Biometrics Its All About You
Biometrics its all about you – Biometrics: It’s All About You. From the subtle fingerprint scan on your phone to the sophisticated facial recognition systems in public spaces, biometrics are rapidly changing how we interact with the world. This blog post dives deep into the fascinating world of biometrics, exploring its applications, security concerns, and ethical implications. We’ll look at everything from the fundamental principles to future trends, and highlight how biometrics are impacting our daily lives in both big and small ways.
This exploration will examine the technologies behind biometric systems, such as fingerprint scanning, facial recognition, and iris scanning, and compare their strengths and weaknesses. We’ll also delve into the everyday applications of biometrics in various industries, and discuss how they enhance security and convenience. Furthermore, we’ll analyze the security and privacy implications, including potential data breaches and the importance of data protection.
Ethical considerations, potential biases, and the societal impact of biometrics will also be explored.
Introduction to Biometrics
Biometrics is the science and technology of measuring and analyzing unique biological characteristics for identification, authentication, and access control. It leverages unique physical or behavioral traits to verify a person’s identity, replacing or supplementing traditional methods like passwords or PINs. This technology has become increasingly prevalent in various sectors, from security to personal devices, due to its potential for high accuracy and enhanced security.The fundamental principles behind biometrics are rooted in the uniqueness and permanence of human biological traits.
Biometrics, it’s all about uniquely identifying you. Recent security recommendations from the NCSP task force, like those detailed in ncsp task force makes security recommendations , highlight the importance of robust authentication methods. Ultimately, this underscores the crucial role of biometrics in safeguarding our personal information in a world increasingly reliant on digital interactions.
Each individual possesses a unique combination of characteristics, making biometrics a strong candidate for reliable identification. This uniqueness and consistency across time, within certain limitations and acceptable variations, form the basis for biometric systems to operate effectively.
Biometric Technologies
Different types of biometric technologies utilize various human traits. These traits range from physical characteristics like fingerprints, facial features, and iris patterns to behavioral characteristics such as voice patterns and gait. Understanding the strengths and weaknesses of each technology is crucial for selecting the most appropriate method for a given application.
- Fingerprint Recognition: This method utilizes the unique patterns of ridges and valleys on a person’s fingertips. It is a widely used biometric technique, known for its high accuracy and relative ease of implementation. The unique patterns of ridges and valleys in the skin of a person’s finger are scanned to form a digital representation of the fingerprint.
This representation is then compared with a stored template for verification.
- Facial Recognition: Facial recognition systems analyze facial features to identify individuals. This method has advanced significantly in recent years, achieving high accuracy rates in controlled environments. It involves analyzing various facial landmarks and patterns, such as the distance between eyes, the shape of the nose, and the contour of the jawline. Images are processed to extract numerical data that represents the unique facial features of the person.
- Iris Scanning: Iris scanning analyzes the unique patterns of the colored part of the eye, the iris. This technique is highly accurate and robust, often used in high-security applications. The iris is scanned to capture its detailed patterns, creating a unique template. This template is then compared with stored templates for authentication.
- Voice Recognition: Voice recognition systems analyze unique vocal characteristics, such as tone, pitch, and cadence. It is frequently used in applications requiring hands-free access control. It can be used in situations where visual identification is not possible, such as in phone calls or when a person is in a restricted area.
- Gait Recognition: Gait recognition analyzes the unique patterns of a person’s walking style. This method can be used in surveillance or access control applications where a person’s walking patterns can be captured from a distance. Gait is analyzed to identify a unique characteristic in the way a person walks.
