Closing Up Wireless Security Holes A Deep Dive
Closing up wireless security holes is crucial in today’s interconnected world. This deep dive explores the vulnerabilities lurking in our wireless networks, from identifying the weaknesses to implementing robust security protocols. We’ll uncover the methods for assessing your network, patching security holes, and staying ahead of emerging threats.
From understanding common attack vectors to implementing advanced security techniques like intrusion detection systems, we’ll cover it all. We’ll also examine real-world case studies to highlight the importance of proactive security measures and how to prevent future breaches. This comprehensive guide equips you with the knowledge to build a secure wireless network.
Identifying Vulnerabilities
Wireless networks, while convenient, are susceptible to various security breaches. Understanding these vulnerabilities is crucial for implementing robust security measures and protecting sensitive data. Knowing the common attack vectors and the potential impact allows for proactive defense strategies. This section delves into the multifaceted landscape of wireless security vulnerabilities.Wireless networks, despite their convenience, often face security challenges due to their inherent nature.
Patching up those pesky wireless security holes is crucial. Recent recommendations from the ncsp task force makes security recommendations provide a solid framework for addressing these vulnerabilities, offering practical solutions for tightening security protocols. Ultimately, these steps help ensure our wireless networks stay protected and resilient against threats.
They rely on radio waves, making them susceptible to interception and manipulation. This makes a deep understanding of common weaknesses essential for safeguarding network integrity.
Common Wireless Security Vulnerabilities
Wireless networks are vulnerable to a variety of attacks, stemming from weaknesses in various aspects of their design and implementation. Understanding these vulnerabilities is paramount to developing robust security protocols.
- Weak or Default Passwords: Many wireless networks use default passwords or easily guessed passwords. Attackers can exploit these weak credentials to gain unauthorized access. This is often due to a lack of proactive password management by users.
- Insufficient Encryption: Outdated or weak encryption protocols (like WEP) are easily cracked, allowing attackers to eavesdrop on network traffic and potentially compromise sensitive data. Modern encryption protocols like WPA2/3 are much more secure, but even they can be vulnerable if not properly configured.
- Misconfigured Access Points: Incorrectly configured access points can leave the network open to attacks. Vulnerable configurations may allow unauthorized devices to connect or expose sensitive data to external entities.
- Rogue Access Points: Malicious actors can place unauthorized access points near legitimate networks. This can lure users into connecting to the rogue network, giving the attacker access to their devices and data.
- MAC Address Spoofing: Attackers can forge their MAC address to bypass network access restrictions. This can allow them to connect to the network without authentication, posing a significant threat.
- Man-in-the-Middle Attacks: Attackers can intercept and manipulate communication between a client and an access point, potentially stealing sensitive information. This often involves the attacker impersonating a legitimate entity to gain trust.
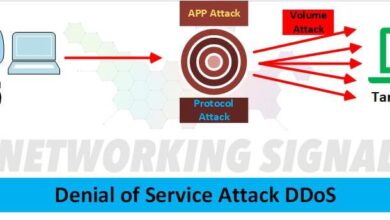
- Denial-of-Service (DoS) Attacks: Attackers can flood the wireless network with traffic, disrupting service for legitimate users. This can be particularly effective in situations where the network is not properly defended against such attacks.
Attack Vectors and Impact
Understanding the specific methods attackers use to exploit these vulnerabilities is crucial. This knowledge allows for a tailored defense strategy against these vectors.
- Exploiting Default Passwords: Attackers can use readily available lists of default passwords or employ automated tools to try various combinations. The impact is unauthorized access to the network, allowing the attacker to potentially steal data or disrupt services.
- Cracking Weak Encryption: Vulnerable encryption protocols, like WEP, are easily cracked using readily available tools. The impact can range from eavesdropping on sensitive data to gaining full control of the network.
- Exploiting Misconfigurations: Attackers can exploit misconfigurations in the access point settings to gain unauthorized access or perform denial-of-service attacks. The impact is varied, from unauthorized access to complete disruption of network services.
Vulnerability Severity Comparison
The severity of a vulnerability depends on various factors, including the ease of exploitation and the potential impact on network security.
| Vulnerability | Category | Impact | Severity |
|---|---|---|---|
| Weak Passwords | Authentication | Unauthorized access, data breaches | High |
| Outdated Encryption | Encryption | Data interception, network compromise | High |
| Misconfigured Access Point | Configuration | Unauthorized access, denial-of-service | Medium |
| Rogue Access Points | Configuration | Unauthorized access, data breaches | High |
| MAC Spoofing | Authentication | Unauthorized access | Medium |
| Man-in-the-Middle | Encryption | Data interception, session hijacking | Critical |
| Denial-of-Service | General | Network disruption, service outage | Medium to High |
Assessing Wireless Networks: Closing Up Wireless Security Holes
Wireless networks, while offering convenience, are susceptible to various vulnerabilities. Understanding how to assess these networks for weaknesses is crucial for maintaining security and preventing unauthorized access. This involves identifying potential threats, performing scans to pinpoint vulnerabilities, and analyzing network traffic to detect malicious activity. Thorough assessment allows for proactive security measures to be implemented, strengthening the overall security posture.
