Lycos Europes DDoS Spam Strategy
Lycos Europe aims to thwart spammers with DDoS attacks, a controversial approach that raises significant questions about the future of online security. This strategy, while potentially effective in the short term, carries considerable risks and ethical implications. The move could set a dangerous precedent, prompting a debate about the appropriateness of using such aggressive tactics against online criminals.
This in-depth analysis explores the rationale behind Lycos Europe’s choice, examining the potential effectiveness, legal and ethical considerations, and the broader impact on the online environment. We’ll also consider alternative strategies and future trends in spam mitigation.
Lycos Europe’s Strategy
Lycos Europe’s recent decision to employ Distributed Denial of Service (DDoS) attacks against spammers represents a significant shift in the approach to online security and a bold stance against malicious actors. This strategy signals a proactive, albeit controversial, response to the persistent problem of spam, which has plagued the internet for decades. The move highlights the escalating sophistication of online threats and the need for equally aggressive countermeasures.Lycos Europe’s strategy appears to center on disrupting the infrastructure supporting spam operations.
By targeting the servers and networks used to disseminate unwanted emails, Lycos Europe aims to cripple the spammers’ ability to operate effectively. This approach is distinct from traditional methods, which often involve filtering and blocking spam after it has already reached users’ inboxes. This proactive measure aims to preemptively neutralize the threat at its source. It remains to be seen whether this will prove an effective and sustainable solution.
Core Strategy
The core strategy behind Lycos Europe’s DDoS attacks is to impose a substantial operational cost on spammers. By flooding spammer infrastructure with traffic, Lycos Europe aims to overwhelm their systems, rendering them unable to send further spam. This approach seeks to deter future spamming activities by making them financially and operationally unviable. It’s a calculated risk, potentially creating a significant deterrent effect.
Historical Context
Similar methods have been employed before, albeit on a much smaller scale and often targeting specific individuals or organizations. Cyberattacks, particularly DDoS attacks, have been used in various contexts to disrupt online operations. However, targeting entire spam networks in a concerted manner as Lycos Europe is attempting is relatively unprecedented. This represents a significant escalation in the sophistication and scale of anti-spam tactics.
The long-term effectiveness of this approach is yet to be seen.
Potential Long-Term Implications
The potential long-term implications of this strategy are multifaceted and potentially impactful. It could set a precedent for other companies to take similar, more aggressive actions against malicious actors online. However, it also raises concerns about the potential for abuse and misuse of such powerful tools. Furthermore, it may spark a new arms race between spammers and those fighting them, leading to an escalating cycle of technological advancements and countermeasures.
The potential for unintended consequences, such as harming legitimate businesses or disrupting essential online services, cannot be ignored.
Comparison to Other Anti-Spam Strategies
| Method | Effectiveness | Potential Drawbacks |
|---|---|---|
| DDoS Attacks (Lycos Europe) | Potentially high, if effectively executed and targeted. May significantly disrupt spam operations. | High risk of collateral damage to legitimate businesses or services. Escalates the conflict and may lead to a cyber arms race. Requires significant resources and expertise. |
| Spam Filters | Moderately effective in blocking known spam. | Can be bypassed by sophisticated spammers. May result in legitimate emails being flagged as spam. Often requires constant updates and refinement. |
| User Education | Low impact on a large scale. Provides awareness, but doesn’t directly stop spam. | Requires sustained effort. May not be effective enough on its own. |
| Legislation and Regulation | Potentially high, if effectively enforced. Addresses the underlying incentives for spam. | Requires international cooperation and agreement. Enforcement can be difficult. May not be sufficient to address all spam. |
DDoS Attack Tactics
Lycos Europe’s proactive stance against spammers includes a robust strategy for countering Distributed Denial of Service (DDoS) attacks. Understanding the tactics employed by attackers is crucial for developing effective defense mechanisms. This involves recognizing the diverse methodologies used, their potential impacts, and the complexities inherent in launching and maintaining such campaigns.The core strategy revolves around identifying and mitigating the specific vulnerabilities exploited by spammers, enabling Lycos Europe to swiftly neutralize these threats.
This proactive approach ensures continuous operation and safeguards against potential disruptions.
Lycos Europe’s plan to combat spammers with DDoS attacks is certainly interesting. It’s a proactive approach, but it also begs the question of long-term effectiveness. Perhaps a more holistic approach, like the innovative advancements in home entertainment technology, as seen in Dell’s recent ventures into dell delves deeper into home entertainment , might offer a more sustainable solution.
