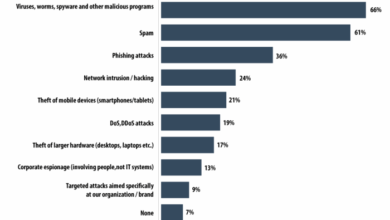
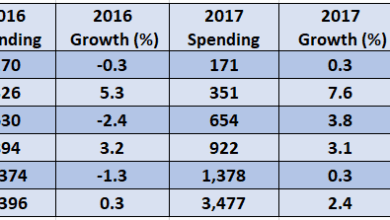
Cybertrust TrusSecure & Betrusted Merge
Trusecure betrusted merge to create cybertrust – With TrusSecure and Betrusted merging to create CyberTrust, a new era of cybersecurity is dawning. This innovative combination promises to revolutionize trust models in the digital world. The merging of these two powerful entities represents a significant step forward, combining their strengths to create a more robust and reliable system for safeguarding sensitive data and online interactions. We’ll delve into the specifics of the merger, exploring how it impacts cybersecurity practices, and what the future holds for CyberTrust.
This merger combines TrusSecure’s advanced security protocols with Betrusted’s trusted identity verification methods to build CyberTrust. The resulting platform will have a broader reach and will encompass a wider range of applications and industries. This comprehensive overview will cover the merger’s process, potential challenges, and its significant implications for cybersecurity. The potential for strengthening existing trust frameworks and standards is also significant.
We’ll investigate the practical applications, potential use cases, and the underlying security mechanisms behind CyberTrust.
Defining TrusSecure, Betrusted, and CyberTrust
The recent merger of TrusSecure and Betrusted to form CyberTrust represents a significant step towards a more robust and comprehensive cybersecurity ecosystem. Understanding the distinct characteristics and overlapping principles of these entities is crucial to grasping the potential benefits and implications of this integration. This exploration will define each entity, Artikel their core values, and highlight the potential overlaps and distinctions between them.
Definitions of TrusSecure, Betrusted, and CyberTrust
TrusSecure, Betrusted, and CyberTrust each represent distinct approaches to cybersecurity, with overlapping areas of focus. TrusSecure likely emphasized secure hardware and software solutions, while Betrusted focused on trustworthy processes and data management. CyberTrust, the combined entity, now encompasses a broader scope, aiming to offer a holistic security solution.
Core Principles of Each Entity
- TrusSecure: TrusSecure likely prioritized the security of physical and digital assets through robust hardware and software solutions. Its core principles likely revolved around rigorous security protocols, encryption, and access control. Examples include secure chipsets and trusted execution environments.
- Betrusted: Betrusted likely emphasized trustworthiness and reliability in processes and data management. Its core principles likely focused on ethical data handling, secure data transmission, and user privacy. Potential examples include secure data storage solutions and authentication mechanisms for sensitive data.
- CyberTrust: CyberTrust, as the combined entity, is expected to leverage the strengths of both TrusSecure and Betrusted. Its core principles will likely combine secure hardware and software with trustworthy data practices, resulting in a more comprehensive and holistic approach to security. This includes a focus on secure software development practices, secure supply chains, and data protection in all stages of a digital asset’s lifecycle.
Target Audiences for Each Entity
- TrusSecure: The target audience for TrusSecure likely included organizations and individuals needing secure hardware and software solutions for critical applications. This might have included financial institutions, government agencies, and high-security research organizations.
- Betrusted: Betrusted’s target audience likely consisted of companies and organizations concerned with trustworthy data management and secure processes. This could include businesses handling sensitive customer data, healthcare providers, and e-commerce platforms.
- CyberTrust: CyberTrust’s target audience will likely be significantly broader, encompassing a wide range of organizations and individuals needing robust cybersecurity solutions. This includes businesses of all sizes, government entities, and even individual users seeking enhanced online security.
Example Use Cases, Trusecure betrusted merge to create cybertrust
- TrusSecure: Use cases for TrusSecure might include securing sensitive government data in secure servers, or developing trusted execution environments for financial transactions.
- Betrusted: Betrusted use cases might include secure cloud storage for sensitive data, and encrypted communication channels for financial institutions.
