Windows XP SP2 A Security History Lesson
Windows XP Service Pack 2 under heavy security scrutiny reveals a fascinating look at vulnerabilities in older systems. This exploration dives into the historical context of SP2’s release, highlighting the security landscape at the time and common security practices. We’ll examine the major security flaws discovered, the responses from the community, and the enterprise implications, all leading to a crucial comparison with modern security standards.
Understanding the security challenges of Windows XP SP2 is more than just historical trivia. The lessons learned from this period inform modern security practices, highlighting the constant evolution of threats and the importance of continuous updates and security awareness. We’ll explore the vulnerabilities, patches, and the community’s response, to understand how security evolved over time.
Historical Context of Windows XP SP2
Windows XP, released in 2001, quickly became a dominant operating system for personal computers. Its intuitive interface and improved performance compared to its predecessors made it a popular choice for both home and business users. However, as with any software, security vulnerabilities were inevitably discovered and exploited. Service Pack 2 (SP2), released in 2004, aimed to address these issues, significantly enhancing the operating system’s overall security posture.The security landscape in the early 2000s was characterized by the rapid growth of the internet and the increasing reliance on networked computers.
This interconnectedness, while offering numerous benefits, also created new avenues for malicious actors to exploit vulnerabilities. The prevalent security practices of the time often relied on simple firewalls and antivirus software, which were sometimes insufficient to protect against sophisticated attacks. The ease of distributing malware through email and file-sharing networks contributed to the growing threat landscape. Exploits targeting vulnerabilities in operating systems and applications were commonly seen, leading to widespread infections and significant damage.
Security Landscape at the Time of SP2 Release
The period surrounding Windows XP SP2’s release was a time of escalating cyber threats. Worm outbreaks and virus epidemics were becoming increasingly common, highlighting the critical need for robust security measures. The internet’s increasing accessibility meant that attackers could reach a broader target audience. This was coupled with a growing understanding of the vulnerabilities within software and operating systems.
