Network Security Warnings Ring Out A Critical Guide
Network security warnings ring out, signaling potential threats to your systems. This comprehensive guide delves into the nature of these warnings, from identifying their source to developing mitigation strategies and responding effectively. Understanding these alerts is crucial for maintaining a secure network environment and preventing significant damage.
We’ll explore the different types of warnings, their potential impact, and the essential steps for analyzing root causes, developing effective mitigation strategies, and responding appropriately. This isn’t just about technical jargon; it’s about safeguarding your valuable data and assets.
Understanding the Nature of Network Security Warnings
Network security warnings are crucial indicators of potential threats to your systems and data. They signal a deviation from normal network behavior, prompting immediate attention and action. Understanding their nature, characteristics, and the importance of prompt responses is paramount for maintaining a secure network environment.These warnings, ranging from minor anomalies to severe breaches, provide valuable insights into the health and integrity of your network infrastructure.
A comprehensive understanding allows for proactive measures to prevent further damage and ensure business continuity.
Defining Network Security Warnings
Network security warnings encompass a broad spectrum of events indicating potential security breaches. These include, but are not limited to, intrusion attempts, unauthorized access attempts, malware infections, suspicious user activity, and configuration errors. Each type of warning has unique characteristics, making a thorough understanding of each crucial.
Common Characteristics of Network Security Warnings
Identifying patterns and indicators of threats is vital for efficient response. Common characteristics often precede or accompany these warnings:
- Unusual network traffic patterns: Sudden spikes in traffic volume, unusual destinations, or unusual protocols can indicate an intrusion attempt or malware activity.
- Login failures or failed authentication attempts: Repeated failed login attempts from a specific IP address or user account might signify a brute-force attack or unauthorized access attempt.
- Suspiciously high CPU or memory usage: Elevated resource consumption by a specific process or application could indicate malware or malicious software attempting to exploit system resources.
- Suspicious file activity: Unexpected file creation, modification, or deletion, particularly in critical system directories, could indicate a malware infection or unauthorized access.
- Unusual or unexpected events in security logs: Monitoring security logs is essential. Any event outside the typical range or pattern should be investigated as a potential warning.
Significance of Timely Detection and Response
Prompt detection and response to network security warnings are paramount for mitigating potential damage. A delay in addressing these warnings can lead to data breaches, financial losses, reputational damage, and legal repercussions. The impact of these delays can be severe, escalating the consequences and complexity of the situation.
Importance of Accurate and Detailed Reporting
Accurate and detailed reporting of network security warnings is critical for effective threat analysis and incident response. Comprehensive reports should include:
- Date and time of the incident.
- Source of the warning (e.g., firewall logs, intrusion detection system, security information and event management (SIEM) system).
- Specific details about the event (e.g., IP addresses, user accounts, file paths).
- Description of the suspicious activity.
- Severity level of the warning.
- Actions taken to mitigate the threat.
Detailed reporting allows security teams to understand the nature of the threat, implement appropriate countermeasures, and prevent similar incidents in the future. Thorough documentation is essential for future analysis, audits, and legal compliance.
Categorizing Network Security Warnings

Network security warnings are crucial for maintaining the integrity and availability of systems. Understanding the source, type, and severity of these warnings allows for proactive response and mitigation of potential threats. Accurate categorization ensures efficient incident response and reduces the risk of overlooking critical vulnerabilities.
Categorization by Source
Network security warnings originate from various sources, each providing unique insights into potential threats. Analyzing the source of a warning helps in determining the nature of the threat and the appropriate response strategy. A comprehensive understanding of warning sources is vital for effective incident response.
| Source | Description | Example |
|---|---|---|
| Firewall Logs | Record attempts to access or leave the network that violate firewall rules. | Blocked connection attempt from an unknown IP address. |
| Intrusion Detection Systems (IDS) | Detect malicious activity or anomalous behavior within the network. | Suspicious network traffic patterns indicating a potential attack. |
| Security Information and Event Management (SIEM) systems | Collect and analyze security logs from various sources, providing a centralized view of security events. | Correlation of multiple events from different sources indicating a coordinated attack. |
Comparison of Warning Types
Different types of network security warnings vary in their potential severity and impact. Categorizing warnings by type aids in prioritizing responses and allocating resources effectively. Knowing the potential impact helps organizations tailor their responses.
