Yahoo EarthLink Build Bulwark Against Spoofing
Yahoo EarthLink build bulwark against spoofing, a critical endeavor in the evolving digital landscape. Spoofing, a technique that deceptively impersonates individuals or entities, poses significant risks to users. From email phishing to phone scams and website impersonation, the methods are diverse and the consequences can be severe, encompassing financial losses, identity theft, and privacy violations. This comprehensive exploration delves into the historical infrastructure of Yahoo and EarthLink, examining their security measures and vulnerabilities, and analyzing how they’re building a robust defense against these deceptive tactics.
This discussion will cover the various types of spoofing, the vulnerabilities in Yahoo and EarthLink’s past systems, and the specific security measures being implemented to fortify against these attacks. We’ll also analyze the evolution of anti-spoofing techniques, highlighting the shift from historical approaches to modern solutions and their impact on user safety. Ultimately, this analysis aims to provide a clear understanding of the measures taken to combat spoofing and the potential future developments in this critical area of cybersecurity.
Defining Spoofing and its Methods

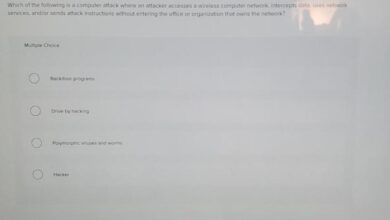
Spoofing, a deceptive practice, involves masquerading as a legitimate entity to gain unauthorized access or manipulate information. It exploits vulnerabilities in various systems and communication channels, leading to significant security risks and financial losses. This article delves into the diverse methods of spoofing, highlighting their techniques, implications, and the crucial steps to safeguard against them.Spoofing techniques are diverse and sophisticated, targeting individuals, organizations, and critical infrastructure.
They rely on creating a false impression of legitimacy to trick victims into revealing sensitive information or performing actions that benefit the attacker. The consequences of spoofing attacks can range from financial fraud to identity theft and reputational damage.
Types of Spoofing Attacks
Spoofing attacks manifest in various forms, each employing specific methods to achieve their objectives. Understanding these types is crucial to developing effective countermeasures.
Email Spoofing
Email spoofing involves forging the “From” address of an email message to make it appear as if it originated from a different sender. This is often used to trick recipients into believing the email is legitimate, potentially leading to phishing attacks, malware distribution, or other malicious activities. Criminals may impersonate trusted individuals or organizations to gain access to sensitive data.
For example, an email that appears to come from a bank asking for account details could be a spoofed email.
Phone Call Spoofing
Phone call spoofing involves altering the caller ID information to make it appear as if the call originated from a different number. This can be used to make fraudulent calls, harass victims, or gain access to sensitive information. This type of spoofing often leverages caller ID spoofing technology to create a false impression of origin. A common example is a spoofed call from a government agency demanding immediate payment.
Website Spoofing
Website spoofing involves creating a fake website that mimics a legitimate website. This is frequently employed in phishing attacks to collect sensitive information from unsuspecting victims. The fake website might look identical to the real one, making it difficult to detect. For example, a fake online banking website could deceive users into entering their login credentials.
Yahoo and EarthLink are bolstering their defenses against spoofing attacks, a critical step in online security. This proactive approach aligns perfectly with recent recommendations from the NCSP task force, which focuses on strengthening internet security protocols. Their recommendations, detailed in the ncsp task force makes security recommendations , highlight the importance of robust anti-spoofing measures. Ultimately, this effort by Yahoo and EarthLink contributes to a more secure online environment for everyone.
Technical Mechanisms Behind Spoofing
Spoofing techniques often exploit vulnerabilities in network protocols and security systems. Understanding the technical mechanisms is crucial for developing effective countermeasures.
IP Address Spoofing
IP address spoofing involves sending packets with a forged source IP address. This technique is used to hide the true identity of the attacker and evade detection. This often involves altering the IP header of a network packet.
DNS Spoofing
DNS spoofing, also known as DNS cache poisoning, involves altering the DNS records to redirect users to malicious websites. This technique exploits the way DNS servers resolve domain names to IP addresses. This is often employed to redirect users to fraudulent websites.
