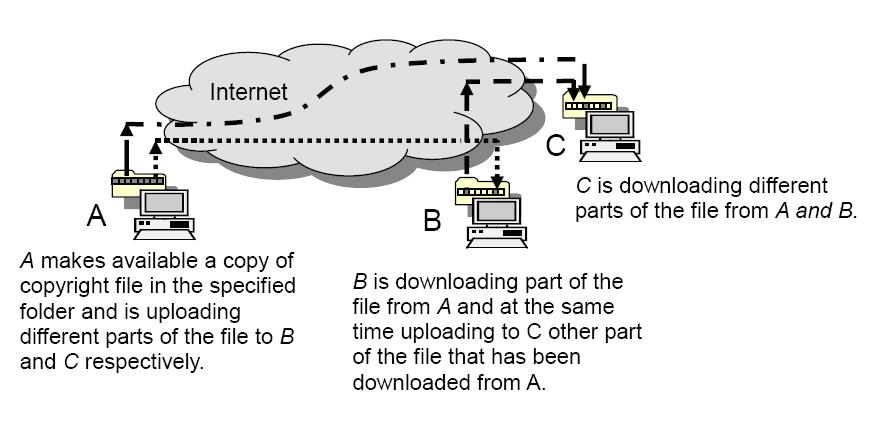
Beyond File Sharing P2P Radio Arrives
Beyond file sharing p2p radio arrives – Beyond file sharing, P2P radio arrives, promising a revolutionary shift in how we communicate and share information. This technology, built on the foundation of peer-to-peer networks, transcends the limitations of traditional broadcasting methods, offering unprecedented potential for real-time communication and collaborative projects. Imagine a world where content is delivered instantly and efficiently, not reliant on centralized servers. This new paradigm opens doors to a vast array of possibilities, pushing the boundaries of what’s possible in information sharing.
This in-depth exploration dives into the technical intricacies of P2P radio, contrasting it with traditional file-sharing methods like BitTorrent. We’ll examine the strengths and weaknesses of various P2P protocols, the security considerations, and potential applications beyond simple file exchange. From content delivery to real-time collaboration, we’ll uncover the fascinating possibilities that this emerging technology unlocks. The discussion will also touch upon the challenges and limitations of scaling P2P radio networks and ensuring their stability.
P2P Radio Technology Overview
Peer-to-peer (P2P) radio represents a revolutionary approach to broadcasting, shifting from a centralized model to a distributed network. This decentralized architecture allows for enhanced resilience, scalability, and potential cost-effectiveness compared to traditional broadcasting methods. This model empowers users to participate actively in the radio ecosystem, enabling a more dynamic and interactive listening experience.P2P radio leverages the inherent strengths of decentralized networks, where multiple participants act as both content providers and recipients.
This inherent distribution eliminates the need for a central server, allowing for a more robust and resilient system capable of withstanding failures or censorship attempts. This distributed nature also fosters a sense of community among participants, potentially leading to a more diverse and engaging listening experience.
Fundamental Principles of P2P Radio
P2P radio fundamentally relies on the concept of distributed communication. Instead of a single broadcaster transmitting to numerous listeners, multiple participants exchange audio data directly. This process involves identifying available peers, establishing connections, and coordinating the transmission and reception of audio streams. The inherent distributed nature of P2P networks offers several advantages over traditional broadcasting models.
P2P Radio Protocols
Various protocols have been developed to facilitate the operation of P2P radio. These protocols often differ in their approach to discovery, routing, and quality of service (QoS). Some popular protocols include protocols based on DHT (distributed hash tables) for efficient content searching and delivery, and others that rely on overlay networks for peer-to-peer communication. Each protocol has unique strengths and weaknesses that affect the performance and characteristics of the radio network.
Technical Aspects of P2P Radio
Signal transmission in P2P radio is significantly different from traditional broadcasting. Peers dynamically negotiate and establish connections to exchange audio streams. This dynamic connection management requires sophisticated algorithms to handle fluctuations in network connectivity and participant availability. Bandwidth management is crucial for efficient resource allocation in P2P radio environments. Efficient algorithms are essential to prevent congestion and ensure a consistent listening experience for all participants.
Sophisticated error correction mechanisms are necessary to mitigate data loss or corruption that might occur during transmission across the distributed network.
