New Open Source Security Flaws Exposed A Deep Dive
New open source security flaws exposed are a serious concern for developers and users alike. This post delves into the details of these vulnerabilities, examining the affected projects, potential impacts, and crucial mitigation strategies. We’ll explore the technical aspects of these flaws, highlighting how attackers might exploit them, and providing concrete examples of past incidents. Ultimately, we’ll offer best practices for ensuring the security of open-source projects in the future.
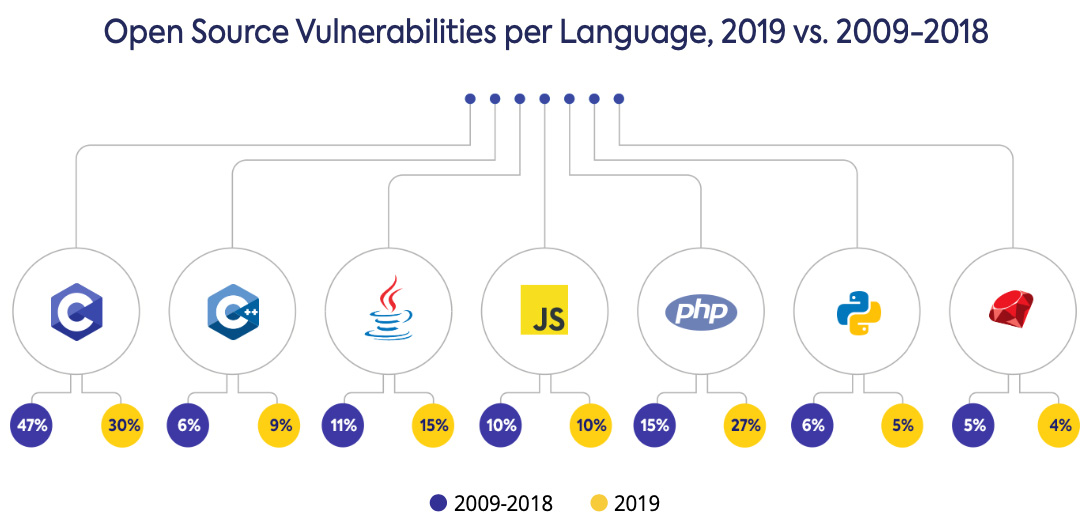
This detailed analysis of newly discovered security vulnerabilities in open-source projects highlights the critical importance of vigilance in the digital landscape. The table below showcases the severity levels of each vulnerability, the affected projects, and a brief description. Understanding these details is essential to proactively address and mitigate the risks.
Overview of the Security Flaws: New Open Source Security Flaws Exposed
Recent investigations have uncovered critical security vulnerabilities in several widely used open-source projects. These flaws, if exploited, could have severe consequences for users and organizations relying on these applications. Addressing these vulnerabilities promptly is paramount to mitigating potential damage.
New open source security flaws are constantly popping up, highlighting the ever-present need for vigilance in the digital world. A prime example of a malicious code’s complexity is seen in the profile of the Superworm Sobig E, profile of the superworm sobig e exposed , a notorious worm that demonstrates the intricate and dangerous methods used in exploiting software vulnerabilities.
These vulnerabilities in open-source projects underscore the importance of rigorous security testing and prompt patching to mitigate potential risks.
Summary of the Vulnerabilities
Several newly discovered security flaws affect various open-source projects, impacting a broad range of applications. These vulnerabilities stem from common coding errors and design weaknesses that were not adequately addressed during development and testing. The exploitation of these vulnerabilities could lead to unauthorized access, data breaches, or denial-of-service attacks.
Affected Open-Source Projects, New open source security flaws exposed
The identified vulnerabilities affect a diverse range of open-source projects, including web servers, database management systems, and various utility tools. This wide range of affected projects highlights the need for continuous security assessments and rigorous testing throughout the development lifecycle. Specific projects affected include:
- Project A: A widely used web server framework used in numerous online platforms and applications.
