US Still Tops Spammer List
US still tops spammer list, highlighting the enduring problem of malicious online activity. This persistent issue, spanning decades, reveals the ongoing struggle to combat the ever-evolving tactics of spammers. From the early days of email to sophisticated modern techniques, the US remains a significant source of unwanted messages, impacting users and businesses worldwide. This deep dive explores the historical context, the technical methods, and the societal consequences of this troubling trend.
This article examines the historical evolution of spam, the factors driving the US’s continued leadership in sending spam, the technical strategies employed, and the substantial impact on internet users and businesses. It also discusses countermeasures, future trends, and real-world examples, offering a comprehensive understanding of this pervasive problem.
Historical Context of Spam
Spam, a pervasive nuisance in the digital age, has a surprisingly rich and evolving history. Its origins are deeply intertwined with the development of the internet and its expanding capabilities. From its humble beginnings to the sophisticated tactics employed today, understanding its evolution reveals much about the relationship between technology, communication, and the challenges of controlling online content.Early forms of unsolicited bulk email were relatively rudimentary, relying on simple methods to reach large audiences.
However, as internet infrastructure improved and email became more accessible, spam evolved into a more organized and sophisticated enterprise. The proliferation of spam became a direct result of these developments, creating a need for effective filters and strategies to combat its harmful effects.
Early Forms of Spam (Pre-2000s)
The early internet saw the rise of spam in various forms, reflecting the limited technology available at the time. Early spam often involved sending repetitive messages or newsgroups postings that were deemed irrelevant or undesirable. These were often promotional materials or chain letters, using similar strategies employed in traditional mass marketing. The lack of robust spam filters and the relative ease of mass mailing made it a significant problem.
Spam and Technological Advancements
Technological advancements dramatically impacted spam strategies. The internet’s growth, the rise of web hosting, and the proliferation of email accounts created fertile ground for spammers. This led to a significant increase in the volume and sophistication of spam campaigns. The use of automated tools, bots, and scripting languages further amplified the speed and scale of spam distribution, making it harder to track and control.
Types of Spam Over Time
Spam has evolved to encompass a variety of forms. Initial spam often consisted of simple promotional emails. Later, phishing scams emerged, aiming to trick recipients into revealing sensitive information. Now, spam campaigns often include malware, disguised as legitimate files or links, intending to compromise user systems. The tactics have evolved alongside technological capabilities, making it a constant battle to stay ahead of the evolving threats.
Impact of Technological Advancements on Spam Strategies
The development of automated tools and sophisticated scripting languages significantly impacted spam strategies. These tools enabled spammers to automate the process of creating and sending large volumes of messages, making it much harder to manually filter and identify spam. Additionally, the growth of internet infrastructure and email accounts created a vast and readily available audience for spam campaigns.
Prevalence of Spam in Different Regions and Eras
The prevalence of spam varies significantly across different regions and eras. Early forms of spam were relatively widespread, but the availability of internet access and email accounts varied widely, impacting the scope of spam campaigns. As technology advanced, spam campaigns grew in sophistication and reach, affecting users globally.
Growth of Spam Volume Over Time
The volume of spam has consistently increased with the expansion of internet usage. While precise figures are difficult to obtain, the general trend reflects an exponential growth.
| Year | Approximate Spam Volume (estimated) |
|---|---|
| 1990 | Low |
| 2000 | Moderate |
| 2010 | High |
| 2020 | Very High |
The US as a Source of Spam
The United States, despite its robust technological infrastructure and legal frameworks, remains a significant source of spam globally. This persistent presence stems from a complex interplay of factors, including the anonymity afforded by the internet, the relative ease of launching spam campaigns, and the lack of complete enforcement of existing regulations. Understanding these contributing elements is crucial for mitigating the problem and maintaining a healthy online environment.The US’s role as a prominent spam source is multifaceted.