Comparison of Biometric Methods
| Biometric Method | Strengths | Weaknesses |
|---|---|---|
| Fingerprint Recognition | High accuracy, relatively low cost, widely available technology | Potential for spoofing with artificial fingerprints, susceptible to damage or injuries to the finger |
| Facial Recognition | Non-intrusive, user-friendly, suitable for large-scale identification | Susceptible to variations in lighting, pose, and expression, potential for misidentification in crowded environments |
| Iris Scanning | High accuracy, difficult to spoof, robust against environmental factors | Requires specialized equipment, potential for discomfort during scanning |
| Voice Recognition | Hands-free operation, convenient for voice-activated devices | Accuracy can be affected by background noise, variations in speaking style |
| Gait Recognition | Can be performed from a distance, unobtrusive | Accuracy is affected by clothing, environmental conditions, and variations in walking patterns |
Biometrics in Everyday Life
Biometrics, the science of identifying individuals based on their unique biological characteristics, is rapidly transforming how we interact with technology and each other. Beyond the realm of high-security environments, biometrics are increasingly woven into the fabric of our daily routines, enhancing convenience and security in various aspects of life. This evolution marks a significant shift in how we authenticate ourselves and access services.The pervasive nature of biometrics is a testament to its ability to streamline processes and improve security.
From unlocking smartphones to accessing financial accounts, the integration of biometrics is no longer a futuristic concept but a tangible reality shaping our present. This seamless integration is driven by the growing demand for efficient and secure authentication methods.
Common Applications in Everyday Scenarios
Biometric authentication is becoming increasingly prevalent in our daily lives. Smartphone unlocking with fingerprint or facial recognition, for instance, is now commonplace. Similarly, access control systems in buildings and businesses utilize biometric identification methods to enhance security and limit unauthorized entry.
Increasing Use in Various Industries
The adoption of biometrics extends far beyond individual devices and personal security. Industries like finance, healthcare, and transportation are increasingly leveraging biometric technologies for a multitude of purposes. The integration of biometrics in these sectors is driven by the need for heightened security and efficiency in transaction processing, patient identification, and passenger verification, respectively.
Enhancing Security and Convenience
Biometric authentication methods offer a significant enhancement to security protocols. By relying on unique biological traits, biometrics reduce the risk of fraudulent access and provide a robust defense against unauthorized access attempts. Simultaneously, the convenience factor is undeniably improved. Biometric systems streamline processes, reducing wait times and simplifying interactions with various services. For example, automated teller machines (ATMs) employing fingerprint scanning eliminate the need for PINs, adding a layer of convenience.
Biometrics, it’s all about uniquely identifying you, isn’t it? Microsoft is looking ahead, predicting the future of search with innovative approaches. Microsoft predicts the future of search by focusing on more natural language processing and user intent. This ties into biometrics, as personal data and authentication methods are crucial for a secure and personalized search experience.
Biometric Applications Across Sectors
| Sector | Application | Enhancement |
|---|---|---|
| Banking | Fingerprint authentication for online banking, facial recognition for ATM access | Enhanced security against fraud, increased convenience |
| Healthcare | Fingerprint identification for patient records, iris scanning for secure access to medical information | Improved patient privacy and security, streamlined patient identification |
| Transportation | Facial recognition for boarding flights or trains, fingerprint scanning for security clearances | Enhanced security at transportation hubs, efficient passenger verification |
| Retail | Fingerprint or facial recognition for loyalty programs, automated checkout | Improved customer experience, streamlined checkout processes |
Security and Privacy Concerns
Biometric systems, while offering convenience and enhanced security, present unique challenges related to security and privacy. The reliance on unique biological traits raises concerns about data breaches, misuse, and potential for discrimination. Understanding these vulnerabilities and implementing robust safeguards are crucial for responsible deployment and societal acceptance of biometric technologies.
Security Implications of Biometric Systems
Biometric systems, designed to authenticate individuals, are susceptible to various security threats. These systems can be compromised through unauthorized access to databases containing biometric data, manipulation of biometric sensors, or sophisticated spoofing techniques. The consequences of a successful attack can range from identity theft to unauthorized access to sensitive information or physical locations.