Ultimately, though, Lycos Europe’s strategy seems like a necessary evil in the fight against online spam.
DDoS Attack Methods
Various methods are used in DDoS attacks, each with unique characteristics and vulnerabilities. Attackers often leverage a combination of techniques to overwhelm the target’s resources. Common methods include flooding the target with traffic from multiple sources, exploiting vulnerabilities in network protocols, and manipulating network configurations.
Examples of DDoS Attacks
Numerous DDoS attack types exist, each with varying levels of sophistication and impact. A SYN flood, for instance, overwhelms a server with connection requests, consuming its resources and preventing legitimate users from accessing services. A UDP flood bombards the target with User Datagram Protocol packets, also leading to server overload. These attacks can cripple online services, impacting users and potentially causing significant financial losses for the target.
For instance, a major e-commerce site experiencing a UDP flood attack would face the risk of losing sales and incurring reputational damage.
Technical Complexities of DDoS Campaigns
Launching and maintaining a successful DDoS campaign against spammers presents substantial technical challenges. Coordinating a vast network of compromised devices, often referred to as a botnet, requires significant resources and expertise. Maintaining control over this network, ensuring its functionality, and adapting to countermeasures deployed by the target are crucial for success. Furthermore, the ever-evolving nature of cybersecurity necessitates continuous adaptation and development of new attack vectors.
Lycos Europe’s plan to combat spammers with DDoS attacks is interesting, but it raises questions about broader strategies for online security. It’s a bit like the big music industry’s recent push for tighter controls on file-sharing in Canada, big music angles for lockdown on canada file sharing , which also involves a complex interplay of legal and technological solutions.
Ultimately, these approaches, while seemingly focused on different targets, both aim to regulate and control online activity, a trend we’ll likely see more of in the coming years. Lycos’s methods, however, are a more direct approach to spam than the more nuanced strategy of the Canadian music industry.
This constant evolution makes DDoS attacks a dynamic and complex problem.
DDoS Attack Vector Comparison
| Attack Vector | Description | Strengths | Weaknesses |
|---|---|---|---|
| SYN Flood | Overwhelms the target with TCP connection requests. | Relatively easy to launch, can quickly saturate server resources. | Can be mitigated with SYN cookies and stateful firewalls. |
| UDP Flood | Overloads the target with User Datagram Protocol packets. | Can be more difficult to filter than SYN floods, often requires high bandwidth. | Mitigation techniques can include rate limiting and filtering at the network layer. |
| ICMP Flood | Uses Internet Control Message Protocol packets to overwhelm the target. | Can be amplified by using reflection attacks. | Can be detected by analyzing network traffic patterns. |
| HTTP Flood | Sends a high volume of HTTP requests to the target server. | Can be stealthy and difficult to detect in some cases. | Requires a significant amount of bandwidth and computational resources. |
Legal and Ethical Considerations
Lycos Europe’s strategy to combat spam through DDoS attacks raises significant legal and ethical concerns. While the intent is to curb malicious activity, the potential for unintended consequences and harm to innocent parties must be carefully weighed against the benefits. This analysis will delve into the potential legal ramifications, ethical implications, and societal counterarguments associated with this approach.The use of DDoS attacks, even in the context of fighting spam, carries significant legal risks.
International laws often prohibit such actions, regardless of the motivation. Penalties for violations can range from substantial fines to criminal charges, depending on the severity of the impact and the jurisdiction. Cyberattacks can be considered criminal offenses in many countries, and the perpetrators may face serious legal consequences.
Potential Legal Ramifications
International laws and regulations often prohibit DDoS attacks, regardless of the motivation. These prohibitions are rooted in the principle that such actions can cause significant harm, including disruption of essential services and economic losses. The legal landscape surrounding cyberattacks is constantly evolving, and Lycos Europe needs to carefully assess the potential legal ramifications under various jurisdictions. For example, the Computer Misuse Act in the UK, or similar legislation in other countries, might classify DDoS attacks as criminal offenses, regardless of the intended target.
Ethical Implications of DDoS Attacks
The ethical implications of using DDoS attacks to combat spam are complex and controversial. While the aim is to disrupt malicious activity, the method itself is aggressive and potentially harmful to legitimate users. The principle of proportionality is a key ethical consideration, demanding a balanced approach between the harm inflicted and the benefit achieved. There is no universally accepted ethical framework to justify the use of DDoS attacks, even if they are aimed at a specific target.
