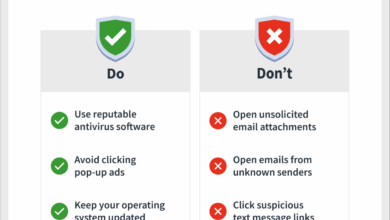
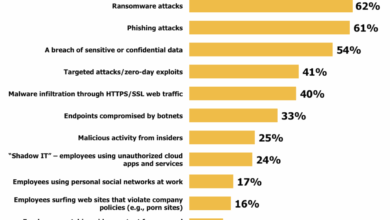
Upgrade and Archive Data Extinction
Upgrade and archive the ongoing threat of data extinction. Imagine a world where vital information, from medical records to financial transactions, vanishes without a trace. This isn’t science fiction; it’s a very real concern in today’s digitally-driven world. This post delves into the critical need to not only understand the risks of data extinction but also to develop and implement proactive strategies for preserving our digital heritage.
We’ll explore the various types of data susceptible to loss, from structured databases to unstructured files, and examine the devastating consequences of such events across diverse sectors. We’ll analyze the contributing factors, from technological failures to human error, and compare and contrast different data preservation methods. This journey will equip us with a practical understanding of how to upgrade and archive our data, ensuring its longevity and accessibility.
Defining Data Extinction
Data extinction, a looming threat in the digital age, signifies the irreversible loss of data beyond recovery. This isn’t merely about losing a file; it’s about the complete and permanent disappearance of information crucial to various sectors, potentially leading to significant societal and economic disruption. The consequences of data loss are far-reaching and require proactive strategies for preservation.Data extinction encompasses a range of scenarios, from accidental deletion to deliberate destruction, and encompasses various forms and causes.
It involves the irreversible loss of data, rendering it unrecoverable, and posing challenges to data recovery and preservation efforts. This issue affects numerous sectors, impacting decision-making processes, operational efficiency, and trust.
Defining Data Extinction
Data extinction is not simply the loss of a few files. It’s the complete and permanent disappearance of data, making it impossible to retrieve or reconstruct. This phenomenon can result from various causes, including hardware failures, natural disasters, malicious attacks, and inadequate data management practices. The impact of data extinction can vary significantly depending on the type of data lost and the sector affected.
Protecting our digital heritage from vanishing is crucial. Upgrading and archiving the ongoing threat of data extinction is paramount, especially as neural network technology moves into the mainstream. These powerful systems, as detailed in neural network technology moves into the mainstream , offer exciting possibilities for data preservation and analysis, which can ultimately aid in tackling this crucial issue.
This could pave the way for a more robust and secure future for data storage.
Types of Data Susceptible to Extinction
Data comes in various formats, each susceptible to extinction. Structured data, such as databases and spreadsheets, is relatively easier to manage and restore if backups are available. Unstructured data, like images, videos, and emails, is more challenging to manage and preserve, and often requires specialized recovery methods. Metadata, which describes data, is also vulnerable to extinction, potentially rendering the associated data useless.
The complete loss of metadata can make the data almost impossible to understand or interpret, making it functionally extinct.
Protecting against data loss is crucial, and upgrading our systems to archive the ongoing threat of data extinction is paramount. Recent advancements in web services interoperability, like the boost toward standardization described in this article web services interoperability gets boost toward standardization , offer valuable opportunities for more resilient data management. This means we can build more robust and reliable systems to effectively upgrade and archive the data we need to protect.
Consequences of Data Loss for Different Sectors
The consequences of data extinction vary significantly across different sectors. In healthcare, the loss of patient records can lead to diagnostic errors, treatment complications, and legal issues. In finance, data loss can result in fraudulent transactions, operational disruptions, and reputational damage. In education, the loss of student records can affect academic progress and hinder educational continuity. These examples demonstrate the far-reaching impact of data extinction on various aspects of modern life.