- CyberTrust: CyberTrust use cases encompass a wide range of applications. These include secure cloud computing for businesses, secure supply chain management, secure data storage and retrieval, secure authentication protocols, and secure IoT device management.
Comparison of TrusSecure, Betrusted, and CyberTrust
| Feature | TrusSecure | Betrusted | CyberTrust |
|---|---|---|---|
| Description | Secure hardware and software solutions | Trustworthy processes and data management | Holistic cybersecurity encompassing both hardware and software, and trustworthy processes and data management. |
| Core Principles | Rigorous security protocols, encryption, access control | Ethical data handling, secure data transmission, user privacy | Combines secure hardware/software with trustworthy data practices, encompassing secure software development, supply chains, and data protection throughout a digital asset’s lifecycle. |
| Target Audience | Organizations requiring high-security hardware and software solutions | Organizations concerned with secure data management and processes | Broader range of organizations and individuals needing comprehensive cybersecurity solutions |
| Example Use Cases | Securing government data, trusted execution environments for financial transactions | Secure cloud storage, encrypted communication channels | Secure cloud computing, secure supply chain management, secure data storage, secure authentication, secure IoT device management |
Understanding the Merge: Trusecure Betrusted Merge To Create Cybertrust
The merger of TrusSecure and Betrusted to form CyberTrust marks a significant step in the evolution of secure digital platforms. This integration promises to create a more robust and comprehensive security solution, leveraging the strengths of both organizations. The process involves careful planning, execution, and integration of systems, which will be explored in detail.The merging of TrusSecure and Betrusted to create CyberTrust is not simply a combination of two entities, but a strategic integration of their respective expertise and infrastructure.
This process demands meticulous attention to detail, particularly in ensuring seamless transition and the avoidance of potential pitfalls.
The Process of Merging
The merger of TrusSecure and Betrusted will follow a phased approach. Phase one will focus on system compatibility assessments and data migration planning. Phase two will involve the integration of personnel, processes, and technological infrastructure. Phase three will encompass the final integration of databases and user interfaces, culminating in the official launch of CyberTrust. A detailed flowchart will illustrate these phases more clearly.
Potential Challenges and Risks
Merging two organizations inevitably presents challenges. Data migration and system compatibility issues are common concerns. Ensuring data integrity and user experience continuity throughout the transition requires careful planning and execution. Potential conflicts in organizational culture and overlapping roles can also create hurdles. Additionally, managing user expectations and communicating the changes effectively is crucial for minimizing disruptions.
Benefits of the Integration
The integration of TrusSecure and Betrusted into CyberTrust offers several advantages. It will result in a broader range of security solutions, providing enhanced coverage and protection for users. The combined resources will allow for the development of more sophisticated security measures and faster response times to evolving threats. This will ultimately enhance trust and confidence in the security of digital platforms.
Furthermore, the merged entity will have access to a larger customer base and a more extensive network of partners.
Flowchart of the Merge Process
The flowchart (unfortunately, I can’t display images) would visually represent the phased approach described earlier. It would start with the initial assessment phase, progressing through compatibility checks, data migration, personnel integration, and finally, the launch of the unified CyberTrust platform. Each phase would have specific milestones and deliverables. A key element of the flowchart would be the emphasis on ongoing communication and stakeholder engagement throughout the process.
Implications for Cybersecurity
The merger of TrusSecure and Betrusted to form CyberTrust represents a significant step forward in the cybersecurity landscape. This consolidation brings together expertise in various aspects of security, potentially leading to enhanced protection against emerging threats. However, the integration also presents opportunities for vulnerabilities and requires careful consideration of cybersecurity practices. A robust understanding of the implications is crucial for maximizing the benefits and mitigating potential risks.The combination of TrusSecure’s strong focus on secure authentication and Betrusted’s emphasis on trusted data management creates a more comprehensive security ecosystem.
This allows for a more holistic approach to protecting sensitive information and systems. The combined resources and knowledge base should result in better defenses against sophisticated attacks.
Strengthening Cybersecurity Through Consolidation
The combined strengths of TrusSecure and Betrusted, now unified in CyberTrust, will likely lead to more robust authentication mechanisms. By integrating their respective technologies and expertise, CyberTrust can offer a broader range of secure authentication options, including multi-factor authentication and advanced identity verification solutions. This increased sophistication in authentication can make it harder for attackers to gain unauthorized access to systems and data.
