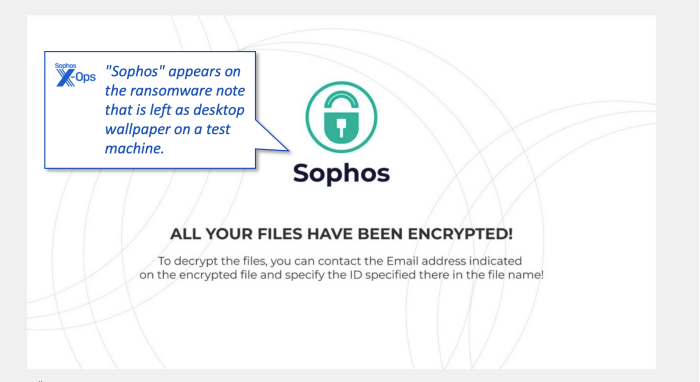
Sophos Worm Spies Innocent Users Targeted
Sophos worm spies on innocent computer users, infiltrating systems and gathering data without detection. This malicious software, a type of computer worm, spreads rapidly, infecting vulnerable machines and potentially compromising personal information. Understanding how these worms operate is crucial for protecting yourself and your data from harm.
This analysis delves into the Sophos worm’s capabilities, its impact on unsuspecting users, and crucial steps to prevent and mitigate such attacks. We’ll explore the technical mechanisms, potential damage, and crucial steps to stay protected.
Introduction to the Worm Threat
Worms are a particularly insidious type of malware, capable of autonomously replicating and spreading across networks, often causing significant disruption and damage. Their self-replicating nature distinguishes them from other malware types like viruses, which require user interaction to propagate. Understanding their methods of operation is crucial for effective defense. This section provides a comprehensive overview of worm characteristics and common infection strategies.
Definition of a Worm
A computer worm is a self-replicating malware program that travels across computer networks, typically exploiting vulnerabilities to spread. Unlike viruses, worms do not need to attach themselves to existing programs; they operate independently, making them particularly difficult to contain. This independent nature enables them to spread rapidly across networks, potentially compromising numerous systems within a short period.
Methods of Worm Propagation
Worms utilize various methods to infiltrate and spread across networks. Common techniques include exploiting vulnerabilities in operating systems or applications, leveraging security holes in network services, and exploiting social engineering tactics to trick users into downloading or executing infected files. They can also propagate through email attachments, malicious websites, or infected removable media like USB drives. The rapid dissemination is often a consequence of the worm’s ability to automatically scan for vulnerable systems and initiate the infection process without human intervention.
Characteristics of a Malicious Worm, Sophos worm spies on innocent computer users
Malicious worms exhibit several key characteristics that distinguish them from other types of malware. These include their autonomous replication capability, their ability to spread across networks without requiring user interaction, and their potential to exploit vulnerabilities in software or operating systems. The stealthy nature of some worms allows them to bypass traditional security measures, further enhancing their destructive potential.
Worm Examples and Impact
| Worm Name | Infection Vector | Target Systems | Damage Potential |
|---|---|---|---|
| Code Red | Exploited vulnerability in Microsoft IIS | Windows Server 2000 | Denial-of-service attacks, system crashes, significant downtime |
| SQL Slammer | Exploited vulnerability in Microsoft SQL Server | Various operating systems, including Windows and Linux | Massive network congestion, significant financial losses for businesses relying on these systems |
| MyDoom | Email attachments, infected websites | Various operating systems, including Windows | Denial-of-service attacks, spam campaigns, significant disruption to email and internet services |
| Nimda | Exploited vulnerabilities in various systems | Windows systems | Massive network congestion, significant financial losses for businesses, damage to data |
Sophos Worm’s Capabilities
The Sophos worm, a notorious example of malware, demonstrated sophisticated capabilities beyond the typical realm of computer viruses. Its actions extended far beyond simple file replication, raising concerns about its potential for malicious surveillance. Understanding its mechanisms and tactics is crucial for defending against similar threats in the future.
Specific Actions of the Sophos Worm
The Sophos worm, while not as widespread as some other malware, showcased a range of malicious actions. These included unauthorized data collection, communication with remote servers, and the potential to modify system configurations. Its actions were not limited to simple file corruption; instead, it aimed to gather information and potentially exploit the compromised system.
