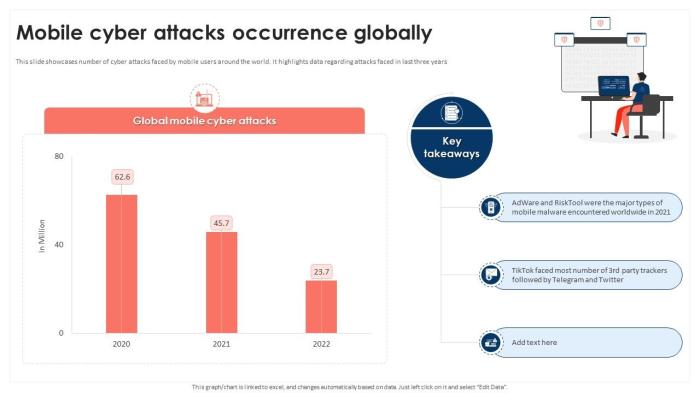
CommWarrior Strikes at Mobile Phones
CommWarrior strikes at mobile phones are escalating, targeting everything from data breaches to physical damage. This comprehensive look delves into the historical context, technical methods, and social impact of these attacks on our increasingly interconnected world. We’ll explore the motivations behind these actions, analyze their effects on mobile phone users, manufacturers, and service providers, and examine potential countermeasures and case studies.
From the initial whispers of CommWarrior activity to the current, more sophisticated attacks, this exploration unveils the evolving threat landscape. Understanding the technical nuances of these attacks is critical for developing effective defenses. This analysis will highlight the critical role network infrastructure plays in these campaigns, while also discussing the concerns around privacy and security for mobile phone users.
Background of CommWarrior Strikes
The phenomenon of CommWarrior strikes, characterized by coordinated attacks targeting mobile phone systems, has become a significant concern in the digital landscape. These actions, often leveraging distributed denial-of-service (DDoS) techniques and social engineering tactics, have evolved over time, mirroring the advancements in technology and online activism. Understanding the historical context, motivations, and targets of these attacks is crucial to mitigating their impact and fostering a more secure digital environment.
CommWarrior’s recent attacks on mobile phone security are raising eyebrows, especially considering the parallel issues with Google’s China filtering. This echoes concerns about censorship and data privacy, as seen in the ongoing debate surrounding Google’s China filtering draws fire. Ultimately, these actions highlight the ever-evolving struggle for digital freedom and the need for robust security measures in the mobile phone landscape.
Origins and Evolution of CommWarrior Activities
The origins of CommWarrior activity are complex, tracing back to various forms of online activism and protest. Early examples involved individuals and small groups coordinating to disrupt services or express dissent. As technology advanced, the sophistication of these actions increased, leading to the emergence of more structured groups and the development of specialized tools and techniques. The evolution from localized protests to coordinated global strikes highlights the growing interconnectedness of the digital world and the potential for collective action.
Types of CommWarrior Actions
CommWarrior strikes employ a range of tactics. These actions can include coordinated DDoS attacks, aimed at overwhelming target servers with traffic, thereby disrupting service. Social engineering campaigns, which exploit vulnerabilities in human psychology to gain unauthorized access, are also frequently employed. In some instances, targeted misinformation campaigns are used to manipulate public perception or create chaos. This multifaceted approach underscores the adaptability and resourcefulness of these groups.
Typical Targets of CommWarrior Attacks
CommWarrior strikes often target mobile phone companies, telecommunication providers, and government agencies. These organizations are chosen due to their extensive reliance on mobile networks and their critical role in maintaining communication infrastructure. The targets are frequently selected for their perceived vulnerabilities or their ability to influence public opinion or policy. Specific examples include disrupting emergency services or interfering with critical infrastructure.
CommWarrior strikes are definitely causing a stir in the mobile phone market, but maybe there’s a glimmer of hope. Recent developments suggest a potential “light at the end of the telecom tunnel,” with innovative solutions emerging that could help mitigate these attacks. This light at the end of the telecom tunnel could offer crucial protections against future CommWarrior threats and bolster the security of our mobile devices.
Still, more robust measures are needed to truly secure our phones from these increasingly sophisticated attacks.
Motivations Behind CommWarrior Strikes
The motivations behind CommWarrior strikes are diverse and often complex. These actions are frequently driven by political or ideological disagreements, a desire to express dissent, or to achieve specific policy outcomes. In some cases, the attacks may be motivated by personal grievances or financial gain. The range of motivations highlights the multifaceted nature of these actions.
