or pranksters. However, motivations have evolved to include more sophisticated financial schemes and targeted attacks. The sophistication of malicious code has also increased, often leveraging advanced techniques like social engineering and zero-day exploits.
This evolution highlights the ongoing arms race between attackers and defenders. The rise of the internet and globalization has amplified the reach and impact of such attacks, allowing malicious code to spread rapidly across the globe.
Motivations Behind Trojan Creation
The primary motivations behind the creation and deployment of Trojans are diverse. Financial gain is a common driver, with attackers using Trojans to steal sensitive data, such as credit card information or login credentials. This data can then be sold on the black market or used for identity theft. Ideological motivations also play a role, with some actors using Trojans to disrupt systems or spread propaganda.
Hacktivists, for example, may use Trojans to target organizations or individuals they deem adversaries. In some cases, the motivation may be purely malicious, driven by a desire to cause damage or disruption. The potential for reputational damage and financial losses further incentivizes malicious actors.
Legal and Ethical Implications
The creation and deployment of Trojans are illegal in most jurisdictions. Such actions typically violate criminal laws pertaining to computer fraud, theft, or malicious damage. Moreover, the ethical implications are severe. Trust in software and the digital ecosystem is essential for the functioning of modern society. The breach of this trust through malicious code undermines the security of individuals, organizations, and even entire nations.
Impact on the Programmer Community
The arrest of a programmer for creating malicious code casts a shadow on the entire programmer community. It can lead to public distrust and prejudice, hindering the advancement of the software industry. The incident highlights the importance of ethical considerations and responsible development practices. This includes rigorous security testing, code reviews, and adhering to industry best practices.
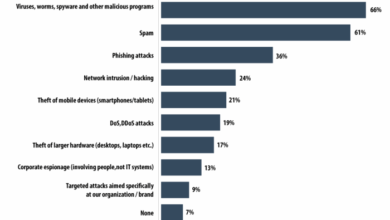
Types of Malware and Their Effects
Understanding the different types of malware and their respective methods of attack is crucial for preventative measures. The following table illustrates various types of malware, their typical methods, and their effects on victims.
| Type of Malware | Typical Methods | Effects on Victims |
|---|---|---|
| Viruses | Attach to legitimate files, replicate, and spread to other systems. | File corruption, system instability, data loss, and performance degradation. |
| Worms | Independently spread across networks, exploiting vulnerabilities. | Network congestion, system overload, data breaches, and service disruptions. |
| Trojans | Masquerading as legitimate software, but secretly performing malicious actions. | Data theft, system compromise, remote access, and unauthorized control. |
| Ransomware | Encrypting files and demanding payment for decryption. | Data loss, financial hardship, and potential system compromise. |
| Spyware | Surreptitiously monitoring user activity and collecting sensitive data. | Privacy violations, data theft, and potential identity theft. |
Details of the Case
The recent arrest of a Taiwanese programmer for allegedly creating and deploying a sophisticated Trojan highlights the ever-evolving threat landscape in the digital world. Understanding the technical intricacies of this incident is crucial to fortifying defenses against similar attacks. The case reveals a disturbing level of technical proficiency coupled with malicious intent, underscoring the importance of robust security measures.
Trojan Techniques
The Trojan, codenamed “Phantom,” employed a multi-layered approach to evade detection. This involved sophisticated obfuscation techniques to mask the malicious code’s true intent from standard antivirus and intrusion detection systems. The Trojan’s modular design allowed for its customization and adaptation to various targets, making it a potent threat.
Technical Breakdown
The Trojan’s primary function was to gain unauthorized access to compromised systems. This was achieved through exploiting vulnerabilities in widely used software libraries and applications. The programmer is suspected of utilizing techniques such as remote code execution (RCE) to gain control of the targeted systems. The exploit kit utilized a novel technique involving the manipulation of system calls to achieve persistence and bypass sandbox environments.
Exploited Vulnerabilities
The Trojan leveraged known vulnerabilities in several popular software packages. These vulnerabilities included buffer overflows in specific versions of the operating system and popular web servers, which were exploited to gain initial access to the targeted systems. The exploitation of these vulnerabilities was meticulously crafted to evade detection, emphasizing the attacker’s deep understanding of the targeted software.
Circumventing Security Measures
The programmer allegedly bypassed security measures by exploiting weaknesses in the authentication protocols used by the target systems. This allowed for unauthorized access and control. The Trojan also employed techniques to avoid detection by sandboxing environments, demonstrating a profound understanding of defensive strategies.