Exploiting these vulnerabilities allowed attackers to gain unauthorized access, disrupt services, or steal sensitive information. Security experts were actively identifying and documenting these vulnerabilities, driving the demand for improved security features in operating systems.
Common Security Practices and Vulnerabilities in the Early 2000s
Common security practices in the early 2000s often focused on reactive measures. Antivirus software was widely used, but it was frequently behind the curve in identifying and neutralizing newly emerging threats. Firewalls, while becoming more common, were sometimes poorly configured or lacked comprehensive protection. The understanding of secure coding practices was not as widespread as it is today.
This lack of awareness contributed to the prevalence of vulnerabilities in software. Remote access exploits and vulnerabilities in network protocols were frequent targets. The proliferation of email-borne malware further underscored the critical need for stronger security measures.
Security Features of Windows XP SP2 Compared to Earlier Versions
| Feature | Windows XP (Original Release) | Windows XP SP2 |
|---|---|---|
| Automatic Updates | Limited or absent | Improved automatic updates for security patches and improvements. |
| Firewall | Basic firewall, often disabled | Enhanced firewall with improved configuration options. |
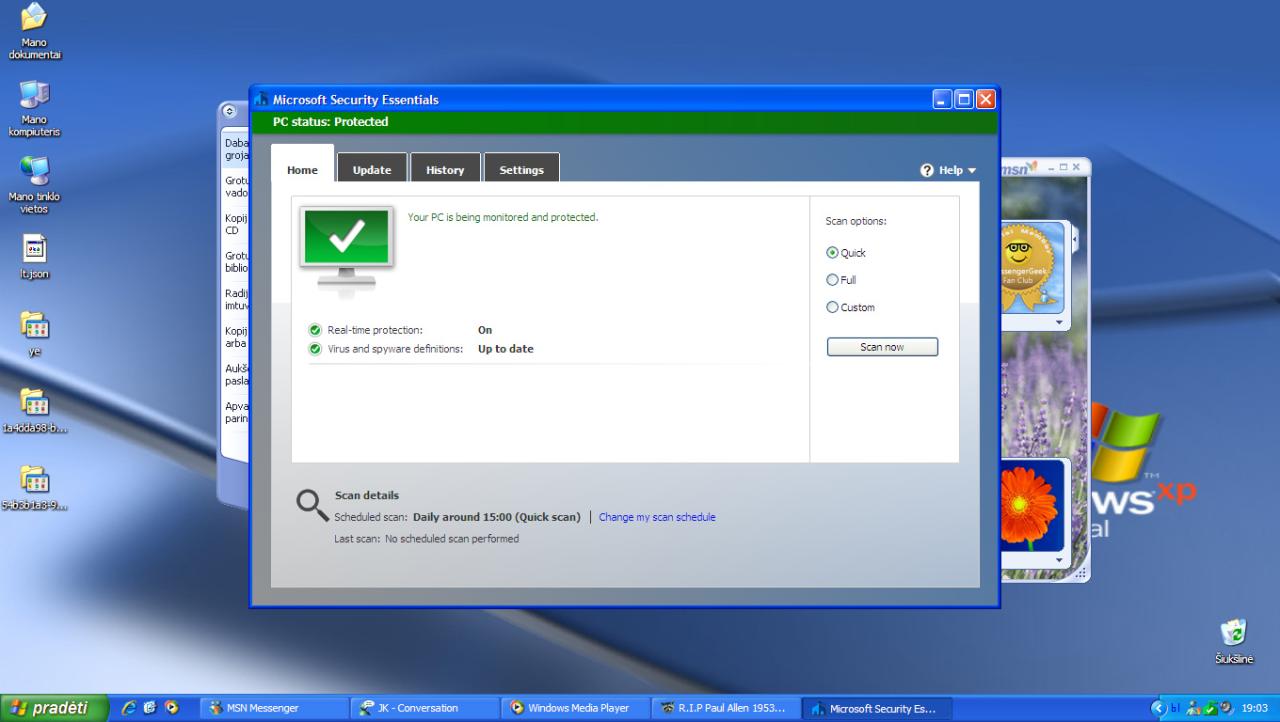
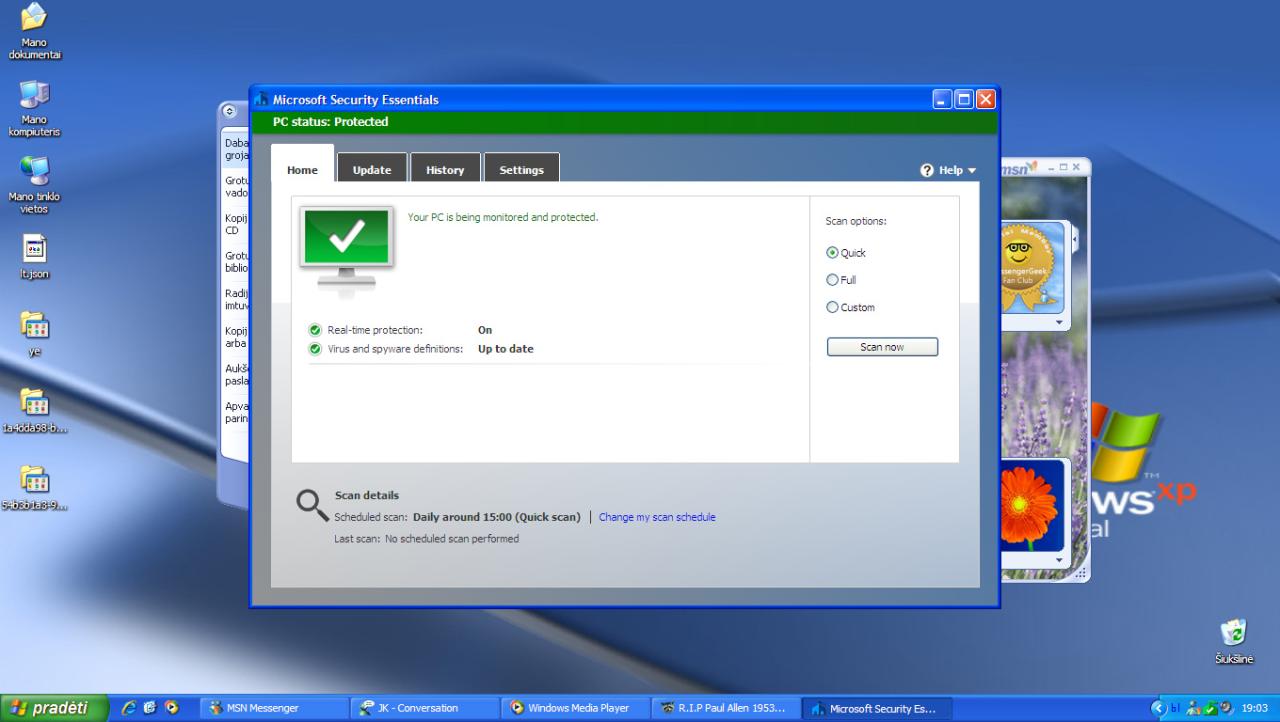
| Security Center | Limited security monitoring tools | Integrated Security Center to monitor and manage security settings. |
| User Account Control (UAC) | No UAC | No UAC, however, SP2 improved security by implementing changes that are relevant to UAC. |
| Anti-Malware Protection | Limited or dependent on third-party solutions | Enhanced anti-malware protection capabilities. |
Windows XP SP2 incorporated significant security improvements over earlier versions. The table above illustrates the notable differences. These enhancements aimed to reduce vulnerabilities and improve overall security. These changes reflected the increasing sophistication of attacks and the need for proactive security measures.
