Hackers Break In to Sony PSP A Deep Dive
Hackers break in to sony psp, exploiting vulnerabilities in the popular Sony PlayStation Portable (PSP). This exploration delves into the history of the PSP, examining its technical weaknesses and the motivations behind these intrusions. We’ll explore the various methods hackers employed, from software exploits to hardware modifications, and analyze the consequences for Sony, users, and the broader digital landscape.
A detailed look at Sony’s security measures and the evolution of hacking techniques against the PSP will be presented.
The PSP, a handheld gaming powerhouse, was initially lauded for its portability and features. However, its technical specifications, particularly regarding its operating system, created avenues for exploitation. This article explores how hackers leveraged these vulnerabilities to gain unauthorized access, demonstrating the ever-present threat in the digital age. The subsequent impact on Sony and its users will be discussed in detail, along with the ethical and legal considerations surrounding these actions.
Introduction to Sony PSP Hacking
The Sony PlayStation Portable (PSP), released in 2004, revolutionized handheld gaming. Its compact size and powerful processing capabilities, coupled with a relatively open architecture, attracted both enthusiasts and malicious actors. This early foray into portable gaming laid the groundwork for innovative hacking communities.The PSP’s design incorporated a custom-built processor, specific memory configurations, and proprietary operating system. These characteristics, while enhancing functionality, also presented vulnerabilities that hackers could exploit.
The PSP’s initial success was quickly followed by the rise of a hacking community, driving the evolution of both the hardware and software landscape.
Technical Specifications and Vulnerabilities
The PSP, while groundbreaking for its time, possessed certain technical weaknesses that proved attractive to hackers. The system’s architecture, combining a MIPS processor with specific memory management, was found to have gaps in security. The custom operating system, while offering a rich gaming experience, also presented avenues for exploitation.
Motivations and Goals of PSP Hackers
Hackers targeted the PSP for various reasons. Some sought to demonstrate technical prowess, showcasing their abilities to bypass security measures. Others aimed to create custom functionalities, such as running alternative operating systems or accessing proprietary software. The desire to circumvent restrictions, allowing for greater freedom in gameplay and content access, was also a strong motivator.
Types of PSP Exploits
PSP hacking involved a variety of exploits. These included:
- Firmware Modification: Hackers modified the PSP’s firmware to enable functionalities beyond the manufacturer’s intent.
- Homebrew Applications: Custom applications, developed by users, were installed on the PSP to perform various tasks.
- Content Piracy: Exploits were used to circumvent copyright restrictions, enabling access to copyrighted games and media without paying.
Evolution of Hacking Techniques
The PSP hacking scene saw a continuous evolution in techniques. Initial methods relied on simple vulnerabilities, but as the security community reacted, hackers adapted. Sophisticated exploits and techniques emerged, reflecting the ongoing battle between security and innovation.
Comparison of PSP Models and Susceptibility to Hacking
| Model | Processor | Memory | Operating System | Vulnerabilities |
|---|---|---|---|---|
| PSP-1000 | MIPS R4000 | Various RAM configurations | PSP OS | Early exploits targeted specific memory management issues and OS loopholes. |
| PSP-2000 | MIPS R4000 | Various RAM configurations | PSP OS | Exploits often involved custom firmware and homebrew application installations. Further refinements in memory management and OS loopholes were exploited. |
Methods of Attack: Hackers Break In To Sony Psp

The Sony PlayStation Portable (PSP) presented a unique landscape for hackers, offering a blend of vulnerabilities that ranged from simple social engineering to sophisticated hardware modifications. Understanding these methods is crucial for appreciating the evolution of hacking techniques and the security challenges they posed. The accessibility of the PSP’s software and the relative ease of modifying its hardware made it a target for both novice and experienced hackers.The PSP’s security was frequently compromised by leveraging a combination of attack vectors, targeting vulnerabilities in both the software and the hardware.
Exploiting these vulnerabilities allowed attackers to gain unauthorized access, control, and ultimately, manipulate the device’s functionality.
Remember those early days of the Sony PSP, when hackers were constantly finding new ways to break in? It was a fascinating time, and while the tech world moved on, innovations like the panasonic debuts blu ray dvd recorder were also emerging. These new recording devices offered a different kind of digital revolution, but the PSP hacking scene remained a compelling example of how technology could be both revolutionary and vulnerable.