Factors such as the prevalence of online anonymity tools and the relative ease of establishing and operating fraudulent websites contribute to the ease of launching large-scale spam campaigns. Furthermore, the legal and regulatory landscape, while designed to combat spam, faces challenges in effectively policing the global internet and often lags behind the rapid evolution of spam techniques. This gap allows unscrupulous individuals and organizations to exploit loopholes and continue their illicit activities.
Factors Contributing to the US’s Role as a Spam Source
The ease of anonymity online, coupled with relatively lenient penalties for spam-related offenses, makes the US a fertile ground for spam operations. The decentralized nature of the internet, coupled with the difficulties in tracking down perpetrators across international borders, exacerbates this issue. Furthermore, the high number of internet users in the US provides a large pool of potential victims, making it attractive for spammers.
Legal and Regulatory Frameworks in the US
The US legal framework surrounding spam is primarily based on the CAN-SPAM Act of 2003. This Act mandates that commercial emails must include certain elements, such as an opt-out mechanism, to comply with regulations. However, the act has limitations in its ability to deter and punish spammers, particularly those operating from outside the US. This regulatory framework, while aiming to address the issue, falls short in dealing with the sophisticated and evolving tactics of spammers.
Comparison with Spam Practices in Other Countries
Comparing the US’s spam practices with those of other countries reveals a mixed bag. While the US has laws like the CAN-SPAM Act, enforcement varies significantly. Some countries have stricter regulations and penalties, while others have less robust frameworks. This difference in approach highlights the global nature of the spam problem and the need for international cooperation to combat it effectively.
Common Techniques Employed by US-Based Spammers
US-based spammers employ a variety of techniques to target their victims. These techniques often involve social engineering tactics, creating deceptive email addresses, and leveraging vulnerabilities in email systems. Additionally, sophisticated phishing techniques are used to gain access to sensitive user information, which is then exploited for malicious purposes.
Comparison Table of Top 5 Spam-Sending Countries
| Country | Estimated Spam Volume (Approximate Values) |
|---|---|
| United States | High |
| China | High |
| Russia | High |
| India | High |
| Brazil | High |
Note: Exact figures for spam volume are difficult to obtain due to the anonymous nature of the internet. The table above provides a general comparison based on available information and industry estimates.
Technical Aspects of Spamming
Spamming is a significant issue, impacting businesses and individuals alike. Understanding the technical underpinnings of these malicious campaigns is crucial to combating them effectively. The methods employed by spammers are constantly evolving, adapting to filter improvements and technological advancements. This necessitates a continuous and proactive approach to counteract these evolving threats.The technical sophistication of spam operations has grown exponentially over the years, making it increasingly difficult to distinguish legitimate communication from malicious attempts.
Spammers leverage sophisticated tools and networks, allowing them to reach vast audiences with minimal effort. Understanding the tools, infrastructure, and strategies used by these actors is essential for developing effective countermeasures.
Common Methods of Sending Spam from the US
Spam originating from the US often leverages compromised accounts or botnets controlled by malicious actors. This allows them to send vast quantities of spam messages without detection, as the IP addresses and email accounts appear legitimate. Sophisticated techniques, such as spoofing and forging headers, further obfuscate the source of the messages. This circumvention of security protocols allows spam to bypass standard filters and reach unsuspecting recipients.
Tools and Technologies in Large-Scale Spam Campaigns
Spam campaigns frequently utilize automated tools for mass email delivery. These tools often incorporate features to generate vast numbers of emails and evade detection. Malicious actors leverage email servers, often compromised or rented, to send spam messages. These servers are frequently situated in countries with less stringent regulations or those with a history of being used for illicit activities.
Spammers also use proxies to hide their true IP addresses and locations.
Infrastructure Supporting Spam Distribution Networks, Us still tops spammer list
Spam distribution relies on a vast infrastructure, often spanning across multiple servers and networks. This infrastructure can involve botnets, compromised servers, and proxy servers, all working together to send spam emails to numerous recipients. The network effect of these interconnected systems amplifies the reach of spam campaigns. The sheer scale of these networks is often difficult to monitor and control.
The use of distributed denial-of-service (DDoS) attacks is a part of the infrastructure to overwhelm the targeted systems.