| Warning Type | Description | Potential Severity | Impact |
|---|---|---|---|
| Unauthorized Access Attempts | Attempts to access resources without proper authorization. | Medium to High | Data breaches, system compromise, service disruption. |
| Suspicious Network Traffic | Unusual or unexpected network activity. | Low to High | Potential for denial-of-service attacks, data exfiltration, or system compromise. |
| Malware Infections | Presence of malicious software on the network. | High | Data breaches, system compromise, financial loss, reputational damage. |
Severity Level Classification, Network security warnings ring out
Classifying warnings into severity levels (e.g., low, medium, high) is essential for prioritizing responses and allocating resources. This allows security teams to focus on the most critical threats first. Establishing clear criteria for each level enhances efficiency.
- Low: Warnings indicating minor deviations from normal activity, such as a small number of failed login attempts or a minor anomaly in network traffic. These are not immediately critical but should still be monitored.
- Medium: Warnings that suggest a potential security risk, such as a large number of failed login attempts or a significant change in network traffic patterns. These require attention and investigation.
- High: Warnings that indicate an imminent threat to the network or system, such as a detected malware infection, a successful unauthorized access attempt, or a large-scale denial-of-service attack. Immediate action is critical.
Structured Categorization Format
A standardized format for categorizing network security warnings ensures consistency in analysis and reporting. This structure helps in identifying trends, patterns, and potential threats more effectively. It also facilitates effective communication between security teams.
A structured format for network security warnings should include the date and time of the event, the source of the warning, the specific type of warning, a detailed description of the event, the severity level, and any relevant supporting information.
Analyzing the Impact of Warnings
Ignoring network security warnings can have severe consequences, potentially leading to significant financial losses and reputational damage. Understanding the potential impact of different warning types and severities is crucial for proactive security management. A proactive approach to addressing these warnings can prevent costly incidents and maintain system stability.Ignoring network security warnings can have far-reaching consequences. From compromised data to operational disruptions, the potential damage can be extensive and costly.
Understanding the potential impact of different warning types is critical for developing effective mitigation strategies. Ignoring these warnings can compromise system security and potentially expose sensitive information.
Potential Consequences of Ignoring Warnings
Ignoring network security warnings can lead to a range of serious consequences. These warnings are not simply annoyances; they often signal potential vulnerabilities that could be exploited. Failing to address these warnings can lead to a variety of negative outcomes.
- Data breaches: Ignoring warnings about vulnerabilities in software or configurations can allow attackers to gain unauthorized access to sensitive data. This can lead to the theft of confidential information, including customer data, financial records, and intellectual property. A recent example of a large-scale data breach highlighted the devastating consequences of neglecting security warnings, resulting in substantial financial losses and reputational damage for the affected organization.
- Financial losses: Data breaches often result in substantial financial losses. These losses can include costs associated with data recovery, legal fees, regulatory fines, and lost revenue. Furthermore, reputational damage can impact future business opportunities and lead to decreased customer trust. Companies often have to invest significant resources to rebuild trust and recover from such incidents.
- Operational disruptions: Security warnings often indicate potential problems with system performance or availability. Ignoring these warnings can lead to service interruptions, downtime, and reduced productivity. The impact of such disruptions can vary greatly depending on the nature of the warning and the criticality of the affected systems.
Impact on System Performance and Availability
Network security warnings can significantly impact system performance and availability. Different types of warnings can trigger varying degrees of disruption. Understanding these impacts is crucial for prioritizing and addressing security issues effectively.
- Performance degradation: Some warnings indicate potential performance bottlenecks or resource constraints. Ignoring these warnings can lead to slower response times, reduced system efficiency, and increased user frustration. For example, a network warning about high CPU utilization could indicate an impending system crash if left unaddressed.
- Service interruptions: Warnings related to critical system components or network connectivity issues can lead to service interruptions. Ignoring these warnings could result in complete system downtime, impacting business operations and potentially leading to significant financial losses. In a recent case, a failure to address warnings about a failing network switch resulted in a prolonged outage, causing substantial operational disruption.
Impact on Business Operations
The severity of warnings can directly affect business operations. Understanding the relationship between warning levels and the potential impact is crucial for effective risk management. Prioritizing and addressing security concerns based on warning severity is key to preventing disruptions and maintaining operational efficiency.
- Operational efficiency: Addressing warnings related to minor performance issues can improve operational efficiency and user experience. Prompt resolution of these issues can prevent them from escalating into more significant problems.