Common Hacking Methods
Various techniques were employed to breach the PSP’s security. These included social engineering, exploiting software flaws, and manipulating the hardware itself. Social engineering, a common attack method, involved tricking users into revealing sensitive information or performing actions that compromised their systems. Software exploits, often found in vulnerable applications, provided a pathway for hackers to gain control of the PSP.
Hardware modifications, in turn, allowed physical manipulation of the device, circumventing many security measures.
Social Engineering Attacks
Social engineering attacks targeted users’ trust and naivety. This involved manipulating users into divulging passwords, downloading malicious software, or granting unauthorized access. Examples included phishing emails, fake websites, and deceptive online interactions that lured users into compromising their accounts. The success of these attacks often relied on psychological manipulation and exploiting the lack of awareness about security threats.
Exploiting Software Flaws
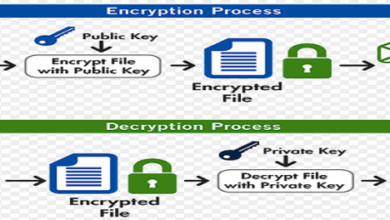
Software vulnerabilities played a significant role in PSP attacks. Hackers identified and exploited weaknesses in the PSP’s operating system or applications, enabling unauthorized access and control. These exploits, often found in firmware or application code, allowed malicious code to execute without the user’s knowledge or consent.
Hardware Modifications
Hardware modifications, though more technically demanding, allowed for bypassing security measures and gaining unauthorized access. These methods typically involved physical access to the PSP and involved altering its firmware or manipulating its components. For example, custom firmware installations or replacing components could grant attackers complete control over the system.
Hacking Tools
Numerous tools were employed to exploit vulnerabilities and execute attacks on the PSP. These ranged from simple scripts to more sophisticated exploits and debugging tools. The choice of tool often depended on the specific vulnerability being targeted and the desired outcome. Some popular tools included custom exploits and homebrew applications. The effectiveness of a specific tool varied based on the targeted vulnerability and the sophistication of the defense mechanisms in place.
Remember those days when hackers were breaking into Sony PSPs? It’s fascinating how the world of software security has evolved since then. Microsoft is taking a proactive approach, and their recent preview of software factories, like microsoft previews vision of software factories , shows a real commitment to building more secure systems. Perhaps this forward-thinking approach could have prevented some of the early exploits seen with the PSP.
Still, those old hacking stories remain a reminder of how crucial constant vigilance is in software development.
Rootkits and Malware
Rootkits and malware were frequently used to conceal the presence of malicious activity on the PSP. Rootkits masked the existence of malicious software, while malware often carried out malicious actions. Their presence often went unnoticed by users, allowing hackers to maintain persistent control over the device. The installation of rootkits or malware frequently compromised the security of the PSP’s system, enabling further attacks and unauthorized access.
Steps in a Typical PSP Hacking Attack
| Step | Description | Tools |
|---|---|---|
| 1 | Identifying a vulnerability in the PSP’s software or firmware. | Vulnerability scanners, debuggers |
| 2 | Developing an exploit to leverage the identified vulnerability. | Exploit frameworks, programming languages |
| 3 | Creating malicious code to execute the exploit and gain control. | Programming languages, assembly code |
| 4 | Deploying the exploit to infect the target PSP. | Various methods, including social engineering |
| 5 | Concealing the malicious activity through rootkits. | Rootkit tools, obfuscation techniques |
Impact and Consequences
The Sony PSP, a groundbreaking handheld gaming device, faced numerous security challenges following its release. Hacking incidents, ranging from simple cosmetic modifications to sophisticated exploits, had significant consequences for Sony, its users, and the broader security landscape. Understanding these impacts is crucial to appreciating the complexities of security breaches and the long-term implications for similar devices.The ramifications of PSP hacking extended far beyond the technical aspects, impacting financial stability, user trust, and the very concept of device security.
The following sections detail these diverse consequences.
Financial Consequences for Sony
Sony faced substantial financial repercussions due to PSP hacking incidents. Loss of revenue from diminished sales, and damage to the brand’s reputation, resulted in a significant financial setback. Reputational damage, including the loss of consumer trust, could lead to a decreased demand for future products, directly affecting Sony’s bottom line. These negative impacts were amplified by the time and resources Sony had to invest in fixing vulnerabilities and implementing security measures.