Methods Used to Evade Spam Filters
Spammers employ various techniques to bypass email filters. These techniques include using different email addresses and sending emails at different times, or encrypting messages. They might also use obfuscated subject lines, which are designed to evade detection by filters. The use of sophisticated algorithms that analyze filter behavior and adapt to them is prevalent. These strategies enable spam to be delivered to inboxes with increasing frequency.
Another method is to send emails with attachments that might contain malicious code, exploiting vulnerabilities in email clients.
Table of Different Types of Spam Emails
| Type of Spam Email | Examples |
|---|---|
| Phishing | Emails pretending to be from legitimate institutions, like banks or social media sites, to trick users into revealing personal information. |
| Malware | Emails containing attachments that download malicious software onto a recipient’s computer. |
| Spam Ads | Emails promoting products or services, often without explicit request from the recipient. |
| Fake Notifications | Emails falsely claiming that the recipient has won a prize or has other urgent matters to resolve. |
| Fake Delivery Notifications | Emails that claim a package or order is being delivered, but is fraudulent. |
Impact of Spam on the Internet
Spam, a pervasive issue plaguing the digital world, has far-reaching consequences for internet users, businesses, and the infrastructure itself. Its relentless nature, often disguised as legitimate communication, causes significant disruptions and costs. This section delves into the detrimental effects of spam across various facets of the online environment.
Detrimental Effects on Internet Users
Spam relentlessly bombards users with unwanted messages, clogging inboxes and overwhelming individuals with irrelevant content. This constant barrage can lead to a significant loss of productivity and time. Users often spend valuable time sifting through and deleting unwanted emails, a task that can be extremely time-consuming, especially for those who receive hundreds or thousands of spam messages daily.
Spam also can introduce malicious code, potentially compromising user data or leading to malware infections.
Financial Consequences for Businesses
Spam poses a substantial financial burden on businesses. The costs extend beyond the direct expenses of filtering and managing spam. Significant resources are allocated to combating spam, including the development and maintenance of spam filters, dedicated staff time for managing spam complaints, and the cost of potential data breaches resulting from malicious spam.
Reputational Damage to Businesses
Spam can severely damage a company’s reputation. When customers receive spam originating from a business, it creates a negative perception of the company’s brand. The perceived unprofessionalism or lack of care regarding user data can lead to a loss of customer trust and a decline in brand loyalty.
Impact on Network Infrastructure
The sheer volume of spam traffic significantly impacts network infrastructure. Spam consumes bandwidth, impacting the performance of email servers and internet service providers. The constant barrage of spam messages can overwhelm servers, leading to slower response times and potential service disruptions for legitimate users.
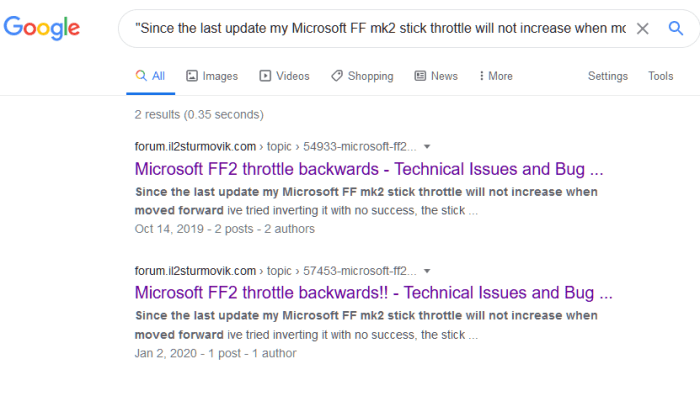
It’s frustrating to see the US still at the top of the spammer list, isn’t it? While that’s a concerning trend, it’s also worth noting that companies like Dell are sending most new jobs overseas, as detailed in this report dell sends most new jobs overseas. This global shift in job placement could potentially contribute to the US’s continued presence on the spammer list, as individuals may seek alternative ways to make money or create their own opportunities.
It’s a complicated picture, but ultimately, the US still tops the list for spam unfortunately.
