Better PC Security Years Away
Better PC security years away is a critical concern, demanding proactive measures to combat increasingly sophisticated threats. This in-depth look delves into the evolution of PC security, from the early days of viruses to the emerging challenges posed by AI, quantum computing, and more. We’ll explore current practices, future advancements in hardware and software, and the importance of collaboration in staying ahead of evolving cyberattacks.
The historical context reveals a pattern of escalating threats, matched by innovative security responses. Looking ahead, we’ll analyze the potential of emerging technologies like AI and quantum computing, and their impact on the future of PC security. The discussion includes critical security practices, future hardware and software developments, and the crucial role of security infrastructure and policies.
PC Security Landscape Evolution: Better Pc Security Years Away
The digital world has witnessed a dramatic transformation in the past few decades, and with it, the nature of threats targeting personal computers has evolved significantly. From rudimentary viruses to sophisticated nation-state attacks, the security landscape has become increasingly complex. This evolution necessitates a continuous adaptation of security measures to mitigate the ever-present dangers.The initial threats were relatively simple, exploiting vulnerabilities in operating systems and applications.
However, as technology advanced, so did the sophistication of attacks, leading to a need for more robust and proactive security solutions. This evolution has shaped the security landscape we know today, demanding constant vigilance and innovation from both individuals and organizations.
Early Threats and Responses (1990s)
The 1990s marked the emergence of computer viruses as a significant concern. These early viruses, often spread through floppy disks and email attachments, primarily caused annoyance through system slowdown or file corruption. However, they demonstrated the potential for malicious code to disrupt operations. Antivirus software, though rudimentary, began to emerge as a response, focusing on signature-based detection.
This early stage of the security arms race saw the initial development of the concept of malware detection and prevention.
Sophistication and Volume Increase (2000s)
The 2000s saw a surge in the volume and sophistication of malware. The rise of the internet and the increasing interconnectedness of systems made it easier for threats to spread rapidly. Worms, exploiting vulnerabilities in network protocols, became a major concern, often causing widespread network disruptions. Phishing scams emerged, targeting users through deceptive emails, leading to data breaches and financial losses.
Security software evolved to incorporate heuristic analysis, enabling detection of previously unknown threats. Real-time scanning and proactive firewall technologies were also developed to mitigate network-based attacks.
Targeted Attacks and Data Breaches (2010s)
The 2010s saw the rise of more targeted attacks, often leveraging social engineering techniques and sophisticated malware to gain access to sensitive data. Ransomware, encrypting user files and demanding payment for their release, became a significant threat. Data breaches, often involving large organizations, exposed massive amounts of personal information, highlighting the vulnerability of systems to organized cybercriminals. Security software continued to evolve, incorporating advanced threat intelligence and sandboxing technologies to detect and block sophisticated malware.
Cloud security became a crucial area of focus.
Advanced Persistent Threats and AI-Powered Attacks (2020s)
The 2020s are characterized by advanced persistent threats (APTs) orchestrated by nation-states or sophisticated criminal organizations. These attacks are highly targeted and persistent, aiming to gain long-term access to systems for espionage or sabotage. The rise of artificial intelligence (AI) is also impacting the threat landscape, with AI-powered malware capable of adapting and evading traditional security measures. Machine learning and behavioral analysis are being integrated into security solutions to identify anomalies and prevent sophisticated attacks.
Zero-trust security models are becoming increasingly important, limiting access to sensitive data and systems.
Key Advancements in Security Technologies
| Year | Threat Type | Security Response | Impact |
|---|---|---|---|
| 1990s | Early viruses, system slowdown | Signature-based antivirus | Initial recognition of malware, rudimentary protection |
| 2000s | Worms, phishing, increased volume | Heuristic analysis, real-time scanning, firewalls | Increased sophistication and prevalence of threats, early development of proactive defenses |
| 2010s | Targeted attacks, ransomware, data breaches | Advanced threat intelligence, sandboxing, cloud security | Significant data breaches and financial losses, highlighting vulnerabilities in large-scale systems |
| 2020s | APTs, AI-powered attacks | Machine learning, behavioral analysis, zero-trust models | Need for more proactive and adaptive security solutions, evolving threats necessitate continuous improvement |
Emerging Threats and Vulnerabilities
The PC security landscape is constantly evolving, with new threats and vulnerabilities emerging at an alarming rate. Staying ahead of these threats requires a proactive and adaptable approach, focusing on emerging technologies and potential attack vectors. Understanding how these threats manifest and the countermeasures available is crucial for maintaining robust PC security.