Impact on Industries
| Industry | Impact of Data Extinction |
|---|---|
| Healthcare | Loss of patient records, leading to diagnostic errors, treatment complications, and legal issues. Inability to track medical history can impact treatment decisions. |
| Finance | Fraudulent transactions, operational disruptions, and reputational damage. Loss of financial records can impact accounting and auditing processes. |
| Education | Loss of student records, affecting academic progress and hindering educational continuity. Loss of research data can halt scientific advancements. |
| Government | Disruption of public services, impacting citizen access to information and administrative functions. Loss of legal records can cause legal disputes and issues. |
| Retail | Loss of customer data, impacting marketing campaigns and customer relationships. Loss of sales data can hinder inventory management and forecasting. |
Understanding the Threat
Data extinction, the irreversible loss of valuable information, is a growing concern in today’s interconnected world. This isn’t just about losing old photos or forgotten files; it’s about losing the historical record of human achievement, scientific discoveries, and cultural heritage. Recognizing the multifaceted nature of this threat is crucial to developing effective preservation strategies.The escalating loss of data is not a sudden phenomenon; rather, it’s a gradual erosion driven by various factors, from technological obsolescence to deliberate acts of destruction.
Protecting our digital heritage from potential data loss is crucial. Upgrading storage systems and archiving data effectively is vital to combat the ongoing threat of data extinction. Recent developments like Transmeta’s new astro chip could revolutionize data storage and backup solutions. Transmeta readies new astro chip potentially offering enhanced speed and security, which would greatly assist in the upgrade and archive processes.
Ultimately, proactive measures like these are essential for safeguarding the vast amount of information we rely on.
Understanding these contributing elements is essential for proactively mitigating the risks.
Major Contributing Factors to Data Extinction
Several factors contribute to the ongoing threat of data extinction. These range from preventable human errors to unforeseen natural calamities and the ever-evolving nature of technology. Understanding these factors is paramount to developing effective countermeasures.
- Technological Failures: The rapid advancement of technology often leads to obsolescence. Hardware and software become outdated, rendering data stored on those systems inaccessible. The constant evolution of digital formats and storage mediums means that older data can become increasingly difficult to retrieve or even interpret as technology changes. Migration strategies are often expensive and complex.
- Human Error: Accidental deletion, improper backups, and inadequate security protocols are all common causes of data loss. Data mismanagement and poor documentation practices can lead to the inability to access or understand data in the future.
- Natural Disasters: Natural events such as floods, fires, earthquakes, and other calamities can devastate physical data storage facilities, resulting in the irreversible loss of crucial information. Geographic locations with high risk of these events pose significant challenges to data preservation.
- Malicious Acts: Deliberate data destruction, whether through cyberattacks or physical sabotage, can lead to significant data loss. Data security and access control measures must be continuously updated to prevent and deter such malicious acts. Data backups and redundancy in geographically diverse locations are essential for protection.
Comparison of Data Preservation Approaches
Various strategies are employed to preserve data. Choosing the most effective approach depends on the type of data, its value, and the resources available. A thorough analysis of the available options is critical.
- Digital Archiving: This involves storing data in digital formats that are expected to be compatible with future technology. However, ensuring long-term compatibility and avoiding obsolescence requires careful consideration of future technology. Migration to new formats is essential to maintain accessibility.
- Physical Archiving: This approach involves preserving data on physical media, such as hard drives, magnetic tapes, or microfilm. Maintaining environmental control and managing the physical storage itself presents a challenge. Physical media can be susceptible to degradation over time.
- Redundancy and Replication: Creating multiple copies of data and storing them in different locations helps mitigate the risk of data loss from any single event. This involves careful consideration of storage locations and security protocols.
- Data Migration and Format Conversion: The transition of data from one format to another, or from one storage system to another, is a crucial part of long-term preservation. Understanding the limitations of current and future technologies is essential.
Escalating Nature of the Threat
The threat of data extinction is escalating due to the exponential growth of data volume and the increasing interconnectedness of systems. The rate of data generation is rapidly outpacing our capacity to preserve it. Developing proactive strategies is crucial.
- Exponential Data Growth: The ever-increasing volume of data generated daily creates an immense burden on preservation efforts. Data management systems must be scalable and resilient to cope with this rapid increase.
- Interconnected Systems: The dependence on interconnected systems for various operations means a failure in one area can potentially affect many others. The cascading effect of a data loss can have wide-ranging consequences.
- Technological Advancements: Rapid advancements in technology are creating obsolescence in current data formats and storage systems. This creates a constant need for data migration and format conversion.
Historical Data Extinction Events
Throughout history, numerous instances of data loss have had significant consequences. Recognizing past events is crucial to understanding the present threat.
