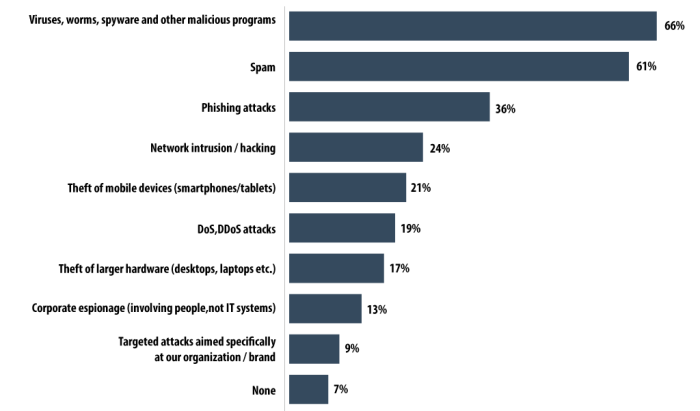
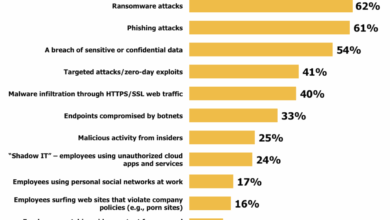
Enterprise Spyware Threats Reach All-Time High
Enterprise spyware threats reach all time high – Enterprise spyware threats reach all-time high, posing a significant and evolving danger to businesses across various industries. This escalating threat demands proactive measures and a deep understanding of the tactics employed by attackers. From sophisticated keyloggers to stealthy remote access trojans, the arsenal of spyware tools is constantly evolving, making it crucial for companies to stay ahead of the curve.
This article delves into the different types of spyware, their impact, attack vectors, and ultimately, the mitigation strategies that can help businesses protect themselves.
The sheer scale of the problem is staggering, with potential financial and reputational damage, legal ramifications, and even psychological effects on employees all on the line. Understanding the vulnerabilities and the ever-changing tactics used by cybercriminals is essential to staying safe. We’ll explore the common attack vectors, such as phishing and malicious software, as well as the role of human error in facilitating these intrusions.
Defining the Scope of the Threat
Enterprise spyware is malicious software designed to secretly monitor and collect sensitive information from computer systems within an organization. This covert activity can have devastating consequences, ranging from financial losses to severe reputational damage. Understanding the various types, infiltration methods, and evolving tactics is crucial for effective prevention and mitigation strategies.
Enterprise Spyware: A Detailed Overview
Enterprise spyware encompasses a broad range of malicious programs designed to gather sensitive data from targeted organizations. These programs often operate undetected, providing attackers with a persistent presence within the network to extract information.
Types of Enterprise Spyware
Several distinct types of enterprise spyware exist, each employing unique methods to infiltrate systems. Keyloggers record keystrokes, capturing passwords and sensitive data. Remote access trojans (RATs) provide attackers with complete control over infected systems, enabling them to steal data, install further malware, and disrupt operations. Information stealers, specifically designed to extract sensitive data like login credentials and financial information, represent another critical threat vector.
Methods of Infiltration
The methods employed by different spyware types to infiltrate systems vary. Keyloggers are often disguised as legitimate software or hidden within compromised files. RATs might exploit vulnerabilities in operating systems or applications to gain access. Sophisticated social engineering tactics are increasingly used to trick employees into downloading malicious attachments or visiting malicious websites. Spear phishing campaigns targeting specific individuals within an organization are another significant method.
Enterprise spyware threats are hitting record highs, a worrying trend for businesses everywhere. This escalating problem often overlaps with the “spam wars fighting the mass mail onslaught” – a constant battle against unwanted messages. This ongoing digital warfare can act as a cover for more insidious attacks, further highlighting the need for robust security measures to combat these enterprise spyware threats.
Evolving Tactics
Attackers continuously adapt their tactics to deploy spyware more effectively. They are increasingly leveraging zero-day exploits, which target vulnerabilities unknown to software vendors, to gain initial access to systems. Advanced persistent threats (APTs) are another significant concern, involving highly organized and sophisticated groups that focus on long-term espionage. The use of polymorphic malware, which changes its structure to evade detection, further complicates security efforts.