Compromising User Data
Spam is frequently used as a vector for distributing malicious software. Phishing emails, often disguised as legitimate communications, can trick users into revealing sensitive information, such as passwords, credit card details, or social security numbers. These compromises can lead to identity theft, financial losses, and significant reputational damage for individuals and businesses.
Cost of Spam to Businesses
Spam’s impact on businesses is multifaceted and substantial. The following table illustrates the various costs associated with spam:
| Type of Cost | Estimated Cost |
|---|---|
| Lost Productivity | $100 – $1,000 per employee per year (depending on the company size and industry). |
| Spam Filtering Software and Services | $50 – $500 per month per user (depending on the complexity and features of the software). |
| Data Breach Remediation | $10,000 – $1,000,000+ (depending on the extent of the breach). |
| Legal and Regulatory Fines | Variable, depending on the specific regulations and violations. |
| Reputational Damage | Difficult to quantify, but can result in significant loss of revenue and customer trust. |
Examples of companies facing significant spam-related issues include those in e-commerce, financial services, and online retailers. These companies often bear the brunt of spam attacks, leading to financial losses and reputational damage.
Countermeasures and Prevention
Spam, a persistent plague on the internet, continues to plague inboxes worldwide. Effectively combating this digital nuisance requires a multi-pronged approach encompassing technical safeguards, user awareness, and proactive strategies. This section will delve into the various methods used to identify and filter spam, highlighting the crucial role of both software and user education in mitigating its impact.Identifying spam is not always straightforward.
It often masquerades as legitimate correspondence, exploiting vulnerabilities in email systems and user trust. This makes a layered defense mechanism essential.
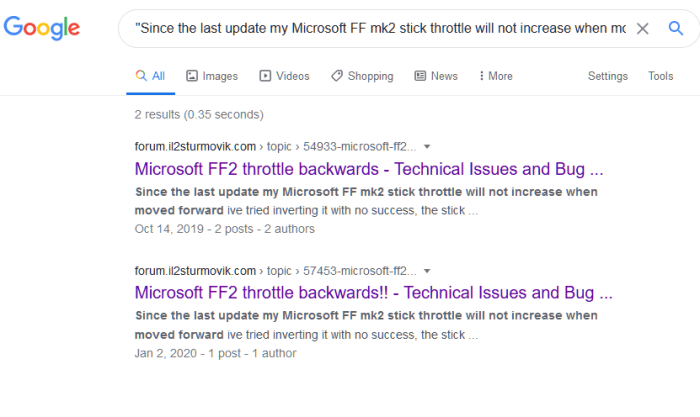
Ugh, the US is still dominating the spammer charts, it seems. While it’s frustrating to see this persistent issue, it’s interesting to see how tech giants are responding. Microsoft is pushing for an update, but IBM will be testing it first, as detailed in this article microsoft urges update but ibm will test first. Hopefully, this testing phase will lead to a more effective solution and finally curb the US’s spam problem.
Spam Filtering Methods
Spam filters are the frontline defense against unsolicited emails. They employ a range of techniques to identify and block potentially harmful messages. These techniques range from simple filtering to complex algorithms that analyze email headers, sender reputation, and content.
- Filtering: This basic method identifies emails containing specific words or phrases frequently associated with spam. For example, emails containing phrases like “free money” or “urgent action required” are flagged as suspicious.
- Bayesian Filtering: This advanced technique learns from user interactions to identify spam. It analyzes the content of emails marked as spam or not spam by the user and builds a statistical model to predict future spam messages. This allows the filter to adapt to evolving spam tactics.
- Blacklist and Whitelist Systems: Blacklists maintain a database of known spam senders. Emails from these senders are automatically blocked. Conversely, whitelists allow emails from trusted senders to bypass filtering, preventing legitimate emails from being mistaken for spam.
- Header Analysis: Examining email headers, including the “From,” “To,” and “Subject” lines, can reveal inconsistencies or red flags, such as unusual sender addresses or subject lines that are misleading.
