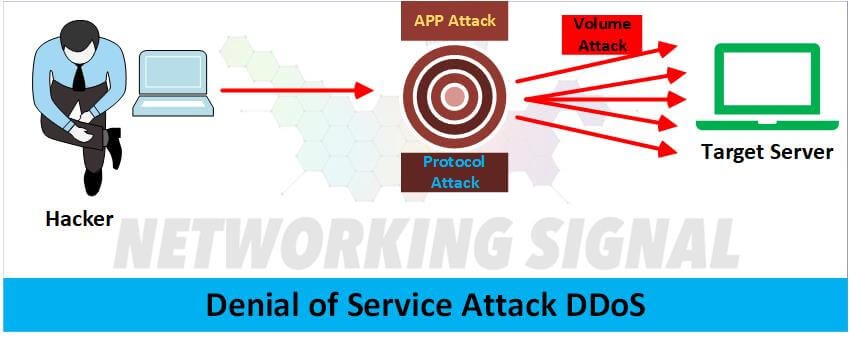
Denial of Service Exposed A Deep Dive
Denial of Service exposed: Understanding the vulnerabilities, impacts, and mitigations is crucial for any organization. This post delves into the intricacies of denial-of-service exposures, exploring everything from the fundamental definitions to real-world case studies. We’ll examine the difference between a denial-of-service attack and the concept of exposure, highlighting common methods and their impact. Prepare to gain insights into the tools and strategies needed to identify, mitigate, and prevent such threats.
From defining the core concept to examining real-world case studies, we’ll navigate the complexities of denial-of-service exposures. We’ll explore various attack types, their exposure vectors, and the potential consequences for businesses. The discussion will also include practical steps for detecting and responding to such incidents. This is a critical topic for anyone responsible for network security.
Defining Denial of Service Exposed

Denial-of-service (DoS) attacks aim to overwhelm a target system, preventing legitimate users from accessing its services. A “denial-of-service exposed” incident, however, focuses not on the attack itself, but on the vulnerabilities that allow an attacker to exploit and expose those weaknesses. It’s less about the act of disruption and more about the underlying weaknesses in the system’s architecture and security posture.The key difference between a standard DoS attack and a “denial-of-service exposed” incident lies in the focus.
A DoS attack is an active attempt to flood a system with malicious traffic. “Exposed” incidents are about vulnerabilities that have been identified but not remediated, leaving the system vulnerable to exploitation. This exposes the potential for a future DoS attack. The exposure is the state of being vulnerable, not the actual attack itself.
Recent revelations about denial-of-service attacks highlight the ongoing threat of cybercrime. Critically, the recent arrest of a suspect linked to the Blaster worm, and the ongoing investigation into the SoBig F virus writer, as detailed in this article feds nab blaster suspect continue tracking sobig f writer , demonstrates law enforcement’s commitment to tracking down those responsible for such attacks.
This ongoing pursuit underscores the need for stronger security measures to prevent future denial-of-service incidents.
Key Characteristics of a Denial-of-Service Exposed Incident
A denial-of-service exposed incident is characterized by identified vulnerabilities in a system’s infrastructure or applications that could be exploited to launch a DoS attack. These vulnerabilities often relate to network configurations, application logic, or inadequate resource allocation. They are a proactive security assessment that finds and highlights weaknesses, rather than the reactive nature of a direct attack.
Defining Exposure in the Context of DoS
Exposure in the context of denial-of-service is the state of vulnerability where a system or service is susceptible to a denial-of-service attack. This vulnerability is often a result of poor design, configuration, or lack of security controls. Exposure can be found in various components, from network infrastructure to application code. The exposure does not have to be exploited for an incident to exist.
Common Methods to Expose Denial-of-Service Vulnerabilities
Vulnerabilities are exposed through various methods, often involving security assessments and penetration testing. Penetration testing simulates real-world attacks to identify weaknesses. Vulnerability scanning tools can automatically detect potential issues in configurations or software. Network analysis and traffic monitoring tools help discover weaknesses in network protocols or design.