Known Vulnerabilities in Windows XP SP2

Windows XP Service Pack 2, while a significant security upgrade, still faced a range of vulnerabilities. Understanding these flaws is crucial for appreciating the ongoing evolution of cybersecurity practices and the importance of patching. These weaknesses, though sometimes exploited in sophisticated attacks, highlight the constant need for vigilance and proactive security measures.
Major Security Flaws
Windows XP SP2, despite its improvements, inherited and introduced some critical security vulnerabilities. These weaknesses often stemmed from complex interactions within the operating system’s architecture, which could be exploited by attackers. Exploiting these vulnerabilities could lead to unauthorized access, data breaches, and system compromise.
Buffer Overflow Vulnerabilities
Buffer overflows, a common vulnerability type, plagued many applications running on Windows XP SP2. These vulnerabilities occurred when a program attempted to write data beyond the allocated buffer size. Attackers could leverage this by crafting malicious input that overwrote critical memory regions, potentially allowing them to execute arbitrary code. This resulted in a wide range of possible exploits, from denial-of-service attacks to remote code execution.
For example, a malicious webpage could exploit a buffer overflow vulnerability in a web browser, allowing an attacker to take control of the user’s system.
Remote Code Execution Exploits
Remote code execution (RCE) vulnerabilities allowed attackers to execute malicious code on a vulnerable system from a remote location. This was often facilitated by flaws in the way the system handled network communications or input from untrusted sources. These exploits could lead to significant security breaches, granting attackers full control over the targeted machine. For example, a compromised web server could utilize an RCE vulnerability in a client-side application to install malicious software on user systems accessing the server.
Vulnerabilities in Third-Party Applications
Many applications, including those used to manage files or access networks, had vulnerabilities. These vulnerabilities often stemmed from flawed code or outdated libraries. Attackers could exploit these vulnerabilities to gain unauthorized access to sensitive data or systems.
Windows XP Service Pack 2 is facing a lot of scrutiny for its security flaws, and it’s a constant headache for anyone still using it. While the older OS is known for its stability, the security concerns are undeniable. Interestingly, the ongoing legal battle between HP and Gateway over PC patents, as detailed in this article hp sues gateway over pc patents , highlights the complex interplay of technological advancement and legacy systems.
Ultimately, the security risks associated with Windows XP Service Pack 2 are still a significant concern for those clinging to older systems.
Security Impact and Patches
- Many vulnerabilities in Windows XP SP2 were exploitable through buffer overflows. These allowed attackers to execute arbitrary code, leading to complete system compromise. Patches were often released to address these issues, but the vulnerability window could be significant before a patch was applied.
- Remote code execution (RCE) vulnerabilities were a critical concern, as they permitted attackers to execute commands on a vulnerable system remotely. This allowed for a variety of malicious activities, such as installing malware, exfiltrating data, or disrupting services. Patches addressed these vulnerabilities to prevent attackers from exploiting them.