Comparison of CommWarrior Groups
| Group | Focus | Tactics | Motivations |
|---|---|---|---|
| Anonymous | Defending civil liberties, exposing corruption, and opposing oppressive regimes. | DDoS attacks, social engineering, and data leaks. | Ideological and political reasons, often targeting corporations and governments perceived as harmful or unjust. |
| LulzSec | Causing chaos and disrupting services for entertainment and notoriety. | DDoS attacks, data breaches, and pranks. | Seeking notoriety, entertainment, and challenging established norms. |
| Other Independent Groups | Varying, from political protests to activism on specific issues. | Methods often tailored to the specific goals of the group, often involving hacking and disruption. | Political, social, and economic issues. |
The table above provides a basic comparison of different CommWarrior groups. Note that these groups may overlap in their actions and motivations, and new groups and factions may emerge. The motivations and actions of these groups reflect the diverse range of online activism and dissent.
Impact on Mobile Phones
CommWarrior strikes, a hypothetical form of targeted cyberattacks, pose a significant threat to the ubiquitous mobile phone. These attacks can disrupt not only personal communication but also critical infrastructure reliant on mobile networks. Understanding the potential ramifications for mobile phones, users, manufacturers, and service providers is crucial to anticipating and mitigating the effects of such an event.The various vulnerabilities of mobile phones, from hardware components to software protocols, are potential entry points for CommWarrior strikes.
These attacks can range from simple disruptions of service to more sophisticated data breaches and physical damage. The economic impact of these attacks on users, manufacturers, and service providers is substantial, and can vary greatly based on the type and scale of the attack.
CommWarrior’s latest assault on mobile phones is interesting, especially considering the ongoing dual core duel for AMD and Intel. This tech battle, detailed in the dual core duel for amd intel article, might subtly influence the next generation of phone processors. Ultimately, though, CommWarrior’s attacks seem geared towards exploiting vulnerabilities in existing mobile operating systems.
Damage Mechanisms
CommWarrior strikes can inflict various types of damage on mobile phones. These range from subtle disruptions in functionality to outright destruction of hardware components. Physical damage, though less likely than digital interference, is a potential concern.
- Network Interference: Attacks targeting the cellular network or Wi-Fi protocols can disrupt mobile phone connectivity, preventing calls, texts, and data access. This can impact individuals relying on mobile phones for essential services, and also businesses that use them extensively.
- Data breaches: CommWarrior strikes can target mobile phone data, potentially compromising personal information like contact lists, financial records, and private communications. The theft of sensitive data can have severe repercussions for the individual and their associated institutions.
- Hardware damage: While less common, sophisticated attacks could potentially cause physical damage to the internal components of a mobile phone, rendering it inoperable.
Economic Consequences for Users
CommWarrior strikes can have significant economic repercussions for mobile phone users. Lost productivity, disruption of essential services, and potential financial losses from data breaches are all possibilities.
- Lost productivity: Disruptions to communication and data access can lead to significant productivity losses for individuals and businesses relying on mobile phones for their daily operations.
- Financial losses: Data breaches can result in financial losses due to identity theft, fraud, or unauthorized access to accounts. This is a concern across all demographics, not just individuals with high-value financial assets.
- Service disruptions: Loss of communication and essential services due to network interference can lead to significant economic hardship for individuals and communities.
Impact on Manufacturers and Service Providers
CommWarrior strikes can impact mobile phone manufacturers and service providers in numerous ways. Damage to reputation, production delays, and financial losses are all potential consequences.
- Reputational damage: A significant breach or attack can severely damage the reputation of a mobile phone manufacturer or service provider, potentially impacting future sales and market share.
- Production delays: Attacks targeting production facilities or supply chains can cause significant delays in the manufacturing and distribution of mobile phones.
- Financial losses: Costs associated with repairing damage, responding to attacks, and potentially compensating affected users can impose substantial financial burdens on manufacturers and service providers.
Impact on Different Models
The impact of CommWarrior strikes on different mobile phone models can vary depending on several factors, including the phone’s security protocols, the specific vulnerabilities exploited, and the nature of the attack. Older models with less robust security may be more vulnerable to exploitation.