Comparison with Traditional Broadcasting
| Feature | P2P Radio | Traditional Broadcasting |
|---|---|---|
| Content Source | Multiple peers | Centralized station |
| Infrastructure | Decentralized network | Centralized broadcasting tower and infrastructure |
| Scalability | Highly scalable due to distributed nature | Limited by the capacity of the broadcasting infrastructure |
| Resilience | Robust against single points of failure | Vulnerable to disruptions in the centralized infrastructure |
| Cost | Potentially lower operational cost | High operational cost due to infrastructure maintenance |
| Interactivity | High level of user participation | Limited user interaction |
Traditional broadcasting models, reliant on a central source, are susceptible to disruptions and often face limited scalability. In contrast, P2P radio, distributed among numerous peers, offers a more resilient and scalable platform. This table clearly illustrates the key differences between the two methods of broadcasting.
Beyond File Sharing
Peer-to-peer (P2P) technology, initially popularized for file sharing, holds significant potential for a wider range of applications. Its decentralized nature, inherent resilience, and ability to leverage the collective resources of numerous users offer unique advantages over traditional client-server models. This exploration delves into how P2P radio can transcend its initial file-sharing roots and embrace a broader spectrum of functionalities.P2P radio, leveraging the strengths of P2P architecture, allows for the creation of a dynamic and adaptable communication network.
This network can distribute information and resources more efficiently, fostering a more resilient and responsive platform for a variety of applications. This distributed nature allows for greater flexibility and scalability, potentially opening doors to applications beyond the current paradigm of file sharing.
Novel Applications of P2P Radio
P2P radio extends beyond its initial file-sharing purpose, enabling real-time communication, collaborative projects, and efficient content delivery. This shift highlights the technology’s adaptability and its potential to revolutionize how we interact with information and each other.
Real-time Communication
P2P radio can facilitate real-time communication channels, allowing for more interactive and responsive experiences. This decentralized communication approach can prove advantageous in situations where a central server is unavailable or unreliable, such as in disaster relief efforts or remote areas. The network’s distributed nature makes it more resilient to outages and censorship.
Collaborative Projects
P2P radio can be a powerful tool for collaborative projects, enabling simultaneous access and editing of shared data. This shared resource model allows participants to contribute and collaborate effectively, fostering a more dynamic and interactive workflow. Imagine multiple engineers simultaneously editing a shared blueprint, with immediate feedback and updates for all involved.
Content Delivery
P2P radio can offer a more efficient and robust method for content delivery. This method can overcome the limitations of centralized servers by distributing content across a network of users. This decentralized model offers increased resilience to attacks and censorship. Content is delivered faster and more efficiently as it is spread throughout the network.
Potential Applications for P2P Radio
- Disaster Relief Communication: P2P radio can provide critical communication channels in disaster zones where traditional infrastructure is damaged or unavailable, facilitating coordination and resource allocation. This ensures rapid dissemination of information and support.
- Remote Healthcare: P2P radio can facilitate remote medical consultations and patient monitoring, providing real-time data exchange and enabling quicker diagnosis and treatment, especially in underserved areas.
- Educational Platforms: P2P radio can create a dynamic learning environment by allowing students to share resources and collaborate on projects, fostering a more interactive and engaging educational experience.
- Scientific Research: P2P radio can facilitate data sharing and analysis among researchers, promoting quicker breakthroughs and discoveries in areas like astronomy or environmental science. Data analysis can be distributed among many users.
- Public Safety Networks: P2P radio can provide a resilient and secure communication channel for emergency services, allowing for immediate and broad communication in times of crisis.
Advantages and Disadvantages of P2P Radio
| Application | Advantages | Disadvantages |
|---|---|---|
| Real-time Communication | Resilient, decentralized, interactive | Potential for network congestion, security concerns |
| Collaborative Projects | Real-time collaboration, distributed resources | Complexity in managing access and permissions, potential for conflicts |
| Content Delivery | Faster delivery, resilient to attacks, decentralized | Requires significant user participation, potential for bandwidth limitations |
| Disaster Relief | Reliable communication in emergencies | Requires prior setup, user adoption |
P2P Radio vs. Traditional File Sharing
P2P radio, a relatively new paradigm in distributed communication, offers a compelling alternative to traditional file-sharing methods. This approach leverages the inherent advantages of peer-to-peer networks for real-time audio and potentially video streaming, creating a decentralized and robust platform. However, comparing it to established systems like BitTorrent reveals both similarities and crucial differences in functionality, speed, reliability, and security.