Impact of Spoofing Attacks
Spoofing attacks can have a wide range of negative impacts, affecting individuals, organizations, and the broader digital landscape. These consequences vary based on the type of spoofing and the specific target.
| Type of Spoofing | Description | Example | Impact |
|---|---|---|---|
| Email Spoofing | Forging the “From” address of an email. | An email pretending to be from your bank asking for login credentials. | Phishing, malware distribution, identity theft. |
| Phone Call Spoofing | Altering caller ID information. | A fraudulent call pretending to be from a government agency. | Fraudulent calls, harassment, access to sensitive information. |
| Website Spoofing | Creating a fake website mimicking a legitimate one. | A fake online banking website. | Phishing attacks, data breaches, identity theft. |
Understanding Yahoo and EarthLink’s Infrastructure
Yahoo and EarthLink, once titans of the internet and email landscape, faced significant security challenges. Their historical infrastructure, while innovative for their time, proved vulnerable to modern-day attacks like spoofing. Examining their past practices reveals crucial lessons about evolving security needs in the digital age. Understanding their architecture and security measures helps illuminate the path towards more robust systems.Yahoo and EarthLink’s email and internet services, during their heyday, relied on a blend of technologies and security protocols.
Yahoo and EarthLink are reportedly strengthening their defenses against spoofing attempts. This proactive measure comes as a new variant of the MyDoom worm, detailed in this new MyDoom variant stalks more victims report, is actively targeting users. Hopefully, these preventative measures will help mitigate the impact of this evolving threat, ultimately safeguarding users from these malicious attacks.
These systems, though capable, lacked the sophisticated defense mechanisms required to counter the increasing sophistication of online threats. Analysis of their vulnerabilities sheds light on the evolving nature of cyberattacks and the ongoing need for adaptive security measures.
Historical Infrastructure Overview
Yahoo and EarthLink, in their earlier iterations, utilized a layered approach to internet service delivery. This approach involved a mix of proprietary technologies and standard protocols. Their infrastructure wasn’t built with the same level of security sophistication as modern systems. Their email services were designed around the then-prevalent protocols, making them susceptible to exploitation.
Security Measures in Place
Yahoo and EarthLink, while having some security measures in place, did not have the comprehensive approach to security seen in modern systems. Early measures often relied on simple access controls and rudimentary spam filters. These measures were effective against some threats, but they lacked the proactive defenses and sophisticated threat intelligence tools found in today’s architectures. The evolution of cyberattacks rendered these initial defenses increasingly inadequate.
Architectural Design Choices
The architectural design choices made by Yahoo and EarthLink during their early stages might have contributed to their vulnerabilities. The reliance on a monolithic architecture, common in those times, potentially limited flexibility and adaptability to evolving threats. Scaling and maintenance could also have been a challenge in the face of increased user demand and sophisticated attacks. Furthermore, the absence of sophisticated threat modeling and penetration testing methodologies likely contributed to vulnerabilities.
Protocols and Technologies Employed
The protocols and technologies employed by Yahoo and EarthLink, while functional at the time, were not designed with the same level of security robustness as current systems. Early versions of SMTP, POP, and IMAP were used, alongside proprietary protocols for their internal systems. These older protocols were vulnerable to various exploits that could not be easily addressed within the design of the time.
The reliance on these protocols made them more susceptible to attacks than modern, more secure, protocols.
Vulnerabilities in the Past
The inherent limitations of the technologies used by Yahoo and EarthLink were a significant factor in their vulnerability to spoofing attacks. These included inadequate authentication mechanisms, lack of robust spam filtering, and a lack of proactive threat intelligence. Additionally, the scaling challenges in their systems also contributed to their vulnerability to attacks.
Comparative Analysis
| Service | Key Technologies | Security Features | Vulnerabilities (Historical) |
|---|---|---|---|
| Yahoo Email | SMTP, POP3, IMAP | Basic authentication, spam filters | Vulnerable to phishing, email spoofing, and exploits due to protocol limitations and lack of advanced security measures. |
| EarthLink Email | SMTP, POP3, IMAP, proprietary protocols | Basic authentication, rudimentary spam filters | Similar vulnerabilities to Yahoo, exacerbated by proprietary protocols potentially lacking the same security standards as open protocols. |
| Yahoo Internet Access | Various networking protocols | Firewalling, access controls | Vulnerable to denial-of-service attacks and exploits in networking protocols; less focus on user authentication compared to today’s standards. |
| EarthLink Internet Access | Various networking protocols | Firewalling, access controls | Similar vulnerabilities to Yahoo, potentially exacerbated by less sophisticated infrastructure and less robust security measures. |
Exploring “Bulwark” Against Spoofing
A bulwark against spoofing in cybersecurity is a comprehensive strategy designed to create impenetrable defenses against malicious attempts to impersonate legitimate entities. This approach necessitates a multi-layered defense system that safeguards various aspects of communication and infrastructure, from email authentication to network security protocols. Effective spoofing prevention requires proactive measures, anticipating potential vulnerabilities and implementing safeguards before attacks occur.