Vulnerability Summary Table
| Vulnerability | Impact | Patches |
|---|---|---|
| Buffer Overflow in File Handling | Remote Code Execution, Denial-of-Service | SP2 updates, subsequent security advisories |
| Remote Code Execution in Network Services | System Compromise, Data Exfiltration | SP2 updates, subsequent security advisories |
| Vulnerabilities in Third-Party Applications | System Compromise, Data Exfiltration | Vendor updates, SP2 updates |
Security Patches and Updates
Windows XP SP2, while a significant improvement in security compared to earlier versions, remained vulnerable to evolving threats. Microsoft’s proactive approach involved releasing numerous security patches to address these vulnerabilities. This proactive strategy was crucial in mitigating risks and extending the lifespan of the operating system.
Timeline of Security Patches
The release of security patches for Windows XP SP2 wasn’t a single event but a continuous process spanning several years. Microsoft meticulously tracked and analyzed reported security flaws, prioritizing those with the highest potential impact. This process involved extensive internal testing and validation before any patch was released to the public. Patches were categorized by their severity, with critical patches addressing vulnerabilities that could lead to system compromise.
Each patch release addressed specific vulnerabilities, and the timeline reflects the dynamic nature of security threats.
Applying Security Patches
Applying these security patches required careful consideration and adherence to specific instructions. Users needed to download the appropriate patch files from Microsoft’s website and then follow the detailed installation guides. The installation process often involved restarting the system to ensure the patch was fully integrated into the operating system. Challenges included the potential for conflicts with existing software or hardware configurations, requiring careful assessment before proceeding.
Furthermore, the patch application process itself was prone to errors if not executed correctly, and potential problems with outdated software were a concern.
Effectiveness of Patches
The effectiveness of these patches in mitigating vulnerabilities was demonstrably high. Patches were often deployed in response to known exploits, and they successfully plugged security holes that could have been exploited by malicious actors. The patching process resulted in a significant decrease in reported security incidents. A crucial element of effectiveness was the swiftness of patch deployment and the detailed information provided by Microsoft on how to apply them.
The patches often prevented attackers from exploiting vulnerabilities, significantly reducing the risk of successful cyberattacks.
Windows XP Service Pack 2 is facing some serious security concerns, understandably so given its age. However, IBM’s upcoming project to build the world’s fastest Linux supercomputer, like this one , highlights a fascinating shift towards modern, more secure operating systems. This further emphasizes the need for upgrading older systems like Windows XP Service Pack 2, which, frankly, is a real concern.
Dissemination of Security Updates
Microsoft employed various methods to disseminate security updates to users. A crucial element was the dedicated security website, providing a central repository for the latest updates. These updates were categorized and prioritized based on the severity of the vulnerability. The updates were also disseminated through the Windows Update service, allowing users to automatically download and install them.
Additionally, Microsoft frequently issued advisories and security bulletins to inform users about the risks associated with specific vulnerabilities. This proactive approach informed users of the need to apply updates, which was crucial for the continued security of the system.
Community Response to Security Scrutiny
The release of Windows XP Service Pack 2 (SP2) brought about a significant wave of security scrutiny, raising concerns about vulnerabilities that could potentially compromise user systems. This scrutiny didn’t just come from security experts; a broader community of users, researchers, and developers also weighed in, shaping the landscape of security discourse around the operating system. This response reveals a dynamic interplay of concerns, discussions, and ultimately, adaptations.The intense scrutiny surrounding Windows XP SP2’s security wasn’t a passive affair.
Instead, it triggered a vibrant community response, including proactive measures by security researchers and the development of online forums dedicated to addressing and discussing the issues. The overall reaction to these vulnerabilities played a crucial role in shaping future security practices.
Community Forums and Online Discussions
The proliferation of online forums and discussion boards provided a critical space for users to share experiences, raise concerns, and collectively address security threats. Dedicated forums emerged, often becoming virtual hubs for technical support and security advice specific to SP2. These online communities served as a vital platform for disseminating information, fostering collaboration, and shaping the narrative around the security of the operating system.
Users actively sought and shared solutions, patches, and workarounds to mitigate identified vulnerabilities.