This exploration will delve into the contrasting characteristics of these technologies.Traditional file-sharing protocols and P2P radio, while both utilizing decentralized networks, differ significantly in their core functionalities. Traditional file-sharing methods, exemplified by BitTorrent, prioritize the rapid dissemination of large files. P2P radio, in contrast, emphasizes the real-time delivery of audio or video content, potentially with low latency requirements.
This fundamental difference dictates the technical infrastructure and design considerations for each system.
Data Transfer Speeds and Reliability
Traditional file-sharing methods, like BitTorrent, prioritize maximizing download speeds. They often employ sophisticated techniques to optimize the distribution of file chunks across a vast network of peers. This results in significantly faster download speeds for large files. However, the reliability of these systems is tied to the availability of active peers. If a critical node goes offline, it might affect the download process for other users.
P2P radio, focusing on real-time streaming, adopts a different approach to data delivery. It emphasizes maintaining consistent data flow, potentially sacrificing the extremely high speeds achievable by BitTorrent for the sake of uninterrupted playback. The reliability of P2P radio often hinges on the robustness of the underlying network and the number of active nodes participating in the stream.
Security Implications
Security is a paramount concern for both P2P radio and traditional file-sharing methods. Traditional file-sharing methods, like BitTorrent, are vulnerable to malicious actors who might introduce corrupted or harmful files into the network. This vulnerability is mitigated by careful peer verification and robust checksumming mechanisms. P2P radio systems, particularly in real-time applications, require even greater attention to security.
The potential for real-time manipulation or injection of malicious audio/video data requires sophisticated authentication and encryption mechanisms. Ensuring the integrity of the transmitted data and preventing unauthorized access is crucial.
Technical Specifications and Performance Metrics
| Feature | P2P Radio | Traditional File Sharing (e.g., BitTorrent) |
|---|---|---|
| Data Type | Audio/Video streams | Large files (e.g., movies, software) |
| Transfer Mode | Real-time, continuous | Asynchronous, intermittent |
| Data Integrity | Emphasis on consistent stream | Emphasis on complete file download |
| Speed | Dependent on network conditions and peer availability, potentially lower than BitTorrent for large files | High speed for large files under optimal conditions, but susceptible to interruptions |
| Reliability | Robust against individual peer failures | Susceptible to peer failures |
| Security | Requires strong authentication and encryption | Requires robust checksumming and peer verification |
Technical Infrastructure and Implementation
Building a Peer-to-Peer (P2P) radio network requires careful consideration of both hardware and software components. This infrastructure needs to support reliable communication and efficient data transfer among participating nodes. Furthermore, robust security measures are critical to protect the integrity of the system and user data.The practical implementation of a P2P radio network necessitates a phased approach, starting with establishing a basic network structure and gradually incorporating advanced features and security protocols.
This process demands careful planning and execution to ensure compatibility and interoperability between the various components.
Hardware Components
A P2P radio network relies on a distributed architecture, meaning no central server controls the flow of data. Each participating node acts as both a sender and a receiver. Crucial hardware components include:
- Radio Transceivers: These devices are essential for transmitting and receiving radio signals. Different types of transceivers cater to various frequency ranges, data rates, and power levels, impacting the network’s range and capacity. Factors like sensitivity and modulation techniques should be carefully evaluated to ensure reliable communication over the intended distances.
- Antennas: Proper antenna selection is vital. Antenna gain, impedance matching, and polarization must be aligned with the transceiver specifications to maximize signal strength and minimize interference. Antenna placement is also crucial for optimal signal reception and transmission.
- Microcontrollers or Embedded Systems: These are the brains of each node. They handle tasks such as signal processing, data encoding, and decoding, as well as communication protocols. The processing power of these units will affect the complexity of the network and the data types that can be transmitted.
- Power Sources: Depending on the deployment location and network size, portable power solutions or dedicated power systems are needed to ensure continuous operation of the radio nodes. Battery life and charging mechanisms need to be robust and reliable.