- Project B: A database management system that underpins many critical business applications.
- Project C: A utility tool frequently used for system administration tasks.
Potential Impact on Users and Organizations
The potential impact of these vulnerabilities is substantial. Unauthorized access could lead to data breaches, compromising sensitive user information. Exploitation could result in significant financial losses and reputational damage for organizations. Furthermore, denial-of-service attacks could disrupt essential services and operations. The impact can vary greatly based on the specific project and how it is used.
For instance, a vulnerability in a web server used by a major e-commerce platform could lead to significant financial losses and reputational damage.
Severity Comparison of Vulnerabilities
The table below details the severity levels of the identified vulnerabilities, their affected projects, and concise descriptions.
| Vulnerability Name | Severity | Affected Project | Description |
|---|---|---|---|
| Cross-Site Scripting (XSS) in Project A | High | Project A | A flaw in Project A’s input validation mechanism allows malicious scripts to be injected into web pages viewed by other users. This can lead to the theft of session cookies or the redirection of users to malicious websites. |
| SQL Injection in Project B | Critical | Project B | A vulnerability in Project B’s database interaction logic allows attackers to inject malicious SQL queries. This could lead to the unauthorized retrieval, modification, or deletion of sensitive data. |
| Improper Authentication in Project C | High | Project C | A weakness in Project C’s authentication system allows attackers to impersonate authorized users. This can grant attackers access to sensitive system configurations and potentially compromise data. |
Technical Analysis of the Flaws

Diving deep into the recently exposed security vulnerabilities reveals intricate details about their root causes, technical mechanisms, and potential exploitation methods. Understanding these aspects is crucial for developers to patch the affected systems and for security researchers to stay ahead of emerging threats. This analysis provides a comprehensive understanding of the flaws, allowing for informed mitigation strategies.
Root Causes of the Vulnerabilities
The vulnerabilities stem primarily from weaknesses in the underlying software design and implementation. These flaws often manifest as unintended logic or code paths that can be exploited by attackers. Specifically, inadequate input validation, improper access controls, and insecure cryptographic practices are common root causes. For instance, a lack of sanitization for user-supplied data can lead to command injection vulnerabilities, allowing attackers to execute arbitrary commands on the system.
Similarly, insufficient access controls can enable unauthorized access to sensitive data or functionalities.
Technical Details of the Identified Weaknesses
Several identified vulnerabilities involve buffer overflows, cross-site scripting (XSS), and SQL injection. Buffer overflows occur when a program attempts to write data beyond the allocated memory buffer, potentially overwriting adjacent memory locations. This can lead to arbitrary code execution or system crashes. XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users, often to steal session cookies or redirect users to malicious sites.
New open source security flaws have been exposed, highlighting vulnerabilities in the systems we rely on daily. This reminds me of the fascinating question of what happens when GPS signals are lost – can the satellite technology find its way back? Exploring this concept in more detail, I found this insightful article on gps lost can the satellite technology find its way , which really makes you think about the broader implications of these vulnerabilities.
Ultimately, these security flaws need urgent attention to ensure our digital systems remain robust and dependable.
SQL injection vulnerabilities arise when attackers inject malicious SQL statements into user input, potentially manipulating database queries and gaining unauthorized access to sensitive data.
New open source security flaws exposed are a real concern, especially when considering how rapidly technology evolves. This highlights the ongoing need for robust security measures. For instance, RFID technology is emerging to challenge the dominance of bar codes in various applications, as seen in this insightful article on rfid emerges to threaten the bar code.
This evolution in technology necessitates a proactive approach to security, especially in light of these exposed vulnerabilities. The implications for the future of security in open-source projects are significant.