Risks Associated with Biometric Data Breaches
A breach of biometric data can have severe consequences. Compromised fingerprints, facial recognition templates, or other biometric identifiers can be used for fraudulent activities, such as impersonating individuals for financial gain or accessing restricted areas. The potential for identity theft and the difficulty in restoring one’s identity once compromised underscores the critical need for robust data protection measures.
Importance of Data Protection in Biometric Systems
Data protection is paramount in biometric systems. Implementing strong encryption techniques, access controls, and secure storage protocols is essential to safeguard biometric data from unauthorized access or modification. Regular security audits and compliance with relevant regulations are critical to ensure the integrity and confidentiality of the collected data. Robust data governance policies should be established to ensure responsible handling and usage of biometric data.
Examples of Biometric Security Measures
Various organizations employ biometric security measures in diverse environments. Financial institutions use fingerprint scanners for transaction authentication, airports utilize facial recognition for passenger screening, and government agencies employ iris recognition for access control. These examples highlight the growing integration of biometric technologies into everyday life and the increasing need for secure and ethical implementation.
Potential Security Threats and Mitigation Strategies
| Security Threat | Mitigation Strategy |
|---|---|
| Unauthorized Access to Databases | Implement strong access controls, multi-factor authentication, and encryption for data at rest and in transit. Regular security audits and penetration testing are vital. |
| Sensor Manipulation | Use robust sensor design, anti-spoofing techniques, and real-time verification methods. Regularly update sensor firmware to patch vulnerabilities. |
| Biometric Spoofing | Employ sophisticated anti-spoofing techniques that can detect attempts to create fake biometric data, such as using 3D printed replicas or photos. |
| Data Breaches | Develop and implement comprehensive incident response plans to quickly contain and recover from security breaches. Regular data backups are essential. |
| Insufficient Data Anonymization | Implement robust data anonymization procedures to protect individual privacy. Data should be de-identified whenever possible. |
Ethical Considerations
Biometric technologies, while offering numerous benefits, raise complex ethical concerns that must be carefully addressed. The pervasive use of these technologies demands a thorough examination of potential harms and benefits, ensuring responsible development and deployment. Balancing the security advantages with the potential for misuse and discrimination is crucial for the ethical implementation of biometric systems.The societal impact of biometrics extends beyond individual convenience to encompass broader community dynamics.
Understanding how these technologies affect different groups and individuals is essential to avoid exacerbating existing inequalities and fostering a more equitable society. This requires a nuanced approach that considers the diverse needs and perspectives within various communities.
Ethical Dilemmas Surrounding Biometric Technologies
Biometric technologies face numerous ethical dilemmas stemming from the potential for misuse and the inherent trade-offs between security and privacy. These technologies can be vulnerable to manipulation, leading to unauthorized access or identification. Ensuring robust security measures and appropriate safeguards against malicious use is paramount. The collection, storage, and usage of biometric data must be subject to strict regulations and ethical guidelines.
Societal Impact of Biometrics on Individuals and Communities
Biometric technologies can profoundly affect individuals and communities. The widespread adoption of biometric systems may lead to increased surveillance and potential erosion of privacy. It’s important to acknowledge the potential for discriminatory outcomes, particularly in communities already facing systemic disadvantages. Strategies to mitigate these risks and ensure equitable access to biometric services are vital.
Potential Biases in Biometric Systems and Their Impact
Biometric systems are susceptible to biases present in the data used to train and develop them. For example, if training data primarily reflects one demographic group, the system may perform poorly on individuals from other groups. This can lead to inaccurate identifications and potentially discriminatory outcomes. Addressing bias in biometric systems requires careful consideration of the data used for training and ongoing monitoring to detect and mitigate biases.
Potential Discrimination Risks Associated with Biometric Applications
The potential for discrimination is a significant concern in biometric applications. Inadequate safeguards and biased data can lead to discriminatory outcomes, particularly against marginalized communities. Examples of this could include differential treatment in access to services or employment based on inaccurate or biased biometric assessments. Robust policies and procedures must be developed to minimize the risk of discrimination.