Security Researchers and Experts’ Role
Security researchers and experts played a pivotal role in identifying and publicizing vulnerabilities in Windows XP SP2. Their findings, often published in academic papers, security advisories, and blog posts, brought these issues to the forefront. Their analysis highlighted the importance of rigorous security testing and prompted further investigation into the vulnerabilities, ultimately leading to the development and implementation of security patches.
Their actions not only informed the public but also prompted the creation of new security standards and practices.
User Group Reactions to Security Issues, Windows xp service pack 2 under heavy security scrutiny
Different user groups reacted to the security concerns surrounding Windows XP SP2 in various ways. The diverse community responses provide valuable insights into how various segments of the population approached and resolved these issues.
| User Group | Typical Reaction | Explanation |
|---|---|---|
| Advanced Users/Tech Enthusiasts | Proactive Investigation and Mitigation | These users were often quick to identify vulnerabilities and develop workarounds or implement security measures. |
| General Users | Cautious Adoption of Patches | General users often relied on the recommendations of security experts and followed instructions for applying patches. |
| System Administrators | Prioritization of Security Policies | System administrators were focused on establishing and enforcing security policies to protect their organizations from potential threats. |
| Software Developers | Adapting to New Security Standards | Software developers were tasked with updating their applications to address compatibility and security issues arising from SP2. |
Impact on Enterprise Security
Windows XP Service Pack 2, while a significant step forward in patching known vulnerabilities, presented unique challenges for enterprises reliant on this operating system. The vulnerabilities, though patched, created a window of opportunity for malicious actors and highlighted the crucial need for proactive security measures. The widespread adoption of XP SP2 across corporate networks amplified the potential impact of any successful exploits.The exposure of critical vulnerabilities in Windows XP SP2 created a real and immediate threat to enterprise security.
Exploits could lead to unauthorized access, data breaches, and significant disruption of business operations. This vulnerability, coupled with the broad deployment of XP SP2 across corporate environments, made the potential for widespread compromise of corporate networks a very real concern. Organizations faced the difficult task of mitigating these risks while maintaining their existing infrastructure.
Enterprise Security Measures Adopted
Enterprises responded to the security concerns surrounding Windows XP SP2 by implementing a variety of security measures. This proactive approach was essential to minimize the impact of potential attacks. These measures focused on both preventive and reactive strategies. A robust security strategy involved more than just patching; it required a multi-layered approach to defense.
Security Protocols Implemented by Enterprises
Implementing robust security protocols was paramount to mitigating the risks. A multi-faceted approach involved several key components:
- Firewall Deployment: Firewalls were strategically placed to monitor and control network traffic, acting as a barrier against unauthorized access. This involved configuring firewalls to block known malicious traffic patterns and suspicious IP addresses. A critical component of network security, firewalls effectively minimized the risk of exploitation from external sources.
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS systems were deployed to monitor network traffic for malicious activity. These systems detected and responded to intrusions in real-time, significantly enhancing the security posture of the enterprise. Real-time monitoring and threat response capabilities were crucial to maintain a secure network environment.
- Antivirus and Anti-malware Software: Comprehensive antivirus and anti-malware solutions were implemented to protect systems from known and emerging threats. Regular updates and scans were critical in combating evolving malware. These software solutions provided a crucial layer of defense against a wide range of malicious software.
- User Account Control (UAC): Implementing UAC restricted the level of access that users had to system resources. This significantly reduced the impact of any successful exploits by limiting the potential damage that a compromised account could cause. This security measure prevented malware from gaining administrator privileges, a common tactic used by attackers.
- Regular Security Audits and Vulnerability Assessments: Regular security audits and vulnerability assessments were performed to identify and address potential security weaknesses. These proactive measures ensured that security protocols remained up-to-date and effective. This proactive approach involved regular checks of security protocols and software.