Methods for Identifying Vulnerabilities in a Wireless Network
Identifying vulnerabilities in a wireless network requires a multi-faceted approach. This includes employing various tools and techniques to probe the network for weaknesses. A systematic approach involves actively testing network configurations, examining the security protocols in place, and analyzing the network traffic for unusual patterns. This proactive approach is essential to identify vulnerabilities before they can be exploited.
Performing a Vulnerability Scan on a Wireless Network
A vulnerability scan is a crucial step in assessing wireless networks. It systematically examines the network infrastructure for potential security weaknesses. This process involves using specialized software to identify vulnerabilities in the network’s hardware, software, and configurations. This scan will highlight areas requiring immediate attention, helping to improve the overall security posture. It’s important to note that a vulnerability scan does not necessarily exploit the found vulnerabilities, but it provides a comprehensive inventory of potential risks.
Step-by-Step Procedure for Analyzing Wireless Network Traffic
Analyzing wireless network traffic is a critical part of assessing vulnerabilities. This involves capturing and examining the data packets flowing through the network. A step-by-step procedure includes: 1) capturing network traffic using a tool like Wireshark; 2) filtering the captured traffic to isolate relevant data; 3) analyzing the filtered traffic for unusual patterns or malicious activity, like unauthorized access attempts or data breaches; 4) identifying potential vulnerabilities based on the analysis; and 5) documenting findings and recommendations for remediation.
Common Tools Used for Wireless Network Assessments
Several tools are commonly used for assessing wireless networks. These tools provide a range of features, from scanning for vulnerabilities to analyzing network traffic. Each tool has its strengths and weaknesses, and the best choice depends on the specific needs of the assessment. Selecting the appropriate tools is essential for effective vulnerability identification.
Table Comparing Different Vulnerability Scanning Tools
| Tool | Features | Pros | Cons |
|---|---|---|---|
| Wireshark | Packet capture and analysis, protocol decoding, filtering, and statistical analysis | Open-source, versatile, supports various protocols, detailed analysis | Steep learning curve, can be overwhelming for beginners, requires manual analysis |
| Aircrack-ng | Wireless network cracking, WEP/WPA/WPA2 cracking | Open-source, effective for testing wireless security protocols, can reveal weak passwords | Can be used for malicious activities, requires technical expertise, may not be suitable for all scenarios |
| Kismet | Wireless network discovery, analysis, and vulnerability assessment | Open-source, detects hidden networks, identifies potential vulnerabilities, provides detailed reports | Can be complex to use, may require a strong understanding of wireless networking |
| Nessus | Comprehensive vulnerability scanner, identifies security flaws across various systems and protocols | Wide range of checks, comprehensive results, detailed reports, often used in enterprise environments | Commercial software, license fees may be involved, may have a larger footprint |
Mitigating Security Holes
Closing wireless security vulnerabilities requires a multi-faceted approach. Simply identifying and assessing weaknesses is only the first step. Effective mitigation strategies involve proactive patching, robust protocol implementation, and meticulous encryption reinforcement. This process ensures a secure wireless network environment, safeguarding sensitive data and preventing unauthorized access.Wireless networks, though convenient, are susceptible to various attacks if not properly secured.
Implementing robust security measures is crucial to prevent data breaches, maintain network integrity, and protect user privacy. This involves understanding the different security protocols, their strengths, and weaknesses, and choosing the appropriate solutions for the specific needs of the network.
Patching Wireless Security Holes
Addressing security vulnerabilities in wireless networks requires a proactive and systematic approach. Regularly checking for updates and applying patches to the operating systems and firmware of wireless devices, including routers and access points, is paramount. This helps to close known security gaps and prevents attackers from exploiting vulnerabilities.
Implementing Robust Security Protocols
Implementing strong security protocols is critical for protecting wireless networks. This involves using protocols that provide authentication and encryption to ensure that only authorized users can access the network and that data transmitted over the network remains confidential. Protocols such as WPA3 and WPA2 offer different levels of security and are designed to address vulnerabilities present in previous protocols.