Defining a Cybersecurity Bulwark
A bulwark in cybersecurity is a robust and multi-faceted defense mechanism that actively resists malicious activities, like spoofing. It’s not just about reacting to attacks; it’s about creating a system that makes attacks significantly more difficult and less effective. A strong bulwark against spoofing combines various security measures to form an integrated and impenetrable shield, protecting against various spoofing methods.
Security Measures to Constitute a Bulwark
Proactive measures are crucial in preventing spoofing. These include enhanced email authentication protocols, improved domain security practices, and fortified network security measures. A strong bulwark encompasses all these aspects.
Email Authentication Strengthening
Robust email authentication protocols are paramount in combating spoofing. These protocols verify the sender’s identity, ensuring that emails are genuinely coming from the claimed source. Implementations like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance) significantly enhance email security.
Domain Security Enhancements, Yahoo earthlink build bulwark against spoofing
Securing the domain name system (DNS) is critical in preventing spoofing. Ensuring proper DNS records, employing DNSSEC (DNS Security Extensions) for authentication, and regularly monitoring DNS for suspicious activity can drastically reduce the risk of spoofing. DNS records are vital for establishing the legitimacy of a domain and its associated services.
Network Security Fortification
Network security plays a crucial role in defending against spoofing attacks. Implementing firewalls, intrusion detection systems, and strong access controls can prevent malicious actors from gaining unauthorized access to systems and impersonating legitimate entities.
Yahoo and EarthLink’s efforts to combat spoofing are definitely a step in the right direction. It’s crucial for online security, but the increasing sophistication of identity theft, like what’s addressed in the new law boosting prison time for ID theft, new law boosts prison time for id theft , highlights the need for these measures. Ultimately, these proactive security measures, combined with stricter legal frameworks, help build a more secure online environment for everyone.
Table of Security Measures Against Spoofing
| Security Measure | Description | Implementation Steps | Expected Outcome |
|---|---|---|---|
| SPF Record | Defines which mail servers are authorized to send emails on behalf of a domain. | Configure SPF records in DNS, specifying authorized mail servers. | Reduces email spoofing by preventing unauthorized mail servers from sending emails using the domain’s address. |
| DKIM | Provides digital signatures for emails to verify the sender’s identity and prevent message tampering. | Configure DKIM records in DNS, creating and signing emails. | Further enhances email authentication by verifying the origin and integrity of emails. |
| DMARC | Policies to define how to handle emails that fail SPF and DKIM checks. | Configure DMARC records in DNS, specifying actions for policy violations. | Provides a comprehensive framework for email authentication, providing feedback on failed authentication attempts. |
| DNSSEC | Secures DNS records, preventing manipulation by malicious actors. | Implement DNSSEC on DNS servers, validating DNS responses. | Protects against DNS spoofing, ensuring the integrity and authenticity of DNS lookups. |
Comparing Historical and Modern Approaches
Early internet email security relied heavily on sender reputation and trust. Yahoo and EarthLink, like many providers, relied on user feedback and community reporting to identify and block spam and spoofed emails. Modern approaches leverage sophisticated authentication protocols and infrastructure improvements, significantly reducing spoofing success rates.The historical methods, while rudimentary, provided a baseline for addressing spoofing. However, the evolution of internet infrastructure and the rise of sophisticated attackers necessitated more robust and automated countermeasures.
This evolution reflects a shift from reactive measures to proactive and preventative strategies.