Software Components
The software components are equally crucial for managing communication and data exchange within the P2P radio network. They handle the logic and protocols that govern the interaction between nodes.
- Network Protocols: Specialized protocols are needed for efficient communication between nodes. These protocols may be custom-designed for the P2P radio network or based on existing standards. These protocols need to handle tasks such as routing, addressing, and error correction to ensure reliable communication across the network.
- Data Encoding and Decoding Algorithms: Appropriate algorithms need to be implemented to encode and decode data in a format suitable for radio transmission and reception. These algorithms must handle signal noise and interference, ensuring data integrity and error-free delivery.
- Security Protocols: Secure communication is paramount. Implementing encryption and authentication mechanisms is essential to protect the data transmitted within the P2P radio network.
- Node Management Software: Software applications are needed to control and monitor the nodes within the P2P radio network. These tools will allow for configuration, monitoring of network health, and management of user privileges.
Network Setup Steps
The initial setup of a basic P2P radio network involves these steps:
- Node Configuration: Each node is configured with its unique identifier, communication parameters, and security credentials.
- Initial Communication Tests: Nodes are tested to ensure they can successfully transmit and receive signals.
- Network Topology Setup: The network topology, defining the relationships between nodes, is established. This could be a star, mesh, or other structure. The optimal topology depends on the communication needs and the physical environment.
- Security Configuration: Encryption and authentication mechanisms are implemented to protect data confidentiality and integrity.
Security Measures
Ensuring the safety and integrity of P2P radio communication is crucial. Robust security measures are necessary to prevent unauthorized access, data interception, and tampering.
- Authentication: Mechanisms for verifying the identity of communicating nodes are essential.
- Encryption: Encrypting the transmitted data is critical to protecting the privacy of information.
- Access Control: Controlling access to the network based on user privileges is necessary to restrict unauthorized participation.
- Secure Channel Management: Using secure communication channels and protocols is paramount.
Network Topology Diagram
A typical P2P radio network topology often employs a mesh architecture. Each node is connected to multiple other nodes, enabling redundant communication paths. This provides robustness and fault tolerance.
Beyond file sharing, peer-to-peer radio is finally arriving, promising a more decentralized and potentially faster way to distribute audio content. This new approach could revolutionize how we access and share music, podcasts, and other audio streams. It’s fascinating to consider the potential applications, and the possibilities are almost endless, especially when paired with tools like sharp ships 3d notebook , allowing for more dynamic and interactive content creation.
Ultimately, this p2p radio will undoubtedly reshape how we consume and create audio, pushing the boundaries of what’s possible.
A mesh topology is a network architecture in which each node is connected to multiple other nodes, creating a network with multiple redundant paths. This provides a higher degree of fault tolerance and reliability compared to other topologies.
[Diagram Description: A diagram illustrating a mesh topology with multiple nodes interconnected by lines representing radio links. Each node is labeled, and arrows indicate the direction of communication. The diagram clearly shows the redundant paths and the potential for communication among all nodes.]
Content Delivery and Broadcasting Capabilities: Beyond File Sharing P2p Radio Arrives
P2P radio, unlike traditional broadcasting methods, offers a unique approach to content delivery, leveraging the collective resources of its users. This decentralized structure allows for the potential of significantly enhanced efficiency and accessibility, but also introduces specific challenges. Understanding these aspects is crucial for evaluating the true potential of P2P radio as a content delivery system.This section delves into how P2P radio can facilitate content delivery, comparing its efficiency with traditional methods, and examining its limitations.
P2P radio is finally emerging beyond simple file sharing, promising a whole new wave of possibilities. It’s fascinating to see this evolution, especially given the ongoing legal battles, like Microsoft’s recent court appearance regarding its aging antitrust case here. Hopefully, these legal hurdles won’t impede the exciting progress of this new generation of peer-to-peer communication. The future of P2P radio is looking bright.
It also contrasts P2P radio with cloud-based solutions, highlighting the advantages and disadvantages of each approach.
Content Delivery Mechanisms
P2P radio’s content delivery relies on users acting as both content providers and recipients. A user sharing a broadcast stream becomes a “node” in the network, simultaneously disseminating and receiving content. This peer-to-peer architecture allows for dynamic and adaptive content distribution, circumventing the need for a central server. Content can be streamed directly from one user to another, without intermediary infrastructure.
