Cybersecurity
-

Phishing Email Fraud An Epidemic
Phishing e mail fraud becoming epidemic – Phishing email fraud becoming epidemic is a growing threat, rapidly impacting individuals and…
Read More » -

Author of Sasser, Netsky Worms Indicted
Author of sasser netsky worms indicted – Author of Sasser, Netsky worms indicted, marking a significant step in combating cybercrime.…
Read More » -

Convergence Quagmire Viruses & Spam
Convergence quagmire viruses with spam is a growing threat in the digital landscape. Malicious actors are increasingly combining viral and…
Read More » -

Brador Trojan Targets Pocket PCs
Brador Trojan targets Microsoft Pocket PC handhelds, highlighting a fascinating chapter in the history of mobile security threats. This piece…
Read More » -

Brador Industry-First PDA Trojan
Industry first trojan horse malware called brador hits pdas sets the stage for this in-depth look at a significant threat.…
Read More » -
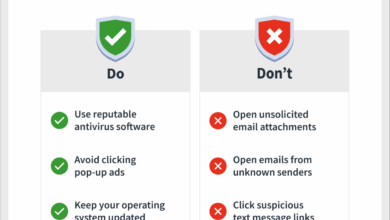
Solutions to Spyware Plague Enterprise Users
Solutions to spyware plague come to enterprise users, offering a crucial defense against the ever-evolving threat landscape. This comprehensive guide…
Read More » -

Managed Security Services Email Attack Defense
Managed security services a hedge against e mail attacks – Managed security services a hedge against email attacks. These services…
Read More » -

Sasser Worm New Security Strategies
Sasser worm prompts new security strategies, forcing a critical look at vulnerabilities and the need for proactive measures. The worm’s…
Read More » -

New Worm Starts Crawling the Net A Deep Dive
New worm starts crawling the net, raising serious concerns about network security. This in-depth exploration examines the nature of this…
Read More » -

Windows Attack Code Surfaces Foretells Worm
Windows attack code surfaces foretells worm, a new and potentially devastating threat to Windows systems. This exposed code reveals a…
Read More »

