Cybersecurity
-

One Hacker Sentenced, Another Indicted A Cybercrime Case Study
One hacker sentenced another indicted sets the stage for this enthralling narrative, offering readers a glimpse into a story that…
Read More » -

Spyware the Next Spam A Growing Threat
Spyware the next spam, a silent menace lurking in the digital shadows, is evolving at an alarming rate. It’s not…
Read More » -
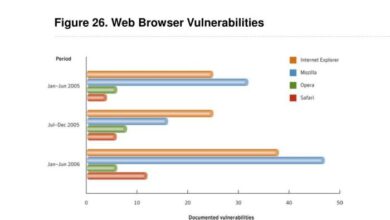
Browser-Based Attacks on the Rise A Growing Threat
Browser based attacks on the rise – Browser-based attacks on the rise are becoming a significant concern for users and…
Read More » -

NCSP Task Force Security Recommendations Unveiled
NCSP task force makes security recommendations, outlining crucial steps to bolster digital defenses. This report delves into the rationale behind…
Read More » -

Cybersecurity Must Be Priority A Crucial Imperative
Cybersecurity must be priority, a critical concern for individuals, businesses, and nations alike. From the ever-evolving landscape of cyber threats,…
Read More » -
Five Zombies Do All the Worlds Phishing
Five zombies do all the worlds phishing – Five zombies do all the world’s phishing. Imagine a world where malicious…
Read More » -
Virus Outbreak Filters New Tool to Block Infections
Virus outbreak filters new tool to block infections are rapidly becoming a critical component of modern cybersecurity. These sophisticated systems…
Read More » -

New Software Vaccinates Against Zero-Day Virus Attacks
New software vaccinates against zero day virus attacks – New software vaccinates against zero-day virus attacks, offering a powerful proactive…
Read More » -
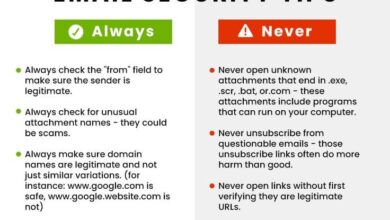
Ten Steps to Email Security A Comprehensive Guide
Ten steps to e mail security – Ten steps to email security is your essential guide to navigating the complex…
Read More » -

Microsoft Warns of JPEG Security Hole
Microsoft warns of jpeg security hole – Microsoft warns of a JPEG security hole, potentially impacting various systems and applications.…
Read More »

