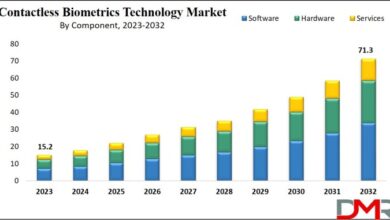
Biometrics A Security Makeover
Biometrics a security makeover – Biometrics: a security makeover is revolutionizing how we think about security. From fingerprint scans to facial recognition, biometric authentication methods are rapidly evolving, offering a more secure and user-friendly approach compared to traditional passwords. This shift is driven by the desire for enhanced security, improved user experience, and the need to address vulnerabilities in existing systems. We’ll explore the different biometric modalities, examine their strengths and weaknesses, delve into security considerations, and look towards the future of this exciting technology.
This in-depth look at biometrics covers everything from the historical context and evolution of biometric technologies to the ethical considerations surrounding their use. We’ll also explore how biometrics can be implemented in various security systems, examining potential attacks and the crucial role of data security protocols.
Introduction to Biometric Security
Biometric security is rapidly transforming how we authenticate ourselves in digital and physical spaces. This method of identification leverages unique, measurable human characteristics to verify identity, offering a powerful alternative to traditional password-based systems. It promises increased security, convenience, and user experience. This approach is increasingly crucial in a world where online transactions and physical access control are becoming ever more prevalent.Biometric authentication methods have a rich history, evolving from early attempts to identify individuals using fingerprints to sophisticated algorithms that analyze complex facial features.
Early applications focused on law enforcement and national security, but the growth of the internet and mobile technology has propelled biometric solutions into everyday life, from unlocking smartphones to accessing sensitive corporate data.
Evolution of Biometric Technologies
The evolution of biometric technologies has been a fascinating journey, starting with rudimentary fingerprint scanners and progressing to complex algorithms capable of recognizing subtle variations in facial features or iris patterns. Early implementations were often limited by the processing power available and the accuracy of the sensors. However, advancements in computing power and sensor technology have significantly improved the performance and reliability of biometric systems.
This progress has led to a greater acceptance and widespread adoption of biometric methods in various sectors. Examples of this evolution include the development of more accurate and faster fingerprint scanners, and the emergence of sophisticated facial recognition algorithms capable of identifying individuals across varying lighting conditions.
Comparison of Biometric Modalities
Different biometric modalities utilize distinct human characteristics for authentication. A comparative analysis of these methods is crucial to understanding their respective strengths and weaknesses.
| Biometric Method | Strengths | Weaknesses | Applications |
|---|---|---|---|
| Fingerprint | High accuracy, relatively low cost, well-established technology, high user acceptance. | Susceptible to damage or injury, potential for spoofing, may not be suitable for all environments, can be affected by environmental conditions. | Mobile devices, access control systems, law enforcement, and border security. |
| Facial Recognition | High usability, non-intrusive, can be implemented in various environments, readily available technology. | Vulnerable to spoofing with high-quality images, impacted by lighting conditions, potential for errors in low-quality images or obscured faces, privacy concerns are a significant factor. | Access control, surveillance, payment systems, and mobile devices. |
| Iris Scanning | High accuracy, highly unique characteristics, difficult to spoof, secure and reliable method. | Requires specialized hardware, can be affected by eye conditions, potentially more expensive to implement than other methods. | High-security access control, government applications, and financial transactions. |
Biometrics and Enhanced Security: Biometrics A Security Makeover
Biometric authentication is rapidly transforming security protocols, offering a powerful alternative to traditional methods. Leveraging unique physical or behavioral characteristics, biometrics provides a highly secure and convenient way to verify identities. This shift towards a more personalized and secure approach is particularly important in an increasingly digital world, where the protection of sensitive information is paramount.Biometrics’ inherent advantage over traditional methods lies in its ability to verify identity based on something unique to the individual, rather than something easily replicated, like a password.
Biometrics are definitely a promising security makeover, offering a unique approach to authentication. However, recent news about a blaster variant suspect arrested, as detailed in this article blaster variant suspect arrested , highlights the ongoing need for robust security measures beyond just biometric systems. Even with sophisticated biometric technology, a strong security infrastructure remains crucial, emphasizing the need for continuous vigilance in the digital realm.
This fundamental difference dramatically reduces the risk of unauthorized access, a significant improvement over passwords which can be compromised through various means. This is further amplified when combined with multi-factor authentication.
