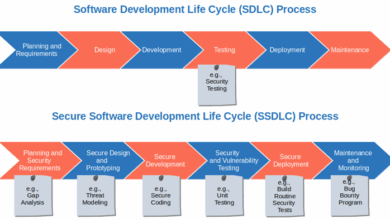
New Efforts Being Taken Against Spyware A Deep Dive
New efforts being taken against spyware are focusing on a multi-faceted approach, encompassing technological advancements, international cooperation, and individual/corporate security measures. This detailed look examines the evolving landscape of spyware threats, from the latest tactics used by cybercriminals to the cutting-edge strategies being employed to counter them. The discussion explores how governments, tech companies, and individuals are collaborating to safeguard against this pervasive threat.
We’ll analyze the technical intricacies, ethical considerations, and the crucial role of user awareness in the fight against spyware.
Current spyware threats include keyloggers, which record keystrokes, and various other forms of malicious software that can compromise sensitive information. These threats often exploit vulnerabilities in systems or rely on social engineering tactics. Recent incidents have highlighted the critical need for robust security measures to combat the sophisticated techniques employed by attackers. This article will delve into the different types of spyware, the methods used to deploy them, and the impact they can have.
Overview of Current Spyware Threats
Spyware, a pervasive threat to both individuals and organizations, is constantly evolving. Sophisticated techniques and readily available tools empower malicious actors to create and deploy highly effective spyware, often disguised within seemingly innocuous software or web pages. Understanding the current landscape of spyware threats is crucial for proactive protection and mitigation.
Prevalence of Spyware Types
Various types of spyware target different vulnerabilities and information. Keyloggers, for instance, meticulously record keystrokes, potentially compromising sensitive information like passwords and financial details. Steganography, a technique that hides data within seemingly harmless files or images, enables the discreet transmission of stolen information. Remote access trojans (RATs) provide malicious actors with unauthorized control over targeted systems, allowing them to execute commands, steal data, and even install additional malware.
Adware, although often less malicious than other types, can still cause significant disruptions by bombarding users with unwanted advertisements and tracking browsing habits. Mobile spyware specifically targets smartphones and tablets, collecting data such as location, contacts, and messages.
Methods of Deployment and Concealment
Spyware authors employ diverse methods to deploy and conceal their malicious software. Phishing emails, masquerading as legitimate communications, often contain malicious attachments or links that download spyware onto unsuspecting victims’ devices. Compromised websites can unknowingly host malicious scripts that silently infect visitors’ systems. Software vulnerabilities, if left unpatched, can be exploited to gain unauthorized access and install spyware.
Social engineering tactics, which manipulate users into unknowingly granting access to their systems or downloading malicious software, remain a significant threat. Furthermore, the use of legitimate-looking software packages containing hidden spyware continues to be a common strategy.
Examples of Recent High-Profile Incidents
Several high-profile incidents highlight the growing sophistication and impact of spyware. One example involved a targeted attack on a political campaign, where spyware was used to access sensitive communications and potentially influence election outcomes. Another incident exposed the vulnerability of critical infrastructure to spyware attacks, showcasing the potential for widespread disruption and damage. These incidents underscore the need for robust security measures and continuous vigilance against spyware threats.
Spyware Functionality and Attack Vectors
| Spyware Type | Functionality | Attack Vectors | Impact |
|---|---|---|---|
| Keylogger | Records keystrokes, captures screenshots, and logs website activity. | Phishing emails, infected websites, malicious software downloads. | Stealing passwords, credit card information, personal data, and intellectual property. |
| Remote Access Trojan (RAT) | Provides unauthorized access and control over a victim’s computer. | Malicious software downloads, exploit kits, infected websites. | Data theft, system manipulation, data breaches, and financial losses. |
| Steganography | Hides data within seemingly harmless files or images. | Malicious email attachments, infected files, and compromised websites. | Secretly transmitting sensitive information, such as confidential documents, or passwords. |
| Adware | Displays unwanted advertisements, tracks user browsing habits, and collects personal data. | Malicious software downloads, infected websites, and software bundles. | Annoying pop-up ads, privacy violations, potential for redirects to malicious websites. |
| Mobile Spyware | Monitors mobile device activity, including location, contacts, and messages. | Malicious apps, infected websites, and social engineering. | Privacy violations, data breaches, and potential for identity theft. |
Emerging Trends in Anti-Spyware Strategies
The fight against spyware is an ongoing battle, requiring constant adaptation to the evolving tactics of cybercriminals. This necessitates a proactive approach, not just reactive measures, and a focus on emerging technologies to stay ahead of the curve. New advancements in detection and prevention are crucial, alongside comprehensive security awareness training for users. The role of AI and machine learning is becoming increasingly important in this arena.
