Network Security Evolving to Unified Management Approach
Network security evolving to unified management approach is reshaping how we safeguard our digital infrastructure. The fragmented, siloed systems of the past are giving way to centralized, integrated solutions. This evolution is driven by the increasing complexity of threats and the need for more efficient and effective responses. From cost savings and enhanced security postures to streamlined troubleshooting, unified management offers a compelling path forward.
This exploration delves into the multifaceted aspects of this transition, examining the benefits, challenges, and considerations involved. We’ll analyze current technologies, examine potential risks, and discuss strategies for successful implementation.
Introduction to Unified Network Management
The digital landscape is constantly evolving, and with it, the demands on network security are increasing exponentially. Traditional approaches to managing network security, often siloed and disparate, are struggling to keep pace with sophisticated threats. This necessitates a paradigm shift towards a more integrated, unified approach that provides a holistic view of the entire network and its security posture.Unified network management is not just about consolidating tools; it’s about fundamentally changing how we perceive and manage network security.
It aims to streamline processes, reduce operational overhead, and enhance the overall security posture by enabling faster threat detection and response. This unified approach aligns with the need for proactive security measures in today’s complex threat environment.
Evolving Security Needs and Traditional Approaches
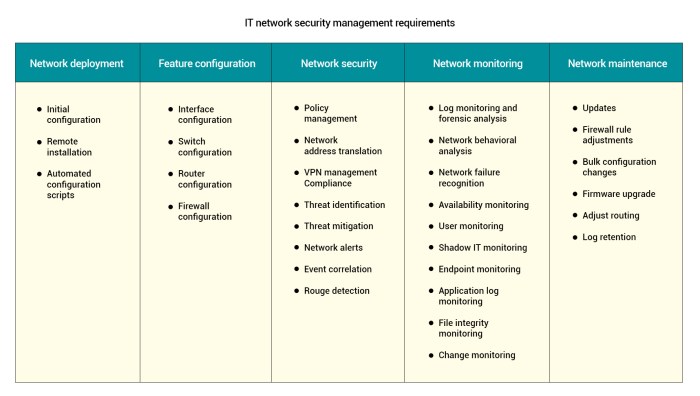
Network security management has evolved significantly since the early days of the internet. Initially, security was primarily focused on perimeter defenses. Firewalls and intrusion detection systems were the primary tools. However, as attacks became more sophisticated, these approaches became less effective. The rise of cloud computing, mobile devices, and the Internet of Things (IoT) further complicated the landscape, leading to a fragmented and often inefficient approach to security management.
Traditional network security management systems often operate in silos, leading to blind spots and difficulties in correlating events across different systems. This creates challenges in understanding the complete security picture and responding to threats effectively.
Benefits of a Unified Approach
Unified network management offers several crucial advantages over traditional approaches. By centralizing security management, organizations gain a comprehensive view of their entire network infrastructure. This holistic view allows for faster threat detection and response, reducing the time it takes to identify and mitigate security incidents. The integration of different security tools streamlines processes, reducing operational overhead and improving efficiency.
Network security is shifting towards a unified management approach, streamlining defenses. It’s like trying to predict the future, except instead of the stock market, you’re looking at the evolving cyber threats. You might even want to bet on the presidential election, given the potential impact on national security and international relations, and how that affects the need for enhanced cyber protections want to bet on the presidential election.
Ultimately, a unified approach is key to keeping pace with these changes and ensuring our digital infrastructure remains resilient.
Moreover, a unified approach facilitates better collaboration between security teams, fostering a more proactive and coordinated security posture. This is vital in the face of ever-evolving threats.
Comparison of Traditional and Unified Network Security Management
| Feature | Traditional Approach | Unified Approach | Advantages/Disadvantages |
|---|---|---|---|
| Security Tools | Separate tools for firewalls, intrusion detection/prevention systems (IDS/IPS), vulnerability scanners, SIEM, etc. | Integrated platform consolidating multiple security tools and functionalities. | Traditional: Potential for overlapping functionality, data silos, complex management; Unified: Streamlined management, consolidated data, improved visibility. |
| Data Correlation | Manual correlation of events from different systems, leading to delayed detection. | Automated correlation of events across all security tools, enabling faster incident response. | Traditional: Time-consuming and error-prone; Unified: Enhanced threat detection, faster incident response. |
| Management Complexity | Multiple consoles and interfaces for managing various security tools, leading to increased complexity. | Single pane of glass for managing all security aspects, simplifying operations. | Traditional: Increased operational overhead, difficulty in scaling; Unified: Simplified management, scalability, improved efficiency. |
| Threat Visibility | Limited visibility into the entire network, creating blind spots. | Comprehensive view of the entire network infrastructure, enhancing threat detection. | Traditional: Difficulty in identifying patterns and trends; Unified: Proactive threat detection, improved security posture. |
Benefits and Advantages of Unified Management
Unified network management offers a significant shift from traditional, siloed approaches. This centralization not only simplifies administration but also unlocks substantial cost savings, enhanced security, and improved operational efficiency. A unified platform allows for a more holistic view of the network, facilitating proactive threat detection and streamlined incident response.Centralizing management tools and data provides a comprehensive perspective, enabling faster issue resolution and improved security posture.