This can lead to significant improvements in speed and responsiveness, particularly in areas with limited or unreliable internet connectivity.
Efficiency Gains Compared to Traditional Broadcasting
Traditional broadcasting methods rely on a central source broadcasting to numerous recipients. This centralized structure has inherent limitations in terms of scalability and responsiveness. P2P radio offers a more distributed approach. By leveraging the bandwidth of numerous users, P2P radio potentially delivers content more efficiently, especially in scenarios with high demand or limited infrastructure. The decentralized nature of the system allows for more dynamic adjustments to user demands and network conditions, potentially leading to improved latency and reduced congestion.
Challenges and Limitations
Several challenges hinder the widespread adoption of P2P radio for content delivery. Maintaining quality and consistency across various user connections is crucial. Maintaining a reliable network requires addressing issues such as fluctuating bandwidth, unreliable connections, and inconsistent user participation. The distributed nature of the system also necessitates effective mechanisms for managing and distributing metadata (e.g., track information, artist details).
Furthermore, ensuring content integrity and preventing unauthorized distribution is an ongoing concern.
Comparison with Cloud-Based Solutions
Cloud-based solutions rely on a centralized infrastructure for content storage and distribution. This model offers high scalability and reliability, but often comes with latency and dependence on a stable network connection. P2P radio, on the other hand, offers potential for lower latency and increased resilience in areas with limited or unstable internet access. However, cloud-based systems excel in providing a stable, consistent, and readily accessible platform for content.
The choice between P2P radio and cloud-based solutions depends heavily on the specific use case, network conditions, and desired characteristics of the content delivery system.
Scalability and Network Management
P2P radio, unlike centralized broadcasting, relies on the collective resources of participating users. This inherent distributed nature presents both exciting opportunities and significant challenges in terms of scalability and management. Understanding how to effectively manage a network of dynamically changing nodes is crucial for maintaining a stable and performant system, particularly as the user base expands.Managing a distributed network involves more than simply adding more users.
It requires strategies to optimize resource allocation, handle network congestion, and ensure quality of service remains high. The design and implementation of appropriate mechanisms for these aspects directly impact the usability and overall success of the P2P radio platform.
User Density and Network Congestion
Managing the increasing number of users in a P2P radio network is a significant challenge. As more users join, the network’s overall bandwidth and processing capacity are stretched. This can lead to congestion, resulting in degraded audio quality, dropped connections, and increased latency. Properly designed protocols and strategies for handling increased user load are essential.
Addressing Network Congestion
Several methods can mitigate congestion in a P2P radio network. One crucial approach is implementing dynamic routing algorithms that adapt to changing network conditions. These algorithms adjust data paths in real-time, directing traffic efficiently to minimize congestion points. Furthermore, adaptive bitrate streaming can dynamically adjust the transmission rate based on network conditions. If the network is overloaded, the stream quality is reduced to maintain stability.
Beyond simple file sharing, peer-to-peer (P2P) radio is emerging. This exciting development signifies a new era in internet communication, and it’s directly influenced by recent breakthroughs in internet protocols, like those developed by scientists. Check out this fascinating research on scientists develop breakthrough internet protocol to see how these advancements pave the way for more efficient and innovative P2P systems, pushing the boundaries of what’s possible in data transmission.
P2P radio promises a future beyond simple file transfers.
Quality of Service (QoS) and Prioritization
Ensuring consistent quality of service is critical for a positive user experience. QoS mechanisms are essential for prioritizing audio streams, guaranteeing a minimum bandwidth allocation for critical data, and managing the flow of data to prevent congestion. Prioritizing streams based on factors like user contribution or established connections helps maintain a stable and responsive environment for all users.
Network Stability and Maintenance
Maintaining network stability under heavy load requires proactive monitoring and maintenance. Regular network diagnostics are essential for identifying potential bottlenecks and performance issues. Continuous monitoring tools can track key metrics like bandwidth utilization, latency, and packet loss, allowing administrators to intervene proactively before issues escalate. Moreover, efficient error handling and robust protocols for connection recovery are essential for maintaining a stable environment.
Scalability Strategies
Several strategies can enhance the scalability of P2P radio networks. One effective method is implementing a hierarchical network structure. This involves dividing the network into smaller, manageable clusters, allowing for more targeted routing and resource allocation. Additionally, employing caching mechanisms can reduce the load on the network by storing frequently accessed content locally. This approach decreases the demand on the network’s core components, thereby improving overall performance and stability.