Historical Security Measures
Early email security focused on simple methods like sender reputation and community reporting. These approaches were often reactive, responding to identified spoofing attempts rather than proactively preventing them. Filters were frequently rule-based, relying on s or patterns to flag potentially malicious emails. User reports played a crucial role in identifying and blocking spam and spoofed messages. However, these methods lacked the granularity and sophistication of modern authentication protocols.
Modern Anti-Spoofing Techniques
Modern anti-spoofing strategies utilize advanced authentication protocols to verify the sender’s identity and the integrity of the email. These methods leverage standards like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance). These protocols require the sender’s domain to publish information about authorized mail servers, ensuring that emails originate from legitimate sources.
This approach is more preventative, aiming to stop spoofing attempts before they reach the recipient.
Evolution of Email Authentication Protocols
Email authentication protocols have significantly evolved from basic sender reputation to sophisticated verification methods. Early approaches focused on simple blacklists and whitelists. SPF, DKIM, and DMARC represent a significant advancement, allowing for more precise verification of email origins. This evolution has made spoofing attempts more difficult and has increased the reliability of email delivery. The transition reflects a move from reactive measures to a more proactive and automated approach.
Impact of Internet Infrastructure Evolution
The evolution of internet infrastructure has significantly impacted spoofing attempts. The increase in email volume and the proliferation of malicious actors have necessitated more sophisticated methods to combat spoofing. The rise of cloud-based email services and the expansion of the internet itself have created new avenues for spoofing, which in turn drives the development of more sophisticated countermeasures.
The dynamic nature of the internet and the ever-evolving threat landscape are major factors in the continuous development of anti-spoofing technologies.
Comparison Table
| Feature | Historical Approach | Modern Approach | Improvements |
|---|---|---|---|
| Sender Verification | Sender reputation, community reports, simple filters | SPF, DKIM, DMARC, multi-factor authentication | Increased accuracy and reliability in verifying sender identity, reduced reliance on reactive measures. |
| Email Volume Management | Rule-based filters, blacklisting | Advanced filtering algorithms, machine learning, real-time analysis | Improved efficiency and scalability to handle massive email volumes, automated threat detection and mitigation. |
| Security Infrastructure | Basic infrastructure with limited monitoring | Robust infrastructure with advanced security measures, distributed systems | Enhanced resilience and adaptability to sophisticated attacks, increased protection against spoofing attempts. |
| Attack Response | Reactive, responding to incidents | Proactive, preventative, and automated responses | Significant reduction in the time taken to detect and mitigate spoofing attacks. |
Analyzing the Impact of Spoofing on Users: Yahoo Earthlink Build Bulwark Against Spoofing
Spoofing, the act of masquerading as a legitimate entity, can have devastating consequences for individuals. It undermines trust in online communication and transactions, leading to a wide range of negative impacts. From financial losses and identity theft to psychological distress and the spread of harmful scams, the repercussions of spoofing are far-reaching and require robust security measures to mitigate.
Financial Losses Due to Spoofing
Spoofing often serves as a gateway for financial fraud. Criminals exploit vulnerabilities in systems to gain unauthorized access to accounts, leading to significant financial losses for victims. This can manifest in various forms, from unauthorized fund transfers to the theft of credit card information. Criminals often employ sophisticated tactics, leveraging stolen credentials or creating convincing imitations of legitimate services.
- Unauthorized transactions on bank accounts and credit cards.
- Theft of online payment information like PayPal or cryptocurrency wallets.
- Loss of funds through fraudulent investments or schemes presented as legitimate opportunities.
- Scams involving fake invoices or bills designed to trick individuals into making payments to fraudulent entities.
Identity Theft and Privacy Violations
Spoofing can directly lead to identity theft, where criminals use stolen personal information to impersonate victims. This can result in severe consequences, ranging from the opening of fraudulent accounts to the damage to creditworthiness. Compromised personal data can also be used to gain access to sensitive information, leading to violations of privacy and potentially life-altering repercussions.
- Opening fraudulent bank accounts or credit lines in the victim’s name.
- Applying for loans or credit cards without the victim’s knowledge or consent.
- Accessing personal information such as social security numbers, driver’s licenses, or medical records.
- Using stolen personal information to file fraudulent tax returns.
Psychological Effects of Spoofing
The emotional toll of spoofing can be significant. Victims often experience feelings of betrayal, anger, anxiety, and even depression. The violation of trust and the fear of further exploitation can have lasting psychological consequences. The knowledge that personal information has been compromised can significantly impact an individual’s sense of security and well-being.