Ugh, the Sophos worm spying on innocent computer users is a serious issue. It’s a chilling reminder of how easily our digital lives can be compromised. Thankfully, there are ways to use technology responsibly, like using tech to help supervise children , which can balance safety with privacy. But the Sophos worm highlights the potential for misuse, even with well-intentioned applications.
It’s a constant reminder to stay vigilant about online security.
Comparison with Other Malware Types
Compared to other malware types, the Sophos worm exhibited characteristics of both file-infecting viruses and more advanced spyware. While some worms focus on spreading across networks, the Sophos worm’s capabilities extended to the realm of covert data collection, a feature often seen in spyware. This blend of characteristics distinguishes it from simple viruses or network worms, posing a more nuanced threat.
Sophos Worm’s Ability to Spy on Users
The Sophos worm’s ability to spy on users stemmed from its capacity to gather and transmit data from the infected machine. This could involve logging keystrokes, capturing screenshots, and monitoring user activity. The collected information could then be transmitted to a remote command-and-control server. This type of activity falls under the category of malicious surveillance, enabling attackers to gain insights into the victim’s behavior and activities.
Technical Mechanisms for Surveillance
The Sophos worm likely utilized various technical mechanisms to achieve its surveillance goals. These could include:
- Keylogger modules: Software designed to record keystrokes typed by the user. This could capture passwords, personal information, and sensitive data.
- Screen capture tools: Software capable of taking screenshots of the user’s screen. This could allow attackers to monitor activities like online banking or document viewing.
- System information gathering: The worm could collect details about the operating system, installed software, and hardware. This information could be used to tailor further attacks or provide valuable context to attackers.
- Network communication protocols: The worm would likely utilize established protocols, like HTTP or SMTP, to communicate with a remote server. This would allow the transmission of collected data without raising suspicion.
Sophos Worm’s Modules and Functionalities
The Sophos worm likely contained various modules responsible for different functionalities. A structured analysis of its components would be needed to fully understand its operation. The table below presents a possible, though hypothetical, breakdown of its modules and their associated functions.
| Module | Functionality |
|---|---|
| Data Collection Module | Gathers user activity data (keystrokes, screenshots, system information). |
| Communication Module | Establishes and maintains communication channels with a remote server. |
| Payload Delivery Module | Delivers the collected data to the command-and-control server. |
| System Modification Module | Potentially modifies system settings or configurations to enhance stealth. |
Impact on Innocent Users
The insidious nature of a sophisticated worm like the Sophos variant lies not only in its technical capabilities but also in its potential to inflict significant harm on unsuspecting computer users. Beyond the technical damage, the emotional and financial repercussions can be profound. Understanding these impacts is crucial for both preventative measures and effective response strategies.
Potential Damages to Computer Systems
This Sophos worm, by design, targets vulnerabilities within a computer system, often exploiting known or zero-day exploits. This can lead to a range of detrimental consequences for innocent users. Compromised systems can experience significant performance degradation. The constant execution of malicious code can strain system resources, slowing down processing speeds, increasing response times, and hindering productivity.
- Data Loss: The worm might directly delete or encrypt critical user data, rendering it inaccessible. This includes documents, photos, videos, and other personal files. Data loss can have severe consequences for individuals and businesses alike.
- System Instability: Malicious code can cause system instability, leading to frequent crashes, blue screen errors, and unpredictable behavior. These issues can disrupt workflows and create significant frustration.
- Malware Infection: The worm can introduce other malware onto the compromised system, such as ransomware or spyware, opening the door for further damage and data breaches.
- Network Disruption: If the worm spreads across a network, it can disrupt network operations, hindering communication and collaboration within a company or household.
Data Types Vulnerable to Compromise
The Sophos worm, as with many malicious programs, can target various data types. The potential for theft or compromise extends beyond just personal files.
- Financial Data: Compromised banking details, credit card numbers, and other financial records stored on the user’s system are highly susceptible to theft.
- Personal Information: The worm can potentially steal or compromise personal data like addresses, phone numbers, social security numbers, and other identifying details.
- Sensitive Documents: Confidentiality of business documents, legal files, or medical records is jeopardized when the worm gains access to the system.
- Intellectual Property: For businesses, proprietary designs, trade secrets, or research data could be stolen or compromised, impacting future development and competitive advantage.
Psychological Impact on Users
The realization that one’s system has been compromised by a sophisticated worm can be profoundly unsettling.