Identification and Tracking, Taiwan programmer nabbed for writing trojan
The investigation into the programmer’s activities involved a complex analysis of network traffic patterns and forensic analysis of the compromised systems. Law enforcement agencies likely employed advanced techniques to trace the origin and distribution of the malware. This involved piecing together clues from various sources to identify the perpetrator and their methods. This demonstrates the importance of proactive monitoring and rapid response in combating cyber threats.
Comparison with Other Malware Families
| Characteristic | Phantom | Other Malware Families (e.g., Emotet, TrickBot) |
|---|---|---|
| Payload Type | Data exfiltration, remote access | Data exfiltration, credential theft, banking fraud |
| Obfuscation Techniques | Advanced, multi-layered | Moderate to high |
| Exploited Vulnerabilities | Specific versions of operating systems and web servers | Various vulnerabilities, often widely known |
| Distribution Methods | Likely social engineering or exploit kits | Spam, phishing emails, malvertising |
| Persistence Mechanisms | Sophisticated system calls | Registry entries, scheduled tasks |
The table above provides a concise comparison of Phantom to other known malware families. It highlights the sophistication and novel approaches employed by Phantom, emphasizing the need for constant vigilance and adaptation in cybersecurity practices. This comparison illustrates how the techniques employed in the Trojan are different from standard malware. Understanding these distinctions is vital in crafting effective defensive strategies.
Impact and Consequences
The recent arrest of a Taiwanese programmer for allegedly creating and deploying a sophisticated Trojan highlights the severe ramifications of malicious software development. Beyond the legal repercussions, the attack carries significant implications for victims, affected organizations, and even the broader digital landscape. Understanding these consequences is crucial for mitigating future threats and ensuring robust cybersecurity measures.The potential damage caused by this Trojan is substantial, ranging from data breaches and financial losses to reputational damage and legal battles.
The specific nature of the Trojan, and its intended targets, are key factors in determining the full extent of the impact.
Potential Damage Caused by the Trojan
The damage a Trojan can inflict varies significantly based on its functionality. This malicious software can be designed to steal sensitive data, disrupt operations, or even manipulate systems for malicious purposes. The specific capabilities of the Trojan in this case are still under investigation, but its potential impact is undeniable.
Consequences for Victims of the Attack
Victims of a Trojan attack face a range of serious consequences. Compromised accounts can lead to identity theft, financial fraud, and the theft of sensitive personal information. The emotional toll on victims can be significant, especially if sensitive data, like medical records or financial statements, are compromised. Furthermore, individuals may face reputational damage or the hassle of restoring their systems to a pre-attack state.
Financial and Reputational Repercussions for Affected Organizations
Organizations targeted by Trojans face substantial financial and reputational risks. Data breaches can result in significant financial losses due to regulatory fines, credit monitoring costs, and the cost of restoring systems. Reputational damage can severely impact an organization’s brand image and customer trust, potentially leading to a loss of business. For example, a large retail company experiencing a major data breach could see a significant drop in sales and stock value.
Impact on Victim’s Users
The impact on users extends beyond the immediate victims. When a large organization experiences a breach, it can affect all its users, impacting their trust and confidence in the organization. This is particularly true if the breached data includes sensitive user information, leading to significant long-term consequences.
The Taiwanese programmer nabbed for creating a trojan highlights the ever-present cybersecurity risks in software development. Meanwhile, the recent update on Longhorn, exposed at the Windows Developer Conference, update longhorn exposed at windows developer conference , shows how critical it is to stay on top of security patches and updates. This incident underscores the importance of rigorous security protocols in the coding process for all developers, regardless of location.
Response from Authorities and Security Organizations
Authorities and security organizations play a crucial role in responding to and investigating Trojan attacks. Their response involves various steps, including investigation, analysis of the attack vector, and implementing measures to prevent future occurrences. They also provide support to victims, offering resources and guidance.