- Feeling of vulnerability and distrust in online interactions.
- Anxiety and stress related to the fear of future attacks.
- Depression and feelings of helplessness due to the extent of the damage.
- Difficulty trusting others, even in legitimate relationships.
Spoofing as a Conduit for Phishing and Fraudulent Activities
Spoofing is a crucial element in phishing scams, allowing perpetrators to create a deceptive environment. By impersonating legitimate entities, spoofers can trick individuals into revealing sensitive information. This can lead to further fraudulent activities, such as identity theft and financial loss.
- Creating fake websites that mimic legitimate online services to steal login credentials.
- Sending fraudulent emails or messages that appear to be from trusted sources.
- Making unauthorized phone calls or text messages pretending to be from banks or other financial institutions.
- Exploiting vulnerabilities in social media platforms to spread phishing links and fraudulent content.
Potential Future Developments
The fight against spoofing is an ongoing evolution, constantly adapting to new techniques and technologies. As cybersecurity threats become more sophisticated, so too must the defenses. Future developments in anti-spoofing technology will likely focus on proactive measures, predictive analysis, and a more holistic approach to security.Future anti-spoofing strategies will increasingly leverage the power of machine learning and artificial intelligence to identify patterns and anomalies indicative of spoofing attempts.
This proactive approach is crucial for mitigating the impact of emerging spoofing methods.
Artificial Intelligence and Machine Learning in Spoofing Detection
Artificial intelligence (AI) and machine learning (ML) algorithms can analyze vast amounts of data to identify subtle patterns and anomalies that traditional methods might miss. These algorithms can be trained on historical spoofing attempts, email headers, and network traffic to develop models that predict and identify spoofing attempts in real-time. For example, a sophisticated AI model could analyze sender email addresses, IP addresses, and the content of emails for anomalies, flags that indicate potential spoofing, and flag potentially fraudulent emails or websites.
By learning from past examples, AI systems can adjust their models to detect more sophisticated attacks as they emerge.
Emerging Trends in Cybersecurity
Emerging trends in cybersecurity, such as the increased use of decentralized identity systems and blockchain technology, can significantly impact the fight against spoofing. Decentralized identity systems, which rely on cryptographic keys and verifiable credentials, can help to reduce the reliance on centralized servers and databases, making it harder for spoofers to impersonate users. Blockchain technology, with its inherent transparency and immutability, can be used to create tamper-proof records of email authentication and user identity.
This makes it harder to forge or manipulate information.
New Protocols and Technologies for Enhanced Security
New protocols and technologies are continually being developed to enhance email security and combat spoofing. One such area of focus is enhancing email authentication protocols, such as DomainKeys Identified Mail (DKIM), Sender Policy Framework (SPF), and Domain-based Message Authentication, Reporting & Conformance (DMARC). These protocols work together to verify the sender’s identity and help prevent spoofing. Further developments in these protocols could include more robust mechanisms for verifying the authenticity of digital signatures and certificates.
Future of Email Authentication Protocols
Email authentication protocols are critical for combating spoofing. The future of these protocols will likely involve a combination of existing and emerging technologies to create a more comprehensive and resilient system. The development of new, more sophisticated methods of authentication, combined with stronger verification processes for email addresses and domains, will be crucial for maintaining the integrity of email communication.
This will likely involve improvements in how email servers interact and share information about the legitimacy of senders. The inclusion of advanced algorithms to analyze and predict fraudulent behavior could further strengthen these protocols. Furthermore, the adoption of end-to-end encryption for email communication could add another layer of security, making it harder for attackers to intercept and manipulate emails.
Final Summary

In conclusion, Yahoo and EarthLink’s commitment to building a “bulwark” against spoofing is crucial in safeguarding users from increasingly sophisticated attacks. The evolution of their security measures, from historical vulnerabilities to modern anti-spoofing techniques, underscores the dynamic nature of cybersecurity. Understanding the diverse methods of spoofing, the historical and modern approaches, and the impact on users provides a comprehensive picture of the ongoing battle against these deceptive tactics.
This analysis highlights the importance of continuous vigilance and adaptation in the ever-changing digital landscape.