Reputational Damage for Sony
PSP hacking incidents eroded Sony’s reputation. Negative publicity surrounding security flaws and subsequent exploits tarnished the company’s image. This loss of trust could deter potential customers, impacting future sales and the overall market perception of Sony products. The impact was compounded by the difficulty in rebuilding consumer trust once it was compromised.
Impact on PSP User Experience
Hacking activities often resulted in unauthorized access to the PSP, leading to modifications that affected the user experience. These modifications could range from simple cosmetic changes to more disruptive alterations, such as enabling access to unauthorized content or features. Unauthorized modifications, while seemingly minor, could detract from the overall user experience and potentially lead to dissatisfaction. Examples included issues with gameplay, performance, and functionality.
Ethical Considerations of PSP Hacking
The ethical implications of hacking the PSP are complex. While some modifications might seem harmless, others could violate terms of service, potentially infringing on copyright or intellectual property rights. Unauthorized access and modifications can harm the interests of the software developers, publishers, and hardware manufacturers. Moreover, the act of hacking itself can raise questions about personal responsibility and the potential for misuse.
Legal Ramifications for Hackers
Individuals involved in PSP hacking faced potential legal ramifications. These could range from civil lawsuits for damages to criminal charges, depending on the nature and extent of the hacking activities. Illegal modifications, distribution of modified software, and other illegal activities related to hacking could result in severe legal consequences, including hefty fines and imprisonment. This varied depending on the local jurisdiction and the specific nature of the hacking actions.
Impact on Security of Similar Handheld Devices
PSP hacking incidents served as a valuable lesson in the importance of robust security measures for handheld devices. These incidents highlighted the vulnerabilities inherent in similar handheld devices, particularly those with easily accessible software or hardware. The vulnerabilities in the PSP prompted increased security measures in the design and development of subsequent handheld devices. The lessons learned from PSP hacking served as a cautionary tale for the industry, leading to better security practices in the design and development of future handheld gaming devices.
Comparative Impact of Different PSP Hacks
| Hack Type | Financial Impact | User Impact |
|---|---|---|
| Cosmetic Modifications | Minimal | Aesthetic changes, potentially no impact on functionality |
| Unauthorized Content Access | Potential loss of revenue from copyright infringement | Access to unauthorized content, violation of terms of service |
| System Exploits | Significant loss of revenue due to security breaches and legal issues | Potential for complete system compromise, loss of data, and functionality |
This table demonstrates the varying degrees of impact, from minor aesthetic changes to significant system breaches, on both Sony’s finances and the user experience.
Security Measures and Countermeasures
Sony, in response to the PSP hacking incidents, implemented a series of security measures. These measures aimed to fortify the system against future attacks and minimize the impact of vulnerabilities. While some measures proved effective, others were later circumvented, highlighting the ongoing arms race between hackers and security professionals. Understanding these measures, their effectiveness, and the subsequent responses is crucial to comprehending the evolution of digital security.
Sony’s Security Measures
Sony employed various techniques to secure the PSP. These included hardware-level protections, firmware updates, and the implementation of cryptographic algorithms. The goal was to create a layered defense system, making it more challenging for hackers to exploit vulnerabilities.
Remember those days when hackers were breaking into Sony PSPs? It’s fascinating how technology evolves. With the FCC mulling airborne mobile phone use, fcc mulls airborne mobile phone use , it makes you wonder what future hacking targets might look like. Maybe the next generation of vulnerabilities will be in the skies. Hopefully, the security measures for the next generation of portable devices will be stronger than those of the Sony PSP.
Effectiveness of Security Measures
The effectiveness of Sony’s security measures was not uniform. Early measures, while initially effective in preventing certain types of attacks, were eventually bypassed by determined hackers. This highlights the dynamic nature of security and the constant need for adaptation and improvement. The success of a security system is measured not only by its initial effectiveness but also by its ability to adapt to evolving threats.
Software Updates and Patches
Sony released numerous software updates and patches in response to discovered vulnerabilities. These updates often addressed specific weaknesses in the PSP’s firmware, operating system, or applications. Examples include fixes for buffer overflows, vulnerabilities in the file system, and issues related to network communication. These updates, while crucial, could not always anticipate every possible attack vector.
Role of Security Researchers
Independent security researchers played a vital role in identifying and reporting vulnerabilities in the PSP. Their work often involved analyzing the system’s code, searching for weaknesses, and reporting their findings to Sony. This collaborative effort was instrumental in mitigating potential security risks. A vibrant community of security researchers, often driven by ethical hacking principles, is critical in ensuring the security of any system.