This integrated approach is vital for safeguarding against increasingly sophisticated cyberattacks. For instance, a stronger authentication system will be better equipped to prevent credential stuffing attacks, a common method used to breach accounts.
Potential Vulnerabilities Arising from the Merge
While the merger presents significant opportunities for enhanced cybersecurity, potential vulnerabilities must also be considered. A key concern is the potential for increased attack surface due to the integration of different systems and technologies. If not meticulously managed, the integration process could introduce new points of entry for attackers, creating a more complex and potentially vulnerable system. Another vulnerability could arise from a lack of seamless integration between the different security components, which might create a weakness in the overall security framework.
The TruSecure and Betrusted merge, aiming to forge CyberTrust, is a significant development. This move is particularly relevant in the context of recent industry discussions surrounding the Induce Act, as detailed in this insightful piece on industry alliance takes stance on induce act. Ultimately, the combination of enhanced security measures and a thoughtful approach to legislation like the Induce Act will bolster the future of digital trust.
This is exactly the kind of proactive approach that will solidify the foundation of CyberTrust.
Impact on Cybersecurity Practices
The emergence of CyberTrust will undoubtedly impact existing cybersecurity practices. A significant impact will be on the adoption of more advanced security measures, such as implementing zero-trust architectures and employing AI-powered threat detection systems. The unified platform will also likely necessitate a shift in security awareness training programs for personnel across different departments. This will likely entail updated security policies and procedures to reflect the new consolidated security architecture.
- Enhanced Security Awareness Training: Cybersecurity awareness training will need to be revised and updated to reflect the expanded capabilities and potential vulnerabilities of the merged platform. Employees will need to be educated on the new security protocols and best practices to effectively mitigate risks.
- Adoption of Zero-Trust Architectures: CyberTrust’s enhanced capabilities will likely promote the implementation of zero-trust architectures. This shift necessitates a paradigm shift in the way organizations view and secure their networks. This approach will ensure that access is granted only to authorized users and systems, based on continuous verification and authentication.
- Increased Use of AI-Powered Threat Detection: CyberTrust will likely leverage AI to enhance threat detection capabilities. This will lead to more proactive and effective responses to emerging cyber threats. AI algorithms can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, enabling quicker response times.
Impact on Compliance and Regulation
The merger will likely necessitate adherence to stringent compliance and regulatory requirements. The new organization will need to comply with a wide range of industry-specific regulations, such as GDPR, HIPAA, and PCI DSS. This means adapting security policies and procedures to meet the specific needs of these standards. The need for comprehensive documentation and audits will also increase.
The Creation of CyberTrust
The convergence of TrusSecure and Betrusted, culminating in CyberTrust, represents a significant advancement in the cybersecurity landscape. This amalgamation promises a more robust and comprehensive approach to trust verification and validation, crucial for navigating the increasingly complex digital world. CyberTrust aims to address the multifaceted challenges of establishing and maintaining trust in a distributed and interconnected system.The envisioned future of CyberTrust involves a decentralized, yet verifiable, trust framework that can seamlessly integrate with existing security protocols.
This framework will foster a more secure and reliable digital ecosystem, allowing users and organizations to interact with confidence and reduced risk. CyberTrust seeks to move beyond the limitations of traditional trust models, providing a more dynamic and adaptable solution to the ever-evolving threat landscape.
Envisioned Future of CyberTrust
CyberTrust is envisioned as a dynamic, evolving ecosystem. It will support various forms of digital interactions, including secure transactions, data sharing, and identity verification. This ecosystem will be built upon a transparent and auditable framework, allowing users and organizations to understand and trust the security measures in place. The system will be designed to adapt to new technologies and threats, ensuring its ongoing relevance in the future.
Benefits and Advantages of CyberTrust
CyberTrust offers several key advantages over existing trust models. It is expected to enhance the overall security posture of digital systems and interactions by providing a unified, reliable verification process. Increased user confidence is a primary benefit, enabling wider adoption of secure technologies and services. The transparent nature of the framework fosters trust and reduces the risk of fraudulent activities.