Security and Privacy Concerns
P2P radio, while offering exciting possibilities for decentralized communication, raises crucial security and privacy concerns. These concerns stem from the very nature of peer-to-peer networks, where multiple untrusted entities participate in the communication process. Understanding these vulnerabilities and implementing robust security measures are essential for the responsible development and deployment of P2P radio technology.The decentralized nature of P2P radio networks can make it difficult to enforce security policies and track malicious activity.
This lack of central control can potentially lead to vulnerabilities that traditional centralized systems might not face. Furthermore, the very essence of P2P relies on the trustworthiness of individual nodes, making it susceptible to various forms of attacks, from simple eavesdropping to more sophisticated malicious interventions.
Vulnerabilities of P2P Radio Networks
P2P radio networks are inherently vulnerable to a range of attacks. These vulnerabilities are often tied to the distributed and decentralized architecture. Nodes participating in the network may be compromised or intentionally malicious, leading to a breakdown of trust and security.
- Eavesdropping: Unauthorized access to radio communications is a significant threat. Malicious actors can potentially intercept and decode transmitted data, compromising sensitive information.
- Man-in-the-Middle Attacks: An attacker can insert themselves into the communication channel between two legitimate nodes, intercepting and potentially modifying data in transit. This poses a serious risk to the confidentiality and integrity of communications.
- Denial-of-Service Attacks: Malicious actors can overload the network with traffic, disrupting service for legitimate users. This can be particularly damaging to a P2P radio network that relies on distributed processing and resource sharing.
- Spoofing: Attackers can impersonate legitimate nodes, sending false information or manipulating communication flows. This can lead to the dissemination of misinformation or the hijacking of communication channels.
Protecting P2P Radio Communications, Beyond file sharing p2p radio arrives
Robust security measures are essential to mitigate the risks associated with P2P radio networks. These measures should address the specific vulnerabilities inherent in this type of architecture.
- Encryption: Employing strong encryption protocols is crucial for protecting the confidentiality of P2P radio communications. End-to-end encryption ensures that only authorized parties can access the transmitted data, effectively preventing eavesdropping and man-in-the-middle attacks. Examples include AES (Advanced Encryption Standard) and TLS (Transport Layer Security).
- Authentication Mechanisms: Implementing strong authentication methods ensures that only authorized nodes can participate in the network. This helps prevent spoofing attacks and ensures that only legitimate users can access the network. This can include digital signatures, certificates, and other cryptographic techniques.
- Network Segmentation: Dividing the network into smaller, isolated segments can limit the impact of a security breach. This compartmentalization restricts the spread of malicious activity and protects other parts of the network.
- Regular Security Audits and Maintenance: Proactive security audits and maintenance procedures are essential to identify and address vulnerabilities. This includes continuous monitoring of network traffic, analysis of logs, and regular security updates to patch vulnerabilities.
Encryption Techniques for Secure P2P Radio Communication
Various encryption techniques can be used to enhance the security of P2P radio communication. These techniques must be carefully chosen to balance security with performance.
- Symmetric-key Encryption: Using the same key for encryption and decryption, this method is relatively fast but requires a secure method for key exchange between communicating parties. Examples include AES (Advanced Encryption Standard).
- Asymmetric-key Encryption: Using different keys for encryption and decryption, this method allows for secure key exchange. Public keys are widely distributed, while private keys are kept secret. Examples include RSA (Rivest–Shamir–Adleman) and ECC (Elliptic Curve Cryptography).
- Hybrid Encryption: Combining both symmetric and asymmetric encryption techniques can leverage the strengths of both approaches. Asymmetric encryption is used for key exchange, while symmetric encryption is used for the bulk of the data transmission. This approach offers a good balance between security and performance.