Strengthening Wireless Network Encryption
Robust encryption is essential to protect the confidentiality and integrity of data transmitted over a wireless network. Using strong encryption algorithms, such as AES (Advanced Encryption Standard), and employing up-to-date encryption protocols, like WPA3, is crucial. The level of encryption should match the sensitivity of the data being transmitted. For instance, confidential financial transactions should be protected by higher-grade encryption than general internet browsing.
Securing Wireless Access Points
Securing wireless access points (WAPs) is a critical aspect of overall network security. Restricting access to the WAP, employing strong passwords, and disabling unnecessary features are all important steps. Regularly changing passwords and implementing access controls based on user roles are crucial for preventing unauthorized access. Also, consider implementing network segmentation to limit the potential impact of a breach.
Security Protocols and Their Characteristics
| Protocol | Strength | Weakness | Use Cases |
|---|---|---|---|
| WPA3 | Stronger encryption (compared to WPA2), enhanced security features against known vulnerabilities. | Can be more complex to implement than older protocols. | Modern networks, especially those handling sensitive data. |
| WPA2 | Widely deployed and relatively easy to implement. | Vulnerable to some attacks (e.g., KRACK), less secure than WPA3. | Older networks where migrating to WPA3 is not feasible. |
| WEP (Wired Equivalent Privacy) | Simple to set up. | Highly vulnerable to cracking; should not be used. | Not recommended for modern networks due to security risks. |
Implementing Security Measures
Securing your wireless network involves more than just setting up a password. A robust security strategy requires careful configuration of your access points, strong authentication methods, and consistent maintenance. This section details best practices for each step, ensuring a strong and resilient wireless network.Implementing appropriate security measures is crucial to protect your network from unauthorized access. By proactively addressing potential vulnerabilities, you can safeguard sensitive data and prevent disruptions to your network operations.
Configuring Wireless Access Points for Enhanced Security
Wireless access points (WAPs) are the gateways to your wireless network. Proper configuration is paramount for security. This involves selecting strong encryption protocols, disabling unnecessary services, and utilizing robust firewall settings.Implementing strong encryption protocols, like WPA3, is essential to protect your network. These protocols use advanced cryptographic algorithms to encrypt data transmitted over the wireless connection, making it virtually impossible for unauthorized users to intercept or decipher it.
Disable any unnecessary services or features on your WAP that aren’t required for your network. This reduces the attack surface and limits potential points of entry. Utilize robust firewall settings to filter network traffic and block unauthorized connections.
Implementing Strong Passwords and Authentication
Strong passwords and robust authentication mechanisms are critical for protecting your network. Weak passwords are easily cracked, leaving your network vulnerable to intruders.Creating strong passwords is a crucial step. Use a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable words or phrases. Employ multi-factor authentication (MFA) whenever possible.
MFA adds an extra layer of security by requiring users to provide multiple verification methods, such as a code from a mobile device, to access the network.
Recommended Security Configurations for Different Wireless Devices
Different wireless devices have varying security requirements. A standardized approach across your network ensures a consistent level of protection.
- Routers: Employ WPA3 encryption, enable strong password policies, and utilize a firewall. Configure MAC address filtering to restrict access to only authorized devices.
- Smart Home Devices: Regularly update firmware for these devices to patch vulnerabilities. Implement strong passwords and consider enabling MFA where available. Utilize network segmentation if possible.
- Laptops and Desktops: Enable encryption for any stored data on the device and ensure the operating system and software are up-to-date. Use strong passwords and MFA for remote access.
The security configuration should adapt to the device’s sensitivity and the data it handles. Routers, as the network’s central hub, need the strongest protection, whereas smart home devices, while potentially less sensitive, can still pose a threat if compromised.
Importance of Regular Security Updates and Maintenance
Regular security updates and maintenance are vital for maintaining network security. Hackers constantly develop new methods to exploit vulnerabilities, making it crucial to stay ahead of these threats.Software vulnerabilities are common targets for hackers. Keeping software updated mitigates these risks. Regularly checking for and installing updates for your wireless devices, operating systems, and applications is crucial. This ensures that you have the latest security patches to protect against known vulnerabilities.
Regularly review and update your wireless network policy to address evolving threats.
Creating a Secure Wireless Network Policy
A well-defined wireless network policy Artikels security procedures and expectations. This policy should be accessible and understood by all users.A comprehensive network policy should clearly Artikel acceptable use guidelines, password policies, and data security protocols. It should specify the consequences of violating these policies. Regularly review and update the policy to reflect changes in the threat landscape.
This ensures a consistent and effective approach to security.
A robust wireless network policy is a critical component of a comprehensive security strategy.