- The Library of Alexandria: The destruction of this ancient library marked a significant loss of knowledge and cultural heritage. This event serves as a cautionary tale about the fragility of data and the importance of preservation.
- The Great Fire of London: This historical event highlights the vulnerability of physical data storage to catastrophic events. The loss of records, documents, and information had lasting impacts on the city and beyond.
- The Dust Bowl: This environmental event, coupled with human mismanagement, led to significant agricultural losses and the loss of vital historical data. The event exemplifies the need for comprehensive data preservation strategies that encompass both technological and environmental factors.
Strategies for Upgrading Data Preservation
Data extinction, a looming threat to our collective knowledge and progress, demands proactive strategies for upgrading data preservation. Ignoring this threat could lead to irreversible loss of crucial information across various sectors, from scientific research to historical records and business operations. Robust data preservation strategies are not just about safeguarding existing data; they’re about ensuring future access and usability.Proactive measures to prevent data extinction require a multifaceted approach encompassing multiple layers of protection.
This includes employing cutting-edge technologies, establishing robust backup and recovery procedures, and implementing effective data redundancy and replication strategies. Understanding the inherent vulnerabilities of different storage mediums and technologies is crucial to building a resilient data infrastructure capable of withstanding unforeseen circumstances.
Data Backup and Recovery Strategies
Robust backup and recovery strategies are essential components of any data preservation plan. They ensure the ability to restore data in the event of catastrophic failures, accidental deletions, or malicious attacks. These strategies should encompass regular, automated backups, employing multiple backup locations to minimize the risk of total loss.
- Regular Automated Backups: Implementing scheduled backups ensures consistent data protection. This includes frequent snapshots of critical data to prevent data loss from unforeseen events. For example, a daily backup of a company’s database can mitigate the impact of a server failure by allowing the company to restore to the previous day’s state.
- Multiple Backup Locations: Storing backups in separate physical locations, ideally geographically dispersed, mitigates the risk of simultaneous disasters impacting all data copies. Offsite storage, cloud-based backups, or a combination of both significantly enhance data resilience. For instance, a company storing critical financial data in a secure offsite vault alongside cloud backups ensures redundancy and prevents loss in case of a local fire or natural disaster.
- Version Control and History: Maintaining historical versions of data allows for easy restoration to previous states. This is especially crucial for collaborative projects or documents that might undergo multiple revisions. This feature is commonly used in software development, where different versions of code are saved, allowing developers to easily revert to a previous working state.
Data Redundancy and Replication
Data redundancy and replication strategies create multiple copies of data, distributed across different locations. This approach enhances data availability and ensures business continuity in the event of a failure or disaster. Implementing these strategies is crucial for critical systems that need high availability, like online banking platforms or emergency services.
- Mirroring: Mirroring involves creating an exact copy of data on a separate system. This ensures instant availability of the data in case of a primary system failure. For example, a web server can mirror its content on a secondary server, enabling continued access to the website even if the primary server malfunctions.
- Data Replication: Data replication involves creating copies of data that are not necessarily identical but can be restored to the original state. This strategy is often used for disaster recovery purposes. A hospital’s patient records can be replicated to a remote server, enabling access to crucial information in the event of a local disaster.
Comparison of Data Storage Technologies
Different data storage technologies offer varying degrees of resilience and cost-effectiveness. Evaluating these technologies based on their reliability and potential for data loss is critical in choosing the most suitable solution for specific data preservation needs.
| Storage Technology | Resilience | Cost | Accessibility |
|---|---|---|---|
| Magnetic Tape | High | Low | Low |
| Hard Disk Drives (HDDs) | Moderate | Moderate | High |
| Solid State Drives (SSDs) | High | High | High |
| Cloud Storage | High (depending on provider) | Variable | High |
Archiving Existing Data
Preserving the wealth of information generated daily is crucial for future research, historical analysis, and societal progress. Archiving existing data streams is not just about storing; it’s about ensuring long-term accessibility and usability. This necessitates careful planning, the adoption of robust techniques, and the understanding of the various formats available. The ongoing threat of data extinction underscores the critical need for effective archiving strategies.