This holistic approach empowers organizations to proactively address vulnerabilities and react swiftly to incidents, ultimately strengthening their security stance.
Cost Savings
Unified network management systems reduce operational costs by streamlining tasks, automating processes, and decreasing the need for specialized personnel. The elimination of redundant tools and processes results in direct savings. Organizations can often reduce the number of IT staff required to manage disparate systems. This is especially valuable in smaller to medium-sized businesses where the cost of maintaining multiple specialized teams can be substantial.
Enhanced Security Posture
Centralized management dramatically improves security posture. By consolidating security tools and data, a unified platform enables quicker identification and response to threats. The centralized view allows for comprehensive threat analysis, correlation of events across various systems, and quicker mitigation strategies. This reduces the risk of undetected breaches and accelerates the remediation process, ultimately lowering the potential impact of security incidents.
Network security is definitely shifting towards a unified management approach, which is crucial for streamlining defenses. This is especially important given that the US continues to be a major source of spam, as highlighted in this recent report on us still tops spammer list. A unified approach to security management will hopefully help address the complexities of handling spam and other threats, leading to more robust and efficient protection for everyone.
Improved Operational Efficiency
Unified management tools often include automation capabilities. Automating tasks like patching, configuration changes, and routine maintenance reduces manual effort and human error, leading to increased operational efficiency. The ability to monitor and manage all network elements from a single pane of glass simplifies troubleshooting and reduces the time to identify and resolve issues. This, in turn, leads to more predictable network performance and reduced downtime.
Improved Incident Response Capabilities
A unified management system empowers quicker and more effective incident response. Real-time visibility into all network segments allows for faster identification of anomalies and potential threats. This rapid identification leads to quicker containment and remediation strategies.
- Automated threat detection and response: Unified platforms can be configured to automatically detect and respond to known threats, minimizing the time from detection to resolution. This automation reduces the reliance on manual processes and human intervention.
- Improved incident correlation: The ability to correlate events across different network segments allows for a more complete picture of incidents, enabling better understanding of the root cause and enabling faster remediation.
- Simplified communication and collaboration: Unified platforms often provide centralized communication tools, allowing security teams and other stakeholders to collaborate effectively during an incident, ultimately improving response times.
- Centralized reporting and analysis: Unified management systems often generate detailed reports on incidents, providing valuable insights into patterns and trends to improve future incident response strategies.
Streamlined Troubleshooting and Remediation
Unified management platforms streamline troubleshooting and remediation efforts by providing a single source of truth for all network information. This centralized view allows for faster identification of problem areas and quicker resolution of issues. For example, if a network outage occurs, the unified platform can pinpoint the affected device or segment immediately, allowing for targeted remediation efforts, potentially saving valuable time and resources.
Challenges and Considerations: Network Security Evolving To Unified Management Approach
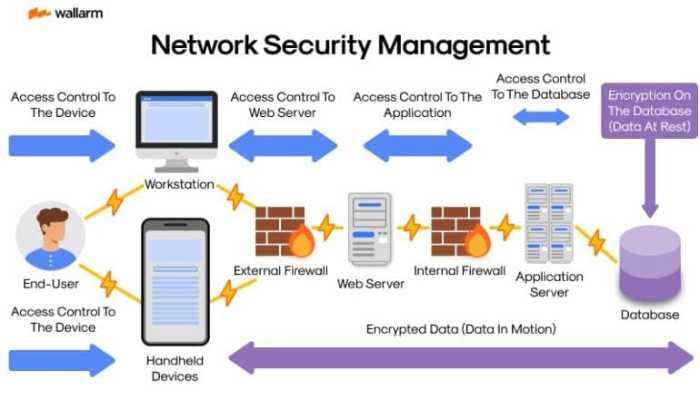
The journey towards unified network management, while promising significant benefits, is not without its hurdles. Integrating disparate security tools and platforms presents a complex challenge, requiring careful planning and execution. Understanding these potential pitfalls is crucial for successful implementation and maximizing the return on investment.Integrating diverse security tools and platforms often leads to compatibility and interoperability problems. Different vendors use varying protocols, data formats, and APIs, making it difficult to seamlessly exchange information.