- Business continuity: Addressing critical warnings related to system stability and security is essential for maintaining business continuity. Ignoring these warnings can lead to major disruptions and potentially irreversible consequences.
Correlation Between Warning Severity and Risks
The following table illustrates the correlation between warning severity and the associated risks. Understanding this correlation is essential for prioritizing security issues and allocating resources effectively.
| Warning Severity | Description | Potential Risks |
|---|---|---|
| Low | Minor performance issues, configuration changes | Reduced efficiency, potential for minor disruptions |
| Medium | Vulnerabilities, potential security breaches | Data compromise, financial losses, reputational damage |
| High | System instability, critical component failures | System downtime, business disruption, significant financial losses |
Investigating the Root Causes
Pinpointing the source of network security warnings is crucial for effective remediation. Ignoring these warnings can lead to escalating risks, from data breaches to system downtime. A proactive approach to investigation is essential to prevent future incidents and maintain a robust security posture. Understanding the underlying causes allows for targeted solutions, preventing recurrence and enhancing overall network security.A deep dive into the potential sources of these warnings is necessary.
This involves examining various factors, including software vulnerabilities, misconfigurations, and even malicious activity. The investigation process should be methodical and systematic, ensuring that all possible causes are explored and documented. This approach fosters a culture of proactive security, rather than simply reacting to alerts.
Potential Sources of Network Security Warnings
Network security warnings often stem from a combination of factors. These range from easily avoidable human errors, such as misconfigurations, to more sophisticated threats like malicious actors exploiting vulnerabilities. Analyzing these potential sources helps in determining the appropriate course of action.
- Software Vulnerabilities: Outdated or vulnerable software packages are a significant source of warnings. These vulnerabilities can be exploited by attackers to gain unauthorized access to the network. Examples include outdated operating systems, web servers, or applications. Regular patching and updates are crucial to mitigate this risk. If a system is known to be vulnerable, implementing appropriate countermeasures, like firewalls or intrusion detection systems, is critical.
- Misconfigurations: Incorrectly configured network devices, such as firewalls or routers, can create security loopholes. Weak passwords, improper access controls, and unsecured ports are all examples of misconfigurations. Regular security audits and configuration reviews can identify and fix these issues. A poorly configured firewall might allow unauthorized traffic, leading to warnings. Similarly, an open port can expose a service to attack.
- Malicious Actors: Sophisticated attacks by malicious actors, such as hackers or cybercriminals, can generate numerous network security warnings. These attacks can range from simple denial-of-service attacks to more complex exploits designed to steal sensitive data. Strong network security measures, including intrusion detection and prevention systems, are essential to detect and mitigate these threats. Examples include phishing attempts, malware infections, and ransomware attacks.
Implementing robust security protocols and user awareness training are vital to prevent such incidents.
Examples of Network Security Best Practices and their Lack
Adherence to network security best practices is critical to minimizing the occurrence of warnings. The opposite, a lack of these practices, can lead to significant vulnerabilities and warnings.
- Regular Security Audits: Regular security audits help identify vulnerabilities and misconfigurations before they lead to serious incidents. A lack of these audits can allow undetected weaknesses to persist. Regular audits identify weak passwords, unauthorized access, and vulnerabilities that malicious actors might exploit.
- Strong Password Policies: Robust password policies, mandating strong, unique passwords, can significantly reduce the risk of unauthorized access. Weak or reused passwords are a common entry point for attackers. The absence of strong password policies can expose systems to brute-force attacks or dictionary attacks.
- Firewall Configuration: Proper firewall configuration is essential to control network traffic and block unauthorized access. Improper firewall configuration allows unwanted traffic to pass, generating warnings. A poorly configured firewall can lead to intrusions or denial-of-service attacks.
Investigating the Root Cause of a Warning
A systematic approach is needed to investigate the root cause of a network security warning. This process should involve a thorough examination of logs, system configurations, and potential threats.
- Reviewing Logs: Network logs contain valuable information about events that triggered the warning. Examining these logs helps to pinpoint the specific actions or events that led to the alert. Log analysis can reveal unusual activity, failed login attempts, or malicious code execution.
- Analyzing System Configurations: Examining the configurations of affected systems, including software versions and network settings, can help determine if any misconfigurations are contributing to the warning. This process involves comparing current configurations to established security best practices and documented standards.