Comparison of Ethical Concerns and Potential Benefits of Biometrics
| Ethical Concerns | Potential Benefits of Biometrics |
|---|---|
| Privacy violations due to data collection and storage | Enhanced security and improved authentication |
| Potential for discrimination and bias in systems | Improved efficiency and automation in various processes |
| Lack of transparency and accountability in use | Reduced fraud and crime rates through improved identification |
| Erosion of trust in institutions due to misuse | Improved access to services and opportunities |
| Potential for misuse and surveillance | Increased security and safety in public spaces |
Future Trends in Biometrics: Biometrics Its All About You
Biometrics, once a futuristic concept, is rapidly becoming integrated into our daily lives. From unlocking smartphones to securing sensitive data, biometric systems are evolving at an astonishing pace. This evolution is driven by advancements in technology and the increasing demand for secure and convenient authentication methods. The future of biometrics promises even more seamless and personalized interactions.The future of biometrics is not merely about improving existing systems; it’s about merging biometric technologies with other cutting-edge fields.
This integration will lead to innovative applications and reshape how we interact with the world around us. This exploration delves into these future trends, highlighting the potential applications and the challenges that accompany them.
Advancements in Biometric Data Analysis
Biometric data analysis is undergoing a significant transformation, driven by the increasing availability of large datasets and the development of sophisticated algorithms. Machine learning techniques are playing a crucial role in improving the accuracy and efficiency of biometric systems. These advancements allow for the development of more sophisticated models, enabling faster identification and more reliable verification. This improved analysis is essential for reducing errors and enhancing the overall security of biometric systems.
The ability to analyze vast amounts of data quickly and accurately is critical for applications like law enforcement and national security.
Integration of Biometrics with Other Technologies
The integration of biometrics with other technologies is a key trend shaping the future. For example, the fusion of biometrics with artificial intelligence (AI) allows for the development of more sophisticated and adaptable systems. AI can analyze biometric data in real-time, making identification and verification processes faster and more efficient. Similarly, the integration with the Internet of Things (IoT) can create smart environments that adapt to individual users’ needs, enhancing security and convenience.
Smart homes, for example, can use biometric authentication to control access to appliances and systems.
Biometrics in Shaping Future Interactions
Biometrics is poised to significantly alter how we interact with the digital and physical world. Imagine a world where biometric authentication is seamlessly integrated into everyday transactions, from paying for groceries to accessing secure facilities. This seamless integration will lead to a more efficient and personalized experience. Imagine using your fingerprint to log into your computer, your face to access your bank account, or your voice to make purchases.
These types of experiences are becoming more and more common.
Potential Future Applications of Biometrics
| Application Area | Description | Example |
|---|---|---|
| Financial Transactions | Secure authentication for online banking, payments, and investments. | Using facial recognition to verify identity during online transactions. |
| Access Control | Automated and secure access to physical and digital spaces. | Using iris scanning to gain entry to secure buildings or sensitive areas. |
| Healthcare | Improved patient identification, personalized treatment plans, and enhanced security of medical records. | Using fingerprints to authenticate patient identity during medical procedures. |
| Law Enforcement | Enhanced crime investigation, identification of suspects, and improved security in public spaces. | Using facial recognition to identify suspects in surveillance footage. |
| Smart Cities | Efficient and secure management of urban services and resources. | Using biometric data to manage traffic flow, access public transportation, or control parking. |
Illustrative Examples of Biometric Applications
Biometrics, the science of measuring and analyzing unique biological characteristics, is rapidly transforming various sectors. From enhancing security in public spaces to streamlining healthcare processes, biometric technologies are proving their worth. This section delves into practical applications, illustrating how biometrics is being used and its impact on our daily lives.