Staying Current with Threats
Staying ahead of evolving wireless security threats is crucial for maintaining a robust network. The landscape of cyberattacks is constantly shifting, with new vulnerabilities and attack vectors emerging regularly. Ignoring these developments leaves organizations susceptible to significant security breaches. This section details strategies for staying informed and proactive in the face of these dynamic threats.
Patching up those pesky wireless security holes is crucial, especially as the internet continues to expand. The recent VeriSign report highlights domain growth, which, while positive, also underscores the growing need for robust security measures. This increased digital footprint demands that we prioritize closing up wireless security holes to protect our networks and sensitive data. VeriSign’s report highlights domain growth clearly demonstrates the importance of staying ahead of the curve in cybersecurity.
Emerging Wireless Security Threats, Closing up wireless security holes
The wireless landscape is evolving rapidly, with new threats constantly emerging. Attackers are increasingly leveraging sophisticated techniques to exploit vulnerabilities in Wi-Fi protocols, IoT devices, and other wireless technologies. These threats include but are not limited to:
- Man-in-the-Middle (MitM) Attacks: Attackers intercept communication between devices, potentially stealing sensitive data or manipulating traffic.
- Rogue Access Points: Unauthorized access points can be set up to capture data or gain unauthorized access to a network.
- Weak Encryption Protocols: Older or poorly configured encryption protocols can be exploited to gain access to network traffic.
- Exploiting IoT Devices: Many IoT devices have weak security, making them easy targets for attackers who can use them to gain access to the network.
- Denial-of-Service (DoS) Attacks: These attacks overwhelm the network, disrupting services and access.
Staying Updated on Security Advisories and Patches
Regularly checking for and implementing security updates is essential. Security advisories and patches address vulnerabilities that attackers might exploit.
- Automated Patch Management Systems: These systems automatically identify and install security updates, minimizing manual intervention and the risk of delays.
- Subscription to Security Newsletters: Following industry security advisories through newsletters and alerts helps keep abreast of newly discovered vulnerabilities.
- Active Monitoring of Security Forums: Participating in security forums and communities allows you to learn about emerging threats and vulnerabilities directly from the experts.
Importance of Ongoing Security Training
Security awareness training empowers employees to recognize and report potential threats. It also helps mitigate the human factor in security breaches.
- Regular Training Sessions: Conduct regular training sessions to educate employees about the latest threats and best practices.
- Phishing Simulations: Simulating phishing attacks helps employees recognize and avoid malicious emails or websites.
- Security Best Practices Training: Training should cover password management, device security, and recognizing suspicious activity.
Resources for Staying Informed
Various resources provide information on emerging threats and vulnerabilities. Staying informed about new threats is critical for proactive security measures.
Patching up those wireless security holes is crucial, especially considering the recent surge in attacks like the “worm takes toll microsoft attack set” worm takes toll microsoft attack set. This highlights the urgent need to fortify our defenses. Staying ahead of these evolving threats requires constant vigilance and proactive measures in closing up those wireless security vulnerabilities.
- Security News Aggregators: Following reputable security news sources provides updates on new vulnerabilities and attack methods.
- Industry Security Blogs and Publications: Many security experts publish blogs and articles that provide insights into current threats and mitigation strategies.
- Vulnerability Databases: Databases like the National Vulnerability Database (NVD) provide comprehensive information on known vulnerabilities.
Establishing a Threat Intelligence Program
A threat intelligence program provides a structured approach to understanding and responding to evolving threats.
- Define Scope and Objectives: Establish clear goals and boundaries for the program.
- Establish a Centralized Data Repository: Collect and store information from various sources.
- Develop a Dissemination Strategy: Establish protocols for sharing threat intelligence with relevant teams.
- Establish a Feedback Loop: Include processes for evaluating the effectiveness of the program.
Case Studies and Examples

Real-world wireless security breaches are unfortunately common, often resulting in significant financial and reputational damage. Understanding these incidents, the strategies used to mitigate them, and the lessons learned is crucial for proactively bolstering network security. Analyzing past breaches provides invaluable insights into vulnerabilities and allows for the development of more robust security measures.By examining successful strategies employed in various scenarios, we can gain practical knowledge for closing security holes in our own networks.
This involves not only identifying vulnerabilities but also understanding the impact of a breach and the proactive steps that can be taken to prevent similar incidents. This section will present specific examples and detailed analysis of breaches, highlighting the security measures implemented and those that could have been taken to prevent them.