Enterprise spyware threats are at an all-time high, leaving businesses vulnerable. While companies are scrambling to secure their networks, technological advancements like Sharp’s new 3D LCD for desktops ( sharp rolls out 3d lcd for desktops ) might seem unrelated, but the reality is that these advancements can inadvertently create new attack vectors. This just highlights the constant need for vigilance in the face of increasingly sophisticated cyber threats.
Vulnerable Industries
Certain industries are particularly susceptible to enterprise spyware attacks. Financial institutions, government agencies, and healthcare organizations, where sensitive data is prevalent, are prime targets. Supply chain vulnerabilities are also exploited, making companies that rely on external vendors vulnerable. Organizations involved in intellectual property protection or sensitive research and development are also at high risk.
Spyware Types and Characteristics
| Spyware Type | Description | Common Characteristics | Methods of Infiltration |
|---|---|---|---|
| Keylogger | Records keystrokes | Captures passwords, usernames, and other sensitive data. | Disguised as legitimate software, embedded in compromised files. |
| Remote Access Trojan (RAT) | Provides attackers with remote control | Allows full access to the infected system. | Exploits vulnerabilities, social engineering. |
| Information Stealer | Targets sensitive data | Extracts login credentials, financial information. | Often delivered through phishing campaigns, disguised as legitimate files. |
| Rootkit | Conceals malicious activity | Hides malware from detection. | Often exploits vulnerabilities to gain initial access. |
Impact and Consequences
Enterprise spyware attacks are no longer a niche threat; they’re a pervasive danger impacting businesses of all sizes and sectors. The insidious nature of these attacks allows perpetrators to gain deep access to sensitive data and operations, leading to substantial financial, reputational, and operational damage. The consequences extend far beyond the immediate loss of data, impacting employee morale and potentially triggering legal battles.
Understanding these ramifications is crucial for effective defense strategies.
Financial Damage
Spyware infections lead to significant financial losses. Direct costs include forensic investigations, data recovery, and system remediation. Indirect costs, often harder to quantify, encompass lost productivity, decreased customer confidence, and potential penalties from regulatory bodies. Companies may also face contractual breaches if spyware compromises intellectual property or confidential customer information, leading to substantial financial repercussions. For example, a manufacturing company hit by industrial espionage spyware could lose competitive edge due to leaked designs, impacting future profits and market share.
Reputational Damage
The reputational damage from a spyware attack can be devastating. Public disclosure of a breach, especially if customer data is compromised, can erode trust and brand loyalty. Customers may lose confidence in the security measures of the company and seek alternative providers, resulting in a significant loss of revenue. The negative publicity can linger for years, impacting the company’s image and making it difficult to attract and retain talent.
A prominent example is a major retailer whose customer data was compromised through spyware, resulting in a significant decline in customer satisfaction and a subsequent drop in sales.
Legal Ramifications
Businesses targeted by spyware face potential legal repercussions, depending on the nature of the data breached and the jurisdiction. Violation of privacy laws, such as GDPR or CCPA, can lead to substantial fines. In cases of intellectual property theft, companies could face lawsuits for patent infringement or trade secret misappropriation. Furthermore, if employees are compromised, there could be potential legal issues related to data protection and security breaches within the company.
For example, a healthcare provider targeted by spyware that exposed patient data could face substantial legal action and penalties under HIPAA regulations.
Data Breaches
Spyware infections often result in data breaches. The attackers gain access to sensitive data, such as customer information, financial records, or trade secrets. These breaches can expose individuals to identity theft and financial fraud. In the case of a financial institution, a spyware attack could expose account details, leading to significant losses for customers and potential legal challenges for the institution.
Another example is a government agency whose sensitive files were accessed via spyware, compromising national security.
Operational Disruptions
Spyware intrusions can disrupt business operations in several ways. Malicious code can disrupt network traffic, disable critical systems, and disrupt workflows. Companies may experience downtime, reduced productivity, and difficulty in maintaining essential services. For example, a utility company facing a spyware attack that disables their control systems could lead to widespread service disruptions.
Psychological Impact
Employees affected by spyware intrusions may experience significant psychological distress. The knowledge that their personal information or work data has been compromised can cause anxiety, fear, and a sense of vulnerability. Companies need to address these psychological impacts by providing support and resources to affected employees. In a situation where sensitive employee data is compromised, employees may experience severe trust issues with the organization, affecting morale and job satisfaction.