- Identifying Potential Threats: Identifying potential threats, such as malicious actors, malware, or compromised accounts, is a critical step in the investigation. This often involves examining network traffic patterns, user behavior, and system logs for suspicious activity. Monitoring for known attack patterns can help in identifying and mitigating threats.
Procedures for Investigating Network Security Warnings
Following established procedures when investigating a network security warning is essential for efficiency and effectiveness. A structured approach ensures that all critical aspects are addressed and that the investigation is thorough.
- Documenting the Warning: Detailed documentation of the warning, including the date, time, source, and description, is critical for future reference and analysis. This documentation aids in tracking the problem and identifying patterns.
- Isolating the Affected Systems: Isolating affected systems from the network can prevent further damage or the spread of threats. This precaution ensures that the issue is contained and doesn’t impact other systems.
- Reporting and Escalation: Reporting the findings to the appropriate personnel, including IT security teams, is crucial. Escalating critical issues is vital for timely resolution. This ensures appropriate resources are allocated to address the issue promptly.
Developing Mitigation Strategies
Network security warnings are more than just alerts; they’re signals of potential vulnerabilities and threats. Proactive mitigation is crucial to preventing breaches and maintaining operational stability. Addressing these warnings head-on through well-defined strategies ensures a robust and resilient network infrastructure.Effective mitigation strategies are not just reactive measures to existing problems, but rather proactive steps to prevent future issues.
They require a structured approach that involves assessing risks, identifying threats, and implementing appropriate countermeasures. This process, coupled with ongoing vigilance and adaptation, forms the cornerstone of a strong security posture.
Importance of Implementing Security Measures
Addressing identified threats through appropriate security measures is paramount. Failure to act on security warnings can lead to significant consequences, ranging from data breaches and financial losses to reputational damage and legal liabilities. Implementing proactive measures minimizes these risks, safeguards sensitive information, and maintains the trust of users and stakeholders. The cost of inaction far outweighs the investment in robust security protocols.
Methods for Mitigating Risks
Various methods are available for mitigating the risks associated with network security warnings. These include:
- Patching Vulnerabilities: Regularly applying security patches to software and operating systems is a fundamental mitigation strategy. Patches address known vulnerabilities that malicious actors might exploit. Failure to apply patches leaves systems exposed to attacks, highlighting the importance of a robust patching process.
- Enhancing Security Protocols: Strengthening security protocols, such as firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs), significantly enhances network defenses. These tools act as barriers against unauthorized access and malicious activity, providing an essential layer of protection. For example, implementing multi-factor authentication adds an extra layer of security to user accounts, preventing unauthorized access even if passwords are compromised.
- Deploying Advanced Security Solutions: Advanced security solutions, such as endpoint detection and response (EDR) tools and security information and event management (SIEM) systems, provide comprehensive protection against sophisticated threats. These solutions monitor network activity, identify anomalies, and respond to incidents in real-time, significantly improving threat detection and response capabilities.
Best Practices for Preventative Measures
Best practices for implementing preventative measures against network security warnings include:
- Regular Security Audits: Conducting regular security audits helps identify potential weaknesses and vulnerabilities before they are exploited. This proactive approach allows for timely remediation and prevents significant breaches.
- Employee Training: Educating employees about security best practices and the importance of recognizing and reporting suspicious activities is crucial. Security awareness training empowers employees to act as the first line of defense against threats.
- Continuous Monitoring: Implementing continuous monitoring tools and techniques allows for real-time threat detection and response. This proactive approach enables organizations to swiftly identify and mitigate potential threats, minimizing their impact.
Structured Approach for Developing Mitigation Strategies
A structured approach for developing mitigation strategies involves:
- Risk Assessment: Identifying potential threats and assessing their likelihood and impact on the network. This includes evaluating the potential financial, reputational, and operational consequences of a breach.
- Threat Modeling: Analyzing potential threats and vulnerabilities, understanding attack vectors, and developing scenarios for potential attacks. This proactive step allows for the development of targeted mitigation strategies.
- Vulnerability Management: Implementing a process for identifying, assessing, and remediating vulnerabilities in software, hardware, and configurations. This ensures that systems are continuously protected against known weaknesses.