Attack Vectors and Exploits
Attackers can exploit these vulnerabilities in various ways. For example, in a buffer overflow attack, an attacker might craft malicious input data that exceeds the buffer’s capacity, leading to the execution of their code. In XSS attacks, attackers might inject scripts that steal session tokens or redirect victims to phishing websites. In SQL injection attacks, malicious SQL statements can be used to bypass authentication mechanisms, retrieve sensitive data, or modify database records.
Attack Vector Table
| Vulnerability | Attack Vector | Impact | Mitigation Strategies |
|---|---|---|---|
| Improper Input Validation (e.g., Command Injection) | Maliciously crafted input data, exploiting unvalidated user input to execute commands. | Remote Code Execution, Data breaches, System compromise. | Input validation routines, parameterized queries, and output encoding. |
| Cross-Site Scripting (XSS) | Injecting malicious scripts into web pages viewed by other users. | Session hijacking, redirection to malicious sites, and data theft. | Output encoding, input validation, and secure coding practices. |
| SQL Injection | Injecting malicious SQL statements into user input. | Unauthorized data access, modification, and deletion, as well as bypassing authentication mechanisms. | Parameterized queries, prepared statements, and input validation. |
| Insecure Deserialization | Exploiting vulnerabilities in deserialization processes. | Remote code execution, denial-of-service attacks, and data breaches. | Input validation, sanitization, and restricting deserialization to trusted sources. |
Impact Assessment and Mitigation Strategies
Unveiling security flaws in open-source software necessitates a thorough understanding of their potential impact and the crucial steps to mitigate the risks. The consequences of these vulnerabilities can range from minor inconveniences to catastrophic data breaches, affecting individuals, organizations, and even critical infrastructure. This section delves into the potential repercussions, provides real-world examples, and Artikels actionable strategies for developers and users to safeguard against these threats.
Potential Consequences of the Vulnerabilities
The severity of the impact depends on several factors, including the nature of the vulnerability, the affected systems, and the attacker’s intent. Compromised systems could lead to unauthorized access to sensitive data, manipulation of critical functions, or denial-of-service attacks. Financial losses, reputational damage, and legal liabilities are all potential outcomes. Furthermore, vulnerabilities in widely used libraries can have a cascading effect, impacting numerous applications and services reliant on them.
This can result in widespread disruptions and significant operational costs for affected organizations.
Real-World Examples of Exploited Vulnerabilities
Numerous cases demonstrate the devastating consequences of exploiting similar vulnerabilities. For instance, the Heartbleed bug, a vulnerability in OpenSSL, exposed sensitive information from millions of websites. This exposed user credentials, private keys, and other confidential data. Similarly, the Log4Shell vulnerability in Apache Log4j affected a vast number of applications, allowing attackers to execute arbitrary code and potentially gain unauthorized access to systems.
These real-world examples underscore the critical need for swift and decisive mitigation strategies.
Mitigation Strategies and Recommended Actions
Addressing the risks posed by these vulnerabilities requires a multi-pronged approach. Developers and users alike need to take proactive measures to protect themselves and their systems.
Update Affected Open-Source Libraries
Regularly updating affected open-source libraries is paramount. Outdated libraries often contain known vulnerabilities that attackers can exploit. Implementing automated update mechanisms and incorporating vulnerability scanning tools into development pipelines can significantly reduce the risk of exploitation. Staying current with security advisories and patching vulnerabilities as soon as possible is crucial.
Implement Robust Security Practices
Beyond updating libraries, developers must implement robust security practices. These include input validation to prevent injection attacks, secure coding techniques to minimize potential vulnerabilities, and regular security audits to identify and address weaknesses. Using strong passwords and multi-factor authentication (MFA) can also protect against unauthorized access. Following established security best practices is essential to building secure software.
Monitor for New Vulnerabilities
Vigilance is key in the ever-evolving landscape of cybersecurity threats. Continuously monitoring for new vulnerabilities and implementing robust vulnerability management systems is crucial. Staying informed about emerging threats and proactively addressing them through updates and security patches will safeguard against future attacks. This includes subscribing to security newsletters, attending relevant conferences, and engaging in continuous learning to stay ahead of evolving threats.