Counterarguments to DDoS Attacks
From a societal perspective, there are compelling counterarguments against using DDoS attacks to combat spam. A more proportionate and less harmful approach is needed. The use of DDoS attacks as a solution risks escalating the conflict, creating a vicious cycle of retaliatory attacks, and potentially harming innocent parties. Instead of resorting to such drastic measures, alternative methods should be explored.
A more comprehensive approach involving collaboration between internet service providers, spam filters, and law enforcement agencies might be a more sustainable and ethically sound solution.
Collateral Damage from DDoS Attacks
DDoS attacks can cause collateral damage, affecting legitimate users who have no involvement in the spam. This damage can include disruptions to online services, financial losses, and reputational harm. For example, if a legitimate website is targeted in a DDoS attack intended to disrupt a spammer’s operations, it will also negatively impact the legitimate users trying to access that website.
Furthermore, the ripple effects of such attacks can spread to interconnected systems, causing broader disruptions. Lycos Europe needs to consider the potential impact on innocent users and the overall stability of the internet ecosystem.
Effectiveness and Impact
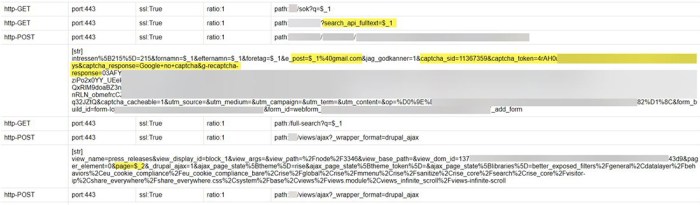
Lycos Europe’s strategy, relying on DDoS attacks to combat spam, presents a complex picture of potential effectiveness and unforeseen consequences. While a direct approach, it’s crucial to assess its predicted impact alongside other mitigation methods and the potential for unintended harm. This analysis will explore the predicted efficacy, compare it to alternative methods, and Artikel potential downsides and ways to measure the strategy’s impact.Predicting the exact reduction in spam through DDoS attacks is challenging, but some general principles can be applied.
A successful DDoS campaign can significantly disrupt spammers’ infrastructure, potentially reducing their ability to send mass emails. However, spammers are often resilient, adapting quickly to countermeasures.
Predicted Effectiveness of the Strategy
The effectiveness of Lycos Europe’s DDoS strategy hinges on several factors. First, the targeted spam infrastructure must be vulnerable and susceptible to disruption. Second, the DDoS attacks must be sufficiently powerful and sustained to significantly impact the spammers’ operations. Finally, the spammers’ ability to adapt and circumvent the attacks is a critical factor. Historical data on DDoS campaign effectiveness against spam networks varies widely depending on the specific network architecture and the strength of the attack.
Comparative Analysis of DDoS vs. Other Methods
DDoS attacks are a blunt instrument compared to more targeted spam-mitigation strategies. Techniques like blacklisting, email filtering, and collaboration between internet service providers (ISPs) are often more effective at preventing spam from reaching legitimate users. These methods are more precise and often lead to long-term reductions in spam volume. DDoS attacks, while potentially disruptive, don’t directly address the underlying causes of spam, such as the profitability of sending spam emails.
Potential Unintended Consequences
The primary unintended consequence of using DDoS attacks is the potential for collateral damage. Legitimate services or businesses that share infrastructure with spammers could also be affected, leading to reputational damage and financial losses. This is a critical ethical concern, especially if Lycos Europe’s actions disproportionately impact businesses not involved in spam activities. Additionally, there’s a risk of escalating the conflict with spammers, potentially leading to more sophisticated and resilient spam operations.
Quantifying the Impact of the DDoS Campaign
Quantifying the impact of a DDoS campaign on spam volume requires careful tracking and analysis. Lycos Europe should monitor key metrics, such as:
- Spam volume before and after the campaign: This provides a baseline and an indication of the campaign’s effectiveness. A significant reduction in spam volume would suggest positive impact.
- Spammer response: Observing how spammers react to the attacks, including changes in their tactics, provides insights into their resilience and adaptability.
- Impact on legitimate businesses: Monitoring the impact on legitimate businesses sharing infrastructure with spammers is crucial for evaluating the campaign’s unintended consequences.
Data collected from these metrics should be analyzed over a sustained period to draw meaningful conclusions about the campaign’s long-term effectiveness and impact. It’s important to note that measuring the impact will require significant resources and a sophisticated monitoring infrastructure.