Importance of Archiving Ongoing Data Streams, Upgrade and archive the ongoing threat of data extinction
Ongoing data streams encompass everything from sensor readings in scientific research to financial transactions in business. These data streams represent a continuous flow of information, reflecting real-time events and trends. Their value extends far beyond their immediate use; they can provide valuable insights into past patterns, trends, and anomalies. Failure to archive these streams leads to irretrievable loss of potentially significant data.
Without proper archiving, vital information might be lost, hindering future analysis and discoveries.
Techniques for Long-Term Data Preservation and Accessibility
Data preservation extends beyond simply storing data. It involves ensuring its integrity, usability, and accessibility over extended periods. Techniques include data redundancy, employing multiple storage media and locations, and utilizing robust encryption to protect sensitive information. Regular backups and version control are also essential for maintaining a complete historical record. Data deduplication is vital to reduce storage space and enhance efficiency.
Use of Specialized Archival Systems and Protocols
Specialized archival systems are designed for long-term storage and retrieval. These systems often employ advanced compression techniques, redundant storage configurations, and robust access protocols to maintain data integrity. Specific protocols, such as checksums and cryptographic hashing, are used to detect and prevent data corruption. Cloud-based archival systems are increasingly utilized for their scalability and accessibility.
Different Formats for Archiving Data
Different data types necessitate tailored archival strategies. Structured data, such as databases and spreadsheets, can be archived using standard database management systems. Unstructured data, including text documents, images, and videos, requires more sophisticated approaches. Metadata is crucial for identifying, retrieving, and understanding the content of archived data. Properly tagging and indexing archived data are critical for searchability and usability.
- Structured Data: Databases, spreadsheets, and other structured data formats are typically archived using specialized database management systems or by converting them into formats compatible with archival systems. Metadata describing the data is essential for its retrieval and analysis.
- Unstructured Data: Images, audio, video, and text documents often require specialized archival systems that support these formats. Conversion to standardized formats is frequently necessary. Metadata about the data’s creation, context, and content is critical for retrieval and analysis.
- Metadata: Metadata is essential for managing and understanding archived data. Metadata elements include file creation dates, descriptions, s, and identifiers. Well-defined metadata standards are crucial for effective searching and retrieval.
Data Security and Disaster Recovery
Protecting data from unauthorized access and ensuring its availability in the face of unforeseen events is paramount for safeguarding its long-term preservation. Robust security measures and comprehensive disaster recovery plans are crucial for mitigating the risk of data loss and maintaining the integrity of our digital heritage. This section delves into strategies for enhancing data security and designing effective recovery procedures.
Data Security Measures
Data security encompasses a wide range of measures designed to prevent unauthorized access, modification, or destruction of data. These measures must be multifaceted and adaptable to evolving threats. Implementing strong access controls, robust encryption, and continuous monitoring is critical for preserving the confidentiality, integrity, and availability of data.
- Access Control Mechanisms: Implementing multi-factor authentication, role-based access controls, and least privilege principles are fundamental for restricting access to sensitive data. This minimizes the potential impact of a compromised account. For example, restricting access to specific data subsets based on user roles ensures that only authorized personnel can view or modify sensitive information.
- Data Encryption: Encrypting data both in transit and at rest is essential for safeguarding confidentiality. Advanced encryption standards, like AES-256, offer strong protection against unauthorized decryption. Implementing end-to-end encryption ensures that only authorized parties can access the data, even if the storage system is compromised.
- Regular Security Audits: Conducting regular security audits and penetration testing is crucial for identifying vulnerabilities and strengthening defenses. These audits help assess the effectiveness of current security protocols and pinpoint potential weaknesses. A regular review of security policies and practices helps ensure they remain relevant and effective in countering emerging threats.
Disaster Recovery Procedures
A well-defined disaster recovery plan is critical for restoring data and systems in the event of a catastrophic event. This plan must be comprehensive and address potential risks such as natural disasters, cyberattacks, and hardware failures.
- Data Backup and Replication: Establishing robust data backup and replication strategies is vital for data recovery. Regular backups should be stored offsite in a secure location, and replication strategies should ensure redundancy and availability. Implementing a tiered backup system that prioritizes data frequency and importance is a good practice to manage backup costs and recovery time objectives (RTO).