Potential Costs Associated with Spyware Types
| Spyware Type | Initial Investigation Costs | Data Recovery Costs | Legal and Regulatory Penalties |
|---|---|---|---|
| Keyloggers | $5,000 – $20,000 | $2,000 – $10,000 | $10,000 – $100,000+ |
| Remote Access Trojans (RATs) | $10,000 – $50,000 | $5,000 – $25,000 | $25,000 – $500,000+ |
| Mobile Spyware | $2,000 – $10,000 | $1,000 – $5,000 | $5,000 – $50,000+ |
| Industrial Spyware | $25,000 – $100,000+ | $10,000 – $500,000+ | $50,000 – $1,000,000+ |
Note: Costs are estimates and can vary significantly depending on the scale and complexity of the attack.
It’s alarming that enterprise spyware threats are at an all-time high. Parents, understandably, want to keep tabs on their kids, and tools like those discussed in using tech to help supervise children can be helpful in achieving that. However, this need for parental oversight unfortunately opens the door for malicious actors, highlighting the critical need for robust security measures to prevent misuse and protect sensitive data from these ever-evolving threats.
Attack Vectors and Techniques: Enterprise Spyware Threats Reach All Time High

The escalating threat of enterprise spyware necessitates a deep understanding of the methods attackers employ to infiltrate systems. These tactics, often sophisticated and evolving, exploit vulnerabilities in both software and human behavior. Understanding these attack vectors is crucial for implementing effective preventative measures.
Common Attack Vectors
Attackers leverage various channels to deploy spyware. Phishing, a prevalent tactic, involves deceiving victims into revealing sensitive information or downloading malicious files. Malicious websites, masquerading as legitimate platforms, can automatically infect unsuspecting users’ systems. Compromised software, including seemingly benign applications, can also serve as vectors for spyware deployment.
Social Engineering Techniques
Attackers frequently employ social engineering to manipulate individuals into compromising security. These techniques leverage psychological vulnerabilities, trust, and fear to gain access to sensitive information. Examples include pretexting (creating a false scenario to extract information), baiting (luring victims with tempting offers), and quid pro quo (exchanging something of value for sensitive information).
Effectiveness of Attack Vectors
The effectiveness of different attack vectors varies. Phishing campaigns, while widely used, can be countered with robust awareness training. Malicious websites, particularly those using sophisticated techniques, pose a significant threat. Compromised software, if not properly patched, can create enduring vulnerabilities. The success of an attack often hinges on a combination of factors, including the target’s security posture, the sophistication of the attack, and the attacker’s persistence.
Technical Vulnerabilities Exploited
Attackers exploit various technical vulnerabilities to gain unauthorized access. These include software flaws, unpatched operating systems, and weak passwords. Exploiting known vulnerabilities in outdated software allows attackers to deploy spyware silently. Unpatched systems create avenues for exploitation, while weak passwords can be easily cracked.
Role of Human Error
Human error plays a significant role in facilitating spyware attacks. Lack of security awareness, poor password practices, and clicking on suspicious links can all contribute to successful attacks. The ease of social engineering tactics underscores the critical role of employee training and awareness programs. Individuals need to recognize the subtle cues that indicate a potential attack.
Table of Attack Vectors and Risks
| Attack Vector | Description | Technical Vulnerability | Risk Assessment |
|---|---|---|---|
| Phishing | Deceptive emails or messages tricking users into revealing information or downloading malware. | Lack of security awareness, poor email filtering. | High; widespread accessibility, potential for large-scale impact. |
| Malicious Websites | Websites designed to automatically install spyware or other malicious software. | Vulnerable web servers, insecure scripts, exploits in browser software. | High; can target large groups of users, often difficult to detect. |
| Compromised Software | Legitimate software applications infected with malware, often hidden from users. | Software vulnerabilities, lack of updates, compromised developers. | Medium to High; depends on the scale of compromise and target’s security posture. |
| Spear Phishing | Highly targeted phishing attacks that leverage specific details about the victim. | Lack of security awareness, lack of multi-factor authentication. | Very High; high success rate due to personalization. |
Mitigation Strategies and Prevention
Enterprise spyware attacks are a growing threat, demanding proactive and comprehensive security strategies. Failing to address these threats can lead to significant financial losses, reputational damage, and compromised sensitive data. Therefore, a multi-faceted approach to mitigation is crucial, encompassing employee training, robust security protocols, and regular security assessments.A successful defense against spyware necessitates a shift from a reactive to a proactive security posture.