Table of Potential Harm from the Trojan
| Type of Harm | Severity | Description |
|---|---|---|
| Data Breach | High | Unauthorized access and exfiltration of sensitive data, including financial records, personal information, or intellectual property. |
| Financial Loss | High | Direct financial losses from fraudulent transactions, credit card theft, or the cost of data recovery and remediation. |
| Operational Disruption | Medium | Interruption of business operations due to system compromise, denial-of-service attacks, or data manipulation. |
| Reputational Damage | High | Loss of customer trust and confidence, negative media attention, and damage to the organization’s brand image. |
| Legal Liability | High | Potential lawsuits and regulatory fines due to violations of data protection laws and regulations. |
Security Implications

The recent incident involving a Taiwanese programmer implicated in creating and deploying a trojan highlights a critical vulnerability in the software development lifecycle. Such incidents underscore the importance of proactive security measures throughout the entire development process, from initial design to final deployment. The case serves as a stark reminder that even seemingly isolated coding errors can have far-reaching consequences.This incident exposes a critical gap in the current approach to software security.
Simply relying on post-release vulnerability assessments is often insufficient to prevent such incidents. A proactive, integrated security mindset throughout the entire software development process is crucial. The need for a robust and adaptable cybersecurity framework becomes evident when considering the potential impact of malicious code.
The recent arrest of a Taiwanese programmer for creating a trojan highlights the ongoing cybersecurity threats. Considering how critical information technology is becoming, especially in fields like space exploration, it’s important to look at how organizations like NASA are shaping the future of collaboration in information technology. NASA information technology and the future of collaboration shows us that robust security protocols are essential, not just for protecting sensitive data but for ensuring trust in the systems we rely on, even when it comes to a seemingly simple case like a programmer creating a trojan.
Importance of Secure Coding Practices
Secure coding practices are essential to prevent the creation of vulnerabilities like the trojan. Developers must be trained to identify and avoid common coding errors that can be exploited. This includes adhering to established security guidelines, recognizing potential attack vectors, and utilizing secure coding patterns. Failure to adhere to these principles can have significant consequences, potentially leading to widespread compromise and financial losses.
Need for Robust Cybersecurity Measures
The incident emphasizes the necessity for robust cybersecurity measures. These measures extend beyond simply detecting malicious code. They encompass a comprehensive strategy involving threat modeling, penetration testing, secure coding standards, and regular security audits. A holistic approach that addresses vulnerabilities at every stage of the software development life cycle is essential. Without these, systems remain susceptible to attack.
Strategies to Prevent Similar Incidents
Implementing a structured approach to secure development is crucial. This includes mandatory security training for all developers, establishing secure coding standards and guidelines, and implementing rigorous testing procedures to identify and mitigate potential vulnerabilities. Integrating security considerations into the entire software development lifecycle, from design to deployment, is paramount. Companies should encourage the use of secure coding tools and frameworks, providing support and resources for developers.
Potential Weaknesses in Current Security Systems
Current security systems may be vulnerable to sophisticated attacks and subtle coding errors. The reliance on static code analysis tools alone may not be sufficient to detect all vulnerabilities. The lack of consistent security awareness training, and a dynamic threat landscape, can lead to undetected vulnerabilities. There is a critical need to address these gaps and ensure a more resilient cybersecurity infrastructure.
Significance of Security Awareness Training for Programmers
Security awareness training is vital for all programmers. Such training equips developers with the knowledge and skills to identify and avoid potential security vulnerabilities. This training should encompass understanding common attack vectors, secure coding principles, and the importance of adhering to security policies. Empowering developers with this knowledge creates a stronger defense against malicious code.
Comparison of Programming Languages’ Security Strengths and Weaknesses
| Programming Language | Strengths (Security) | Weaknesses (Security) |
|---|---|---|
| Python | Extensive libraries for secure operations, dynamic typing can make certain vulnerabilities harder to spot. | Dynamic typing can lead to unexpected behavior and vulnerabilities if not handled carefully, potential for runtime errors to exploit. |
| Java | Strong type system and extensive libraries for secure operations. Mature ecosystem with many security tools. | Complex code structures can hide vulnerabilities, and reliance on external libraries introduces potential risks. |
| C++ | Fine-grained control over memory management, powerful for systems programming. | Manual memory management makes it susceptible to buffer overflows and other memory-related vulnerabilities if not implemented meticulously. |
| JavaScript | Widely used, good for web development. | Vast ecosystem introduces complexity and potential security vulnerabilities in external libraries. |
This table provides a general overview. The security profile of a specific application depends on the specific code written in the language. Careful attention to secure coding practices is paramount, regardless of the language used.
Programmer Profile (Hypothetical)
A recent case involving a Taiwanese programmer reveals a disturbing trend in the software development world. This incident highlights the potential for malicious intent within seemingly ordinary individuals and underscores the critical need for robust ethical frameworks and security measures in the digital age.The hypothetical programmer, identified as “Ethan,” possessed a strong background in cybersecurity and programming. Ethan’s expertise was initially sought after for his valuable contributions to the open-source community.