Enhanced Security Protocols, Biometrics a security makeover
Traditional security protocols, often relying on passwords, are susceptible to various forms of attacks. Phishing, brute-force attacks, and stolen credentials are common threats, leaving sensitive data vulnerable. Biometrics, on the other hand, creates a significantly stronger barrier to unauthorized access. The unique and immutable nature of biometric data makes it extremely difficult to replicate or compromise. This inherent strength is crucial in protecting sensitive information in today’s digital landscape.
Multi-Factor Authentication with Biometrics
Multi-factor authentication (MFA) significantly enhances security by requiring multiple verification steps. Combining biometric authentication with traditional methods like passwords or one-time codes creates a robust layered security system. This approach dramatically increases the complexity for attackers, making unauthorized access far less likely. The added layer of security significantly reduces the potential for compromise compared to single-factor authentication.
Improved User Experience
Biometric logins offer a significantly improved user experience. The seamless and often rapid authentication process, eliminating the need to remember and type passwords, enhances user satisfaction. This convenience is particularly important in today’s fast-paced digital environment, where efficiency is highly valued.
Addressing Security Vulnerabilities
Existing security vulnerabilities, such as weak passwords and credential stuffing, are significantly mitigated by biometric systems. By shifting from relying on easily guessable or compromised data, biometrics dramatically reduces the risk of unauthorized access. This transition is vital for organizations and individuals looking to bolster their security posture in the face of increasingly sophisticated attacks.
Implementation in Security Systems
Biometrics can be integrated into a wide range of security systems, significantly enhancing their effectiveness. In access control, biometric systems can authenticate individuals entering restricted areas, verifying identities in real-time. In online transactions, biometric verification can authenticate users making online purchases, protecting financial information and reducing fraud.
| Security System | Biometric Implementation |
|---|---|
| Access Control | Fingerprint scanners at building entrances, iris recognition for high-security areas. |
| Online Transactions | Facial recognition for online banking logins, voice recognition for verifying payments. |
Security Considerations in Biometric Systems
Biometric systems, while offering enhanced security, introduce unique security challenges. Understanding these considerations is crucial for implementing robust and trustworthy systems. Careful attention to privacy, secure storage, potential attacks, and data handling protocols is essential for maintaining public trust and preventing misuse.Biometric data, encompassing fingerprints, facial recognition, and iris scans, is highly sensitive. Its unique nature makes it vulnerable to various security threats if not handled with the utmost care.
Protecting this data requires a multi-layered approach encompassing secure storage, robust encryption, and access controls.
Privacy Concerns
The collection and storage of biometric data raise significant privacy concerns. Individuals may be apprehensive about the potential for misuse of their personal biometric identifiers, particularly in the context of surveillance or data breaches. Data breaches could expose sensitive information, potentially leading to identity theft, discrimination, or other harmful outcomes. Furthermore, the long-term implications of biometric data collection and storage on individual freedoms and rights require careful consideration.
Biometrics are promising a security makeover, offering a new layer of protection. But the past also shows us how easily things can change. Take, for example, the Aussie record industry’s raids on Kazaa offices, a significant event in the history of online file-sharing , demonstrating the evolving nature of digital security challenges. Even with advanced biometrics, staying ahead of these ever-shifting threats remains crucial for a truly secure future.
Secure Storage and Transmission
Robust security measures are paramount for safeguarding biometric data. Secure storage involves using encrypted databases and physical security measures to prevent unauthorized access. Transmission of biometric data must also employ strong encryption protocols to protect against interception and manipulation during transit. Data encryption, using techniques like Advanced Encryption Standard (AES), plays a crucial role in maintaining confidentiality.
Potential Attacks on Biometric Systems
Various attack vectors exist for compromising biometric systems. These include spoofing attacks, where individuals attempt to mimic biometric traits using fabricated or counterfeit data. For example, a fake finger or a manipulated facial image could be used to bypass security measures. Furthermore, attacks targeting system vulnerabilities or the data itself, such as phishing or social engineering tactics, pose significant risks.
Biometrics is definitely shaking up security, offering a fresh approach to access control. But, with the recent announcement of IBM introducing low price storage server, IBM’s new offering could significantly impact the infrastructure needed to support those biometric systems. This lower-cost storage might be a game-changer, making biometric security more accessible and potentially paving the way for broader adoption across various industries.
Intruders may try to obtain access to biometric databases, exploit vulnerabilities in the system architecture, or deceive users into divulging sensitive information.