Network security is definitely moving towards a unified management approach, which is great for streamlining operations. Think about how things like pocketskype offers free VoIP for pocketPCs pocketskype offers free voip for pocketpcs — a tiny bit of that early digital revolution— foreshadowed a more interconnected world. Ultimately, this evolution in network security means fewer silos and more efficient protection against threats, something we all need more of in today’s complex digital landscape.
This lack of standardization can create data silos and hinder the ability to gain a holistic view of the security posture.
Integrating Diverse Security Tools and Platforms
The multitude of security tools and platforms used in a typical organization often leads to fragmented security information. Each tool might collect and store data in its own format, making it challenging to correlate events across different systems. This fragmented approach can result in blind spots and missed threats. Addressing this requires a standardized approach to data collection, storage, and analysis.
The key to success lies in careful planning and selecting tools that are compatible and interoperable.
Compatibility and Interoperability Issues
Compatibility and interoperability issues are common when integrating various security tools. Differences in data formats, protocols, and APIs can hinder the seamless exchange of information between platforms. This lack of interoperability can lead to data silos, where critical security data remains isolated and inaccessible to a unified view. Vendors should prioritize standardization and open APIs to facilitate easier integration.
Examples include differences in log formats, reporting structures, and alerting mechanisms, which can complicate correlation and analysis.
Importance of a Strong SIEM System
A robust security information and event management (SIEM) system is essential in a unified network management approach. A SIEM acts as a central hub for collecting, correlating, and analyzing security events from various sources. It provides a consolidated view of the security posture, enabling security analysts to detect and respond to threats more effectively. A strong SIEM system is crucial for identifying patterns, anomalies, and potential security breaches that might be missed with disparate systems.
Without a central repository, organizations risk losing valuable insights into their security posture.
Potential Data Silos in a Non-Unified Structure
A non-unified network management structure can create numerous data silos. Each security tool might collect and store data in its own format and database. This isolation prevents a holistic view of security events, hindering threat detection and response. For example, firewalls might log network intrusions, while intrusion detection systems might record suspicious activities. Without a central platform to correlate these events, a complete picture of the threat landscape remains elusive.
A typical example is a company using a firewall from vendor A, an intrusion detection system from vendor B, and an antivirus solution from vendor C. Each vendor likely uses its own format and schema, creating a data silo.
Necessity for Skilled Personnel
Unified network management requires a skilled workforce capable of managing and maintaining the integrated system. Personnel need expertise in configuring, integrating, and maintaining the various security tools and platforms. They must also be adept at analyzing security events, identifying threats, and responding to incidents. The complexity of a unified system demands professionals with deep understanding of different security tools and platforms, as well as expertise in security operations and incident response.
Failure to adequately staff with trained personnel can lead to the system becoming a black box, negating the benefits of unification.
Technology and Tools
Unified network management hinges on the convergence of various technologies. This evolution allows organizations to consolidate security tools and processes, improving visibility and streamlining threat response. Modern security landscapes are complex, requiring sophisticated tools to effectively manage diverse network elements. A unified approach simplifies this complexity, enabling quicker detection and response to security incidents.
Current Technologies Enabling Unified Network Management
Several technologies underpin unified network management. Centralized logging and analytics platforms aggregate data from disparate sources, providing a comprehensive view of network activity. Automation tools, including scripting languages and orchestration platforms, automate tasks, reducing manual intervention and human error. API integrations between different security tools are crucial, enabling seamless data exchange and interoperability. Sophisticated threat intelligence feeds provide real-time insights into emerging threats, aiding proactive security posture management.
Common Unified Security Management Platforms
Unified security management platforms are consolidating various security functions into a single interface. These platforms offer a consolidated view of security events, simplifying incident response and threat hunting. They often integrate with existing security infrastructure, minimizing disruption during implementation. Comprehensive reporting and analytics capabilities empower security teams to identify trends, prioritize risks, and optimize security investments.