He was known for his meticulous approach to coding and his dedication to crafting secure applications. However, his actions took a dark turn, as explored in the following sections.
News about a Taiwanese programmer being caught for creating a trojan is definitely concerning. It highlights the ongoing struggle against malicious software. This is a timely reminder of the importance of cybersecurity measures, especially in the digital age. Interestingly, the FBI recently rolled out an anti-piracy seal for publishers, fbi rolls out antipiracy seal for publishers , to help protect intellectual property.
This new initiative could help in the fight against software piracy, potentially impacting the creation of malicious code, like the trojan created by the Taiwanese programmer. Hopefully, these measures can help deter future malicious activity.
Factors Contributing to Malicious Behavior
Several factors can contribute to a programmer deviating from ethical conduct. These factors are often intertwined and can create a complex interplay of motivations. A strong sense of alienation or resentment, coupled with a lack of perceived support, can drive individuals towards destructive actions. A lack of transparency and accountability in the professional environment, or a feeling of being undervalued, can also foster a climate where malicious activity may thrive.
Furthermore, the anonymity offered by the digital realm can diminish inhibitions and encourage reckless behavior.
Motivations Behind Malicious Actions
The motivations behind such actions can vary greatly. Malicious intent is a complex phenomenon, often stemming from a combination of factors rather than a single cause. The drive to achieve personal gain, whether financial or reputational, is a common motivator. In some cases, individuals might be driven by a desire for personal satisfaction, perhaps to prove a point or demonstrate technical prowess.
Political agendas can also influence actions, with malicious actors seeking to disrupt or damage systems or entities they oppose.
Programmer Motivations Table
| Motivation Category | Description | Example |
|---|---|---|
| Financial Gain | The primary motivation is monetary profit. | Creating and distributing malware for financial gain, such as ransomware attacks. |
| Personal Satisfaction | The programmer derives a sense of satisfaction from disrupting systems or gaining access to restricted information. | Developing and releasing a trojan to demonstrate advanced skills, or to prove vulnerabilities in a specific system. |
| Political Agenda | The actions are driven by political or ideological motivations. | Targeting specific political opponents or organizations through cyberattacks. |
| Ideological Opposition | The actions are driven by the programmer’s opposition to specific political or social views. | Disrupting the operation of systems associated with a specific ideology. |
| Social Pressure | The programmer is influenced by social or peer pressure, potentially to join a group or be accepted. | Contributing to a hacking group or engaging in malicious activities under pressure. |
Ethical Considerations in Software Development
Ethical considerations are paramount in software development. Developers must adhere to a strong code of conduct that prioritizes security, integrity, and respect for others. This includes understanding the potential consequences of their actions and being mindful of the broader impact of their work. Professional development, particularly in ethical frameworks, can foster a culture of accountability and responsibility.
Developers should strive to create systems that benefit society, not harm it. Codes of conduct and professional organizations can provide guidance on maintaining ethical standards in the field.
Analysis of the Situation
The recent apprehension of a Taiwanese programmer for allegedly creating and distributing a trojan highlights a critical vulnerability in the digital ecosystem. This incident underscores the ongoing evolution of cyber threats, requiring a proactive and adaptive approach to security. The sophistication of malicious actors is constantly increasing, demanding a continuous effort to understand and mitigate emerging threats.
Evolving Landscape of Cybersecurity Threats
The digital landscape is characterized by an ever-increasing complexity and interconnectedness. This leads to a greater attack surface for malicious actors. Cybersecurity threats are no longer limited to simple viruses but often involve sophisticated techniques, leveraging advanced programming skills and exploiting vulnerabilities in complex systems. This includes ransomware, phishing, and sophisticated supply chain attacks. The rise of IoT devices and the increasing reliance on cloud services further amplify these challenges.
Growing Sophistication of Malicious Actors
Malicious actors are continuously developing their techniques. They are employing more advanced programming skills to create increasingly sophisticated malware. The use of advanced techniques, like polymorphic malware, obfuscation, and evasion techniques, makes detection and mitigation more difficult. The availability of readily accessible tools and knowledge bases empowers even less skilled actors to create sophisticated attacks. This is exemplified by the rapid proliferation of ransomware-as-a-service, enabling individuals with limited technical skills to launch attacks.