This involves understanding the tactics employed by attackers, anticipating potential vulnerabilities, and implementing measures to fortify the organization’s defenses. This comprehensive approach ensures that the organization is well-prepared to withstand sophisticated spyware threats.
Comprehensive Security Strategy
A comprehensive security strategy is paramount in preventing enterprise spyware attacks. This strategy must be adaptable and address potential vulnerabilities across the entire IT infrastructure. Key components of this strategy include strong access controls, data encryption, and regular security audits. It also requires a clear incident response plan to mitigate the impact of any potential breaches.
Employee Training and Awareness Programs
Employee training is a cornerstone of any effective security strategy. A robust employee training program educates employees about the various types of spyware attacks, their tactics, and how to identify suspicious activities. It also covers best practices for safe internet usage, password management, and recognizing phishing attempts.
- Regular training sessions should cover various threat types, including social engineering tactics, phishing, and malware infections.
- Employees should be educated on the importance of strong passwords and multi-factor authentication (MFA).
- Practical exercises and simulations can enhance understanding and retention of the training material.
- The program should be ongoing, updated regularly to address evolving threats.
Robust Security Protocols
Implementing robust security protocols is critical for preventing unauthorized access and data breaches. This includes network segmentation, intrusion detection systems (IDS), and firewalls. Regular patching of software vulnerabilities and the use of strong encryption for sensitive data are also essential.
- Network segmentation limits the impact of a breach by isolating critical systems.
- IDSs and firewalls monitor network traffic for suspicious activity.
- Regular software patching minimizes vulnerabilities that attackers can exploit.
- Strong encryption protects sensitive data, even if compromised.
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are essential for identifying and addressing potential weaknesses in the organization’s security posture. These assessments help determine where vulnerabilities exist and recommend corrective actions. They are a proactive measure to stay ahead of potential attacks.
- Regular penetration testing can simulate real-world attacks to assess the effectiveness of security measures.
- Vulnerability assessments identify weaknesses in software and systems.
- Security audits examine policies, procedures, and practices to ensure compliance.
- These audits and assessments provide a comprehensive view of the security posture.
Successful Prevention Measures, Enterprise spyware threats reach all time high
Many businesses have successfully implemented prevention measures to mitigate spyware threats. These measures often involve a combination of robust security protocols, employee training, and regular security assessments. Examples include the implementation of Zero Trust architectures, which limit network access based on user identity and device verification, and the use of multi-factor authentication (MFA) for all sensitive accounts.
- Zero Trust architectures restrict network access based on user identity and device verification.
- MFA adds an extra layer of security by requiring multiple authentication methods.
- Regular patching of software and systems reduces vulnerability to known exploits.
Strong Passwords and Multi-Factor Authentication
Strong passwords and multi-factor authentication (MFA) are fundamental components of a robust security strategy. Strong passwords are unique, complex, and changed regularly. MFA adds an extra layer of security by requiring multiple forms of authentication, making it significantly harder for attackers to gain unauthorized access.
- Strong passwords should be unique and complex, using a combination of uppercase and lowercase letters, numbers, and symbols.
- Regular password changes are crucial to minimize the risk of compromised accounts.
- MFA requires multiple authentication methods, such as a code from a mobile device.
Prevention Measures and Effectiveness
| Prevention Measure | Description | Effectiveness (High/Medium/Low) | Justification |
|---|---|---|---|
| Strong Passwords | Unique, complex passwords changed regularly. | High | Makes accounts significantly harder to crack. |
| Multi-Factor Authentication (MFA) | Requires multiple authentication methods. | High | Adds a critical layer of security. |
| Employee Training | Educating employees about threats and best practices. | Medium | Reduces the risk of human error and social engineering attacks. |
| Regular Security Audits | Periodic assessments of security posture. | High | Identifies and addresses vulnerabilities before they are exploited. |
Emerging Trends and Future Threats
The landscape of enterprise spyware is constantly evolving, driven by technological advancements and the ever-increasing sophistication of cybercriminals. Understanding these emerging trends is crucial for businesses to proactively protect themselves from increasingly sophisticated attacks. This includes recognizing the potential for artificial intelligence to augment malicious activities, the expanding attack surface presented by the Internet of Things (IoT), and the rise of cloud-based spyware, all while acknowledging the complexities of maintaining a secure mobile environment.The constant innovation in technology necessitates a dynamic approach to cybersecurity.