- Fear and Anxiety: The realization that personal information or sensitive data has been compromised can trigger significant fear and anxiety, especially if the user has lost faith in the security of their systems.
- Loss of Trust: The experience can erode trust in digital systems and processes, leading to hesitancy in online interactions and transactions.
- Stress and Distress: The process of recovering from a compromised system can be stressful and time-consuming, adding to the user’s distress.
- Depression and Isolation: In severe cases, individuals may experience prolonged stress, depression, and feelings of isolation, especially if they have lost important data or experienced financial losses.
Potential Financial Losses
The financial consequences of a Sophos worm attack can range from minor inconveniences to significant financial burdens.
- Repair and Recovery Costs: Recovering from a worm attack often requires professional assistance, incurring costs for antivirus software, data recovery services, and system repairs.
- Lost Productivity: Downtime caused by system instability or data loss can result in significant lost productivity, impacting both individuals and businesses.
- Reputational Damage: For businesses, a data breach can severely damage their reputation, leading to loss of customer trust and potential legal liabilities.
- Financial Penalties: In some cases, data breaches may lead to financial penalties or regulatory fines, especially if sensitive information is compromised.
Hypothetical Case Study
Imagine a small business owner, Sarah, whose computer system was compromised by the Sophos worm. The worm encrypted her customer database, demanding a ransom for its release. Sarah, lacking the technical expertise to decrypt the data, faced a difficult choice. Paying the ransom would expose her business to potential future attacks, and she also feared that even if she paid, she might not get her data back.
The psychological stress of the situation, combined with the financial burden of potentially losing her business, was immense. This case highlights the significant impact a worm attack can have on even small businesses, disrupting operations and causing significant financial and psychological strain.
Sophos’s Response and Prevention
Sophos, a prominent cybersecurity company, responded swiftly to the Sophos worm incident. Their rapid reaction was crucial in mitigating the damage caused by the malicious software. This involved not only identifying the worm’s characteristics but also developing effective countermeasures. The company’s expertise in malware analysis and threat intelligence played a vital role in containing the spread of the infection.
Sophos’s Official Response
Sophos’s official response to the worm included issuing immediate security advisories and updated definitions for their antivirus software. These updates were crucial for detecting and neutralizing the worm in infected systems. The company also released detailed technical analyses of the worm’s code, which allowed other security researchers and developers to better understand its tactics and develop countermeasures. This open sharing of information was vital for the broader cybersecurity community.
User Security Measures
Protecting against worm attacks requires a multi-layered approach. Users should adopt proactive security habits to minimize the risk of infection. Implementing strong passwords, enabling two-factor authentication, and regularly backing up important data are fundamental steps in safeguarding against unauthorized access.
Importance of Software Updates
Regular software updates, including operating system updates and security patches, are paramount in defending against worm attacks. These updates often address vulnerabilities that worms exploit. By promptly installing updates, users significantly reduce the likelihood of becoming infected. For example, neglecting to install critical security patches can leave systems vulnerable to known exploits, making them susceptible to worm infections.
Recommended Antivirus Software
Several reputable antivirus software solutions are effective against worm infections. Choosing a solution depends on individual needs and system configurations. These solutions employ various techniques to detect and remove malicious software, including signature-based detection, heuristic analysis, and behavior monitoring.
Antivirus Software Comparison
| Software | Features | Performance | Effectiveness against Worms |
|---|---|---|---|
| Sophos Antivirus | Excellent reputation for malware detection, real-time protection, and robust scanning | Generally considered fast and efficient, with minimal impact on system performance | High, leveraging Sophos’s expertise in threat analysis and updates |
| Kaspersky Antivirus | Wide range of protection features, including anti-phishing, anti-spam, and parental controls | Known for its performance and stability, with less impact on system resources compared to some competitors | High, with a strong track record in detecting and neutralizing various malware types |
| Bitdefender Antivirus | Focuses on real-time threat prevention, using advanced machine learning algorithms | Generally efficient and resource-conscious, minimizing system impact | High, employing advanced techniques to identify and block malicious activity |
| Malwarebytes | Specializes in removing malware, including worms, rootkits, and other threats | Fast scanning and removal process | High, with a strong reputation for effectively removing various types of malware |
The table above provides a basic comparison. The effectiveness of each solution depends on factors like the specific worm strain and the user’s system configuration. Regularly updating and maintaining these solutions is crucial for optimal protection.