Comparison of Unified Security Management Platforms
| Platform | Key Features | Pros | Cons |
|---|---|---|---|
| Splunk Security | Threat detection, incident response, compliance monitoring, SIEM | Comprehensive threat detection, highly scalable, extensive reporting capabilities, wide range of integrations. | Steep learning curve, licensing costs can be high, requires significant configuration effort. |
| Palo Alto Networks Prisma Access | Secure access service edge (SASE), cloud security, network security, Zero Trust | Comprehensive cloud security approach, integrated security policies, simplified network management, reduced attack surface. | Requires significant infrastructure changes, may not be suitable for smaller organizations, potential integration challenges with existing infrastructure. |
| Forcepoint | Endpoint security, network security, cloud security, identity and access management (IAM) | Strong security posture across multiple environments, extensive threat intelligence, improved incident response capabilities, comprehensive policy management. | Implementation can be complex, integration with existing systems may require extensive configuration, pricing can be a barrier for smaller organizations. |
| CrowdStrike Falcon | Endpoint detection and response (EDR), threat intelligence, security information and event management (SIEM) | Highly effective endpoint protection, proactive threat hunting, strong threat intelligence capabilities, integrated threat response. | Can be expensive, may require specialized expertise for deployment and management, primarily focused on endpoint security. |
Emerging Technologies Shaping the Future of Unified Network Security
Artificial intelligence (AI) and machine learning (ML) are transforming security operations. AI-powered threat detection systems can identify subtle anomalies and predict potential threats, improving the speed and accuracy of incident response. The increasing adoption of cloud-native architectures necessitates the development of cloud-specific security management tools. Zero Trust security models are gaining traction, requiring platforms to adapt to dynamic and granular access policies.
Important Considerations for Selecting Unified Security Management Tools
Selecting the right unified security management tools requires careful consideration of several factors. Integration with existing infrastructure is crucial to minimize disruption during deployment. Scalability is essential to accommodate future growth and changing security needs. Security posture management capabilities are critical for continuous improvement and compliance. Support and training are essential for effective implementation and long-term success.
The platform’s ability to adapt to emerging threats and technologies is also a key factor.
Security Implications of Unified Management
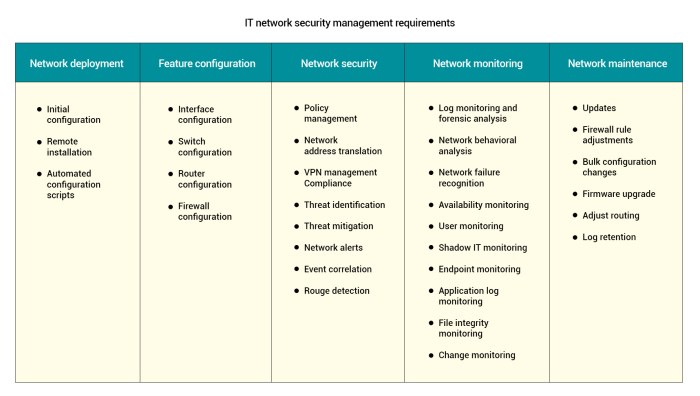
Unified network management platforms offer significant efficiency gains, but they also introduce new security considerations. Centralizing control and data inevitably alters the security landscape, demanding a proactive approach to address potential vulnerabilities. A robust security strategy is paramount to ensuring the safety and integrity of the unified platform and the data it manages.
Access Control and User Permissions
Effective access control is critical within a unified management platform. Granular user permissions, defining what actions each user can perform, are essential to prevent unauthorized access and modification of critical system settings. A robust role-based access control (RBAC) model is highly recommended, assigning specific roles with predefined permissions. This prevents accidental or malicious modification of sensitive configurations. Failure to implement or maintain appropriate access controls can lead to data breaches and system compromises.
Risks of Centralized Data Storage
Centralized data storage, a hallmark of unified management, presents unique risks. A single point of failure, if compromised, can expose vast amounts of sensitive information, including network configurations, user credentials, and security policies. Thorough data encryption and regular backups are crucial to mitigate this risk. A comprehensive security audit, including penetration testing, can help identify vulnerabilities in the centralized storage system.
A distributed data storage approach, while more complex, offers a degree of redundancy and resilience against these threats.
Security Monitoring and Logging
Robust security monitoring and logging are vital in a unified environment. Real-time monitoring of system activities, combined with detailed logging of events, facilitates early detection of suspicious activity and potential threats. Comprehensive log analysis tools, capable of correlating events and identifying patterns, are essential for threat detection and response. Continuous monitoring of security logs helps in identifying anomalies and reacting to threats promptly.