Security Protocol Implementation Details
| Security Protocol | Description | Implementation Details |
|---|---|---|
| Firewall | Controls network traffic, blocking unauthorized access. | Configuration to block known malicious traffic patterns and suspicious IP addresses. |
| IDS/IPS | Monitors network traffic for malicious activity. | Real-time monitoring and response to intrusions. |
| Antivirus/Anti-malware | Protects systems from known and emerging threats. | Regular updates, scans, and proactive threat analysis. |
| UAC | Limits user access to system resources. | Restricting access to system files and settings. |
| Security Audits/Vulnerability Assessments | Identify and address potential security weaknesses. | Regular testing, patching, and configuration adjustments. |
Legacy Systems and Security
Maintaining the security of older operating systems, especially those that have reached end-of-life support, presents significant challenges. Organizations often face pressure to keep systems running for operational reasons, but the absence of security updates and patches leaves these systems vulnerable to known and emerging threats. This vulnerability, coupled with the difficulty of updating these systems, necessitates proactive mitigation strategies to safeguard sensitive data and systems.Organizations often face a dilemma when dealing with legacy systems.
The desire to maintain operations with familiar software and infrastructure may conflict with the need to ensure security. These conflicts arise from the inherent limitations of older systems and the evolving nature of cyber threats.
Challenges of Maintaining Security on Legacy Systems
Legacy systems, like Windows XP SP2, present numerous security challenges. They often lack the advanced security features found in modern operating systems, making them susceptible to exploits. The absence of regular security updates means that known vulnerabilities are not patched, creating avenues for attackers to exploit weaknesses. Furthermore, the limited support from vendors and the difficulty in finding qualified personnel to manage these systems exacerbates the situation.
Examples of Organizations Still Relying on Windows XP SP2
Small businesses, particularly those in rural areas or with limited IT resources, may still rely on Windows XP SP2. The cost of upgrading to newer operating systems, along with the lack of understanding or training on new systems, can be significant barriers. Furthermore, some legacy applications may not be compatible with newer operating systems, making the transition even more difficult.
Risks Associated with Keeping Legacy Systems Unpatched
Keeping legacy systems unpatched exposes organizations to a range of risks. The most critical risk is the potential for successful attacks that can lead to data breaches, financial losses, and reputational damage. Furthermore, malware infections can cripple operations, leading to significant downtime and productivity losses. The vulnerability of these systems also makes them attractive targets for advanced persistent threats (APTs) that can exploit known or unknown vulnerabilities for long-term infiltration.
Approaches to Mitigating Risks in Organizations Using Legacy Systems
Several approaches can mitigate the risks associated with legacy systems. Implementing robust network security measures, including firewalls and intrusion detection systems, can limit the potential impact of successful attacks. Regular vulnerability assessments and penetration testing can identify potential weaknesses before they are exploited. Implementing strong access controls and user authentication measures can further reduce the risk of unauthorized access.
Training employees on security best practices is crucial, especially when dealing with legacy systems that might have different user interfaces and security protocols compared to newer systems. Finally, implementing a phased approach to system upgrades, combined with appropriate risk assessments and budgeting, can enable a gradual transition to newer, more secure systems.
Comparison with Modern Security Standards
Windows XP SP2, while a significant improvement over earlier versions, represents a vastly different security landscape compared to modern operating systems. The evolving threat landscape, coupled with the rapid advancement of computing technologies, has necessitated a fundamental shift in security paradigms. The foundational security mechanisms and patching strategies of XP SP2 are starkly contrasted with the layered defenses and continuous updates employed by contemporary systems.
Windows XP Service Pack 2 was under intense security scrutiny, a common theme in the early 2000s. Interestingly, around the same time, the Psion Netbook Pro, a device that once promised a powerful epoc-based platform, surprisingly made a switch to Windows CE. This move, detailed in this insightful article about psions netbook pro abandons epoc in favor of windows ce , highlights the evolving landscape of operating systems and the ever-present need for robust security in the face of rapidly changing technology.
Ultimately, the security concerns surrounding Windows XP Service Pack 2 highlight the ongoing challenges of keeping pace with emerging threats.
Advancements in Security Technologies
Modern operating systems leverage a far more comprehensive suite of security technologies. These include advanced intrusion detection and prevention systems, more sophisticated access control mechanisms, and a robust ecosystem of security tools, including anti-virus and anti-malware software. This layered approach significantly reduces attack surface and provides more granular control over user permissions.
Evolution of Threat Models
The threat landscape has dramatically evolved since the release of Windows XP SP2. Phishing attacks, ransomware, and sophisticated targeted attacks are now commonplace. The threat models of the past, focusing primarily on traditional viruses and worms, have been replaced by more complex and targeted campaigns. This evolution necessitates constant adaptation and improvements in security infrastructure. Modern threat models also incorporate social engineering, exploiting vulnerabilities in human behavior, as well as sophisticated techniques like zero-day exploits.