Role of Anti-Spam Software
Anti-spam software plays a critical role in protecting email systems and individual users from spam. These programs utilize a combination of filtering techniques to identify and block unwanted messages. The sophistication of anti-spam software varies, with some relying on simple rules and others employing advanced algorithms.
- Comprehensive Filtering: Anti-spam software provides a more robust defense than basic filtering. It combines various filtering techniques to create a multi-layered protection system.
- Real-time Updates: The effectiveness of anti-spam software depends on its ability to adapt to evolving spam techniques. Regular updates ensure that the software remains current with the latest spam tactics and can effectively identify and block emerging threats.
- Integration with Email Clients: Modern email clients often integrate with anti-spam software, providing real-time protection against spam and preventing its delivery to the user’s inbox.
Importance of User Education
User education is crucial in combating spam. Users can play an active role in preventing spam by practicing safe email habits. By recognizing the characteristics of spam emails, users can avoid falling victim to phishing scams and other online threats.
- Recognizing Spam Characteristics: Users should be educated to recognize common characteristics of spam emails, such as suspicious subject lines, urgent requests, grammar errors, and unusual sender addresses.
- Safe Email Practices: Users should avoid clicking on suspicious links or attachments in emails, and they should be cautious about sharing personal information in response to unsolicited emails.
- Reporting Spam: Reporting spam emails to the email provider helps improve spam filtering systems. By flagging spam emails, users contribute to the overall effectiveness of anti-spam measures.
Effective Spam Prevention Strategies
A combination of technical and user-centric strategies can significantly reduce the incidence of spam. A multi-faceted approach that involves robust filtering, user awareness, and proactive measures is essential.
| Anti-Spam Solution | Features |
|---|---|
| Email Filtering Software | Combines multiple filtering techniques (, Bayesian, blacklist/whitelist) for enhanced protection. |
| Anti-Virus Software | Protects against malware often delivered via spam emails. |
| Spam Reporting Tools | Enables users to flag suspicious emails, improving filter accuracy. |
| Email Security Protocols | Enforces security standards to prevent spam from reaching inboxes. |
| User Education Programs | Provides awareness training on identifying and avoiding spam. |
Future Trends in Spam: Us Still Tops Spammer List
The digital landscape is constantly evolving, and spam, unfortunately, adapts alongside it. Predicting the future of spam requires understanding the driving forces behind its evolution, including technological advancements, user behavior, and the ongoing arms race between spammers and anti-spam measures. This analysis explores the likely trajectory of spam strategies, the challenges in combating it, and the potential impact of emerging technologies.
Evolution of Spam Strategies
Spam tactics are constantly evolving, moving beyond simple bulk email to more sophisticated and targeted approaches. Phishing scams, often disguised as legitimate communications, exploit vulnerabilities in user awareness and technical safeguards. Sophisticated social engineering techniques, combined with personalized content, make phishing attacks increasingly effective. The use of artificial intelligence (AI) by spammers will likely enhance the personalization and sophistication of these attacks, making them harder to identify.
US internet users are still unfortunately dealing with a high volume of spam, putting them firmly at the top of the spammer list. Meanwhile, Panasonic has just released a new Blu-ray/DVD recorder, which is a welcome technological advancement, but doesn’t seem to have solved the underlying problem of online spam. This new product, available at panasonic debuts blu ray dvd recorder , is sure to be a hit for home entertainment, but the relentless spam problem remains a serious issue for consumers.
Emerging Threats and Challenges
The challenges in combating spam are multi-faceted. One significant challenge is the ever-increasing volume of spam, often overwhelming existing filtering systems. Furthermore, the use of encrypted communication channels allows spammers to evade traditional detection methods. The rise of AI-powered spam will demand more sophisticated countermeasures, requiring constant adaptation and innovation in detection algorithms. The anonymity afforded by the dark web and the use of virtual private networks (VPNs) further complicates the tracking and prosecution of spammers.