Responding to Network Security Warnings: Network Security Warnings Ring Out
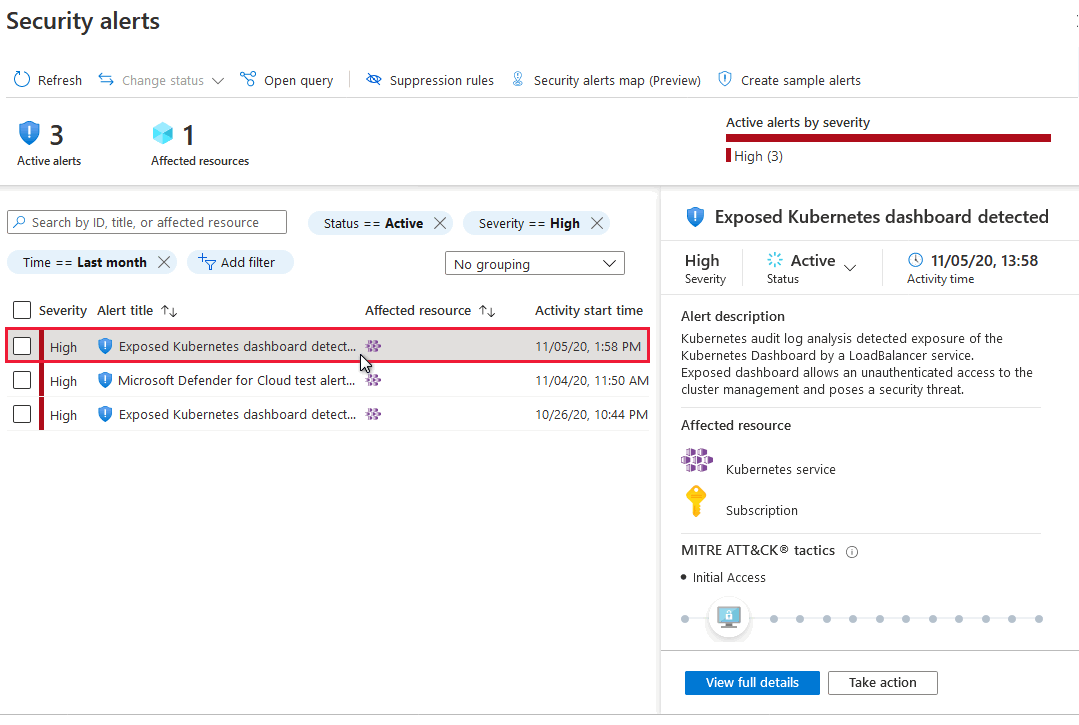
Network security warnings, ranging from minor anomalies to critical breaches, require a swift and well-defined response plan. A proactive approach, coupled with a clear understanding of escalation procedures, is crucial to minimizing damage and maintaining operational stability. Ignoring these warnings can lead to significant losses, both financially and reputationally. A robust response plan ensures the timely containment and resolution of potential threats.
Response Plan for Different Warning Levels
A tiered response plan based on the severity of the warning is essential. This allows for appropriate resource allocation and prioritization of actions. Different warning levels trigger different response protocols, from basic monitoring to full-scale incident response. The plan should Artikel specific actions for each level, including escalation procedures and contact information.
- Low-level warnings: These warnings often indicate minor anomalies, such as unusual network traffic patterns or software vulnerabilities. The response involves monitoring the situation closely, potentially patching vulnerabilities, and performing routine security checks. This step ensures the issue doesn’t escalate to a more serious threat.
- Medium-level warnings: Medium-level warnings signal potential threats that require immediate attention. The response includes investigating the root cause, isolating affected systems, and implementing temporary mitigation strategies. This could involve blocking suspicious IP addresses or temporarily disabling vulnerable services.
- High-level warnings: These warnings signify significant security breaches or imminent threats. The response escalates to a full-scale incident response, involving a dedicated team to contain the threat, assess the damage, and implement permanent mitigation measures. This may involve notifying affected users, coordinating with law enforcement, and conducting forensic analysis.
Procedure for Isolating Affected Systems or Networks
Isolating affected systems or networks is a crucial step in containing a security incident. This prevents the threat from spreading further and allows for focused investigation and remediation. The isolation procedure should be well-documented and readily available to security personnel.
- Identify affected systems: Use network monitoring tools and logs to pinpoint systems or networks exhibiting anomalous behavior.
- Isolate affected systems: Employ network segmentation, firewalls, and other controls to isolate the compromised systems or networks from the rest of the network.
- Document the isolation procedure: Detailed documentation of the isolation process is critical for incident reporting and future reference.