Hypothetical Scenario: Biometrics Enhancing Public Space Security
Imagine a bustling city center. Pedestrians navigate busy streets, while security personnel monitor potential threats. A new biometric system is implemented, utilizing facial recognition and gait analysis. This system subtly tracks individuals’ movements and identifies known criminals or individuals of interest. The system alerts security personnel in real-time, allowing for immediate intervention and preventing potential harm.
The system also provides anonymous statistical data on crowd flow patterns and potential safety concerns. This proactive approach enhances security without imposing a sense of surveillance on the public.
Case Study: Biometrics in Healthcare Efficiency
In a large hospital, patient identification and record retrieval are streamlined by integrating a fingerprint-based biometric system. Patients can now quickly and accurately be identified by their unique fingerprints, reducing the risk of mix-ups and ensuring the correct medical records are accessed. This significantly reduces administrative overhead, allowing nurses and doctors more time for patient care. The system also integrates with electronic health records (EHRs), automating data entry and reducing manual errors.
This improved efficiency translates to better patient outcomes and reduced healthcare costs.
Biometric System in a Specific Industry: Manufacturing, Biometrics its all about you
A manufacturing plant employs a biometric time-attendance system based on iris scanning. This technology accurately records employee arrival and departure times, eliminating the need for manual timekeeping and reducing labor disputes. The system also tracks employee access to restricted areas, safeguarding sensitive equipment and intellectual property. The system generates detailed reports on employee productivity and work patterns, enabling the company to optimize workflow and resource allocation.
This implementation enhances security and provides valuable data for improving operational efficiency.
Biometrics – it’s all about uniquely identifying you, right down to your fingerprint or facial features. But what if your digital life gets scrambled? Thankfully, tools like backontrack eases pain of computer crashes can help recover lost files and data, keeping your digital identity safe. Ultimately, biometrics is still a crucial aspect of ensuring your personal information remains yours alone.
Unique and Innovative Biometric Application: Remote Access Control
A new biometric system for remote access control utilizes voice recognition and behavioral biometrics. The system analyzes individual speech patterns and typing styles for authentication. By combining these modalities, the system enhances security and mitigates the risk of unauthorized access to sensitive information. This innovative approach offers a more secure and convenient method of verifying identities, especially in remote work environments.
Diverse Biometric Application Scenarios
| Application Area | Description |
|---|---|
| Public Safety | Facial recognition in public spaces, identifying individuals of interest, enhancing crowd management, improving security in high-traffic areas. |
| Healthcare | Patient identification and record retrieval, streamlining administrative tasks, reducing medical errors, improving patient care. |
| Manufacturing | Automated time-keeping, access control to restricted areas, tracking employee productivity, improving operational efficiency. |
| Finance | Fraud detection, secure online transactions, verifying customer identities, enhancing financial security. |
| Retail | Customer identification for loyalty programs, personalized shopping experiences, reducing theft and fraud. |
Methods for Data Collection and Processing
Biometric data collection and processing are crucial components of any biometric system. Accurate data acquisition is paramount for reliable authentication, while efficient processing and storage are vital for scalability and security. Robust methods ensure the integrity and confidentiality of sensitive biometric information.The procedures for collecting and processing biometric data must be meticulously planned and executed to guarantee accuracy and prevent errors.
Strict adherence to these procedures is critical for the reliability of biometric systems.
Biometric Data Collection Procedures
Biometric data collection procedures involve a range of methods depending on the specific biometric trait being measured. These procedures aim to standardize the process, minimize errors, and ensure data quality. Accurate data collection is essential for reliable authentication.
- Fingerprint Scanning: This involves using specialized scanners to capture the unique patterns of ridges and valleys on a fingertip. High-quality images are crucial for accurate matching, requiring consistent finger placement and pressure on the scanner. Careful calibration of the scanner is necessary to minimize errors and ensure consistent image quality.
- Facial Recognition: Facial recognition systems utilize cameras to capture facial images. Factors such as lighting conditions, facial expressions, and angles need to be carefully controlled during data collection to maintain accuracy. Sophisticated algorithms are often used to process facial images and extract relevant features for identification.