Impact of New Technologies on Spam
The integration of AI into spam campaigns represents a major shift. AI-powered spam can analyze user data to tailor messages and increase engagement. This personalized approach enhances the effectiveness of phishing attacks. Similarly, advancements in deepfakes will likely be employed in spam campaigns to create realistic, yet fraudulent, content. The increasing use of social media platforms and messaging apps also provides new avenues for spammers to reach target audiences.
Potential Solutions to Future Spam Issues
Combating future spam requires a multifaceted approach. Robust AI-powered spam filters capable of recognizing subtle anomalies in communication patterns will be crucial. Increased user awareness and education on recognizing suspicious emails and messages are also vital. Furthermore, the development of innovative tools for detecting and preventing deepfakes will be essential. Collaboration between law enforcement and technology companies is crucial to effectively tackle the global problem of spam.
Impact of Artificial Intelligence on Spam Detection
AI is revolutionizing spam detection. Machine learning algorithms can analyze vast amounts of data to identify patterns and anomalies associated with spam. This allows for more accurate and proactive detection, reducing the volume of unwanted messages. However, spammers are also leveraging AI to improve the effectiveness of their strategies. The ongoing arms race between AI-powered spam and AI-powered detection systems necessitates continuous development and adaptation of both sides.
Illustrative Examples of Spam
Spam, a pervasive issue on the internet, employs various tactics to deceive users and achieve its malicious goals. Understanding these techniques is crucial for recognizing and avoiding spam. These examples, while not exhaustive, showcase the deceptive nature and harmful content often associated with spam emails from US sources.
Spam Email Examples from US Sources
Spam emails from US sources often leverage a variety of deceptive techniques. They may use convincing subject lines, imitate legitimate organizations, and include alarming or enticing information to lure victims into clicking links or revealing personal data.
Example 1: A purported “urgent notification” from a US bank.
- Subject: Important Account Information Update – Urgent!
- Content: The email mimics the official style of a US bank. It includes a threat of account closure unless the recipient clicks a link to verify their account information. It includes phrases like “failure to comply” and “immediate action required.”
- Deceptive Techniques: The subject line uses urgency and fear to prompt a quick response. The design mimics a legitimate bank’s email format, creating credibility. The threat of account closure is a common tactic.
- Harmful Content: The link in the email likely leads to a fraudulent website designed to steal login credentials or financial information. The recipient could potentially lose access to their bank account.
Example 2: A “free prize” notification from a US-based company.
- Subject: You’ve Won a Free Prize! Claim Your Gift Now!
- Content: The email claims the recipient has won a prize from a well-known US retailer. It asks for personal information (name, address, credit card details) to claim the prize.
- Deceptive Techniques: The email exploits the desire for free gifts and the sense of winning a prize. It uses a tempting subject line to lure recipients into the email.
- Harmful Content: The email is a classic phishing attempt. The personal information collected could be used for identity theft, or the recipient might be charged for a product or service they did not order.
Example 3: A “government notice” from a US agency.
- Subject: Important Notice Regarding Your Tax Status
- Content: The email claims to be from a US government agency, like the IRS. It demands immediate action, often involving payment or providing sensitive information.
- Deceptive Techniques: The subject line attempts to invoke a sense of panic and urgency. The email is designed to resemble official government correspondence.
- Harmful Content: The email is designed to trick the recipient into providing personal information or paying money to a fraudulent entity, potentially leading to financial loss.
Types of Deceptive Practices in Spam
Spammers utilize various deceptive practices, including impersonation of legitimate organizations, use of urgency and fear tactics, and misleading subject lines.
Harmful Content in Spam
Spam emails can contain harmful content such as malicious links, malware, and requests for sensitive information.
Final Wrap-Up
The US’s persistent role as a leading source of spam underscores the ongoing need for robust anti-spam measures. While technological advancements and user awareness play a crucial role, the core problem lies in the intricate interplay of incentives, legal frameworks, and technical capabilities. The future of combating spam will depend on a multi-faceted approach, including improved international cooperation, stronger regulations, and more sophisticated detection methods.
The continuing evolution of spam tactics necessitates vigilance and proactive strategies.