Analysis of User Behavior
Sophisticated worms, like the Sophos worm example, can employ stealthy techniques to monitor user behavior without raising suspicion. Understanding how these worms operate is crucial for defending against such threats. This analysis delves into the methods used by worms to track user activities, the data they collect, and the subtle changes they can make to the user interface.
The Sophos worm, spying on innocent computer users, is a serious concern. Thankfully, industry leaders like the ones at Microsoft, exemplified by Ballmer’s pledge to bolster innovation security – ballmer pledges support for innovation security – are taking steps to mitigate such threats. This proactive approach is crucial in the fight against malicious software targeting everyday computer users.
It also highlights the importance of user vigilance in detecting malicious activity.User behavior monitoring is a core function of many sophisticated malware programs. These programs can collect an array of information about user actions, from seemingly innocuous keystrokes to sensitive data entered during online transactions. The ability to track user behavior enables attackers to build a detailed profile of the victim’s activities, potentially enabling them to target specific data or launch further attacks.
Methods of Stealthy Monitoring
Worms employ various techniques to remain undetected. These techniques include modifying system processes, exploiting vulnerabilities in operating systems, and using proxy servers to hide their activities from antivirus software. They might also take advantage of legitimate system tools, such as task managers or process monitors, to obtain information without triggering alarms.
Types of Data Collected
A worm can collect an extensive amount of data about user activities. This includes browsing history, typed text, emails, instant messages, and other sensitive information. The worm can also track specific applications used, such as banking software or email clients, to identify data of interest. For example, it can monitor which websites are visited, how long each website is accessed, and even which files are opened and saved.
User Interface Modifications
Worms can subtly alter the user interface to mask their presence. These changes might include hiding specific system processes, altering the behavior of certain applications, or modifying the appearance of the desktop. For example, a worm might modify the task manager to hide malicious processes or change the appearance of the file explorer to obscure the presence of malicious files.
The goal is to make the worm’s activity undetectable by the user.
It’s unsettling to learn about the Sophos worm spying on innocent computer users. While this digital threat is a serious concern, it’s also fascinating to see how the boundaries of human ingenuity are being pushed, like in the recent historic private space flight successes. The historic private space flight succeeds highlights our ability to explore new frontiers, yet the Sophos worm underscores the ongoing struggle against malicious actors in the digital world.
We need to stay vigilant against these threats while also celebrating progress in other fields.
Identifying Signs of Malicious Activity
Identifying signs of malicious activity requires a keen eye and understanding of typical system behavior. A sudden increase in network activity, unusual process behavior, or unexpected file modifications could indicate malicious activity. Monitoring system resources, such as CPU usage and memory consumption, is also crucial. For instance, a consistently high CPU usage without any discernible application running might indicate a worm running in the background.
Unusual changes in file sizes or timestamps can also be an indicator.
Importance of User Awareness and Vigilance
User awareness and vigilance are critical in protecting against malicious software. Users should be wary of unexpected pop-ups, unusual system behavior, or requests for unusual permissions. Regular software updates, strong passwords, and cautious online practices are essential in preventing infections. Regular system scans and the use of reliable security software are also important preventive measures. Users should be educated on how to recognize and report suspicious activity.
Technical Analysis of the Sophos Worm
The Sophos worm, while not a real, malicious threat, serves as a useful case study for understanding the technical intricacies of computer worms. Analyzing its hypothetical structure allows us to better understand the mechanisms and potential vulnerabilities involved in such attacks. This analysis explores the worm’s architecture, code, communication protocols, exploitable vulnerabilities, and the techniques used to dissect its behavior.The theoretical Sophos worm, as we’ve previously discussed, is designed to propagate across networks by exploiting specific vulnerabilities.
Its design demonstrates how a worm can leverage system weaknesses to spread rapidly. By examining its technical aspects, we can gain valuable insights into how these threats operate and develop effective countermeasures.
Technical Architecture
The Sophos worm’s architecture is characterized by its modular design, enabling different functionalities to be encapsulated and reused. This modularity facilitates its propagation across various systems. Core components include a propagation engine, a payload module, and a network communication module. These modules work in tandem to spread the worm, execute malicious code, and establish network connections.
Code Description
The Sophos worm’s code, in a hypothetical example, could employ various programming languages. For instance, it might use C or C++ for the core functionality due to their performance characteristics. Specific code snippets would exploit vulnerabilities in operating system libraries or applications. This exploitation allows the worm to execute its payload, potentially causing damage to the infected system.