- Recovery Point Objective (RPO) and Recovery Time Objective (RTO): Defining clear RPOs and RTOs are essential for establishing recovery goals. RPOs specify the maximum amount of data loss acceptable after a disaster, and RTOs specify the maximum time allowed to restore systems and data. These metrics are critical for evaluating the effectiveness of the disaster recovery plan and for resource allocation.
- Testing and Validation: Regularly testing the disaster recovery plan is crucial for ensuring its effectiveness. This includes simulating various disaster scenarios to assess the response time and the ability to restore data and systems. This helps identify any gaps or weaknesses in the plan and refine it accordingly.
Security Protocols and Efficacy
Implementing appropriate security protocols is critical for maintaining data integrity and confidentiality. Different protocols address various security needs.
| Security Protocol | Efficacy | Description |
|---|---|---|
| Firewall | High | A firewall acts as a barrier between a network and the outside world, controlling incoming and outgoing traffic. This is a fundamental security layer that prevents unauthorized access. |
| Intrusion Detection/Prevention Systems (IDS/IPS) | High | IDS/IPS systems monitor network traffic for malicious activity. IPS systems actively block malicious traffic, while IDS systems alert administrators to suspicious activity. |
| Virtual Private Networks (VPNs) | High | VPNs encrypt data transmitted over public networks, enhancing confidentiality and integrity. This is crucial for secure remote access to sensitive data. |
Ethical Considerations

The preservation of data transcends mere technological concerns; it deeply impacts our ethical responsibilities towards individuals and society. Data extinction, the potential loss of critical information, carries profound implications that demand careful consideration of the values we hold dear. We must ask ourselves not just
- how* to preserve data, but
- why* and
- for whom*. This chapter delves into the ethical landscape surrounding data preservation, examining the intertwining of privacy, security, legal frameworks, and organizational responsibilities.
Ethical Implications of Data Extinction
Data extinction has far-reaching ethical consequences. Loss of historical records, personal documents, and crucial research data can lead to a loss of cultural heritage, impede scientific advancement, and erode trust in institutions. The erosion of personal identities and the inability to trace lineages or verify past experiences are just a few examples of the profound impact on individuals.
Data Privacy and Security in Preservation
Data privacy and security are paramount in the context of data preservation. Protecting sensitive information, ensuring confidentiality, and limiting access to authorized personnel are fundamental aspects of ethical data management. Robust encryption techniques, access controls, and regular security audits are crucial elements in safeguarding data from unauthorized access and misuse. Individuals and organizations have a moral obligation to handle data with the utmost care, respecting the inherent rights of data subjects.
Legal Frameworks Surrounding Data Ownership and Access
Legal frameworks play a vital role in defining data ownership and access rights. Data privacy laws, such as GDPR in Europe and CCPA in California, establish guidelines for collecting, using, and protecting personal data. Understanding these regulations is crucial for organizations and individuals to ensure compliance and maintain ethical data practices. Intellectual property rights and data ownership disputes are areas requiring careful consideration in the context of data preservation.
For example, the legal complexities around digital archives and the rights of creators to their work need careful consideration in the preservation process.
Responsibilities of Organizations in Data Protection and Archiving
Organizations bear significant responsibility for protecting and archiving data. This responsibility extends beyond legal compliance; it’s a moral obligation to maintain the integrity and accessibility of information vital to society. Organizations must establish clear policies and procedures for data preservation, ensuring data quality and integrity. Investment in robust data management systems, skilled personnel, and ongoing maintenance is essential to ensure the long-term preservation of data assets.
The principle of transparency regarding data handling practices should be paramount for building public trust.
Illustrative Examples
Data extinction, though a looming threat, isn’t purely theoretical. Real-world events, though not complete data loss, demonstrate the vulnerability of our digital archives and the critical need for proactive preservation strategies. Understanding these examples, and the procedures for recovery, is crucial for developing robust data protection plans.
Hypothetical Data Extinction Scenario
A catastrophic cyberattack targeting a global financial institution could result in the irreversible loss of crucial transaction records, customer data, and financial instruments. The ramifications would be severe, causing widespread economic disruption, reputational damage, and potentially legal repercussions. Recovery efforts would be immensely complex and time-consuming, requiring meticulous reconstruction of lost data and processes.