Security Protocols for Biometric System Implementation
Implementing biometric systems demands a comprehensive set of security protocols. These protocols aim to prevent unauthorized access, data breaches, and manipulation of biometric data.
| Security Protocol | Description | Implementation Steps |
|---|---|---|
| Data Encryption | Using encryption algorithms to protect biometric data at rest and in transit. | Employing strong encryption algorithms like AES, securing data storage with encryption keys, and implementing encryption for network communications. |
| Access Control | Restricting access to biometric data based on user roles and permissions. | Implementing multi-factor authentication, defining clear access levels, and regularly reviewing and updating access privileges. |
| Biometric Template Protection | Protecting biometric templates to prevent unauthorized access and tampering. | Using secure storage methods for templates, employing hashing techniques, and ensuring the integrity of template generation and management processes. |
| Regular Security Audits | Conducting periodic security assessments to identify and address vulnerabilities. | Implementing penetration testing, vulnerability scanning, and regular security audits to identify and remediate any weaknesses in the system. |
Data Anonymization and De-identification
Data anonymization and de-identification techniques are crucial for mitigating privacy risks. Anonymization removes identifying information from biometric data, while de-identification techniques transform or mask identifying features. This process helps protect individual privacy while enabling the use of biometric data for legitimate purposes. For example, anonymized data can be used for research or analysis without compromising the identity of individuals.
Future of Biometric Security
Biometric security is rapidly evolving, driven by advancements in technology and the increasing need for robust authentication methods. The future promises even more sophisticated and integrated biometric systems, impacting everything from access control to financial transactions. This evolution will depend on the ongoing development of AI, hardware, and software, creating a more secure and convenient future.Emerging technologies are poised to reshape the landscape of biometric security, demanding a deeper understanding of their integration and potential implications.
From enhanced accuracy and speed to increased user convenience, the future of biometrics holds significant promise. The integration of AI, in particular, is set to dramatically alter how we perceive and use biometric systems.
Predictions on Future Biometric Technologies
Biometric technologies are likely to become more pervasive and integrated into daily life. We can expect to see a rise in the use of multi-factor authentication, combining various biometric traits for enhanced security. Furthermore, the development of more sophisticated algorithms and sensor technology will contribute to increased accuracy and reduced false acceptance rates. For example, facial recognition systems are already becoming commonplace in public spaces, and their accuracy is constantly improving.
Integration with Emerging Technologies
Biometrics will likely integrate seamlessly with emerging technologies, such as the Internet of Things (IoT) and wearable devices. This integration will facilitate more convenient and automated authentication processes. For instance, imagine unlocking your home door using a smartwatch or logging into your online banking account with a simple glance at a camera. The use of these technologies in conjunction with biometrics will offer a more secure and user-friendly experience.
Impact of Artificial Intelligence on Biometric Systems
AI is poised to significantly impact biometric systems. AI-powered algorithms can enhance the accuracy and speed of biometric identification, and can adapt to changing conditions or environments. For example, an AI system can learn to identify a user’s unique biometric traits even when they are under different lighting conditions or have slight variations in their posture. This adaptability will prove crucial in real-world applications.
Emerging Biometric Technologies and Applications
- DNA-based authentication: This emerging technology promises unprecedented security by using unique genetic markers for identification. Potential applications include high-security access control and criminal investigations.
- Brainwave-based authentication: Using patterns in brain activity for authentication could be highly secure and unique to each individual. This technology could revolutionize password-based authentication and access control.
- Liveness detection: Ensuring that the biometric sample is from a live individual is essential. Advancements in liveness detection will prevent spoofing attacks, improving the reliability of biometric systems.
The development of these technologies will require significant research and investment.
Influence of Hardware and Software Advancements
Advancements in hardware and software are driving improvements in biometric accuracy and efficiency. High-resolution sensors, more powerful processors, and sophisticated algorithms are making biometric systems more reliable and less prone to errors. This continuous development is crucial for widespread adoption.For example, the improvement in mobile phone cameras has significantly enhanced the performance of facial recognition systems, making them more accessible and practical for daily use.
Similarly, the development of more sophisticated algorithms can help to reduce false positives and negatives in fingerprint recognition systems.
Ethical Implications of Biometric Security
Biometric security, while offering significant advantages in safeguarding sensitive information, raises critical ethical concerns that must be carefully considered. The increasing reliance on unique biological traits for identification necessitates a thorough examination of potential pitfalls and safeguards to ensure responsible implementation. These concerns range from data privacy and potential misuse to the need for transparency and informed consent.The use of biometrics, like fingerprints, facial recognition, or DNA analysis, for security purposes, while potentially very effective, brings with it the ethical responsibility of ensuring that such technologies are deployed and managed in a manner that respects individual rights and freedoms.