Comparison of DoS Attack Types and Exposure Vectors
| Attack Type | Exposure Vector | Description |
|---|---|---|
| SYN Flood | Network Configuration | A SYN flood attack exploits the TCP three-way handshake. Improperly configured firewalls or network devices might not be able to handle the overwhelming number of SYN requests, leading to exhaustion of system resources. |
| UDP Flood | Application Layer | UDP floods bombard a target with UDP packets. Vulnerable applications might not be able to handle the sheer volume of requests, leading to resource exhaustion and service disruption. |
| HTTP Flood | Application Logic | An HTTP flood exploits the resources of the web server by sending numerous HTTP requests. Insufficient rate limiting or buffering mechanisms can make a web server vulnerable to this attack. |
| Ping Flood | Network Configuration | A ping flood overwhelms a system with ICMP echo requests. Weaknesses in the network infrastructure or misconfigurations can allow this attack to overwhelm the target. |
Impact and Consequences: Denial Of Service Exposed
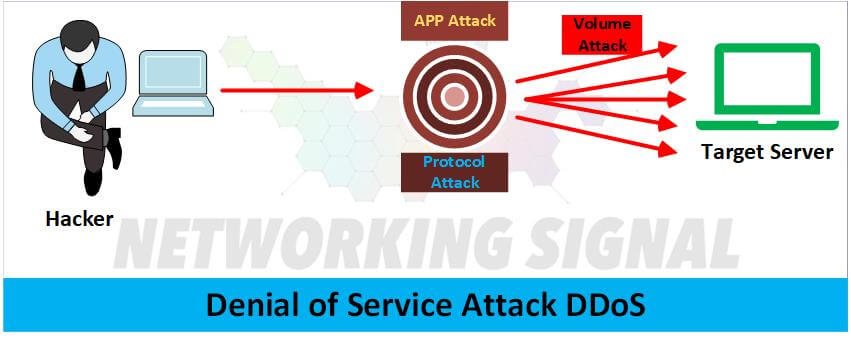
A denial-of-service (DoS) exposure can have devastating consequences for any organization. Beyond the immediate disruption of service, a DoS incident can erode trust, damage reputation, and trigger significant financial losses. Understanding the multifaceted impacts is crucial for proactive risk management.A successful DoS attack can cripple an organization’s operations, impacting everything from online sales and customer support to internal communication and critical infrastructure.
The consequences are far-reaching and can manifest in various ways, including financial losses, operational inefficiencies, and reputational damage.
Financial Costs
The financial ramifications of a DoS exposure can be substantial. Direct costs include expenses incurred during the attack, such as increased server capacity to mitigate the attack, and potential data loss recovery. Indirect costs are often far greater, encompassing lost revenue due to downtime, decreased customer confidence, and the cost of implementing security enhancements. The cost of customer acquisition may also increase as the organization struggles to rebuild trust.
Furthermore, legal fees and settlements related to a breach or associated damage may also be significant.
Operational Impacts
A DoS exposure can significantly disrupt an organization’s operational efficiency. Downtime caused by the attack can halt essential business processes, leading to lost productivity and potential delays in project completion. Disruptions to online services can impact customer service, leading to frustration and lost sales. Moreover, the attack can disrupt internal communications, creating inefficiencies in workflows and impacting overall productivity.
In addition, the response effort to the attack may involve significant staff time and resources, diverting attention from other business priorities.
Regulatory and Legal Implications
Organizations must be aware of the regulatory and legal implications of a DoS exposure. Depending on the industry and location, there may be specific regulations that require organizations to report security incidents or implement specific security measures. Failure to comply with these regulations can result in significant penalties, including fines, legal action, and damage to the organization’s reputation.
Furthermore, data breaches that result from a DoS attack may expose the organization to legal action from affected customers or stakeholders.
Customer and Stakeholder Impact
A DoS exposure can negatively impact customer and stakeholder relationships. Downtime and service disruptions can lead to frustration, lost trust, and a decline in customer satisfaction. This can result in decreased customer loyalty, lost sales, and a negative impact on brand image. Stakeholders, including investors and partners, may also experience concerns regarding the organization’s stability and resilience, which may lead to financial losses and reputational damage.