- Iris Scanning: Iris scanning involves capturing detailed images of the unique patterns in the iris of the eye. This method is highly accurate and often used in high-security applications. The process typically involves positioning the eye correctly in front of the scanner to ensure clear and complete images.
Biometric Data Processing and Storage Methods
Efficient processing and storage are critical for managing large volumes of biometric data. These methods must be secure to protect sensitive information.
- Data Normalization: Biometric data often needs to be normalized or standardized before it can be used for comparison. Normalization techniques ensure that data from different sources or collected at different times are comparable, minimizing discrepancies in data quality. For example, facial images from different angles need to be aligned before comparison.
- Data Encryption: Encryption plays a critical role in securing biometric data during storage and transmission. Strong encryption algorithms are used to protect the data from unauthorized access. This is a fundamental step in data security.
- Data Compression: Data compression techniques can significantly reduce the storage space required for biometric data. Lossless compression methods are often preferred to maintain the integrity of the data.
- Database Management: Robust database management systems are used to organize and manage biometric data. These systems ensure efficient retrieval and access to the data when needed. Data integrity is critical to prevent errors or manipulation.
Importance of Data Encryption in Biometric Systems
Data encryption is a fundamental security measure for protecting biometric data.
Data encryption safeguards sensitive biometric information from unauthorized access, ensuring confidentiality and preventing potential misuse. Strong encryption algorithms are essential to mitigate the risks associated with data breaches. In practice, encryption protects the data in transit and at rest.
Data Security Protocols in Biometric Data Management
Implementing strong data security protocols is essential for protecting biometric data. This includes access control, data integrity checks, and regular security audits. Strict adherence to these protocols minimizes the risks associated with data breaches and unauthorized access.
- Access Control: Access to biometric data should be restricted to authorized personnel. Strong passwords, multi-factor authentication, and role-based access control are examples of effective access control measures. This is a critical component of data security.
- Data Integrity Checks: Regular checks are necessary to ensure the integrity of the biometric data. This includes verifying data accuracy and detecting any unauthorized modifications. This is crucial to maintaining data trustworthiness.
- Regular Security Audits: Security audits help identify vulnerabilities and weaknesses in the system. These audits should be performed regularly to ensure the system remains secure. This proactive approach is essential for maintaining a strong security posture.
Authentication Using Biometric Data
Biometric data is used for authentication by comparing the collected data with the stored data. If a match is found, access is granted. This process relies on the accuracy and integrity of the biometric data.
- Matching Algorithms: Sophisticated algorithms are used to compare the collected biometric data with the stored data. These algorithms determine the similarity or difference between the two sets of data. This process is critical to determine if the user is authorized.
- Thresholds: Authentication systems often use thresholds to determine if a match is sufficient for granting access. These thresholds balance security with usability. High thresholds increase security but might also result in false rejections.
- Verification vs. Identification: Verification confirms that a person is who they claim to be, while identification determines who a person is. Biometric systems can be used for both verification and identification. Different methods are employed for each task.
Historical Context and Evolution
Biometric technologies, once the stuff of science fiction, are now woven into the fabric of our daily lives. From unlocking smartphones to securing national borders, biometrics have rapidly evolved from rudimentary identification methods to sophisticated security systems. Understanding this evolution provides crucial context for appreciating the technology’s current capabilities and potential future applications.The earliest forms of biometric identification relied on observable physical characteristics, such as fingerprints.
Early efforts to systematize these methods laid the groundwork for the sophisticated systems we use today. This historical journey reveals the crucial technological advancements that spurred biometric progress.
Early Forms of Biometric Identification
The concept of using unique physical traits for identification has roots stretching back centuries. Ancient civilizations, for instance, used fingerprints for documentation purposes. These early practices, though rudimentary compared to modern techniques, marked a crucial step towards the development of systematic identification methods. These early forms of biometric identification focused on physical attributes, often relying on manual processes and limited technological support.