Public Perception and Response
Lycos Europe’s strategy of employing DDoS attacks against spammers raises complex questions about public perception and response. This approach, while potentially effective in curbing spam, carries significant risks, especially regarding public opinion and the broader implications for internet service providers and users. The strategy’s success hinges not only on technical effectiveness but also on how the public perceives and reacts to it.The anticipated public reaction to Lycos Europe’s strategy is multifaceted and potentially volatile.
Positive responses may come from users frustrated with spam, recognizing Lycos Europe’s proactive approach. However, negative responses are equally probable, particularly from those who perceive the strategy as an overreach, a violation of ethical principles, or an infringement on freedom of expression online. This dynamic interplay of opinions will shape public discourse and the ultimate impact of Lycos Europe’s actions.
Anticipated Negative Publicity and Criticism
Potential negative publicity stems from the perception of Lycos Europe’s strategy as disproportionate and potentially harmful. Criticism from internet freedom advocates and privacy groups is likely, arguing that DDoS attacks, even when targeted, can have unintended consequences for legitimate users and infrastructure. Concerns about the potential for collateral damage and the escalation of online conflicts are likely to be raised.
Furthermore, regulatory scrutiny and legal challenges are possible, depending on the jurisdiction and applicable laws. Spam filters and other less aggressive strategies might be perceived as more ethical alternatives.
Potential Responses from Internet Service Providers and Users
Internet service providers (ISPs) might react in various ways. Some might support Lycos Europe’s approach, viewing it as a legitimate method for combating spam. Others might express concerns about the potential for widespread disruption and legal repercussions. Users might experience a range of responses, from support to apprehension. Those affected by spam might applaud Lycos Europe’s actions, while others might fear the potential for similar tactics to be used against them or their own providers.
The potential for retaliatory actions by other spammers cannot be excluded. Real-world examples of online conflicts, like the “war” between certain DDoS actors and websites, show how a cycle of aggression can emerge.
Lycos Europe’s strategy to combat spammers with DDoS attacks is a fascinating approach. It’s a direct, albeit potentially controversial, tactic. Interestingly, this mirrors the work of organizations like the Electronic Frontier Foundation, which is actively challenging abusive patents electronic frontier foundation targets abusive patents to protect digital freedom. Ultimately, both Lycos Europe’s actions and the EFF’s efforts aim to create a healthier, more secure online environment for everyone.
Public Discourse and Debate Scenarios
Public discourse surrounding Lycos Europe’s tactic is likely to focus on the ethical implications of using DDoS attacks. Discussions will likely involve the balancing of freedom of speech online with the need to combat malicious activity. The effectiveness and fairness of the strategy will be debated, with differing perspectives emerging from various stakeholder groups. The potential for escalation, where spammers retaliate with DDoS attacks against Lycos Europe or other providers, is a key concern and must be addressed in the long term.
Cases where similar strategies were used in the past, although often with less public attention, could provide useful context and lessons.
Alternative Solutions
Lycos Europe’s approach, while aiming to deter spammers through DDoS attacks, raises significant concerns about its ethical and legal implications. Alternative methods, focusing on proactive measures rather than reactive attacks, offer a more sustainable and potentially less damaging solution to the spam problem. These approaches encompass a broader spectrum of strategies, addressing the root causes of spam rather than simply fighting its effects.The efficacy of any anti-spam strategy hinges on its ability to prevent spam from reaching users in the first place.
Lycos Europe’s method is a blunt instrument, potentially harming legitimate users. Instead, a multi-pronged approach involving various preventative measures is crucial for long-term success. This section will explore alternative solutions, emphasizing user education, robust filtering mechanisms, and the importance of blacklisting to combat spam effectively.
Filtering Mechanisms
Spam filters are essential in identifying and blocking unwanted emails. Sophisticated filtering techniques analyze email headers, content, and sender reputations to detect and classify spam. Advanced filters leverage machine learning algorithms, allowing them to adapt and learn from new spam patterns. These algorithms can analyze vast datasets of emails, identify characteristics associated with spam, and progressively improve their accuracy over time.
Regular updates and fine-tuning of these filters are crucial for maintaining their effectiveness against evolving spam tactics.
Blacklisting
Blacklisting is a crucial aspect of spam prevention. By maintaining a database of known spam senders and domains, email providers can automatically block messages originating from these sources. This approach is proactive and helps prevent spam from even reaching users’ inboxes. Collaboration between different email providers and internet service providers (ISPs) is essential for maintaining an up-to-date and comprehensive blacklist.