AI-Powered Attacks
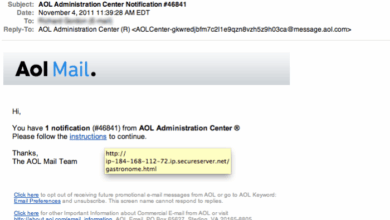
Artificial intelligence (AI) and machine learning (ML) are transforming both cybersecurity and cyberattacks. Attackers are increasingly leveraging AI to automate malicious activities, personalize attacks, and evade traditional security measures. This includes the development of sophisticated phishing campaigns tailored to individual users, the creation of more realistic deepfakes for social engineering, and the automation of malware creation. Sophisticated botnets and automated denial-of-service (DoS) attacks are also likely to become more common.
PC security improvements seem a long way off, likely years away. The debate around advancements like nanotechnology, as seen in the recent controversy surrounding Prince Charles’s views on prince charles attacked for opinions on nanotech , highlights the complex interplay between innovation and security concerns. Ultimately, we’re still a long way from truly robust PC security solutions.
Quantum Computing Threats
Quantum computing presents a significant long-term threat to current encryption methods. Algorithms like RSA and ECC, widely used for secure communication, are vulnerable to attacks from quantum computers. If large-scale quantum computers become available, they could potentially decrypt sensitive data encrypted using current methods, jeopardizing financial transactions, national security, and personal privacy. The development of quantum-resistant encryption algorithms is an urgent priority.
Future-Proofing PC Security
Future-proofing PC security against these emerging threats requires a multi-layered approach. This includes enhancing endpoint security with advanced threat detection and response capabilities, implementing robust access control measures, and promoting user awareness and training on emerging threats. Collaboration between security researchers, industry professionals, and government agencies is crucial to develop and implement effective countermeasures.
Potential Attack Vectors and Countermeasures
| Threat | Description | Mitigation Strategy | Impact |
|---|---|---|---|
| AI-powered phishing | Sophisticated phishing campaigns tailored to individual users using AI to analyze data about the target. | Advanced email filtering, machine learning-based detection of malicious emails, user training on identifying suspicious emails. | Financial losses, data breaches, reputational damage. |
| Quantum-enabled decryption | Decryption of sensitive data encrypted using current methods with the advent of large-scale quantum computers. | Transition to quantum-resistant encryption algorithms, development of post-quantum cryptography standards, investments in quantum-resistant hardware. | Compromised financial transactions, compromised national security, compromised personal data. |
| Automated malware creation | AI-powered creation of malware, including new variants and evading traditional detection methods. | Advanced malware analysis techniques, machine learning-based malware detection, proactive security updates, sandboxing technology. | Widespread system infections, data breaches, operational disruption. |
| Deepfake-based social engineering | Use of deepfakes to manipulate individuals into performing actions, like transferring funds or divulging sensitive information. | Improved image and video analysis tools, training users on identifying deepfakes, authentication measures beyond simple passwords. | Financial losses, reputational damage, compromise of sensitive information. |
Security Practices and Habits
PC security is an ongoing battle, constantly evolving with new threats. While specific technologies and tools may change, fundamental security practices remain crucial. These are the building blocks of a strong defense against cyberattacks, regardless of the latest malware or exploit. This section will explore the timeless principles of secure computing and the ongoing importance of user education.The future of cybersecurity hinges on a combination of technological advancements and user vigilance.
Strong security habits, coupled with a proactive approach to learning and adapting, will be essential for maintaining a secure digital environment. User education is not a one-time event but a continuous process of staying informed about emerging threats and adapting to changing security landscapes.