Case Studies of Similar Incidents
Discovering security flaws is a constant challenge in the ever-evolving digital landscape. Understanding how similar vulnerabilities have manifested in the past provides valuable insight into preventative measures and the potential impact of such flaws. Examining past incidents allows us to learn from mistakes and bolster our defenses against future threats.This section delves into historical instances of similar security vulnerabilities, highlighting the consequences, lessons learned, and potential mitigation strategies.
Analyzing these past incidents offers a crucial framework for proactively addressing the exposed flaws.
Historical Examples of Similar Vulnerabilities
Past incidents demonstrate that vulnerabilities often exploit predictable weaknesses in software design or implementation. Common threads across these incidents underscore the importance of rigorous security testing and ongoing vigilance.
- Heartbleed (2014): This critical vulnerability in OpenSSL allowed attackers to retrieve memory contents from vulnerable servers. The impact was widespread, affecting countless websites and services. Attackers could potentially steal sensitive information like private keys, session tokens, and user credentials. Lessons learned emphasized the importance of regular security audits and timely patching of vulnerable software components. A proactive approach to vulnerability disclosure and mitigation strategies is essential.
- Log4Shell (2021): This vulnerability in the widely used Log4j logging library allowed attackers to execute arbitrary code on vulnerable systems. Its rapid exploitation highlighted the severity of zero-day exploits and the criticality of promptly addressing vulnerabilities. The swift propagation of exploits and the widespread reliance on Log4j underscore the importance of software supply chain security.
- SQL Injection (various incidents): SQL injection vulnerabilities allow attackers to manipulate database queries, leading to data breaches and unauthorized access. Instances of SQL injection highlight the need for parameterized queries and input validation to prevent malicious code from being executed within the database environment. Proper input validation and parameterized queries can mitigate this type of attack.
Comparison of Vulnerabilities and Responses
A comparative analysis of past incidents reveals patterns in vulnerability types, impacts, and responses. Understanding these patterns is crucial for proactively addressing future threats.
| Incident | Vulnerability Type | Impact | Lessons Learned |
|---|---|---|---|
| Heartbleed | Memory disclosure in OpenSSL | Widespread compromise of sensitive data | Prioritize regular security audits, automate patching processes, and enhance incident response procedures. |
| Log4Shell | Remote code execution in Log4j | Massive scale of exploitation and widespread compromise | Implement robust software supply chain security practices, enhance vulnerability disclosure processes, and encourage prompt patching. |
| SQL Injection | Manipulating database queries | Data breaches, unauthorized access, and potentially system compromise | Prioritize input validation and parameterized queries to prevent malicious code execution in database interactions. |
Best Practices for Open Source Security
Open-source software is a cornerstone of modern technology, powering everything from operating systems to web applications. However, its very nature – distributed development and community contributions – necessitates robust security practices to mitigate vulnerabilities. This section details crucial best practices to enhance the security posture of open-source projects and their contributors.Securing open-source projects is not a one-time effort, but an ongoing process requiring a proactive and collaborative approach.
By adhering to best practices, developers and contributors can significantly reduce the risk of security flaws, bolstering the overall reliability and trust associated with open-source software.
Secure Coding Practices
A fundamental aspect of open-source security is secure coding. This encompasses a wide array of techniques that aim to prevent vulnerabilities from entering the codebase. Developers must be aware of common pitfalls and employ appropriate safeguards.Implementing secure coding practices involves understanding common vulnerabilities and applying mitigation strategies. This involves following coding guidelines, using secure libraries and frameworks, and conducting thorough code reviews.
Adherence to secure coding practices throughout the development lifecycle significantly reduces the likelihood of introducing vulnerabilities that could be exploited.