The collection, storage, and utilization of biometric data must be governed by robust ethical frameworks and legal regulations to prevent potential harm and abuses.
Potential Misuse of Biometric Data
Misuse of biometric data can take various forms. Unauthorized access to biometric databases can lead to identity theft, impersonation, and fraudulent activities. For example, compromised facial recognition systems could enable individuals to gain access to restricted areas or systems by using someone else’s biometric data. This has already happened in the past with various data breaches and security lapses in both government and private sectors.
Need for Clear Guidelines and Regulations
Clear guidelines and regulations are crucial for managing biometric data responsibly. These regulations should address the collection, storage, processing, and disposal of biometric data, ensuring compliance with privacy laws and ethical principles. They should also Artikel the circumstances under which biometric data can be accessed, used, and shared. The absence of such guidelines can create a breeding ground for misuse and abuse, jeopardizing individual rights.
Importance of Informed Consent and Data Privacy
Informed consent is paramount in biometric systems. Individuals must be fully aware of how their biometric data will be collected, used, and protected. They must be provided with comprehensive information regarding the purpose, scope, and potential risks associated with the use of their biometric data. Strict data privacy measures are equally important. Strong encryption and access controls are essential to prevent unauthorized access and protect the confidentiality of sensitive biometric information.
Importance of Transparency in Biometric Systems
Transparency in biometric systems is essential to build trust and accountability. Individuals should have access to information about how their biometric data is being used and stored. Clear and concise explanations of the system’s workings, along with the mechanisms for redressal in case of errors or misuse, are necessary. Lack of transparency can lead to suspicion and erode public confidence in the system.
Openness about the system’s capabilities and limitations can help mitigate concerns and promote responsible use.
Case Studies and Examples
Biometric security is no longer a futuristic concept; it’s rapidly transforming various industries. This section explores real-world applications of biometric systems, highlighting successful implementations and the associated security considerations. We’ll examine how different industries leverage biometrics, analyzing the security measures put in place and the lessons learned from these case studies.
Real-World Implementations of Biometric Security
Biometric systems are increasingly used to enhance security and streamline processes across numerous sectors. This section presents a few notable examples of successful biometric security implementations.
| Industry | Case Study | Biometric Method | Security Measures |
|---|---|---|---|
| Finance | Example Bank (Hypothetical) | Facial Recognition | Multi-factor Authentication (MFA), including a one-time password (OTP) sent via SMS or email, in addition to facial recognition. Regular security audits and penetration testing. Facial recognition software updates are frequently implemented to prevent vulnerabilities. Robust data encryption protects sensitive customer data. |
| Healthcare | Secure Patient Access System (Hypothetical) | Fingerprint Scanning | Biometric data is stored securely, encrypted, and backed up regularly. Strict access controls are implemented based on user roles and permissions. Regular security awareness training for staff is conducted. Robust incident response plans are in place. |
| Transportation | Airport Security Screening (Hypothetical) | Iris Scanning | Biometric data is stored separately from other passenger information. Data encryption protects sensitive information during transmission. Robust authentication procedures verify identity. Regular security assessments are conducted to identify and address potential vulnerabilities. |
Challenges and Lessons Learned
While biometric systems offer significant security advantages, implementing them comes with its own set of challenges. Understanding these challenges and learning from past experiences are crucial for successful implementation.
- Data Privacy and Security:
- Accuracy and Reliability:
- Cost and Scalability:
- Ethical Considerations:
Protecting biometric data is paramount. Robust encryption, access controls, and secure storage protocols are essential. Regular audits and security assessments are vital to identify and mitigate potential vulnerabilities. Data breaches can severely damage reputation and result in legal repercussions.
Biometric systems are not foolproof. Factors like environmental conditions (lighting, temperature), user characteristics (fingerprints may change over time), and the quality of the biometric data can impact accuracy. Robust error detection and mitigation mechanisms are necessary.
Implementing biometric systems can be expensive, particularly in large-scale deployments. Careful planning and cost-benefit analysis are essential. The technology should be scalable to accommodate future growth.
The use of biometrics raises ethical concerns regarding data privacy and potential biases in the algorithms. Transparent data policies and algorithmic audits are crucial.
Ultimate Conclusion
In conclusion, biometrics: a security makeover presents a compelling alternative to traditional security methods. While promising enhanced security and user experience, it’s essential to acknowledge the potential privacy concerns and the need for robust security protocols. As biometric technologies continue to evolve, understanding their implications and challenges is paramount for responsible implementation and maximizing their benefits. The future of security is undeniably intertwined with biometrics, and this discussion highlights the path forward.