Impact on Compliance and Regulatory Requirements
Unified management platforms significantly impact compliance and regulatory requirements. Organizations must ensure that the platform aligns with industry-specific regulations (e.g., HIPAA, PCI DSS) and data privacy laws. Thorough documentation, auditing, and reporting procedures are crucial to demonstrate compliance and meet regulatory obligations. Implementing security controls that align with compliance requirements is crucial to prevent penalties and maintain operational continuity.
Security Threats and Mitigation Strategies
Unified management systems are susceptible to various security threats. A proactive approach to mitigation is essential.
| Threat Type | Description | Mitigation Strategy | Impact |
|---|---|---|---|
| Unauthorized Access | Unauthorized users gaining access to sensitive data or system controls. | Strong access controls, multi-factor authentication, regular security audits. | Data breaches, system compromises, financial losses. |
| Malware Infections | Malicious software infiltrating the unified management platform. | Robust anti-malware solutions, regular software updates, secure software patching. | Data loss, system downtime, reputational damage. |
| Denial-of-Service Attacks | Overwhelming the system with traffic, disrupting its functionality. | Network intrusion detection and prevention systems (IDS/IPS), traffic filtering, load balancing. | Service disruptions, loss of revenue, operational downtime. |
| Insider Threats | Malicious or negligent actions by authorized personnel. | Strict access controls, background checks, regular security awareness training. | Data breaches, system compromises, regulatory penalties. |
Implementation Strategies
Unified network security management is no longer a futuristic concept; it’s a necessity for modern organizations. Implementing this approach requires a phased, well-planned strategy to ensure a smooth transition and avoid disruption to existing operations. Successful implementation hinges on careful consideration of all aspects, from initial assessment to ongoing maintenance.A key element of a successful implementation is understanding that it’s not a one-time project but an ongoing process.
It requires a dedicated team, clear communication channels, and continuous monitoring to address evolving threats and maintain optimal security posture. Change management is critical to ensure buy-in and adoption from all stakeholders.
Phased Approach to Implementation
Implementing a unified security management system requires a phased approach to ensure a smooth transition. This allows for a gradual integration of tools and processes, minimizing disruption to ongoing operations.
- Assessment and Planning Phase: This initial phase involves a thorough evaluation of the existing network infrastructure, security tools, and processes. Identify the specific gaps in the current security posture and potential benefits of a unified platform. Define clear goals, objectives, and expected outcomes for the implementation. This is crucial for determining the scope and scale of the project and ensuring alignment with the organization’s overall strategic objectives.
- Pilot and Validation Phase: Select a specific segment of the network (e.g., a department or a particular application) for a pilot implementation. This allows for testing the unified platform’s functionality, performance, and compatibility with existing systems in a controlled environment. Detailed metrics and reporting mechanisms are established to measure the effectiveness of the platform in the pilot group. Monitor and evaluate the results, identify any necessary adjustments to the configuration or processes, and refine the implementation plan based on the pilot findings.
Documentation of the pilot phase is essential to inform future steps.
- Full Deployment and Optimization Phase: Once the pilot project has successfully validated the unified platform, it’s time for a complete rollout. Thorough training programs are developed for all stakeholders, including administrators and end-users. This ensures consistent understanding and operation of the new system. Monitor system performance closely, identifying potential issues and implementing corrective actions as needed. The focus shifts to optimizing the platform for maximum efficiency and effectiveness in addressing security threats.
- Continuous Monitoring and Improvement Phase: The implementation doesn’t end with the deployment. Continuous monitoring of system performance, threat detection capabilities, and user adoption is crucial. Regular security audits are conducted to identify vulnerabilities and ensure the platform remains effective. The system is adaptable to emerging threats and evolving security landscape. The process includes regular updates and enhancements to the platform based on monitoring and analysis.
Step-by-Step Transition Guide
A phased transition from a traditional to a unified security approach is essential. A step-by-step guide ensures a controlled and manageable process.
- Inventory and Assessment: Document all existing security tools, their functionalities, and their interdependencies. Identify the specific vulnerabilities in the current system and the potential benefits of unification.
- Selection of Unified Platform: Evaluate potential unified platforms based on specific needs, budget constraints, and scalability requirements. This includes a thorough evaluation of vendor support, service level agreements, and future roadmap.
- Data Migration Planning: Develop a comprehensive plan for migrating data from legacy systems to the unified platform. This involves careful consideration of data integrity and security protocols during the migration process. A phased migration approach is often preferred for large-scale data transfers.