Real-World Examples
Numerous real-world examples highlight the severity of DoS exposures. For instance, large e-commerce platforms have experienced significant revenue losses due to prolonged service disruptions caused by targeted attacks. Similarly, critical infrastructure providers have faced challenges maintaining service availability during DoS attacks, leading to potential disruptions in essential services. In these cases, the financial impact, operational disruption, and reputational damage were substantial, emphasizing the importance of robust security measures.
Identifying and Detecting Exposures
Denial-of-service (DoS) attacks are a serious threat to any online system. Identifying potential vulnerabilities and proactively monitoring for malicious activity are crucial for mitigating the risk of such attacks. Early detection allows for faster response times and minimizes the impact of an attack.
Common Indicators of DoS Exposure
Various indicators signal potential DoS exposures. These range from unusual spikes in network traffic to unexpected resource consumption patterns. Understanding these indicators is the first step in effective threat detection. Careful observation of system metrics and network logs is essential.
Denial-of-service attacks are a real headache, exposing vulnerabilities in current internet infrastructure. Thankfully, a shift towards the future internet protocol, IPv6, is promising. This new standard, as detailed in internet protocol for the future ipv6 poised for adoption , could potentially mitigate some of these issues by offering enhanced security and scalability. Ultimately, a more robust protocol like IPv6 will hopefully make denial-of-service attacks less impactful in the future.
- High volumes of traffic originating from a single source or a small group of sources can indicate a potential attack. This might manifest as abnormally high packet rates or unusual traffic patterns, potentially exceeding normal operational thresholds.
- Sudden and significant increases in network latency or packet loss can be indicative of an attack. These disruptions often precede or coincide with a surge in traffic.
- Unusual or unexpected spikes in CPU or memory usage, especially on critical servers, are strong indicators of potential exploitation. Such anomalies might result from a flood of requests that overwhelm the system’s capacity.
- A noticeable increase in failed login attempts or authentication failures can be associated with attempts to gain unauthorized access, which might be part of a larger attack or a reconnaissance phase.
Proactive Monitoring of Network Traffic and System Resources
Regular monitoring of network traffic and system resources is essential for early detection of DoS attacks. This involves employing various tools and techniques to track key metrics and identify anomalies. Implementing automated alerts based on predefined thresholds can be extremely beneficial.
Recent revelations about denial-of-service attacks exposed vulnerabilities in online systems. This highlights the ongoing struggle to secure digital infrastructure, particularly in the face of increasingly sophisticated cyber threats. For instance, the recent legal battle between the Recording Industry Association of America (RIAA) and several major internet service providers, such as the one detailed in sbc fights back over riaa subpoenas , demonstrates how crucial these security measures are in protecting digital freedom and access.
This underscores the critical need for constant vigilance and proactive measures to prevent such attacks from undermining online services.
- Utilizing network monitoring tools like Wireshark allows detailed analysis of network traffic patterns. This can help identify unusual traffic flows, abnormal packet sizes, and other potential indicators of malicious activity.
- Monitoring system resources, such as CPU utilization, memory usage, and disk I/O, provides insights into resource consumption patterns. Anomaly detection systems can be implemented to alert on unusual spikes in resource usage.
- Employing intrusion detection systems (IDS) and intrusion prevention systems (IPS) can provide real-time alerts and mitigation capabilities. These systems analyze network traffic and system logs to detect malicious activity.
- Implementing logging mechanisms to record all significant events, including network traffic data, system activity, and security alerts, is crucial. These logs provide a historical record of activity and help in identifying patterns and trends.
Tools and Technologies for DoS Detection and Response
Various tools and technologies are available for detecting and responding to DoS exposures. Choosing the appropriate tools depends on the specific needs and resources of an organization.
- Wireshark, a powerful network protocol analyzer, is invaluable for examining network traffic in detail. It allows for identification of unusual traffic patterns and protocols, enabling investigation of suspicious activity.
- Snort, an open-source intrusion detection system (IDS), can detect various types of network attacks, including DoS attacks. It uses predefined rules and signature-based matching to identify malicious patterns.
- Security Information and Event Management (SIEM) systems consolidate security logs from various sources. These systems can identify correlated events and provide comprehensive visibility into potential threats, including DoS attacks.
- Cloud-based security platforms offer advanced threat detection and response capabilities. They often provide real-time monitoring and automated mitigation techniques for various cyber threats, including DoS attacks.