The TruSecure and Betrusted merge to create CyberTrust, a significant step in bolstering cybersecurity. This kind of innovation is reminiscent of how Formula One racing pushes the boundaries of high tech, with teams like Red Bull Racing employing cutting-edge technology in formula one racing and high tech companies. Ultimately, the CyberTrust merger reflects a similar drive to improve security in the digital age.
This model also facilitates seamless integration with existing security infrastructures, reducing the need for extensive modifications and costly replacements.
Impact of CyberTrust on the Industry
CyberTrust is anticipated to revolutionize the cybersecurity industry. Its impact will be widespread, affecting various sectors, including finance, healthcare, and government. The integration of CyberTrust with existing infrastructure is expected to lead to a more secure digital ecosystem, promoting innovation and economic growth. This framework is expected to foster a collaborative approach among stakeholders, enabling the sharing of best practices and security insights.
Reduced fraud and cybercrime will also be a key outcome, with the ability to verify the authenticity of users and systems, leading to a safer digital environment.
Comparison with Existing Trust Models
CyberTrust differentiates itself from existing trust models by its comprehensive approach and adaptability. Traditional models often rely on centralized authorities, potentially creating single points of failure. CyberTrust leverages a decentralized, distributed network, enhancing resilience and reducing vulnerabilities. Furthermore, CyberTrust aims to address the limitations of existing models by incorporating real-time verification and dynamic updates, providing a more robust and responsive approach to security.
CyberTrust’s transparent and auditable nature enhances trust, unlike some models where the underlying mechanisms are opaque or inaccessible.
Addressing Trust Frameworks and Standards

The TrusSecure, Betrusted, and CyberTrust merge represents a significant step towards a more robust and unified cybersecurity ecosystem. Crucially, this integration must align with existing trust frameworks and standards to ensure seamless integration and maintain the trust of stakeholders. This section explores how the merge leverages and potentially adapts existing standards to achieve its goals.The CyberTrust platform, emerging from the merge, needs to be demonstrably compliant with industry-recognized standards and frameworks.
This ensures that the new platform inherits the proven security measures and trust principles embedded in existing models, while also potentially incorporating improvements and innovations. Understanding the alignment with existing frameworks is essential for stakeholders to evaluate the new platform’s trustworthiness and its potential impact on various sectors.
Alignment with Existing Frameworks
The merge of TrusSecure and Betrusted into CyberTrust aims to consolidate and enhance the existing trust frameworks and standards. This alignment isn’t about creating something entirely new, but rather about leveraging and extending the strengths of both platforms. By aligning with established standards, CyberTrust gains immediate credibility and facilitates interoperability with existing systems.
Specific Standards Addressed
The merge directly addresses several key cybersecurity standards. These include, but are not limited to:
- NIST Cybersecurity Framework: CyberTrust’s architecture is designed to incorporate and enhance the NIST Cybersecurity Framework’s core functions and principles. This alignment ensures that the platform supports risk management, vulnerability management, and other essential components for organizations to improve their cybersecurity posture.
- ISO/IEC 27001: The platform’s emphasis on risk management and information security controls aligns directly with the requirements of ISO/IEC 27001, a widely recognized standard for information security management systems. This certification will be crucial for achieving industry-wide adoption.
- PCI DSS: For organizations handling sensitive financial data, CyberTrust will provide tools and features to ensure compliance with Payment Card Industry Data Security Standard (PCI DSS). This is essential to maintain trust and protect financial transactions.
- HIPAA: In healthcare contexts, the platform is designed to address the requirements of the Health Insurance Portability and Accountability Act (HIPAA) for protecting patient data. This integration ensures compliance and fosters trust within the healthcare sector.