Future Trends and Developments
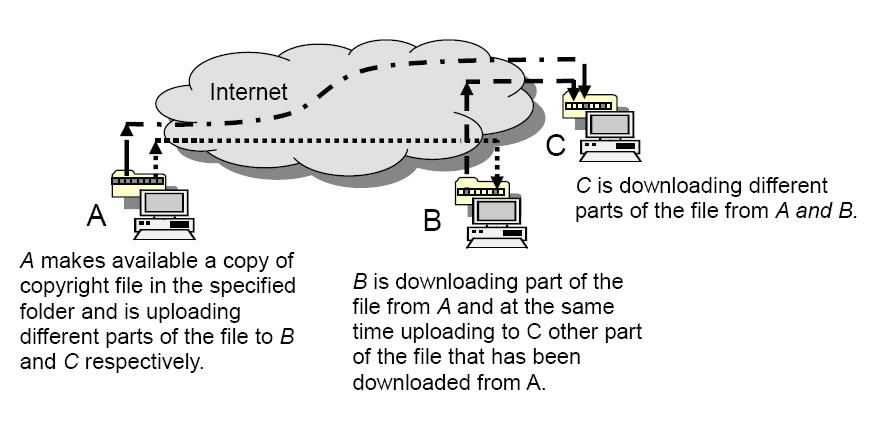
P2P radio, having evolved from its file-sharing roots, is poised for significant growth and adaptation. The technology’s inherent decentralization and potential for high-bandwidth content delivery are driving innovation in various sectors. This evolution extends beyond just improved file sharing protocols and explores new possibilities in broadcasting, streaming, and interactive experiences.Emerging trends in P2P radio systems are focused on enhancing the user experience, increasing efficiency, and exploring new applications.
These trends encompass aspects like improved security measures, more sophisticated content delivery mechanisms, and integration with other technologies. The potential for P2P radio to disrupt existing media models and create novel business opportunities is substantial.
Emerging Architectures and Protocols
P2P radio architectures are evolving beyond simple peer-to-peer file sharing. New protocols are being developed to optimize data transmission, manage network traffic, and enhance security. This shift reflects a need to address the challenges of scalability and maintain a robust and reliable network. Improved routing algorithms and adaptive protocols are crucial for seamless content delivery and management of the decentralized network.
For example, protocols leveraging blockchain technology for secure and transparent content distribution are being explored, potentially offering solutions to copyright infringement and content verification.
Content Delivery and Broadcasting Enhancements
The delivery and broadcasting capabilities of P2P radio are being refined. Real-time audio and video streaming are becoming increasingly important. New techniques for dynamic content adaptation are emerging, allowing for more efficient and adaptable content delivery based on user bandwidth and network conditions. These advancements will be crucial for applications requiring high-quality audio and video streams in diverse environments, including live events and educational broadcasts.
Advanced metadata tagging systems are also emerging to enable more sophisticated search and discovery capabilities for audio and video content.
Integration with Other Technologies
P2P radio systems are increasingly being integrated with other technologies, creating synergistic effects. Integration with social media platforms allows for the creation of interactive listening experiences, where users can engage with content and each other. Integration with location-based services could enable targeted broadcasts based on user location, fostering new opportunities in advertising and information dissemination. Furthermore, integration with smart devices, such as smart speakers and wearables, could create innovative personal listening experiences, allowing users to access content in new ways.
Scalability and Network Management Improvements
Scalability remains a key concern in P2P radio systems. New techniques for managing network traffic and peer discovery are being explored to ensure that the system can handle a growing number of users and content. Advanced load balancing algorithms and distributed caching strategies are being developed to improve performance and maintain responsiveness. The use of cloud-based infrastructure and distributed databases could significantly improve scalability, enabling efficient management of large-scale P2P radio networks.
Security and Privacy Enhancements
Robust security measures are critical for the success of P2P radio. Advanced encryption techniques and authentication protocols are being implemented to protect user data and prevent malicious activity. Addressing issues of anonymity and user privacy is crucial for creating a trustworthy and secure environment. The development of secure peer identification and authentication mechanisms is an important step in establishing user trust and preventing unauthorized access.
Utilizing blockchain-based security measures can create a more transparent and secure environment.
Outcome Summary
In conclusion, P2P radio, while still in its nascent stages, presents a compelling alternative to traditional broadcasting and file-sharing models. Its potential to revolutionize content delivery and real-time communication is undeniable. While hurdles remain in terms of scalability and security, the potential benefits are significant. This emerging technology is poised to reshape how we interact with information and potentially transform industries from entertainment to education.
The future of P2P radio is bright, and we are only beginning to scratch the surface of its potential.