Data Restoration Procedures
Restoring data after a significant event necessitates a well-defined, multi-faceted approach. This includes utilizing robust backups, employing specialized recovery software, and engaging skilled data recovery professionals. Redundant backups in multiple secure locations are essential to mitigate the risk of data loss from localized disasters. Recovery protocols should be regularly tested and updated to ensure efficacy. Key steps include:
- Identifying the scope of data loss. This involves meticulous analysis to determine the extent of the damage and affected data types.
- Accessing and restoring backups. The recovery process begins with retrieving backups from secure storage locations. Restoration tools are crucial for this step.
- Verifying data integrity. Post-recovery, data validation is paramount to ensure accuracy and completeness.
- Implementing preventative measures. Lessons learned from the event must be incorporated into future data protection protocols to prevent similar incidents.
Successful Data Preservation Strategies
Several industries have implemented effective data preservation strategies. For instance, museums meticulously document and archive artifacts, employing digital imaging and preservation techniques to maintain historical records. Libraries use sophisticated cataloging systems and digital preservation strategies to safeguard valuable texts and knowledge.
Examples of Successful Data Preservation Projects
| Institution/Organization | Data Type | Preservation Strategy | Outcome |
|---|---|---|---|
| National Archives of the United Kingdom | Government documents | Microfilming, digitization, and archival storage | Preserved vast quantities of historical records |
| Smithsonian Institution | Cultural artifacts | Digital imaging, conservation techniques, and specialized storage | Safeguarded invaluable cultural heritage |
| NASA | Space exploration data | Redundant backups, secure data centers, and cloud storage | Preserved crucial data for scientific research and future missions |
Technological Advancements
The relentless march of technological innovation presents both challenges and opportunities for data preservation. Emerging technologies offer unprecedented avenues for enhancing data security and resilience, while also introducing new complexities. This section explores these advancements, focusing on their potential applications in safeguarding our digital heritage.Modern data preservation strategies need to adapt to the evolving technological landscape. This includes integrating emerging technologies like blockchain, cloud computing, and artificial intelligence to bolster data security and mitigate the risks of data loss.
Addressing these evolving challenges requires a proactive and adaptable approach.
Emerging Technologies Enhancing Data Preservation
Advancements in hardware and software are continuously transforming data storage and management. New methods for data encoding, encryption, and replication offer increased protection against threats. The integration of these advancements into existing systems is crucial for effective data preservation. For instance, advancements in magnetic storage density and memory technology enable greater data capacity at lower costs.
Potential Applications of Blockchain Technology in Data Security
Blockchain technology, renowned for its decentralized and immutable nature, presents compelling opportunities for data security. Its inherent cryptographic security and transparency can help verify data authenticity and integrity. Distributed ledger technology (DLT) facilitates the creation of tamper-proof records of data changes, thus strengthening the security posture. This can be applied to maintain a secure history of data modifications and versions.
For instance, recording each modification of a critical document on a blockchain ensures its integrity.
Benefits and Limitations of Cloud-Based Data Storage Solutions
Cloud-based data storage offers scalability, accessibility, and cost-effectiveness. Data is replicated across multiple servers, enhancing fault tolerance and resilience against disasters. Cloud providers often employ robust security measures, including encryption and access controls. However, reliance on third-party providers introduces potential security risks and privacy concerns. Furthermore, the inherent dependence on internet connectivity can be a drawback, especially in regions with unreliable network infrastructure.
Role of Artificial Intelligence in Predicting and Mitigating Data Loss
Artificial intelligence (AI) can be a powerful tool for predicting and mitigating data loss. AI algorithms can analyze historical data patterns and identify potential vulnerabilities. This proactive approach allows for the implementation of preventive measures, including automated backups and restoration protocols. AI can also detect anomalies and unusual activity that might signal impending data breaches or failures.
For example, AI can analyze sensor data from storage systems to predict potential hardware failures and trigger preventative actions.
Ending Remarks: Upgrade And Archive The Ongoing Threat Of Data Extinction
In conclusion, safeguarding our data is paramount in today’s interconnected world. The threat of data extinction is real and ever-evolving, demanding proactive measures for upgrading and archiving our data. By understanding the potential risks, implementing robust preservation strategies, and staying informed about emerging technologies, we can ensure the continuity and accessibility of our digital assets. This is not just about protecting information; it’s about safeguarding our future.