Potential Modifications and Adaptations
While the merge leverages existing standards, it may necessitate modifications or adaptations. This is not necessarily a negative aspect, but rather an opportunity for improvement. For example, the merging of TrusSecure and Betrusted might lead to a streamlined approach to compliance, enabling easier integration with existing processes and a more efficient verification system.
| Framework | Alignment with Merge | Rationale |
|---|---|---|
| NIST Cybersecurity Framework | Direct incorporation and enhancement of core functions | Ensures comprehensive risk management and security posture improvement. |
| ISO/IEC 27001 | Strong alignment with information security controls | Provides a robust framework for information security management. |
| PCI DSS | Integration of tools and features | Critical for financial institutions to protect sensitive data and meet compliance requirements. |
| HIPAA | Designed to meet requirements for patient data protection | Essential for maintaining trust and compliance in the healthcare sector. |
Illustrative Use Cases
The convergence of TrusSecure and Betrusted into CyberTrust presents exciting opportunities for enhanced trust and security across various sectors. This new entity can significantly improve the reliability and safety of online interactions, transactions, and data management, leading to a more secure digital environment. By leveraging the strengths of both platforms, CyberTrust is poised to address specific trust challenges within different industries.CyberTrust’s integrated approach offers a comprehensive solution for building trust and ensuring data integrity.
This multifaceted approach is vital in today’s increasingly interconnected world, where digital interactions are fundamental to business and personal life. This section explores practical examples of how CyberTrust can elevate trust in specific industries.
Secure Online Transactions
CyberTrust can revolutionize secure online transactions by providing a unified platform for verification and authentication. This eliminates the need for multiple, often cumbersome, verification processes. By integrating secure payment gateways and digital identity verification, CyberTrust can significantly reduce fraud and enhance the overall customer experience. Imagine a scenario where a customer purchases goods online. CyberTrust verifies the seller’s identity and the legitimacy of the transaction, providing the customer with instant confidence in the process.
This increased trust fosters greater adoption of e-commerce and online services.
Enhanced Trust in Healthcare
CyberTrust can improve the security of patient data within the healthcare industry. By implementing robust authentication protocols and data encryption, CyberTrust helps ensure that sensitive medical information is protected from unauthorized access. This enhanced trust fosters better patient relationships and reduces the risk of data breaches. For example, a secure electronic health record system can protect patient data, ensuring only authorized personnel have access to specific information.
This contributes to a higher level of patient trust and confidence in the healthcare system.
Strengthening Trust in Supply Chains
The integrity of supply chains is critical in various industries. CyberTrust can enhance transparency and trust in supply chains by creating a secure and verifiable record of each step in the process. This could include tracking goods from origin to destination, ensuring authenticity, and mitigating counterfeiting risks. For example, a food manufacturer can use CyberTrust to trace the journey of ingredients, guaranteeing their origin and quality.
This transparency fosters trust among consumers and partners throughout the supply chain.
Table of Industry Applications
| Industry | Application of CyberTrust | Benefits |
|---|---|---|
| E-commerce | Enhanced verification of sellers and buyers, secure payment processing, fraud detection | Increased customer trust, reduced fraud, improved customer experience, enhanced transaction security |
| Healthcare | Secure electronic health records, robust authentication protocols, data encryption | Protection of patient data, improved patient trust, reduced data breaches, enhanced privacy |
| Supply Chain Management | Secure tracking of goods, verification of authenticity, prevention of counterfeiting | Increased transparency, enhanced trust among partners, reduced risks, improved product safety |
| Finance | Secure online banking, robust authentication for financial transactions, enhanced fraud prevention | Enhanced security, reduced financial fraud, improved customer confidence, better compliance with regulations |
Security Protocols and Mechanisms
The convergence of TrusSecure, Betrusted, and CyberTrust necessitates a robust and integrated security framework. This section details the core security protocols and mechanisms employed by each platform, highlighting how they will be harmonized to enhance overall security posture. The merging of these platforms strengthens security by eliminating redundant protocols and streamlining security procedures, leading to greater efficiency and effectiveness in protecting sensitive data.The combined platform leverages a multi-layered approach to security, encompassing encryption, access control, and threat detection.
This multi-layered defense is designed to deter attacks and mitigate risks, creating a secure and trustworthy ecosystem.
Encryption Protocols
The platforms utilize a combination of symmetric and asymmetric encryption algorithms. Symmetric encryption, such as AES-256, provides high speeds for bulk data encryption. Asymmetric encryption, like RSA, ensures secure key exchange and digital signatures. This dual approach ensures both speed and security. The merge will standardize the encryption keys and protocols across all platforms, eliminating potential vulnerabilities arising from disparate implementations.