Strong Passwords and Multi-Factor Authentication, Better pc security years away
Robust passwords are the first line of defense against unauthorized access. Users should employ strong passwords that are difficult to guess or crack. These should be unique to each account and include a mix of uppercase and lowercase letters, numbers, and symbols. Complex passwords, coupled with the use of password managers, enhance security significantly. Multi-factor authentication (MFA) adds an extra layer of security by requiring more than just a password.
This often involves receiving a one-time code via text message or authenticator app. The addition of MFA greatly reduces the risk of account compromise even if a password is stolen. Examples include using Google Authenticator or similar applications.
Regular Software Updates
Software updates are critical for patching vulnerabilities that attackers exploit. Leaving software unpatched creates an open door for malicious actors to gain access to systems. Regularly updating operating systems, applications, and security software is a fundamental security practice that must be followed. These updates often contain critical security fixes that mitigate known threats. Failing to update systems exposes users to potentially severe security breaches.
User Education
User education plays a vital role in preventing security breaches. Educating users about phishing attacks, social engineering tactics, and other common threats empowers them to identify and avoid potential dangers. Training should cover topics like recognizing suspicious emails, avoiding suspicious links, and understanding the importance of strong passwords. Comprehensive user education programs can significantly reduce the risk of human error-related security incidents.
Regular Backups and Data Recovery Procedures
Regular backups are essential for data recovery in the event of a ransomware attack, hardware failure, or accidental deletion. Data loss can be devastating to individuals and organizations. Backups should be stored in a secure location, preferably offline, to prevent data loss from events affecting the primary system. Implementing a robust data recovery procedure allows for a quick restoration of lost data, minimizing disruption and downtime.
Cloud-based backup services and external hard drives are popular options.
Essential Security Practices
| Practice | Description | Importance | Implementation |
|---|---|---|---|
| Strong Passwords | Unique, complex passwords for each account. | Prevents unauthorized access. | Use a password manager, mix upper/lower case, numbers, symbols. |
| Multi-Factor Authentication (MFA) | Adds an extra layer of security. | Reduces risk of account compromise. | Enable MFA wherever possible. |
| Regular Software Updates | Patching vulnerabilities. | Mitigates known threats. | Enable automatic updates or set reminders. |
| User Education | Understanding security threats. | Reduces human error. | Regular training sessions, security awareness campaigns. |
| Regular Backups | Data recovery in case of loss. | Minimizes downtime and disruption. | Use cloud storage, external hard drives, or a combination. |
Hardware and Software Advancements
The future of PC security hinges on a symbiotic relationship between innovative hardware and sophisticated software. As threats evolve, so must our defenses. This section delves into the upcoming advancements in both areas, highlighting their potential to fortify our digital fortresses. The integration of cutting-edge technologies promises to make our PCs more resilient against emerging attacks.The increasing sophistication of cyberattacks necessitates a proactive approach to security.
Better PC security seems a long way off. While we ponder the future of digital defenses, it’s interesting to see how past tech trends, like Sony’s testing of copy-protected CDs, sony tests copy protected cds , foreshadowed some of the security issues we face today. Ultimately, progress in PC security is still a journey, not a sprint.
Future hardware and software developments will be crucial in countering these threats, enabling more robust protection against vulnerabilities.
Advancements in Hardware
Hardware advancements are poised to dramatically enhance PC security. New processors with built-in security features will provide a critical layer of defense against malicious code. These processors will incorporate hardware-level security mechanisms, effectively isolating potentially compromised software from the rest of the system.
Potential Advancements in Software
Software advancements are equally important in the ongoing battle against cyber threats. The development of more sophisticated intrusion detection systems (IDS) and prevention systems (IPS) is likely. These systems will learn from past attacks, proactively identifying and mitigating new threats in real-time.
Importance of Security-Focused Hardware Components
Security-focused hardware components, such as secure enclaves, are essential for protecting sensitive data. Secure enclaves are isolated hardware areas that can execute code without exposing it to the rest of the system. This protection is vital for safeguarding cryptographic keys and other sensitive information. They function as trusted execution environments, protecting data from unauthorized access even if the operating system is compromised.