Technological Advancements in Spyware Detection and Prevention
Modern anti-spyware tools leverage sophisticated techniques beyond simple signature-based detection. These methods include behavioral analysis, which monitors application activities for suspicious patterns, and anomaly detection, which identifies deviations from normal user behavior. Machine learning algorithms play a critical role in these advancements, enabling systems to learn and adapt to new and evolving spyware threats in real-time. For instance, a system trained on vast datasets of known spyware and legitimate software can recognize subtle characteristics that distinguish malicious code.
The Role of Artificial Intelligence and Machine Learning in Identifying and Mitigating Spyware Threats, New efforts being taken against spyware
AI and machine learning are revolutionizing anti-spyware strategies. These technologies enable automated threat identification and response, significantly improving the speed and efficiency of detection. AI algorithms can analyze vast amounts of data, including network traffic, system logs, and user behavior, to identify subtle indicators of spyware infections. For example, an AI-powered system can recognize a spike in network activity from a particular application that matches known spyware behavior, triggering an alert.
Machine learning models can be trained to detect zero-day exploits, new and previously unknown vulnerabilities that cybercriminals exploit to install spyware. The continuous learning capability of these systems makes them highly effective in the face of rapidly evolving spyware threats.
New Approaches to Security Awareness Training for Users
Security awareness training is no longer just about educating users about phishing scams. Modern training programs need to be dynamic and engaging, teaching users to recognize the subtle signs of spyware infection. These signs can range from unusual system performance to unexpected pop-ups or changes in browser settings. Practical exercises and simulations are crucial to reinforce these lessons.
For instance, users can participate in simulated phishing attacks or scenarios where spyware is attempted to be installed. This hands-on experience is more effective in creating a proactive security mindset than simply presenting a list of rules. Additionally, training should be personalized and adaptive, tailoring content to individual user roles and responsibilities within the organization.
New efforts against spyware are definitely promising, but it’s interesting to consider how things like Google loosening its grip on trademarked keywords in searches ( google loosens reins on trademarked keywords ) might indirectly affect those efforts. This could potentially lead to a more open playing field, but also more challenges in identifying and combating malicious software. The interplay between these trends is definitely something to keep an eye on.
Comparison of Anti-Spyware Software Solutions
The following table provides a comparative overview of different anti-spyware software solutions, highlighting key features and differences. It’s crucial to choose software that aligns with specific needs and budget constraints.
| Software | Detection Method | User Interface | Pricing |
|---|---|---|---|
| Sophos Home Premium | Heuristic analysis, behavioral monitoring, and signature-based detection | Intuitive and user-friendly, with clear dashboards | Paid subscription |
| Malwarebytes Premium | Behavior analysis and machine learning-based detection | Clean and straightforward interface | Paid subscription |
| Bitdefender Antivirus Plus | Combination of signature-based, heuristic, and behavioral detection | Easy to navigate, with clear visual cues | Paid subscription |
| Microsoft Defender Antivirus | Heuristic analysis and machine learning-based detection | Integrated into Windows OS, simple and streamlined | Free (included with Windows) |
Government and International Cooperation
Global spyware threats necessitate coordinated efforts across nations. The complexity and sophistication of modern spyware demand international cooperation to effectively counter its proliferation and misuse. Governments and international organizations are increasingly recognizing the need for shared intelligence, standardized responses, and collaborative enforcement mechanisms.International cooperation is vital because spyware often transcends national borders. A single country’s efforts may not be sufficient to address the scope of the problem.
Sharing information, developing joint strategies, and enforcing consistent regulations are essential to disrupt spyware operations and protect citizens worldwide.
Collaborative Efforts Between Governments
Governments are actively engaging in collaborative efforts to combat spyware. This involves intelligence sharing, joint investigations, and coordinated enforcement actions. For example, countries often exchange information about spyware tactics, techniques, and procedures (TTPs) to better understand and counter emerging threats. This intelligence sharing is crucial for anticipating and responding to new forms of spyware. Furthermore, governments may collaborate on joint investigations to identify and dismantle spyware operations that target multiple countries.
This can lead to the arrest of perpetrators and the seizure of infrastructure.