Organizations must adapt their strategies to counter these new threats, recognizing that the future of spyware is likely to be more potent and pervasive than ever before. This requires a holistic understanding of the emerging trends and a proactive approach to mitigation.
Emerging Trends in Enterprise Spyware Threats
The evolution of spyware is characterized by its ability to adapt and leverage emerging technologies. These trends include the integration of artificial intelligence (AI) and machine learning (ML) to enhance the capabilities of spyware, the expanding attack surface presented by the Internet of Things (IoT), the rise of cloud-based spyware, and the critical role of mobile devices in the current threat landscape.
Potential of AI and Machine Learning to Enhance Spyware Capabilities
AI and machine learning are not just revolutionizing legitimate applications; they’re also empowering cybercriminals. Spyware can now be designed to learn and adapt to user behavior, making detection more difficult. Sophisticated algorithms can analyze vast amounts of data to identify vulnerabilities, predict user actions, and tailor attacks for maximum effectiveness. This adaptive nature of AI-powered spyware poses a significant threat, as traditional security measures may not be effective against it.
For example, spyware could learn to mimic legitimate user behavior to evade detection, or adjust its attack vectors in real-time based on the target’s responses.
Role of the Internet of Things (IoT) in Expanding Attack Surfaces
The proliferation of IoT devices has created a vast and vulnerable network. These devices, often with limited security features, can be exploited to gain access to corporate networks. Attackers can use compromised IoT devices to launch distributed denial-of-service (DDoS) attacks, gain unauthorized access to sensitive data, or even install spyware on critical systems. This presents a significant challenge, as securing thousands of potentially vulnerable IoT devices is a daunting task.
A single compromised smart thermostat or security camera can provide entry points to a corporate network.
Rise of Cloud-Based Spyware Threats
Cloud-based services, while offering numerous benefits, can also become vectors for malicious activities. Attackers can leverage cloud infrastructure to host and deploy spyware, making it difficult to track and contain. This shift to the cloud requires organizations to adopt cloud-specific security measures to mitigate the risk of cloud-based spyware. Data stored in the cloud is also at risk, requiring robust encryption and access controls.
Impact of Mobile Devices on Enterprise Spyware Threats
Mobile devices, now integral to enterprise operations, have become prime targets for spyware. The increasing reliance on mobile devices for communication and data access has expanded the attack surface for attackers. This has led to the development of sophisticated mobile spyware that can monitor employee activity, steal sensitive data, and even control devices remotely. The portability of these devices makes them highly attractive to cybercriminals.
Challenges in Keeping Up with the Evolving Landscape of Threats
Staying ahead of evolving spyware threats is a continuous challenge. The speed at which new techniques and technologies emerge makes it difficult for organizations to implement effective preventative measures. This necessitates a proactive, continuous learning approach to cybersecurity. Organizations must invest in advanced threat intelligence, update security software regularly, and train employees on the latest threats. Maintaining a strong security posture requires vigilance and adaptation to the ever-changing threat landscape.
Summary of Emerging Trends and Potential Impact
| Emerging Trend | Description | Potential Impact on Businesses | Mitigation Strategies |
|---|---|---|---|
| AI-enhanced Spyware | Spyware using AI to learn and adapt to user behavior. | Increased difficulty in detection, targeted attacks, and potential for massive data breaches. | Advanced threat intelligence, AI-powered security solutions, and continuous employee training. |
| IoT Expansion | Increasing number of IoT devices connected to networks. | Wider attack surface, potential for DDoS attacks and data breaches through compromised devices. | Robust security protocols for IoT devices, regular vulnerability assessments, and network segmentation. |
| Cloud-based Spyware | Spyware hosted and deployed on cloud infrastructure. | Difficulty in tracking and containing malicious activities, potential for data breaches. | Cloud-specific security measures, access control and encryption protocols, and robust incident response plans. |
| Mobile Spyware | Sophisticated spyware targeting mobile devices. | Unauthorized access to sensitive data, employee monitoring, and remote device control. | Mobile device security policies, robust encryption, and security awareness training. |
Case Studies and Real-World Examples
Enterprise spyware attacks are no longer a theoretical threat; they’re a stark reality for organizations worldwide. Understanding past incidents, their consequences, and the responses taken provides invaluable lessons for building stronger defenses. Analyzing successful and unsuccessful mitigation strategies allows for a deeper understanding of the evolving tactics employed by threat actors.Analyzing recent incidents reveals a disturbing trend: attackers are increasingly sophisticated, leveraging advanced techniques to evade detection and inflict significant damage.