Identifying Vulnerabilities in Network Configurations
Vulnerabilities in network configurations can expose systems to DoS attacks. Regular security assessments are critical to identify and address these weaknesses.
- Misconfigured firewalls or intrusion prevention systems (IPS) can inadvertently allow malicious traffic to reach targeted systems. Thorough firewall rules and IPS configurations are essential.
- Open ports and services on servers can be exploited for DoS attacks. Only necessary services should be exposed to the internet.
- Weak or default passwords for network devices and systems can allow attackers to gain unauthorized access and initiate attacks. Implementing strong passwords and multi-factor authentication is crucial.
- Insufficient bandwidth or processing power on servers can make them vulnerable to DoS attacks. Sufficient capacity should be allocated to prevent the system from being overwhelmed by malicious requests.
Security Monitoring Tools for DoS Exposures
A table outlining various security monitoring tools and their use cases is presented below:
| Tool | Use Case | Description |
|---|---|---|
| Wireshark | Network Traffic Analysis | A powerful network protocol analyzer used to capture and examine network traffic, helping to identify unusual patterns, protocols, and malicious activities. |
| Snort | Intrusion Detection | An open-source intrusion detection system (IDS) that analyzes network traffic for malicious activity based on predefined rules and signatures. |
| Suricata | Intrusion Detection | A high-performance, open-source IDS and IPS that excels in detecting a broad range of threats, including DoS attacks, leveraging rule-based detection. |
| SolarWinds Security Center | Security Information and Event Management (SIEM) | A comprehensive SIEM platform that collects security logs from various sources, allowing for analysis and correlation of events, providing valuable insights into security threats, including DoS attacks. |
Mitigation and Response Strategies
Denial-of-service (DoS) attacks pose a significant threat to online services and infrastructure. Effective mitigation and response strategies are crucial for minimizing damage and restoring functionality swiftly. A comprehensive plan encompassing preventative measures, immediate actions, and long-term security enhancements is essential.A proactive approach to DoS protection is paramount. By anticipating potential vulnerabilities and implementing robust defenses, organizations can significantly reduce the likelihood of successful attacks.
This proactive approach must be coupled with a well-defined response strategy, enabling swift and effective action in the event of an attack.
Comprehensive Mitigation Plan
A comprehensive mitigation plan involves a layered approach, combining preventative measures with reactive strategies. This plan should be tailored to the specific needs and vulnerabilities of the targeted infrastructure.
- Network-Level Defenses: Implementing firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) is critical. These tools can filter malicious traffic, block known attack patterns, and alert administrators to suspicious activity. Proper configuration and regular updates are essential for maintaining effectiveness.
- Traffic Filtering and Rate Limiting: Implementing traffic filtering and rate limiting mechanisms helps to identify and mitigate abnormal traffic patterns characteristic of DoS attacks. These mechanisms can be configured to identify and block traffic exceeding predefined thresholds.
- Load Balancing and Redundancy: Distributing traffic across multiple servers through load balancing can absorb the impact of a DoS attack. Redundant systems provide backup capacity, ensuring continued service even if one component is overwhelmed.
- Application-Level Defenses: Implementing application-layer defenses like web application firewalls (WAFs) can help mitigate attacks targeting specific applications or services. These defenses can identify and block malicious requests and safeguard the integrity of applications.
Immediate Actions Upon Detection
Swift action upon detecting a DoS attack is critical to minimizing damage and restoring service.
- Alerting and Escalation: Immediately notify the relevant personnel and incident response team. Establish clear communication channels and escalation procedures for rapid response.
- Isolate the Affected Systems: Isolating the affected systems from the network can limit the spread of the attack and prevent further damage. This might involve temporarily disconnecting vulnerable servers or shutting down specific applications.
- Logging and Monitoring: Thoroughly document the attack, including timestamps, IP addresses, and the nature of the attack. Detailed logging provides crucial information for forensic analysis and future prevention efforts.
- Contacting ISP or Security Providers: Reach out to your internet service provider (ISP) or security providers for assistance and support, especially for large-scale attacks. They may have tools or resources to help mitigate the attack.