Key Milestones in Biometric Development
Significant advancements in the 20th century propelled biometric technology forward. These advancements were driven by the growing need for secure identification methods. The development of reliable and affordable sensors played a key role. Early digital image processing techniques also enabled the analysis of biometric data.
- 1960s-1970s: The development of automated fingerprint identification systems (AFIS) represented a pivotal moment. These systems, initially deployed in law enforcement agencies, automated the comparison of fingerprints, significantly improving efficiency and accuracy over manual methods. This was a major breakthrough in automating the identification process.
- 1980s-1990s: The advent of advanced image processing techniques allowed for the analysis of more complex biometric traits, such as facial recognition. This period saw increased research and development in iris and voice recognition. These advancements expanded the range of biometric applications.
- 2000s-Present: The rise of mobile computing and the Internet brought biometric technologies to a wider audience. Smartphone integration, for instance, made fingerprint and facial recognition readily available for everyday use. Cloud-based systems enabled the storage and analysis of vast amounts of biometric data. The ongoing development of more accurate and robust algorithms continues to improve the efficiency and security of biometric systems.
Technological Advancements Driving Biometric Progress
Technological advancements in various fields have fueled the evolution of biometric technologies.
- Computing Power: Increased computing power has enabled the development of more sophisticated algorithms for processing and analyzing biometric data. The ability to perform complex calculations rapidly is crucial for real-time identification and verification.
- Sensor Technology: Improvements in sensor technology have led to more accurate and reliable data collection. Miniaturization and affordability of sensors have made biometric systems more accessible. More sensitive and precise sensors translate to improved accuracy in biometric recognition.
- Data Analysis Techniques: Advanced data analysis techniques, including machine learning and artificial intelligence, allow for the development of more accurate and robust biometric algorithms. These algorithms can identify subtle patterns in biometric data, enabling more reliable identification.
Timeline of Biometric Evolution
| Year | Event |
|---|---|
| 1880s | Fingerprinting first used for identification. |
| 1960s | Automated fingerprint identification systems (AFIS) developed. |
| 1990s | Facial recognition technology advances. |
| 2000s | Biometrics integrated into smartphones and other devices. |
| Present | AI and machine learning enhance biometric accuracy and application. |
Wrap-Up
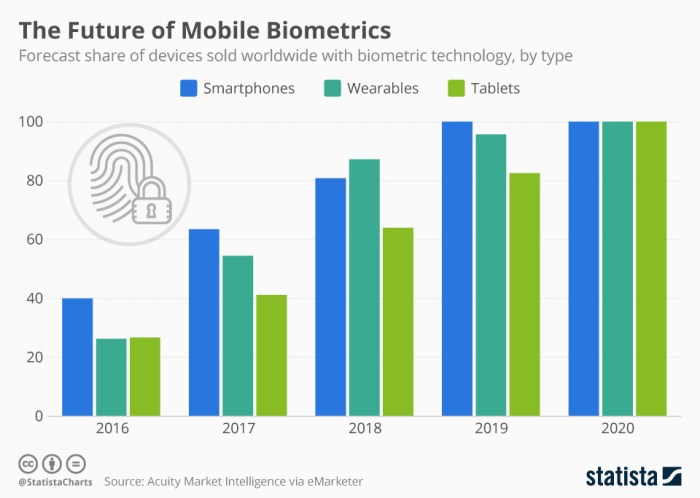
In conclusion, biometrics is a powerful technology with the potential to revolutionize many aspects of our lives. While offering enhanced security and convenience, it’s crucial to address the security and privacy concerns, and carefully consider the ethical implications. From its historical context to future trends, biometrics is a fascinating field constantly evolving, and understanding its nuances is critical to navigating this rapidly changing landscape.
We’ve explored the potential for biometrics to shape our future interactions and how data collection and processing methods are key to ensuring security and trust.