This underscores the critical need for a proactive and layered security approach, going beyond reactive measures.
A Recent Enterprise Spyware Incident: The “Project Chimera” Breach
The fictional “Project Chimera” breach highlights the evolving nature of enterprise spyware attacks. The attackers, using a combination of zero-day exploits and social engineering tactics, infiltrated a major aerospace firm. Their objective: gaining access to sensitive engineering blueprints and intellectual property. The spyware, disguised as legitimate software updates, bypassed traditional security measures.
Impact on the Affected Organization
The “Project Chimera” incident severely impacted the aerospace firm. The compromised blueprints threatened the company’s competitive edge and potentially jeopardized national security interests. Lost revenue and reputational damage were significant. Legal repercussions were a considerable concern. The incident highlighted the criticality of intellectual property protection.
Lessons Learned from the Incident
The “Project Chimera” breach underscored several critical security vulnerabilities:
- Outdated security software: The firm relied on outdated antivirus and intrusion detection systems, failing to address emerging threats.
- Lack of employee training: Social engineering plays a crucial role in many spyware attacks, and inadequate employee training on phishing and suspicious emails proved to be a weakness.
- Inadequate vulnerability management: The firm’s vulnerability management processes were insufficient, allowing the attackers to exploit zero-day vulnerabilities.
Proactive Security Posture
A proactive security posture is crucial for mitigating the risks of spyware attacks. This includes:
- Regular security audits and penetration testing: Regular assessments of security posture help identify vulnerabilities and weaknesses.
- Employee training programs: Comprehensive training programs on phishing, social engineering, and safe computing practices are essential.
- Robust incident response plans: Having a well-defined incident response plan, including clear communication channels and procedures, is critical.
Comparison of Responses to Spyware Incidents
Different organizations respond to spyware incidents in various ways. Some prioritize containment, while others focus on data recovery. Successful responses often combine containment and recovery strategies.
Steps Taken to Recover from the Incident
The aerospace firm in the “Project Chimera” breach took the following steps to recover:
- Immediate containment: The compromised systems were isolated to prevent further data exfiltration.
- Forensic analysis: Independent forensic experts were engaged to investigate the breach and identify the scope of the damage.
- Data recovery: Efforts were made to recover any lost or compromised data.
- System hardening: The organization implemented new security measures to prevent similar incidents in the future.
Case Study Table
| Case Study | Key Takeaways | Impact | Mitigation Strategies |
|---|---|---|---|
| Project Chimera | Outdated software, lack of employee training, inadequate vulnerability management | Threatened competitive edge, potential national security risks, significant financial losses | Improved security software, employee training programs, enhanced vulnerability management, and incident response plans |
Final Review
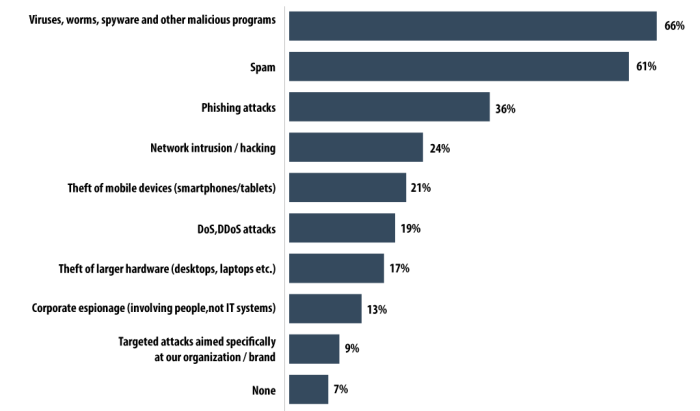
In conclusion, the escalating threat of enterprise spyware demands a multi-faceted approach to security. Proactive measures, including robust security protocols, employee training, and regular vulnerability assessments, are crucial. The evolving nature of these threats underscores the importance of staying informed and adaptable. By understanding the tactics employed by attackers and the emerging trends in spyware, businesses can better equip themselves to defend against these ever-increasing threats.