“A robust blacklist system, updated regularly, is vital in reducing the volume of spam reaching inboxes.”
User Education, Lycos europe aims to thwart spammers with ddos attacks
User education plays a vital role in reducing the impact of spam. Educating users about recognizing and avoiding phishing scams, suspicious links, and attachments is essential. Clear and concise instructions on safe email practices can empower users to make informed decisions and protect themselves from potential harm. Regularly updated information campaigns, disseminated through various channels, can enhance user awareness and vigilance against spam.
Comparative Analysis of Approaches
| Feature | Lycos Europe’s Approach (DDoS Attacks) | Filtering | Blacklisting | User Education |
|---|---|---|---|---|
| Effectiveness | Potentially effective in short-term, but can cause collateral damage. | Highly effective in long-term, proactive prevention. | Highly effective in blocking known spam sources. | Reduces spam impact by empowering users to avoid it. |
| Ethical Considerations | Potentially harmful to innocent users and raises legal concerns. | Ethical and non-harmful. | Ethical and non-harmful, if used appropriately. | Ethical and empowering for users. |
| Cost | High operational costs associated with DDoS attacks. | Low operational costs, mainly for development and maintenance. | Low operational costs, mainly for database maintenance. | Low operational costs, primarily for content creation and distribution. |
| Sustainability | Short-term solution, not sustainable in the long run. | Sustainable, adaptable to evolving spam tactics. | Sustainable, as long as it’s kept updated. | Sustainable, as awareness can be continuously reinforced. |
Future Trends: Lycos Europe Aims To Thwart Spammers With Ddos Attacks

The fight against spam is an ongoing battle, constantly evolving with the technological landscape. Anti-spam strategies must adapt to new tactics and tools employed by spammers, and proactively address emerging threats. This necessitates a forward-thinking approach, anticipating future trends to effectively mitigate spam and maintain a secure online environment.The future of anti-spam strategies will be characterized by a sophisticated interplay of evolving technologies, more targeted methods, and the increasing importance of artificial intelligence and machine learning.
This will require continuous research and development, and a willingness to embrace new approaches to combat this ever-changing challenge.
Potential Evolution of Anti-Spam Strategies
Anti-spam strategies will likely shift from reactive measures to more proactive and predictive models. This includes analyzing vast datasets to identify patterns and anomalies indicative of spam activity before it even reaches users. The focus will be on anticipating and preventing future spam campaigns, rather than simply reacting to them.
Impact of Emerging Technologies on Spam Mitigation
Emerging technologies, like blockchain technology and decentralized identifiers (DIDs), can offer new avenues for verifying sender authenticity and combating spoofing. This can significantly impact the effectiveness of spam filters by enabling the verification of sender identity and preventing the creation of fake email addresses or domains. Blockchain’s inherent transparency could also help in tracing spam activity back to its origin, potentially deterring future campaigns.
Development of Sophisticated and Targeted Spam-Fighting Methods
Future spam-fighting methods will likely incorporate more sophisticated techniques. This includes utilizing advanced natural language processing (NLP) to identify subtle linguistic cues and patterns associated with spam, going beyond simple filtering. Machine learning algorithms can also be trained to identify new types of spam, like those exploiting emerging social media platforms or specific types of online communities.
This proactive approach would involve the creation of increasingly sophisticated and tailored detection mechanisms.
Impact of Artificial Intelligence and Machine Learning on Spam Detection and Prevention
Artificial intelligence (AI) and machine learning (ML) will play a pivotal role in improving spam detection and prevention. AI-powered systems can analyze massive datasets of emails, websites, and other online content to identify patterns and anomalies indicative of spam activity with far greater speed and accuracy than traditional methods. ML algorithms can be trained to identify new and evolving spam techniques, adapting to the ever-changing tactics of spammers.
For instance, Google’s spam filters rely heavily on ML to detect phishing attempts and malicious links.
End of Discussion
Lycos Europe’s decision to employ DDoS attacks against spammers is a bold, albeit controversial, move. While it may initially appear effective, the potential for unintended consequences, legal repercussions, and the broader societal implications must be carefully considered. Alternative, less aggressive methods exist, suggesting that a more nuanced approach to spam mitigation is crucial in the long run. The future of online security depends on a balanced approach that prioritizes both effectiveness and ethical considerations.