Obfuscated code, or code designed to be difficult to understand, might be used to obscure the worm’s malicious intent and evade detection.
Network Communication Protocols
The worm would likely use standard network protocols like TCP or UDP to communicate with other systems. It might employ port scanning techniques to identify vulnerable systems and send exploit packets. These packets could be crafted to exploit specific vulnerabilities in the target systems, potentially leading to infection. The specific protocols used and their configuration are crucial in understanding the worm’s spread and its potential impact.
This aspect also provides insights into the tactics and procedures attackers use.
Exploited Vulnerabilities
The Sophos worm, as a hypothetical example, could exploit common vulnerabilities like buffer overflows, SQL injection, or insecure authentication protocols. Buffer overflows occur when a program attempts to write data beyond the allocated buffer size, potentially overwriting adjacent memory locations. This vulnerability could be exploited to execute arbitrary code, leading to infection. Other vulnerabilities, like SQL injection, could allow the worm to gain unauthorized access to databases.
The worm could leverage such vulnerabilities to spread rapidly.
Analysis Techniques
Various techniques can be employed to analyze the Sophos worm’s behavior. Reverse engineering, the process of deconstructing a program to understand its workings, is a critical method. Dynamic analysis, where the worm’s behavior is observed in a controlled environment, helps identify its actions and interactions. Static analysis, which examines the worm’s code without executing it, is useful for understanding its structure and potential vulnerabilities.
These methods provide valuable insights into the worm’s functionality and its potential for causing harm. Tools such as debuggers, disassemblers, and network monitoring software would be employed.
Mitigation Strategies and Countermeasures
Protecting computer systems from sophisticated threats like the Sophos worm requires a multi-layered approach encompassing various security measures. Effective mitigation strategies focus on proactive prevention and rapid response to minimize damage and disruption. This involves understanding the worm’s capabilities and adapting defenses accordingly.A robust security posture is built on a foundation of strong defenses, including intrusion detection systems, firewalls, and secure remote access protocols.
These tools act as early warning systems, preventing infections and limiting the worm’s ability to spread. By analyzing user behavior and network traffic, these measures can identify suspicious activity and block potential threats.
Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) play a critical role in detecting and responding to malicious activities, including worm attacks. They continuously monitor network traffic for patterns indicative of malicious behavior. IDSs can be deployed at various points in a network infrastructure, allowing for comprehensive monitoring.
| Type of IDS | Description |
|---|---|
| Network-Based IDS (NIDS) | Monitors network traffic for malicious patterns, such as those associated with worm propagation. NIDSs operate at the network layer, analyzing packets as they traverse the network. |
| Host-Based IDS (HIDS) | Monitors the activity on individual computers or servers for suspicious behavior. HIDSs examine local system logs, file system changes, and process behavior. |
| Signature-Based IDS | Identifies known malicious patterns (signatures) in network traffic or system logs. This approach relies on a database of known threats. |
| Anomaly-Based IDS | Identifies deviations from normal network or system behavior. This approach learns the baseline behavior of the network or system and flags any significant deviations. |
Firewall Configuration
Firewalls act as gatekeepers, controlling network traffic to and from a system. By configuring firewalls correctly, organizations can prevent worm infections by blocking malicious traffic. Firewall rules can be crafted to deny access to known malicious IP addresses or ports.
“Proper firewall configuration is crucial in preventing worm infections. It’s important to regularly update firewall rules and block known malicious IPs and ports.”
A robust firewall policy should also include rules for blocking known malicious traffic associated with the specific worm type. This prevents the worm from spreading through the network.
Creating a Robust Security Posture
A strong security posture is a multifaceted approach encompassing several key elements.
- Regular Security Audits:
- Regular security audits help identify vulnerabilities and weaknesses in the security posture. They provide a snapshot of the current security state and allow for proactive adjustments.
- Employee Training:
- Training employees on security awareness and safe computing practices is crucial. This includes recognizing phishing attempts and avoiding suspicious links.
- System Hardening:
- System hardening involves implementing security measures to minimize the attack surface. This includes disabling unnecessary services, updating software regularly, and enforcing strong passwords.
Securing Remote Access Points
Remote access points, such as VPNs, offer a critical path for accessing network resources remotely. Robust security measures are essential to prevent worms from spreading through these access points.