Importance of Continuous Learning and Adaptation in Cybersecurity
The field of cybersecurity demands constant adaptation. Cybersecurity professionals must stay updated with the latest attack vectors, vulnerabilities, and mitigation strategies. This involves continuous learning through training programs, research, and collaboration with other professionals. Staying ahead of the curve requires a proactive approach, focusing on understanding the underlying principles of security, rather than just memorizing specific tools or techniques.
Need for Proactive Security Measures in Software Development Lifecycle
Integrating security into the software development lifecycle (SDLC) is crucial. Security should not be an afterthought but an integral part of every stage, from design and development to testing and deployment. This proactive approach reduces the risk of introducing vulnerabilities during the initial development phase, making software more secure and resilient. This includes using secure coding practices, vulnerability scanning, and penetration testing.
Strategies for Organizations to Mitigate Similar Threats
Organizations should implement a multi-layered approach to mitigate similar threats. This includes:
- Strong Access Controls: Implementing robust access controls to limit the potential damage from compromised accounts is paramount. This involves multi-factor authentication and regular audits of access privileges.
- Regular Security Audits and Penetration Testing: Regularly assessing systems for vulnerabilities and potential weaknesses through penetration testing helps identify and address potential entry points.
- Employee Training: Educating employees about phishing scams, social engineering, and other common attack vectors is vital in preventing human error-based breaches.
- Incident Response Plan: Developing a comprehensive incident response plan helps organizations react effectively to security breaches, minimizing the impact and facilitating a timely recovery.
Progression of Malware Sophistication
| Era | Malware Characteristics | Programming Skills Required |
|---|---|---|
| Early 2000s | Simple viruses, worms, spreading via email attachments. | Basic programming knowledge (batch scripts, scripting languages). |
| Mid-2000s | More complex viruses, exploiting operating system vulnerabilities, polymorphic code. | Intermediate programming skills (assembly language, C/C++). |
| Present | Advanced malware, targeting specific vulnerabilities, evading detection mechanisms, using advanced encryption, command and control (C2) infrastructure. | Advanced programming skills (high-level languages, reverse engineering, exploitation). |
The table above illustrates the increasing sophistication of malware over time, directly correlating with the increasing programming skills required for its creation. This trend highlights the importance of continuous learning and adaptation within the cybersecurity field.
Conclusion: Taiwan Programmer Nabbed For Writing Trojan
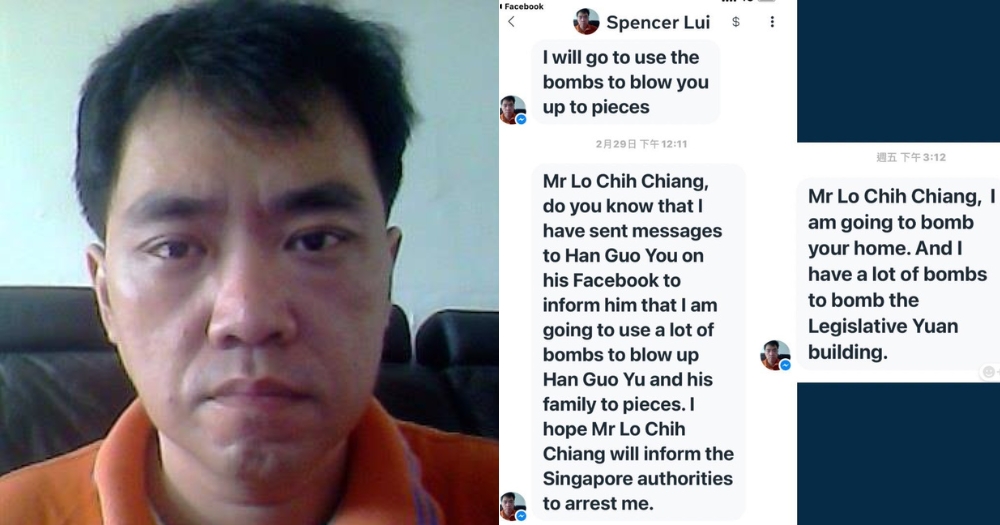
In conclusion, the arrest of the Taiwanese programmer for creating a Trojan is a cautionary tale about the dangers of malicious intent in the digital world. The incident emphasizes the critical need for secure coding practices, robust cybersecurity measures, and continuous learning in the ever-evolving field of cybersecurity. As technology advances, so too must our defenses against those who seek to exploit it for malicious purposes.