- Integration and Testing: Integrate the unified platform with existing security tools. Comprehensive testing should be conducted to identify and resolve potential issues before full deployment.
- Training and Support: Provide comprehensive training to staff on the new platform and processes. Establish a robust support system for addressing any issues or questions that arise during the transition period.
- Monitoring and Evaluation: Monitor the system’s performance and effectiveness after deployment. Conduct regular audits to ensure the platform is meeting the established security goals and objectives. Gather feedback from users and make necessary adjustments based on their experiences.
Checklist for Implementing a Unified System
A well-defined checklist ensures that no critical aspect of the implementation is overlooked.
| Phase | Tasks |
|---|---|
| Assessment | Inventory of existing tools, identification of gaps, definition of objectives, budget allocation |
| Pilot | Selection of pilot group, setup of test environment, implementation of the platform, monitoring of results, adjustments to the plan |
| Deployment | Full-scale implementation, user training, system integration, testing, data migration |
| Maintenance | Ongoing monitoring, security audits, platform updates, user support, feedback mechanisms |
Future Trends and Predictions
Unified network security management is poised for significant evolution, driven by the relentless pace of technological advancements and the ever-increasing sophistication of cyber threats. This dynamic landscape demands proactive strategies for managing and adapting to the complexities of modern security challenges. Anticipated advancements in unified management will fundamentally alter how organizations approach network protection, demanding continuous learning and adaptation from security professionals.The future of unified network security management will be profoundly shaped by the integration of cutting-edge technologies, especially Artificial Intelligence (AI) and Machine Learning (ML).
These technologies will play a critical role in enhancing threat detection, response, and prevention capabilities, making security operations more efficient and effective. The integration of these technologies into unified management systems will allow for proactive identification and mitigation of potential threats before they can cause significant damage.
Anticipated Advancements in Unified Network Security Management
Unified management systems are moving towards greater automation and self-healing capabilities. This trend will reduce the workload on security teams and allow them to focus on more strategic initiatives. Integration with existing security tools and platforms is another key development, allowing for seamless data flow and improved threat intelligence gathering.
Impact of AI and Machine Learning on Unified Management, Network security evolving to unified management approach
AI and ML are poised to revolutionize unified network management. AI-powered threat detection systems will be able to analyze vast amounts of network data to identify patterns and anomalies indicative of malicious activity. ML algorithms can continuously learn and adapt to new threats, improving the accuracy and efficiency of threat detection over time. For example, a system might identify a new malware variant by recognizing its behavior patterns in relation to known malicious activities, and take action to block or isolate it.
Future Role of Automation in Network Security
Automation will play an increasingly crucial role in unified network security management. Automated threat response systems will allow for faster incident response times and reduce the impact of security breaches. Automated patching and configuration management will also minimize vulnerabilities. These automated processes will reduce the manual workload on security teams, freeing up time and resources for other tasks.
Examples of this include automated responses to known malware patterns or the automatic implementation of security updates across a network.
Evolving Threat Landscape and Unified Management
The evolving threat landscape is a significant driver for the need for unified network security management. The increasing sophistication of attacks, the rise of ransomware and other advanced persistent threats, and the growing attack surface created by the proliferation of connected devices necessitate a unified approach. Unified management systems provide a centralized platform for managing these complex threats and minimizing their impact.
This is crucial as the attack surface continues to expand, and new threat vectors emerge, necessitating the need for centralized and integrated tools. The proliferation of IoT devices and the increasing reliance on cloud services present entirely new vectors for attack, demanding a more comprehensive and unified approach to security.
Importance of Continuous Learning and Adaptation
The security landscape is constantly evolving, requiring organizations to continuously learn and adapt. Unified management systems must be designed with flexibility and scalability in mind to accommodate new threats and technologies. Regular updates, continuous monitoring, and the incorporation of threat intelligence are crucial for staying ahead of evolving threats. Organizations need to build a culture of continuous learning and adaptation among their security teams, fostering the ability to quickly respond to new and emerging threats.
Regular training and updates are crucial for this process, ensuring the security teams are equipped with the knowledge and skills needed to effectively manage the changing landscape.
Final Review
In conclusion, the shift towards unified network security management presents a significant opportunity to enhance security, streamline operations, and adapt to the ever-evolving threat landscape. While challenges exist, the potential rewards—from cost savings to improved incident response—are substantial. Ultimately, embracing this unified approach is crucial for maintaining a robust and resilient digital ecosystem.