Importance of Communication and Collaboration
Effective communication and collaboration among security teams, IT personnel, and other stakeholders are paramount during a security incident. A well-defined communication plan facilitates the rapid dissemination of information, ensuring everyone is aware of the situation and their roles.
- Establish communication channels: Designate clear communication channels for incident updates and information sharing.
- Foster collaboration: Encourage cooperation among different teams involved in the incident response process.
- Provide regular updates: Keep all stakeholders informed of the progress of the incident response, including any changes to the situation.
Process for Reporting and Documenting Security Incidents
Reporting and documenting security incidents is critical for learning from past events and improving future security posture. A standardized incident reporting process ensures consistency and completeness of information.
- Incident report template: Develop a standardized template for reporting security incidents, including details about the incident, impact, response actions, and corrective measures.
- Record all relevant data: Collect and document all relevant data related to the incident, such as logs, screenshots, and communication records.
- Follow established procedures: Adhere to the established procedures for incident reporting and documentation to ensure accuracy and completeness.
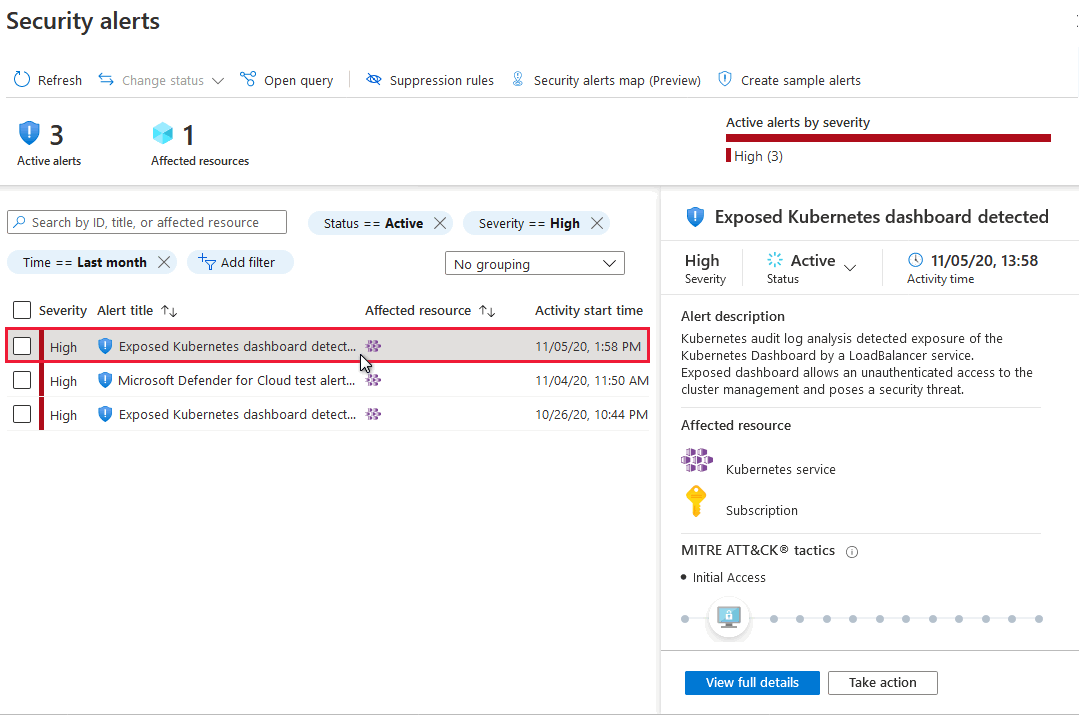
Illustrative Examples of Network Security Warnings
Network security warnings are crucial indicators of potential threats to your systems. Understanding their nuances allows for swift and effective responses, minimizing potential damage. These warnings, ranging from minor anomalies to severe breaches, require careful analysis to pinpoint the root cause and implement appropriate countermeasures.
Examples of Network Security Warnings
Various types of network security warnings exist, each signifying different potential problems. These warnings often come in the form of log entries, alerts, or notifications, prompting immediate investigation. The specific content of these warnings depends on the type of security tool used, but common themes emerge.
- Suspicious Login Attempts: A user account might be targeted for unauthorized access. This is often indicated by a series of failed login attempts from unusual IP addresses. A log entry might read: “Failed login attempt from 192.168.1.100 for user ‘admin’ at 10:00 AM.” The potential implication is a brute-force attack or a credential-stuffing attempt. This example underscores the importance of strong passwords and multi-factor authentication.