Security Protocols Used
Various security protocols were employed to protect the PSP systems. The effectiveness of these protocols often depended on the specific implementation and the sophistication of the attack attempts.
| Protocol | Description | Effectiveness |
|---|---|---|
| Digital Signature Verification | Ensuring the authenticity and integrity of downloaded content. | Moderately effective, though bypassed in some cases. |
| Access Control Lists (ACLs) | Restricting access to specific files and functions. | Partially effective, as ACLs can be circumvented. |
| Encryption Techniques | Protecting data in transit and at rest. | Varied effectiveness depending on the specific algorithm used. |
| Firewall Mechanisms | Controlling network traffic and preventing unauthorized access. | Generally effective in preventing basic attacks. |
PSP Hacking in the Digital Landscape

The Sony PlayStation Portable (PSP) hacking incidents, while seemingly focused on a specific device, had a profound impact on the broader digital security landscape. These exploits exposed vulnerabilities not only in the PSP’s architecture but also in the broader design philosophy of handheld devices, highlighting the crucial need for robust security measures across all digital platforms. The lessons learned from these events resonated throughout the industry, shaping security practices and prompting proactive measures to prevent similar attacks on future devices.The PSP’s relatively open architecture and accessible firmware allowed for a variety of exploits.
This accessibility, while fostering a vibrant hacking community, also demonstrated a vulnerability that could be replicated in other devices. The ease with which hackers could gain unauthorized access served as a stark reminder of the importance of secure design principles in the development of any electronic device. This case study also highlighted the importance of proactive security measures and rapid responses to emerging threats in the ever-evolving digital world.
Influence on Broader Digital Security Discussions, Hackers break in to sony psp
The PSP hacking incidents brought the issue of digital security to the forefront of public and industry discussions. These events prompted a critical examination of security practices across various sectors, emphasizing the importance of robust security protocols from the design phase to ensure that vulnerabilities were not exploited. The experiences highlighted the need for a holistic approach to security, encompassing not just technical solutions but also user awareness and education.
Comparison with Other Electronic Device Attacks
PSP hacking, while notable, was not unique in the realm of electronic device attacks. Similar exploits targeted other handheld devices and embedded systems, demonstrating the common vulnerability to sophisticated attacks. The difference often lay in the accessibility of the target systems and the resources available to hackers. The availability of readily accessible information and tools, combined with the PSP’s architecture, allowed for a broader impact than similar attacks on less accessible devices.
Broader Implications of Handheld Device Vulnerabilities
The vulnerabilities discovered during PSP hacking highlight the potential consequences of neglecting security in handheld devices. These devices often handle sensitive data, from personal information to financial transactions. The ease with which hackers could potentially access this data emphasized the critical need for robust security protocols in all handheld devices, extending beyond the technical aspects to encompass physical security and user awareness.
Lessons Learned for Future Device Development
PSP hacking served as a valuable case study for developers and designers of future devices. The incidents revealed the importance of secure coding practices, rigorous testing, and proactive vulnerability assessments. Furthermore, the rapid response to these exploits highlighted the need for collaboration between researchers, developers, and security experts to identify and address vulnerabilities quickly. Developers started incorporating more secure coding practices and more rigorous security testing.
Table: Impact on Security Practices
| Year | Key Developments | Impact |
|---|---|---|
| 2004-2007 | Initial PSP hacking exploits, showcasing vulnerabilities in firmware and hardware. | Increased awareness of security vulnerabilities in embedded systems, particularly handheld devices. |
| 2007-2009 | Emergence of advanced hacking techniques targeting the PSP, and development of custom exploits. | Triggered development of stronger security measures in firmware and operating systems. Increased emphasis on secure development practices. |
| 2009-2011 | PSP hacking incidents leading to the adoption of security features in handheld devices, such as improved access controls. | Handheld device manufacturers started incorporating more advanced security features, prompting a broader industry-wide adoption of better security practices. |
Ultimate Conclusion
In conclusion, the hacking of the Sony PSP serves as a crucial case study in digital security. The vulnerabilities exploited, the methods employed, and the resulting consequences shed light on the ongoing battle between attackers and defenders in the digital world. This analysis highlights the importance of robust security measures and continuous vigilance in the face of evolving threats.
The lessons learned from this period continue to influence security practices in handheld devices and beyond.