Future Role of Trusted Execution Environments
Trusted execution environments (TEEs) are gaining traction in modern PCs. They provide a secure space for executing code, isolated from the main operating system. This isolation is crucial for safeguarding sensitive operations, such as cryptographic key management and secure boot processes. TEEs are essential in preventing malicious code from manipulating critical system components.
Anticipated Hardware and Software Features
| Feature | Description | Impact | Timeline |
|---|---|---|---|
| Secure Enclaves | Dedicated hardware areas with enhanced isolation for sensitive operations, such as cryptographic key management. | Increased protection against hardware-level attacks, safeguarding sensitive data. | 2024-2027 |
| Hardware-Assisted Encryption | Processors with built-in hardware support for encryption and decryption, speeding up security operations. | Faster and more efficient encryption and decryption, reducing computational overhead. | 2025-2028 |
| Advanced Intrusion Detection and Prevention Systems (IDS/IPS) | Software solutions that learn from past attacks to identify and mitigate new threats in real-time. | Proactive threat detection and mitigation, reducing the impact of zero-day exploits. | 2023-2026 |
| Self-Healing Operating Systems | Operating systems with built-in mechanisms to detect and automatically fix security vulnerabilities. | Reduced downtime due to security breaches and automatic patching. | 2026-2029 |
| Quantum-Resistant Cryptography | Algorithms that can withstand attacks from future quantum computers. | Ensuring the security of cryptographic systems even with advancements in computing power. | 2027-2030 |
Security Infrastructure and Policies

The future of PC security hinges on a robust and adaptable infrastructure, encompassing not just software but also policies and the evolving role of cloud-based solutions. A strong security posture requires proactive measures to anticipate and mitigate emerging threats. This necessitates a shift from reactive to predictive security strategies, incorporating user education, continuous monitoring, and the development of advanced threat detection mechanisms.
The Role of Cloud-Based Security Solutions
Cloud-based security solutions are rapidly becoming integral to PC security. These solutions leverage distributed computing power to analyze threats in real-time, enabling quicker response times and proactive threat detection. Services like cloud-based anti-malware and intrusion detection systems can identify and neutralize threats before they compromise individual PCs. Furthermore, cloud storage solutions, when coupled with robust access controls, enhance data protection by centralizing and encrypting sensitive information.
The scalability and flexibility of cloud solutions allow for dynamic adjustments to security protocols as new threats emerge.
Evolution of Security Policies and Frameworks
Security policies and frameworks are continuously evolving to address the increasing complexity of cyber threats. Traditional security policies often focused on perimeter defenses, but modern frameworks incorporate layered defenses, including endpoint security, data loss prevention, and user awareness training. The Zero Trust model, emphasizing continuous verification of users and devices, is gaining prominence, moving away from the assumption of trust.
This evolution ensures that security policies remain relevant and effective in the face of evolving threats and attack vectors.
Importance of Secure Configurations for Networks and Systems
Secure configurations are critical for protecting PCs and networks. This involves implementing strong passwords, enabling multi-factor authentication, and regularly updating software and operating systems. Regular vulnerability assessments are vital to identify and patch security weaknesses before attackers exploit them. Strict access controls and network segmentation limit the impact of a potential breach. The principle of least privilege, granting users only the necessary access, is paramount in mitigating potential damage.
PC security improvements seem a long way off. While we wait for those advancements, it’s interesting to see how companies are pushing the boundaries of other tech. Virgin, for example, is testing mobile TV, a fascinating development that might signal the future of entertainment. Virgin tests mobile tv could revolutionize how we consume media, but even these exciting leaps don’t seem to be speeding up the much-needed strides in better PC security, which remains a crucial area needing attention.
Increasing Importance of Privacy-Preserving Technologies
Privacy-preserving technologies are becoming increasingly important in the PC security landscape. Techniques like differential privacy, homomorphic encryption, and secure multi-party computation allow for data analysis and processing without compromising sensitive information. These methods are critical in fields such as healthcare, finance, and research, where data privacy is paramount. By implementing these technologies, organizations can balance the need for data utilization with the critical need to protect user privacy.