- Unauthorized File Access: A warning may indicate that a file or directory has been accessed by an unauthorized user or process. A log entry could be: “User ‘attacker’ accessed file ‘confidential.txt’ at 14:30.” This could be a sign of a compromise, where an attacker gained unauthorized access to critical data. The importance of robust access control mechanisms is evident.
- Anomalous Network Traffic: Sudden spikes in network traffic from unusual sources or destinations can signify a Distributed Denial-of-Service (DDoS) attack or malware activity. A log entry might be: “Excessive network traffic from IP range 10.0.0.0/24 observed between 18:00 and 19:00.” The implication is a potential network overload or a denial-of-service attack, potentially disrupting services. This example highlights the need for intrusion detection systems and traffic monitoring.
- Malicious Software Detected: A security tool might detect known malicious software on a system. A log entry could be: “Malware ‘Trojan.Downloader’ detected on system ‘server1’ at 12:00 PM.” This warning signifies a significant security breach, possibly leading to data exfiltration or system compromise. This example demonstrates the critical role of antivirus software and regular system updates.
Interpreting Warning Messages
Analyzing warning messages requires understanding the context of the event. Details like the source IP address, user account, time of occurrence, and the specific file or resource involved can help in identifying the potential threat. A comprehensive understanding of the warning message’s content is critical for determining the appropriate course of action.
- Source Identification: Identifying the source of the warning is essential. Is it an internal user, an external IP address, or a known malicious actor? This helps to assess the severity of the threat.
- Event Timeline: Examining the sequence of events surrounding the warning can reveal a pattern or a series of actions that point to a larger security incident.
- Correlation Analysis: Correlating different warnings together can provide a clearer picture of the threat. For instance, if a suspicious login attempt is followed by unauthorized file access, it strengthens the evidence of a compromise.
Proactive Security Measures
These examples showcase the importance of proactive security measures. Implementing robust security policies, regularly updating software, employing intrusion detection systems, and educating users about security best practices are vital to mitigate the risks. Regular audits and security assessments can help to identify vulnerabilities before they are exploited.
Visual Representation of Security Warnings
Network security warnings are crucial for proactive threat management. Understanding their nature, impact, and lifecycle allows for effective response and mitigation. Visual representations provide a clear framework for comprehending these complex processes, aiding in faster incident response and improved security posture.
Flowchart of Detection, Analysis, and Response
A flowchart depicting the process of detecting, analyzing, and responding to network security warnings is a valuable tool for illustrating the sequential steps. It begins with the detection of a warning, which triggers an automated or manual alert. This alert is then analyzed to determine the severity, potential impact, and the source of the warning. Subsequently, a response plan is developed and implemented, encompassing mitigation strategies and communication protocols.
Finally, the effectiveness of the response is evaluated and documented for future reference. This cyclical process enhances the organization’s ability to adapt and improve its security posture.
Impact of Warnings on Network Performance
Different types of network security warnings have varying degrees of impact on network performance. A minor warning, such as a low disk space alert, may have a negligible effect. However, a severe warning, such as a distributed denial-of-service (DDoS) attack, can significantly degrade performance, leading to service disruptions and downtime. A visual representation using a bar graph or a color-coded system can effectively illustrate the correlation between the type and severity of the warning and its impact on network performance metrics like bandwidth utilization, latency, and packet loss.
Secure Network Architecture and Warning Handling
A secure network architecture must incorporate mechanisms for detecting and handling security warnings effectively. A schematic diagram illustrating a secure network architecture would showcase a layered approach to security, including intrusion detection systems (IDS), firewalls, and security information and event management (SIEM) systems. These systems work together to collect, analyze, and respond to security warnings, preventing potential threats from escalating.
Network Security Warning Lifecycle
The network security warning lifecycle is a continuous process, from detection to resolution and subsequent preventative measures. A visual representation of this lifecycle can be a cycle diagram illustrating the stages of detection, analysis, response, and evaluation. This diagram helps to highlight the importance of continuous monitoring and improvement in network security.
Closing Summary
In conclusion, network security warnings are vital indicators of potential threats. By understanding their nature, categorizing them, analyzing their impact, investigating root causes, developing mitigation strategies, and responding promptly, you can effectively protect your network. This guide provides a structured approach to navigate these critical alerts and maintain a secure digital environment.