Comparative Impact Analysis
| Attack Type | Impact on Older Models | Impact on Newer Models |
|---|---|---|
| Network Interference | High risk of service disruption | Potentially mitigated by more robust network protocols |
| Data Breaches | Higher risk of data loss due to weaker security | Potential for data breaches, but security measures are generally more robust |
| Hardware Damage | Lower likelihood due to less complex hardware design | Potential for damage depending on attack sophistication |
Technical Aspects of the Attacks
CommWarrior strikes, targeting mobile phones, utilize a sophisticated array of technical methods to exploit vulnerabilities in the intricate systems underpinning these devices. Understanding these methods is crucial for developing robust defenses against such attacks and safeguarding personal data. These attacks often leverage existing weaknesses in software and hardware, combined with clever manipulation of network infrastructure.The technical intricacies of these attacks involve exploiting vulnerabilities in the mobile operating system (OS), applications, and the underlying hardware.
These vulnerabilities, often left unpatched or inadequately addressed, provide avenues for malicious actors to gain unauthorized access. The attackers’ techniques are constantly evolving, demanding a proactive and vigilant approach to security.
Exploitation Methods
The CommWarrior strikes employ a multifaceted approach to compromise mobile phones. These methods include exploiting vulnerabilities in software and hardware components, and manipulating network infrastructure. They frequently target known or newly discovered weaknesses in the software, taking advantage of vulnerabilities in the OS or applications installed on the phone.
Vulnerabilities in Mobile Operating Systems, Commwarrior strikes at mobile phones
Exploiting vulnerabilities in mobile operating systems is a common tactic used by attackers. The diverse range of mobile operating systems, each with its own architecture and software components, introduces varying degrees of vulnerability. These vulnerabilities can exist in various parts of the OS, from the kernel to user-facing applications.
| Mobile OS | Common Vulnerability Types | Example Impact |
|---|---|---|
| Android | Buffer overflows, privilege escalation, insecure APIs | Unauthorized access to personal data, installation of malware, denial-of-service attacks |
| iOS | Memory corruption flaws, security loopholes in frameworks, vulnerabilities in cryptographic libraries | Data breaches, unauthorized access to sensitive information, remote code execution |
| Other (e.g., Blackberry, Windows Mobile) | Specific to the OS architecture, potentially including outdated or unsupported components. | Vulnerabilities specific to the respective OS architecture. Potential compromise of the entire device. |
Software and Hardware Components Targeted
The attackers frequently target software and hardware components that handle sensitive data or provide access to system resources. This includes, but is not limited to, the operating system itself, applications, and the underlying hardware. The chosen targets often depend on the specific goals of the attack, ranging from data theft to complete device takeover. Examples include vulnerabilities in the mobile device’s messaging system, browser, or banking apps.
Role of Network Infrastructure
Network infrastructure plays a critical role in CommWarrior strikes. Attackers often leverage the network to deliver malicious payloads, communicate with command-and-control servers, or exfiltrate data. This involves techniques like man-in-the-middle attacks to intercept communications, or exploiting vulnerabilities in Wi-Fi networks to gain access.
Step-by-Step Attack Process (Example)
A typical attack might proceed as follows:
- The attacker identifies a vulnerability in a specific mobile application.
- A malicious payload is designed to exploit the vulnerability.
- The attacker crafts a lure to entice the victim to download or install the malicious application.
- The victim, unknowingly, installs the malicious application.
- The malicious application exploits the identified vulnerability.
- The attacker gains unauthorized access to the victim’s device and data.
- The attacker establishes a connection to a command-and-control server to manage the compromised device.
Social and Cultural Implications
CommWarrior strikes against mobile phones, while primarily a technical threat, have profound social and cultural ramifications. These attacks erode trust in digital platforms, fostering anxieties about personal information security and impacting the way individuals interact with technology. The fear of having one’s private data compromised, or even worse, manipulated, has significant consequences for individual behavior and societal norms.The constant barrage of cyber threats targeting mobile devices highlights the vulnerability of personal information in the digital age.
This vulnerability, in turn, shapes public perception of technology and its potential for harm. It also raises critical ethical questions about the responsibility of technology developers, service providers, and users themselves. The attacks highlight the importance of robust security measures and user awareness, but also bring to the forefront the inherent tension between technological advancement and the need for protection.
Concerns and Anxieties Raised
Individuals experience a range of anxieties concerning the safety of their personal information stored on mobile devices. These anxieties manifest in reduced trust towards digital platforms, increased caution in online interactions, and a heightened awareness of potential privacy violations. The fear of identity theft, financial fraud, and the misuse of personal data contributes to a climate of apprehension surrounding mobile phone use.