Continuous updates are crucial to address these evolving threats.
Security Features and Practices Comparison
| Feature | Windows XP SP2 | Modern Operating Systems (e.g., Windows 11) |
|---|---|---|
| Firewall | Basic firewall included, but less comprehensive than modern counterparts. | Robust, integrated firewall with advanced filtering and configuration options. Often includes application-level controls and real-time monitoring. |
| Antivirus | Reliance on third-party antivirus solutions was common. Real-time protection was not as pervasive. | Built-in antivirus and anti-malware engines with constant updates, threat intelligence feeds, and proactive protection. |
| Security Updates | Patches were released, but the frequency and scope were limited compared to modern systems. | Continuous security updates are delivered via automatic updates, patching vulnerabilities as they emerge. This constant patching is vital in modern systems. |
| User Account Control (UAC) | Limited user account controls. | Advanced UAC controls restrict unauthorized access to critical system resources. Elevation of privileges is carefully managed. |
| Data Encryption | Limited built-in encryption options. | Built-in encryption capabilities, like BitLocker for data protection. |
| Hardware Security | Limited hardware security features. | Modern hardware often incorporates security features like Trusted Platform Modules (TPMs) for enhanced security. |
This table highlights the significant advancements in security features and practices across different operating systems. The shift from basic security measures to a multi-layered, proactive approach reflects the evolution of the threat landscape and the increasing sophistication of cyberattacks.
Continuous Updates and Patching
A key difference lies in the approach to security updates. Windows XP SP2 relied on periodic releases of service packs. Modern operating systems embrace a continuous patching model, delivering updates and security patches frequently to address emerging threats. This proactive approach minimizes the window of vulnerability.
“Continuous updates are essential to maintain security in a dynamic threat landscape.”
This is a direct response to the constantly evolving nature of malware and cyberattacks. The frequent updates reflect a more sophisticated understanding of security. The proactive approach is a key component of modern systems’ robust security.
Lessons Learned from Windows XP SP2 Security
The security scrutiny surrounding Windows XP Service Pack 2 (SP2) offered a valuable, albeit painful, learning experience. While SP2 addressed many vulnerabilities, the experience underscored the continuous nature of the threat landscape and the critical importance of proactive security measures. The fallout from the exposed weaknesses provided valuable insights into the essential elements of a robust security posture.
Timely Updates and Security Awareness
The widespread exploitation of vulnerabilities in Windows XP SP2 highlighted the critical need for timely updates and security awareness among users. The failure to install critical security patches left systems vulnerable to attacks. This experience underscored the need for proactive measures to keep systems up-to-date and for users to be educated on the importance of these updates. A lack of awareness, coupled with inaction on security advisories, contributed significantly to the security breaches.
Proactive Security Measures
The security issues surrounding Windows XP SP2 emphasized the necessity of proactive security measures. These measures extend beyond just installing patches; they encompass a comprehensive approach to system hardening, including strong passwords, robust access controls, and regular security audits. The proactive approach emphasizes the importance of preventing vulnerabilities rather than just reacting to them. Failure to implement proactive measures can leave systems vulnerable to exploitation, even with the latest patches.
Best Practices for Security Maintenance in Operating Systems
Maintaining a secure operating system requires a multifaceted approach. Regular security audits are vital to identify potential weaknesses in system configurations. Using strong, unique passwords for accounts and employing robust access controls are essential security best practices. Implementing robust firewalls and intrusion detection systems are crucial to monitor network traffic and detect suspicious activities. Regular backups, coupled with a well-defined disaster recovery plan, are essential to minimize the impact of security breaches and ensure business continuity.
Final Thoughts: Windows Xp Service Pack 2 Under Heavy Security Scrutiny
In conclusion, the security scrutiny surrounding Windows XP Service Pack 2 offers valuable lessons about maintaining security in legacy systems. The vulnerabilities exposed during this period underscore the ever-evolving nature of cyber threats and the critical role of proactive security measures. This exploration not only provides a historical context but also highlights the need for continuous updates and security awareness in modern systems.