Future Role of Security Infrastructure
| Infrastructure | Description | Impact | Future Implications |
|---|---|---|---|
| Cloud-based security platforms | Centralized threat analysis, real-time detection, and response. | Enhanced threat detection and mitigation, reduced response times, scalability. | Integration with existing security systems, automated incident response, proactive threat intelligence. |
| Zero Trust security models | Verify every user and device before granting access. | Reduced attack surface, enhanced security posture, greater control over access. | Dynamic access controls, micro-segmentation of networks, improved security in cloud environments. |
| AI-powered threat detection systems | Proactive identification of advanced threats. | Early detection of novel and complex attacks, reduced breach windows. | Automation of security tasks, predictive threat modeling, personalized security recommendations. |
| Privacy-preserving technologies | Protect sensitive data during analysis and processing. | Increased data utility while maintaining user privacy. | Wide-scale adoption in healthcare, finance, and research, ethical use of data. |
The Role of Collaboration and Research
The future of PC security hinges on a robust collaborative ecosystem. Successfully tackling emerging threats requires a multifaceted approach involving researchers, industry experts, and government agencies. Isolated efforts, while valuable, are insufficient to address the complexity and rapid evolution of cyber threats. Shared knowledge and resources are crucial to stay ahead of malicious actors.The collaborative nature of security research and development is critical for building robust and adaptable defenses.
A shared understanding of evolving threats, coupled with a unified approach to developing countermeasures, is essential to future-proof PCs against increasingly sophisticated attacks.
Collaborative Efforts in Security
Collaborative efforts between researchers, industry, and government are essential for developing and implementing future-proof security solutions. This includes sharing threat intelligence, coordinating vulnerability disclosure processes, and jointly funding research projects. Effective collaboration fosters innovation and accelerates the development of new security technologies.
Significance of Open-Source Security Tools and Initiatives
Open-source security tools and initiatives are instrumental in strengthening the overall security landscape. Open-source projects offer transparent codebases, enabling community scrutiny and rapid identification of vulnerabilities. This transparency fosters collaborative problem-solving and promotes the rapid patching of security flaws. The collaborative nature of open-source projects allows for a wider range of expertise to contribute, leading to more comprehensive and robust security solutions.
Examples of Organizations Actively Involved
Numerous organizations are actively engaged in future-proofing PC security. Examples include organizations like the National Institute of Standards and Technology (NIST) in the United States, which develops and promotes security standards and best practices. Likewise, organizations like the Open Source Security Foundation (OpenSSF) play a crucial role in promoting secure open-source software development. Additionally, major technology companies are actively investing in research and development to enhance the security of their products and services.
Need for Continuous Research and Development
The ever-evolving nature of cyber threats necessitates continuous research and development in PC security. New vulnerabilities are discovered regularly, and attackers are constantly refining their techniques. This continuous cycle of threat analysis, vulnerability identification, and solution development is vital to maintain a robust defense. A proactive approach to security research is essential to mitigate future risks.
Key Organizations and Initiatives
| Organization | Focus | Impact | Initiatives |
|---|---|---|---|
| National Institute of Standards and Technology (NIST) | Developing and promoting security standards and best practices. | Provides a framework for secure systems and practices. | NIST Cybersecurity Framework, various security standards documents. |
| Open Source Security Foundation (OpenSSF) | Promoting secure open-source software development. | Enhances the security of open-source projects. | Security best practices, secure coding guidelines, vulnerability disclosure programs. |
| MITRE | Research and development in cybersecurity. | Provides resources and tools for threat analysis and vulnerability mitigation. | STIGs (Security Technical Implementation Guides), vulnerability databases. |
| Major Technology Companies (e.g., Google, Microsoft, Apple) | Integrating security into their products and services. | Creates secure products and services for end-users. | Regular security updates, proactive vulnerability research, development of security tools. |
Last Word

In conclusion, securing our PCs for the future requires a multi-faceted approach. While historical trends offer valuable lessons, the rapid evolution of technology demands continuous adaptation and proactive measures. From bolstering user habits and infrastructure to embracing innovation in hardware and software, the journey toward better PC security is a continuous process, demanding ongoing vigilance, collaboration, and research.
The need for better security will only increase with time, and the key is proactive measures that adapt to the ever-changing threat landscape.