Role of International Organizations
International organizations play a pivotal role in establishing standards and guidelines for combating spyware. Organizations like the United Nations (UN) and the Organization for Economic Co-operation and Development (OECD) promote international cooperation and share best practices. These organizations often facilitate discussions and workshops to promote the adoption of international standards and frameworks for cybersecurity, which include the development of strategies to combat spyware.
Recent efforts to combat spyware are crucial, especially with the increasing sophistication of these threats. While tech companies are working hard to develop new defenses, innovations like Panasonic’s new Blu-ray DVD recorder panasonic debuts blu ray dvd recorder highlight the continued importance of robust security protocols for all devices. Ultimately, staying ahead of the curve in cybersecurity is key to maintaining a safe digital environment.
The development of international legal frameworks is also critical for addressing the issue of spyware across borders.
Legislative Measures and Regulatory Frameworks
Numerous countries have implemented legislative measures and regulatory frameworks to address spyware threats. These measures often include provisions for regulating the development, distribution, and use of spyware. For example, some countries have enacted laws requiring companies to disclose the use of spyware to law enforcement. Others have introduced penalties for the misuse of spyware, aiming to deter malicious actors.
Stricter regulations on the export of spyware technology and tools can also be seen as a response to these threats.
Table of International Agreements and Initiatives
| Agreement/Initiative | Participating Countries | Key Provisions | Impact |
|---|---|---|---|
| Budapest Convention on Cybercrime | Various countries, including EU members | Addresses cybercrime, including spyware-related offences; facilitates international cooperation on investigations. | Provides a framework for international cooperation on cybercrime, including spyware. |
| OECD Principles on AI | OECD member countries | Addresses ethical considerations related to the use of AI, including potential spyware applications. | Provides guidelines for responsible AI development, which can indirectly affect spyware development. |
| UN Cybersecurity Initiatives | Various UN member states | Focuses on international cooperation on cybersecurity threats, including spyware; promotes capacity building. | Encourages global awareness of cybersecurity threats and cooperation. |
| EU Cybersecurity Act | European Union member states | Introduces harmonized cybersecurity requirements for digital products and services. | Aims to bolster cybersecurity across the EU by setting standards for the development and deployment of technologies, potentially affecting spyware. |
Individual and Corporate Security Measures

Protecting against spyware requires a multifaceted approach, combining proactive measures for individuals and robust security protocols for organizations. Failing to address these issues can lead to significant financial losses, reputational damage, and privacy violations. This section details key strategies to mitigate the risk of spyware infections.Spyware, whether targeting individuals or corporations, can have devastating consequences. Proactive measures are crucial in preventing these threats.
Effective strategies encompass a wide range of techniques, from using strong passwords to implementing advanced security software. This section delves into specific measures to enhance personal and corporate security.
Proactive Measures for Individuals
Protecting personal devices from spyware requires a combination of awareness and technical safeguards. Individuals should prioritize vigilance in their online activities and take steps to enhance their digital security posture.
- Strong Password Practices: Employing complex and unique passwords for each online account is paramount. Avoid using easily guessable information like birthdays or names. Utilize a password manager to generate and store strong passwords securely. A strong password policy is crucial, and it includes avoiding reuse of passwords across different platforms.
- Regular Software Updates: Keeping operating systems and applications updated is essential. Updates often include crucial security patches that address vulnerabilities exploited by spyware. Regularly checking for and installing updates is a fundamental preventative measure.
- 谨慎的下载行为: Be cautious about downloading files from untrusted sources. Avoid clicking on suspicious links or attachments. Always verify the source before downloading any software or files. Only download software from reputable sources.
- 谨慎的社交媒体互动: Be mindful of social media interactions. Avoid sharing personal information or clicking on links from unknown sources. Verify the legitimacy of any request for personal data.
- Use of Anti-Spyware Software: Installing and regularly updating reputable anti-spyware software can help detect and remove malicious programs before they cause harm. Regular scans and real-time protection are crucial for ongoing protection.
Robust Security Protocols for Organizations
Implementing robust security protocols is crucial for organizations to prevent spyware infections. These protocols must be tailored to the specific needs and vulnerabilities of the organization.
- Network Security Measures: Implementing firewalls, intrusion detection systems, and antivirus software on all network devices is vital. These tools can block malicious traffic and detect suspicious activity, acting as a primary defense against spyware infiltration.
- Employee Training: Educating employees about the risks of spyware and phishing attacks is essential. Training programs should cover topics such as recognizing suspicious emails, links, and attachments. This human element of security is critical in preventing infections.