Strengthening Network Security
Proactive measures are crucial for preventing future DoS exposures.
- Regular Vulnerability Assessments: Regularly assess the network and applications for vulnerabilities to identify potential attack vectors. This helps in proactively addressing weaknesses before they are exploited.
- Security Awareness Training: Educating personnel on DoS attack tactics and best practices for recognizing and reporting suspicious activity can significantly reduce the risk of internal compromise.
- Security Hardening: Implementing security hardening procedures on all systems and applications can improve overall security posture and make it more difficult for attackers to penetrate the network.
- Patch Management: Regularly applying security patches and updates to software and operating systems is crucial for closing known vulnerabilities.
Importance of Incident Response Teams
Incident response teams play a vital role in handling DoS attacks.
- Coordinating Response Efforts: Incident response teams coordinate the efforts of different teams (network, security, operations) to effectively handle the attack.
- Proactive Planning and Training: Incident response teams plan for different scenarios and train personnel on responding to various types of cyber threats, including DoS attacks.
- Post-Incident Analysis: The team analyzes the attack to understand the causes, identify weaknesses, and implement preventative measures to prevent similar attacks in the future.
Step-by-Step Procedure for Handling a DoS Exposure
A structured procedure facilitates a coordinated response to a DoS attack.
- Alerting and Escalation: Immediately notify the incident response team and relevant personnel.
- Immediate Mitigation: Implement network-level defenses to limit the impact of the attack, including rate limiting and traffic filtering.
- System Isolation: Isolate affected systems to prevent further damage and the spread of the attack.
- Data Collection and Analysis: Thoroughly document the attack, gather logs, and analyze the attack pattern.
- Restoration of Service: Restore services and systems to normal functionality once the attack subsides.
- Post-Incident Review: Conduct a post-incident review to identify weaknesses and implement preventative measures.
Prevention Measures
Denial-of-service (DoS) attacks pose a significant threat to network infrastructure, disrupting services and causing substantial financial losses. Proactive prevention measures are crucial to mitigate the risk of such attacks. Implementing robust security strategies across the network, from the firewall to the application layer, is paramount to safeguarding systems.
Robust Firewall Rules, Denial of service exposed
Firewalls act as the first line of defense against unauthorized access and malicious traffic. Implementing strict and regularly updated firewall rules is essential to prevent DoS attacks. These rules should filter out known attack patterns and suspicious traffic based on IP addresses, ports, and protocols. A layered approach, combining static and dynamic rules, is recommended. Static rules define general network policies, while dynamic rules adapt to real-time threats and traffic patterns.
Regularly reviewing and updating firewall rules to reflect emerging threats is crucial for maintaining effectiveness. For instance, blocking traffic originating from known malicious IP ranges can effectively deter attacks.
Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are crucial for identifying and responding to malicious activities in real-time. IDS solutions monitor network traffic for anomalies and suspicious patterns, alerting administrators to potential threats. By analyzing network traffic, IDS systems can detect various DoS attack signatures, such as flooding attacks, and trigger alerts, enabling prompt responses. Implementing both signature-based and anomaly-based detection methods provides a comprehensive approach to identifying potential threats.
Signature-based detection uses predefined patterns to identify known attacks, while anomaly-based detection identifies deviations from normal traffic patterns, helping detect novel attacks.
Network Segmentation and Isolation
Network segmentation divides the network into smaller, isolated segments. This approach limits the impact of a DoS attack within a single segment, preventing it from spreading across the entire network. By isolating critical systems, organizations can minimize disruption and maintain essential services during an attack. Restricting communication between different segments prevents malicious traffic from affecting other parts of the network.
For example, separating the web server from the internal database server through a firewall can protect the database if the web server is targeted.
Application Hardening
Hardening applications and services against exploitation is a crucial aspect of DoS prevention. This involves implementing security best practices throughout the software development lifecycle, from design to deployment. Implementing input validation, output encoding, and rate limiting mechanisms can prevent exploitation. By validating user input, applications can prevent attackers from injecting malicious code. Output encoding protects against cross-site scripting (XSS) vulnerabilities.
Rate limiting mechanisms prevent attackers from overwhelming servers with excessive requests.