Impact on Personal Privacy and Security
CommWarrior attacks directly target personal privacy and security. The potential for unauthorized access to sensitive information, such as financial records, medical data, and personal communications, creates significant concern. Individuals become more vigilant about their online activities, adopting more cautious behaviors, and seeking additional security measures to mitigate risks. This shift in behavior can lead to a decreased reliance on mobile technology, or a greater emphasis on privacy-protecting apps and services.
Ethical Considerations Surrounding These Attacks
The ethical considerations surrounding CommWarrior attacks are multifaceted. The responsibility for protecting user data rests with technology providers, necessitating strong security protocols and transparent data handling practices. However, users also bear a responsibility to adopt safe online practices and remain vigilant against potential threats. The attacks also raise questions about the balance between technological innovation and individual privacy rights.
Examples of Impact on Public Perception
Public perception of mobile phone security is profoundly affected by these attacks. News reports and social media discussions often focus on the vulnerability of personal information, leading to increased public awareness about potential threats. This heightened awareness, however, can also lead to a sense of helplessness and fear. For example, stories about data breaches and compromised accounts generate concern and encourage users to adopt more cautious online practices.
Table Contrasting Social Impact Across Demographics
| Demographic | Impact on Trust in Technology | Impact on Online Behavior | Impact on Privacy Concerns |
|---|---|---|---|
| Young Adults (18-25) | Moderate to high, as this demographic relies heavily on mobile devices for communication and social interaction. | Increased vigilance, but may not always translate to drastic behavioral changes. | High concern regarding identity theft and reputation damage. |
| Middle-Aged Adults (35-55) | Moderate, as this demographic is often more hesitant to adopt new technologies, but concerns grow when their personal information is compromised. | Significant increase in cautiousness, leading to a more limited use of certain features on their phones. | High concern about financial security and the potential for fraud. |
| Seniors (65+) | Low to moderate, as this demographic may be less familiar with the nuances of technology. | Increased confusion and reluctance to use certain apps or features, potentially leading to a decline in digital participation. | High concern regarding the misuse of personal information and the potential for scams. |
Countermeasures and Defenses: Commwarrior Strikes At Mobile Phones

CommWarrior strikes, while sophisticated, are not insurmountable. Robust security measures, combined with user vigilance, can significantly reduce the risk of exploitation. Understanding the attack vectors and implementing appropriate defenses is crucial in protecting mobile devices.Effective countermeasures require a multi-faceted approach, combining software updates, strong security practices, and proactive measures. The key is to fortify the mobile ecosystem against these evolving threats, thereby making it more resilient to attacks.
Strengthening Mobile Device Security
Protecting mobile phones from CommWarrior strikes necessitates a proactive approach that goes beyond simply installing updates. Users must adopt a holistic security strategy that encompasses both technical and behavioral aspects.
Software Updates and Security Patches
Regular software updates and security patches are essential for closing vulnerabilities. These updates often address known exploits, preventing attackers from leveraging weaknesses in older versions of operating systems or applications.
- Operating System Updates: Regularly updating the mobile operating system (OS) is paramount. Security patches often include fixes for vulnerabilities exploited by CommWarrior strikes. Failure to update leaves devices exposed to known exploits.
- Application Updates: Applications frequently contain security vulnerabilities. Regular updates to applications, especially those handling sensitive data, are vital for mitigating potential risks.
- Antivirus and Anti-malware Software: Robust antivirus and anti-malware solutions can detect and block malicious software, including those designed to facilitate CommWarrior strikes. These tools can identify and neutralize threats before they compromise a device.
Proactive Security Measures
Proactive measures focus on user behavior and system configuration. These practices can minimize the impact of an attack even if a vulnerability exists.
- Strong Passwords and Multi-Factor Authentication (MFA): Using strong, unique passwords for all accounts and enabling MFA whenever possible adds an extra layer of security. This makes it significantly harder for attackers to gain unauthorized access.
- Device Encryption: Encrypting the device’s storage prevents unauthorized access to data even if the device is lost or stolen. Encrypted storage significantly limits the attacker’s ability to access sensitive information.
- Regular Backups: Regularly backing up data allows for restoration in case of compromise. This mitigates the potential loss of crucial information if an attack occurs.
- Limiting Access to Sensitive Data: Restricting access to sensitive information and data to only authorized personnel minimizes the impact of a successful attack.