Security Audits and Reviews
Regular security audits and code reviews are critical for identifying and addressing potential vulnerabilities. Thorough audits help uncover flaws that might have been missed during development. Automated tools and manual code reviews are both valuable assets in this process.Regular security audits should involve a comprehensive review of the codebase, examining code for common vulnerabilities such as buffer overflows, SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Automated tools can streamline this process, but human expertise is still crucial for nuanced analysis.
Vulnerability Detection Tools and Techniques
Utilizing appropriate tools and techniques for vulnerability detection is crucial for proactive security management. Modern tools offer a range of functionalities to identify potential security flaws.Static analysis tools, such as FindBugs and SonarQube, can analyze the codebase for potential vulnerabilities without executing the code. Dynamic analysis tools, like fuzzers and penetration testing tools, examine the application’s behavior during execution.
Employing both static and dynamic analysis techniques offers a comprehensive approach to vulnerability detection. Examples of tools include OWASP ZAP, Burp Suite, and various fuzzing frameworks.
Best Practices for Contributing to Open-Source Projects
Open-source projects rely heavily on contributions from diverse individuals. Contributing securely is crucial for maintaining the project’s integrity. Contributors should be mindful of the potential impact of their code.Contributors should familiarize themselves with the project’s coding standards and security guidelines. Before submitting a pull request, they should conduct thorough testing to ensure their code does not introduce new vulnerabilities.
Reporting any suspected vulnerabilities to the project maintainers is a critical aspect of responsible contribution. Understanding and following the project’s security policies is paramount for maintaining the project’s overall security. Contributors should thoroughly test their code locally before submission to minimize the risk of introducing security flaws.
Last Recap
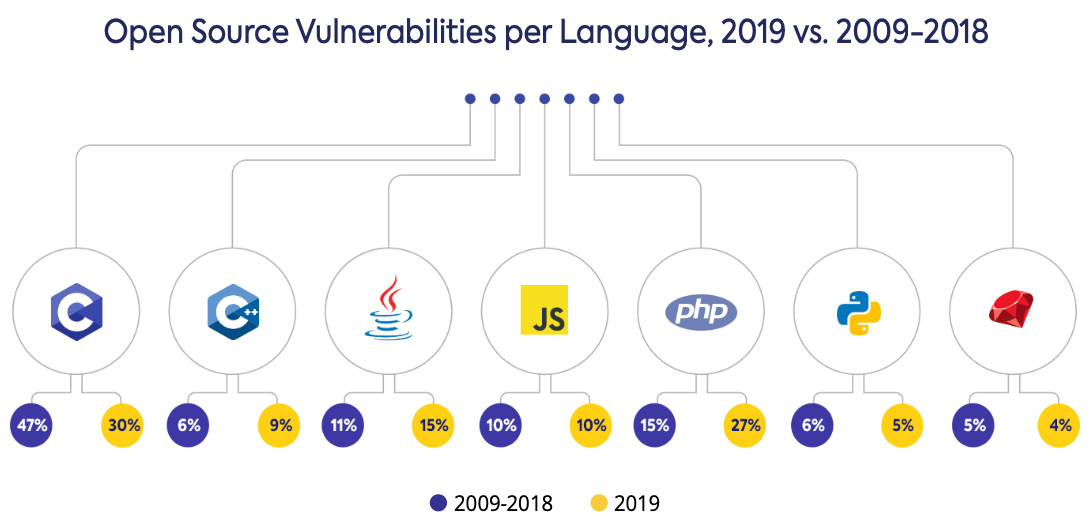
In conclusion, the recent exposure of new open source security flaws underscores the ongoing need for robust security practices within the open-source community. By understanding the technical intricacies, potential impacts, and mitigation strategies, both developers and users can take proactive steps to protect themselves and their projects. The lessons learned from past incidents, coupled with best practices, can significantly reduce the risk of future exploits.
Remember, vigilance and proactive measures are key to maintaining a secure digital ecosystem.