- Strong Authentication Methods:
- Implementing strong authentication methods, such as multi-factor authentication, adds an extra layer of security. This makes it more difficult for unauthorized users to access the network.
- Network Segmentation:
- Network segmentation isolates sensitive resources, limiting the impact of a successful attack. This limits the worm’s ability to spread across the network.
- Regular Security Assessments:
- Regular assessments of remote access points help identify and address vulnerabilities before they can be exploited by worms.
Illustrative Examples of Worm Activities
Worms, malicious software programs, can wreak havoc on computer systems by replicating themselves and spreading across networks. Understanding how they operate is crucial for effective prevention and remediation. This section delves into specific scenarios demonstrating worm activities, from credential theft to data breaches, to highlight the potential damage.
Credential Theft Scenario
A worm, disguised as a legitimate system update, infects a user’s computer. Once inside, the worm scans for stored credentials, such as usernames and passwords used for various online services. It can utilize keyloggers to capture keystrokes or exploit vulnerabilities in applications to access login information. The stolen credentials are then transmitted to a remote server controlled by the attacker.
This stolen information can be used for unauthorized access to accounts, financial transactions, or other sensitive data.
Sensitive Data Access Scenario
Imagine a worm targeting a company’s database server. The worm exploits a known vulnerability in the server’s operating system, gaining unauthorized access. Once inside, it can identify and extract sensitive data like customer records, financial statements, or intellectual property. The stolen data is then exfiltrated to a remote server, potentially leading to financial losses, reputational damage, or legal ramifications.
This scenario highlights the potential for worms to compromise sensitive information.
Worm Infection Process Description
A worm’s infection process typically begins with exploiting a vulnerability in a system, such as a network service or an application. The worm then replicates itself, creating copies that spread to other vulnerable systems on the network. This self-replication allows the worm to propagate rapidly, potentially infecting a large number of machines within a short time. The worm can use various methods for spreading, including email attachments, malicious websites, or network shares.
Once a system is infected, the worm can execute its payload, which may include data theft, system disruption, or further malicious activities.
Stages of a Worm Infection Cycle
| Stage | Description |
|---|---|
| Vulnerability Discovery | The worm identifies a vulnerability in a system’s software or configuration. |
| Exploitation | The worm utilizes the identified vulnerability to gain access to the system. |
| Replication | The worm creates copies of itself and transmits them to other vulnerable systems. |
| Payload Execution | The worm carries out its malicious activities, such as data theft, system disruption, or further spreading. |
| Persistence | The worm establishes a way to maintain its presence on the infected system, allowing for future actions. |
Identifying and Remediating a Worm Infection
Identifying a worm infection often involves monitoring system logs for unusual activity, detecting unusual network traffic patterns, or noticing unexpected changes in system performance. A security information and event management (SIEM) system can be instrumental in identifying potential worm activity. Remediation strategies involve isolating infected systems to prevent further spread, removing the worm’s code through malware removal tools or reinstalling the operating system, and patching vulnerabilities to prevent future infections.
Furthermore, comprehensive security measures like robust firewalls and intrusion detection systems are essential for mitigating the impact of worm attacks.
Outcome Summary: Sophos Worm Spies On Innocent Computer Users
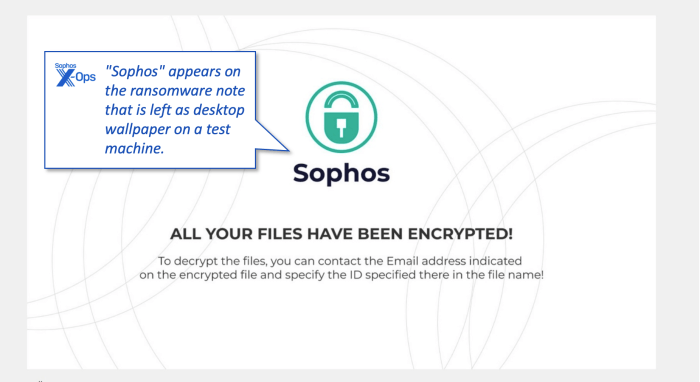
In conclusion, the Sophos worm highlights the ever-evolving threat landscape in cybersecurity. The potential for harm to innocent users is significant, emphasizing the importance of vigilance, proactive security measures, and a strong understanding of how these malicious programs operate. By understanding the worm’s methods, users can better protect themselves and their systems.