- Data Encryption: Encrypting sensitive data both in transit and at rest can prevent unauthorized access and exploitation by spyware. This measure safeguards data even if a system is compromised.
- Regular Security Audits: Conducting regular security audits can help identify vulnerabilities in security protocols and implement necessary changes. This proactive approach helps organizations stay ahead of emerging threats.
Handling a Suspected Spyware Infection
A well-defined procedure for handling a suspected spyware infection is essential. A standardized process helps organizations and individuals respond effectively to such incidents.
- Isolate the Infected System: Immediately disconnect the infected system from the network to prevent further spread of the infection. This measure is critical in containing the threat.
- Identify the Malicious Software: Use reputable anti-malware tools to identify and analyze the suspected spyware. This step is crucial in understanding the nature of the threat.
- Quarantine and Remove: Quarantine the suspected spyware and remove it from the system. Follow the instructions provided by the anti-malware tool to ensure complete removal. Removing the spyware completely is critical.
- System Restoration: If necessary, restore the system to a known good state. This step helps ensure that the system is free from the infection and malware.
- Report and Analyze: Report the incident to the appropriate personnel and analyze the cause of the infection to prevent similar incidents in the future. Understanding the root cause is vital in preventing future infections.
Identifying and Removing Malicious Software
Identifying and removing malicious software requires expertise and the use of reliable tools. A methodical approach is crucial to ensure complete removal and prevent recurrence.
- Utilize Anti-Malware Software: Reputable anti-malware software provides tools for identifying and removing malicious software. Regular updates to the software are crucial to ensure effectiveness.
- Scan for Malware: Regularly scan systems for malware to detect and remove any infections. This proactive approach can prevent the escalation of issues.
- Use Specialized Tools: Employ specialized tools for deeper analysis and removal of malware. These tools can help in situations where standard tools fail.
Example of a Strong Password Policy
A strong password policy is a crucial element of security. It minimizes the risk of unauthorized access and subsequent spyware infections.
A strong password policy should mandate the use of complex passwords, including upper and lower case letters, numbers, and symbols. Passwords should be at least 12 characters in length and changed regularly. Password reuse across platforms should be strictly prohibited.
This policy helps to prevent unauthorized access and ensures that the system is secure.
Technical Aspects of Anti-Spyware Technologies
The digital landscape is constantly evolving, and so too must our defenses against insidious spyware. Understanding the technical mechanisms behind anti-spyware tools is crucial for effective protection. This exploration delves into the core technologies used to identify and neutralize malicious software, highlighting the importance of ongoing updates and robust encryption.Anti-spyware tools are not static entities; they are dynamic systems designed to adapt to the ever-changing threat landscape.
Their efficacy hinges on a deep understanding of spyware’s techniques and a proactive approach to threat detection.
Identifying Malicious Code
Sophisticated anti-spyware solutions employ a variety of techniques to identify malicious code. These include signature-based detection, heuristic analysis, and behavioral monitoring. Signature-based detection relies on a database of known spyware signatures, essentially a “wanted” list for malicious code. Heuristic analysis examines code patterns and behaviors that are atypical or suspicious, flagging potential threats even if they haven’t been seen before.
Recent efforts to combat spyware are crucial, particularly in the context of broader technological advancements. These new defensive measures are becoming increasingly sophisticated, mirroring the ever-evolving tactics of malicious actors. This proactive approach to security is directly connected to the complex issue of fighting terrorism through technology, fighting terrorism through technology , and ultimately bolstering national security.
The goal remains the same: to protect sensitive information and infrastructure from those seeking to exploit vulnerabilities.
Behavioral monitoring tracks the actions of running processes, identifying programs that exhibit unusual or malicious activity. For example, a program repeatedly attempting to access sensitive files or contacting a remote server without explicit user permission could be flagged as suspicious.
Neutralizing Spyware Threats
Once malicious code is identified, anti-spyware tools employ various strategies to neutralize the threat. These include quarantining infected files, blocking malicious processes, and removing spyware from the system. Quarantine isolates the potentially harmful files, preventing them from interacting with the system. Blocking malicious processes prevents the spyware from executing its intended actions. Removing spyware involves deleting the malicious code from the system, restoring the system to a clean state.
Importance of Software Updates
Regular software updates and patching are fundamental to maintaining an effective anti-spyware defense. Security vulnerabilities in software are frequently discovered and exploited by malicious actors. These vulnerabilities can be exploited by spyware to gain access to systems. Updates often include critical patches that address these vulnerabilities, closing potential entry points for malicious code. Consider a scenario where a software update addresses a known vulnerability in a web browser.