Web Application Security Best Practices
A comprehensive approach to web application security is vital to prevent DoS attacks. Following established best practices is paramount. These include:
- Input Validation: Validate all user inputs to prevent malicious code injection.
- Output Encoding: Encode all output data to prevent cross-site scripting (XSS) vulnerabilities.
- Rate Limiting: Implement rate limiting mechanisms to prevent attackers from overwhelming the server with excessive requests.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and address vulnerabilities.
- Security Information and Event Management (SIEM): Implement a SIEM system to collect and analyze security logs for potential threats.
These best practices, when implemented diligently, significantly enhance the security posture of web applications, reducing the risk of DoS attacks.
Case Studies and Examples
Denial-of-service (DoS) attacks are a persistent threat to organizations of all sizes. Understanding how these attacks manifest in real-world scenarios and the strategies employed for mitigation is crucial for proactive defense. Learning from past experiences helps organizations build more resilient systems and prevent future disruptions.
Illustrative Case Studies of DoS Attacks
Numerous organizations have fallen victim to sophisticated DoS attacks, suffering significant financial and reputational damage. Analyzing these incidents offers valuable insights into attack vectors and effective mitigation techniques.
- The 2016 DDoS Attack on Dyn DNS: This massive distributed denial-of-service (DDoS) attack crippled numerous popular websites, highlighting the vulnerability of internet infrastructure to coordinated attacks. The attack leveraged a vast botnet, demonstrating the potential for widespread disruption when attackers gain control of a significant number of compromised devices. This attack underscored the importance of robust DDoS protection measures and the need for proactive threat intelligence.
- The 2021 Attack on a Major E-commerce Platform: This specific attack targeted an e-commerce platform, disrupting online sales and causing significant revenue losses. The attack exploited vulnerabilities in the platform’s infrastructure, emphasizing the importance of continuous security assessments and proactive patching. This incident illustrated how a seemingly minor vulnerability can be exploited for substantial financial damage.
Lessons Learned from Case Studies
The case studies underscore several crucial lessons for organizations. Firstly, a proactive security posture, encompassing continuous monitoring, vulnerability assessments, and incident response planning, is paramount. Secondly, diversification of service infrastructure and implementing redundant systems are essential to prevent complete service outage during attacks. Finally, building a strong partnership with internet service providers and security vendors can significantly enhance the effectiveness of mitigation strategies.
Successful Mitigation Strategies
Organizations have successfully mitigated DoS attacks using various strategies. These include implementing rate limiting to control the influx of requests, employing content delivery networks (CDNs) to distribute traffic and absorb attack volume, and leveraging specialized DDoS mitigation services.
- Rate Limiting: This technique restricts the number of requests a user or IP address can make within a specific timeframe. This effectively slows down or prevents attackers from overwhelming the system with excessive requests.
- Content Delivery Networks (CDNs): CDNs distribute website content across multiple servers globally, enabling faster delivery to users and absorbing a significant portion of attack traffic.
- DDoS Mitigation Services: Dedicated services specifically designed to handle DDoS attacks can filter malicious traffic, protecting the organization’s infrastructure and ensuring continued service availability.
Comparative Analysis of Mitigation Strategies
A comparative analysis of mitigation strategies reveals varying levels of effectiveness and cost. Rate limiting is relatively inexpensive but might not be sufficient against sophisticated attacks. CDNs provide a cost-effective way to distribute traffic and absorb attacks, while dedicated DDoS mitigation services offer the most comprehensive protection but come at a higher cost.
Severity and Impact of DoS Attacks
The following table illustrates the potential severity and impact of different DoS attack types.
| Attack Type | Severity | Impact |
|---|---|---|
| SYN Flood | High | Significant downtime and complete service disruption |
| UDP Flood | Moderate | Partial service disruption and decreased performance |
| HTTP Flood | High | Significant performance degradation and potential website outage |
Last Recap
In conclusion, denial-of-service exposures are a serious threat to any organization. This comprehensive overview has highlighted the importance of proactive security measures, robust incident response plans, and continuous monitoring. By understanding the various attack types, their potential impacts, and the practical steps for mitigation, organizations can significantly reduce their vulnerability to these threats. This discussion serves as a valuable resource for anyone seeking to bolster their network security posture.