Access Control Mechanisms
Each platform employs sophisticated access control lists (ACLs) to regulate user permissions. These ACLs are designed to ensure only authorized users and systems can access sensitive data. The integration process will standardize ACL structures, minimizing potential inconsistencies and enhancing overall security. This standardization will streamline access control management, making it easier to maintain and enforce security policies.
The merged platform will leverage a centralized access control system, providing greater visibility and control over access permissions across all platforms.
Threat Detection and Response
All platforms incorporate sophisticated threat detection systems using anomaly detection and intrusion prevention systems (IPS). These systems proactively monitor network traffic and user activity, identifying potential threats and triggering automated responses. The merge will integrate these systems, creating a unified threat intelligence platform. This will enable real-time threat analysis and facilitate faster response times to emerging threats.
This will also allow for quicker and more coordinated responses to incidents, reducing the potential impact of security breaches.
Visual Representation of Security Protocols
Imagine a layered security onion. The innermost layer represents the data itself, encrypted using a combination of symmetric and asymmetric algorithms. The next layer is the access control mechanism, filtering access based on predefined rules. The outermost layer comprises threat detection and response systems, constantly monitoring for anomalies and malicious activities. The merge enhances this structure by integrating the layers, enabling a unified and more effective defense against various threats.
The TruSecure and Betrusted merger aims to create a stronger CyberTrust, a crucial step in bolstering online security. This new initiative dovetails nicely with the work of a new internet security forum, new internet security forum seeks to end phishing , which is tackling the growing problem of phishing attacks. Ultimately, both efforts are vital in safeguarding our digital world from malicious actors.
The result is a seamless and comprehensive security framework for all platforms.
Future Trends and Developments
The merging of TrusSecure and Betrusted to form CyberTrust represents a significant step forward in the evolving cybersecurity landscape. Understanding future trends and developments is crucial for effectively leveraging the combined strengths of these entities and mitigating emerging threats. This analysis explores potential advancements, the positioning of CyberTrust within future challenges, and the proactive strategies necessary to address emerging threats.
Potential Future Developments
Cybersecurity is a dynamic field, constantly adapting to new threats and technologies. The future of CyberTrust hinges on its ability to anticipate and address these evolving challenges. Key developments include the increasing sophistication of cyberattacks, the proliferation of interconnected devices, and the growing importance of data privacy. CyberTrust must remain adaptable and innovative to remain effective.
Positioning for Future Challenges
The combined resources and expertise of TrusSecure and Betrusted provide CyberTrust with a strong foundation for addressing future challenges. The merged entity possesses a comprehensive understanding of various security protocols and standards, a critical asset for navigating the complexity of modern cybersecurity threats. This amalgamation positions CyberTrust to lead the industry in proactive security measures and innovation.
Emerging Threats and CyberTrust’s Response
Emerging threats, including advanced persistent threats (APTs), ransomware attacks, and the exploitation of vulnerabilities in the Internet of Things (IoT), require a multifaceted approach. CyberTrust will need to continuously update its security protocols and mechanisms to address these evolving threats. Real-world examples of successful security breaches and subsequent improvements highlight the necessity for constant adaptation. CyberTrust’s commitment to research and development will be crucial in proactively identifying and addressing emerging threats.
Potential Future Integrations and Partnerships
Collaboration is essential for effectively combating cyber threats. Future integrations and partnerships with other cybersecurity firms, government agencies, and academic institutions will be vital to sharing knowledge, best practices, and resources. Partnerships will enable the development of more comprehensive and effective security solutions. This collaboration is crucial for navigating the complexities of the evolving digital landscape. An example of a successful partnership would be a collaboration with a leading IoT device manufacturer to integrate security protocols directly into the devices, thus mitigating vulnerabilities from the source.
Furthermore, partnerships with educational institutions can foster a skilled workforce capable of addressing future challenges.
Ultimate Conclusion
The TrusSecure and Betrusted merge into CyberTrust represents a pivotal moment in cybersecurity. By integrating their core principles and expanding their reach, the combined entity aims to redefine trust in the digital realm. The implications for the future of cybersecurity are profound, offering a more secure and trustworthy online environment. The detailed exploration of security protocols, future trends, and use cases further underscores the transformative potential of this innovative merger.