This vulnerability could have been exploited by spyware to install itself on a user’s computer. Regular updates reduce the risk of exploitation, providing a significant layer of protection.
Challenges of Keeping Anti-Spyware Tools Up-to-Date
Maintaining the effectiveness of anti-spyware tools requires ongoing effort to stay current with the latest threats. Keeping anti-spyware tools updated is often challenging. The constant emergence of new spyware variants necessitates continuous updates to detection signatures and heuristic rules. Additionally, the sheer volume of updates and the need for frequent testing to ensure compatibility can create challenges for users.
Users must be informed about the importance of updates and be provided with mechanisms for efficient and timely implementation.
Robust Encryption for Data Protection
Robust encryption methods are critical for safeguarding sensitive data from unauthorized access. Encryption transforms data into an unreadable format, making it useless to those without the decryption key. Advanced encryption standards, like AES (Advanced Encryption Standard), are employed to encrypt data at rest and in transit. This protection is essential for protecting confidential information, such as financial data or personal records.
A strong encryption system acts as a formidable barrier against unauthorized access.
Ethical Considerations of New Efforts: New Efforts Being Taken Against Spyware

New anti-spyware technologies promise enhanced security, but their implementation raises crucial ethical questions. Balancing the need to protect individuals and organizations from malicious actors with the fundamental right to privacy is a complex challenge. This necessitates a careful evaluation of potential trade-offs and the impact on individual freedoms. The introduction of advanced surveillance tools requires a thoughtful consideration of ethical frameworks and societal values to ensure responsible development and deployment.The development and deployment of anti-spyware technologies necessitate a careful evaluation of the potential ethical dilemmas and trade-offs associated with them.
The potential for misuse and unintended consequences must be proactively addressed through stringent ethical guidelines and transparent regulatory frameworks. This proactive approach ensures responsible innovation and protects the rights and freedoms of individuals.
Balancing Security and Privacy
The pursuit of enhanced security often necessitates measures that may infringe upon individual privacy. A delicate balance must be struck between safeguarding against malicious activities and respecting the fundamental right to privacy. This necessitates the development of robust legal frameworks and ethical guidelines that establish clear boundaries for the use of anti-spyware technologies.
Impact on Freedom of Expression and Information Sharing
New anti-spyware technologies may potentially impact freedom of expression and information sharing. Restrictions on access to information or limitations on communication could have far-reaching consequences. This raises concerns about the potential for censorship and the erosion of democratic principles. It is crucial to evaluate the potential impact on free speech and ensure that anti-spyware technologies do not unduly restrict the dissemination of information.
Ethical Frameworks for Evaluating Anti-Spyware Technologies
Different ethical frameworks offer distinct perspectives on the evaluation of anti-spyware technologies. Understanding these frameworks helps in identifying potential challenges and guiding the development of responsible solutions.
| Ethical Framework | Key Principles | Application to Anti-Spyware | Potential Challenges |
|---|---|---|---|
| Utilitarianism | Maximizing overall happiness and well-being | Prioritizing security over privacy when overall societal well-being is demonstrably enhanced. | Potential for disproportionate harm to individuals or groups if security measures are implemented without sufficient safeguards to protect vulnerable populations. |
| Deontology | Adherence to moral duties and rules | Prioritizing respect for individual rights and privacy as fundamental duties, even if it means accepting some level of security risk. | Potential for difficulty in establishing clear and universally accepted moral duties regarding the use of surveillance technologies. |
| Virtue Ethics | Developing virtuous character traits | Promoting transparency and accountability in the development and deployment of anti-spyware technologies to cultivate trust and responsibility. | Potential for differing interpretations of virtuous conduct regarding the balance between security and privacy. |
| Rights-Based Ethics | Respecting fundamental rights and freedoms | Ensuring that anti-spyware technologies do not violate fundamental rights such as privacy, freedom of expression, and due process. | Potential for conflicts between competing rights, for example, the right to privacy versus the right to security. |
Final Thoughts
In conclusion, the fight against spyware necessitates a holistic strategy that addresses technological, governmental, and individual factors. The emerging trends in anti-spyware technologies, coupled with international cooperation and proactive security measures, represent significant progress. However, ongoing vigilance and a proactive approach remain crucial in the face of evolving threats. Individuals and organizations must remain informed about the latest spyware tactics and adapt their security practices accordingly.
The ongoing discussion surrounding ethical considerations, privacy, and freedom of expression will continue to shape the future of anti-spyware efforts.