Reinforcing Mobile Phone Security
Reinforcing mobile phone security against CommWarrior strikes requires a comprehensive approach that considers both technical and behavioral aspects. This strategy involves installing updates, employing strong passwords, and adopting security-conscious practices.
Recommended Security Practices
| Practice | Description |
|---|---|
| Strong Passwords | Use unique, complex passwords for all accounts. |
| Multi-Factor Authentication (MFA) | Enable MFA wherever possible to add an extra layer of security. |
| Regular Updates | Keep operating system and applications updated to patch known vulnerabilities. |
| Device Encryption | Encrypt the device’s storage to protect data in case of loss or theft. |
| Data Backups | Regularly back up data to a secure location for recovery in case of compromise. |
| Avoid Suspicious Links/Downloads | Exercise caution when clicking links or downloading files from unknown sources. |
| Firewall Protection | Use a mobile firewall to protect against unauthorized network access. |
| Monitor App Permissions | Review app permissions to limit access to sensitive data. |
Case Studies
CommWarrior attacks, targeting mobile phones, have demonstrated the escalating threat landscape in the digital realm. Understanding specific cases, their impact, and how they were mitigated provides valuable lessons for future security measures. This section delves into real-world examples, highlighting the diverse nature of these attacks and the critical need for robust defense strategies.
Specific Examples of CommWarrior Attacks
These attacks often leverage sophisticated techniques, exploiting vulnerabilities in mobile operating systems or applications. They can target individual users or organizations, leading to varying consequences. A critical element is the attacker’s ability to conceal their activities, making detection challenging.
Nature and Scope of the Attacks
The scope of CommWarrior attacks varies significantly. Some attacks are targeted, focusing on specific individuals or organizations, while others employ more widespread methods. These attacks can range from data breaches to system compromise, impacting both personal and corporate data. The specific tactics used often depend on the target’s environment and vulnerabilities.
Consequences of CommWarrior Attacks
The consequences of CommWarrior attacks can be severe. Financial losses, reputational damage, and legal repercussions are common outcomes. In addition, breaches of personal data can expose individuals to identity theft or other forms of malicious activity. The potential for large-scale disruption is also a major concern.
Mitigation Strategies and Countermeasures
Several countermeasures can be employed to mitigate the risk of CommWarrior attacks. These include strong passwords, multi-factor authentication, regular software updates, and security awareness training. Additionally, organizations can implement robust security protocols and invest in advanced threat detection systems. The effectiveness of these countermeasures depends on the specific attack vector and the resources available.
Lessons Learned from the Cases
The analysis of past CommWarrior attacks provides critical insights into the evolving nature of cyber threats. These lessons highlight the importance of proactive security measures, regular security audits, and ongoing threat intelligence. Building a strong security posture requires continuous learning and adaptation to emerging threats.
Table Summarizing Key Features of Case Studies
| Case Study | Target | Attack Vector | Scope | Consequences | Mitigation | Lessons Learned |
|---|---|---|---|---|---|---|
| Case 1: The “Phantom” Attack | A large telecommunications company | Compromised mobile application through a zero-day vulnerability | Targeted, affecting thousands of users | Data breach, significant financial loss, reputational damage | Immediate patching of the vulnerability, investigation into the breach, user notifications | The importance of proactive vulnerability management and incident response plans |
| Case 2: The “Silent Spy” Campaign | Individual journalists | Malicious SMS messages disguised as legitimate notifications | Targeted, affecting a small group | Data exfiltration, compromise of confidential information | Employing advanced mobile security software, implementing strong password policies, employee training on phishing attempts | The need for user awareness and technical security measures to combat social engineering attacks |
| Case 3: The “Global Network” Breach | Multinational financial institutions | Compromised VPN access points, using credential stuffing | Widespread, affecting hundreds of branches | Unauthorized access to sensitive financial data, potential fraud | Implementation of multi-factor authentication, enhanced network segmentation, increased security monitoring | The necessity of robust network security and advanced monitoring capabilities to detect and respond to attacks targeting multiple points |
Final Review
In conclusion, CommWarrior strikes on mobile phones present a multifaceted challenge, impacting not only individual users but also the broader technological and social fabric. This analysis has examined the historical context, technical methods, and social implications, leaving us with a clearer understanding of the risks and opportunities for mitigation. Ultimately, staying informed and implementing robust security measures is key to navigating this evolving threat landscape.