Real-World Wireless Security Breach Example: The Coffee Shop Attack
The recent rise in remote work has led to an increase in public Wi-Fi usage. Many individuals connect to open wireless networks in coffee shops or other public spaces, often without proper security measures. A targeted attack on a coffee shop’s wireless network can compromise the security of numerous users simultaneously.
Vulnerability Analysis: The Weak Access Point
A common vulnerability in public wireless networks is the use of weak or default passwords for the access point. Attackers can exploit this by using readily available tools to scan for vulnerable access points. This allows them to gain unauthorized access and potentially gain control over the entire network.
Mitigation Strategy: Implementing WPA3 and Strong Passwords
To prevent such breaches, the coffee shop owner should implement WPA3 security protocols on their wireless network. WPA3 significantly enhances security compared to older protocols like WPA2, making it harder for attackers to gain access. Implementing a robust password policy, using strong, unique passwords for the access point and regular network security audits is also critical.
Security Measures Implemented Post-Breach
After the breach, the coffee shop owner implemented WPA3, changed all passwords to strong, unique ones, and conducted regular security audits. They also educated staff on security best practices.
Preventive Security Measures
To prevent a similar breach, the coffee shop should have proactively implemented WPA3 and used strong passwords. Regular vulnerability assessments and security awareness training for staff are also crucial. They should have considered network segmentation to limit the impact of a potential breach. Using a VPN for sensitive data transmission and implementing robust firewall rules to protect against external threats are further proactive measures.
Analysis of Past Breaches: Identifying Common Patterns
Past breaches reveal recurring patterns in wireless network vulnerabilities. These include the use of default passwords, inadequate security protocols, and a lack of proactive security measures. A thorough analysis of these breaches enables us to identify common patterns and implement preventive strategies. This involves detailed examination of the attack vectors, the impact of the breach, and the security measures taken.
This is an iterative process, as new threats and vulnerabilities emerge constantly.
Conclusion
Analyzing real-world examples and the subsequent mitigation strategies provide a practical understanding of securing wireless networks. By understanding common vulnerabilities and implementing robust security measures, organizations can significantly reduce the risk of future breaches.
Advanced Security Techniques
Fortifying wireless networks against sophisticated threats requires a multi-layered approach beyond basic security measures. Advanced techniques, like intrusion detection systems and firewalls, offer a crucial second line of defense. Implementing these strategies can significantly enhance the overall security posture of a wireless network, mitigating risks and ensuring data integrity.Wireless security is an ongoing process. Staying ahead of evolving threats necessitates a proactive stance.
Advanced techniques, while not a replacement for fundamental security, offer an additional layer of protection, significantly improving the overall robustness of the network. These methods can identify and respond to threats that basic security measures might miss.
Intrusion Detection Systems (IDS) and Firewalls
Intrusion Detection Systems (IDS) monitor network traffic for malicious activity, while firewalls act as gatekeepers, controlling incoming and outgoing data. A well-configured IDS can detect unauthorized access attempts, suspicious patterns, and other security breaches. Firewalls, on the other hand, filter traffic based on predefined rules, preventing malicious traffic from entering the network and protecting it from external attacks.
Wireless Security Gateways
Wireless security gateways act as a central point of control for managing wireless network access. They often incorporate multiple security features, including authentication, authorization, and encryption, into a single device. This centralized approach simplifies management and enhances security. Gateways can be configured to monitor network activity, block unauthorized devices, and enforce security policies.
VPN Use for Secure Wireless Connections
Virtual Private Networks (VPNs) create an encrypted tunnel over the internet, protecting wireless connections from eavesdropping. By encrypting all data transmitted over the wireless network, VPNs create a secure channel, shielding sensitive information from potential attackers. VPNs can be particularly beneficial for users accessing the network remotely.
MAC Filtering and Access Control
MAC filtering is a method of restricting access to a wireless network based on the Media Access Control (MAC) address of a device. This approach allows only authorized devices with specific MAC addresses to connect. This method provides a basic level of access control, but it’s not foolproof and is less effective against sophisticated attacks. More comprehensive access control mechanisms may include authentication methods that require a username and password.
Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring more than one form of verification to access a network. This approach combines something you know (password), something you have (token), or something you are (biometric data). This approach makes it significantly harder for attackers to gain access even if they manage to compromise one form of authentication.
Ultimate Conclusion
In conclusion, securing your wireless network requires a multifaceted approach. This exploration of vulnerabilities, assessments, mitigation strategies, and advanced techniques provides a strong foundation for building a robust wireless infrastructure. By understanding the threats, implementing appropriate security measures, and staying informed about emerging risks, you can effectively close up wireless security holes and protect your network from potential breaches.
Regular updates and proactive security measures are paramount in maintaining a secure network.