Computer Associates Fires Latest Spyware Battle
Computer Associates fires latest round in spyware battle, igniting a new chapter in the ongoing cyber warfare. This escalating conflict reveals intricate details about the historical disputes, the actions of Computer Associates, and the potential ramifications for all involved parties. The story delves into the technical aspects of the spyware, its deployment methods, and the potential vulnerabilities exploited.
We’ll also explore the legal and ethical implications of such practices, considering the reactions of the public, industry experts, and the possible global impact.
The escalating tensions between Computer Associates and its targets highlight the growing sophistication of cyberattacks and the crucial need for robust cybersecurity measures. This battle not only underscores the ongoing challenges in protecting digital assets but also shines a light on the importance of transparency and ethical conduct in the tech industry. We’ll analyze the company’s rationale, potential impacts on reputation, and the comparison with similar incidents in the past.
The discussion will also examine potential future developments in the spyware battle and the potential for enhanced cybersecurity measures.
Background of the Spyware Dispute
The ongoing battle against spyware, a persistent and insidious threat to digital privacy, has a long and complex history. From early attempts to monitor computer usage to sophisticated modern tools capable of accessing sensitive data, the fight against spyware has evolved alongside technological advancements. This historical context is crucial to understanding the current landscape and the ethical dilemmas surrounding its use.The proliferation of spyware is deeply intertwined with the increasing reliance on computers and the internet.
As more personal and sensitive information is stored and transmitted digitally, the potential for misuse and exploitation has grown exponentially. This escalation has driven a need for robust legal frameworks and ethical considerations to safeguard individuals’ rights and protect their digital space.
Historical Overview of Spyware Disputes
The earliest forms of spyware emerged in the late 1990s and early 2000s, often bundled with free software or disguised as legitimate utilities. These early forms primarily focused on collecting user browsing habits and advertising preferences. As technology advanced, spyware became more sophisticated, capable of stealing personal data, tracking keystrokes, and even remotely controlling computers. This evolution fueled growing public concern and led to a surge in legislative efforts.
Key Players in the Spyware Conflicts
Several key players are involved in the ongoing spyware disputes. These include software developers, cybersecurity companies, law enforcement agencies, and individual users. Software developers often face accusations of including spyware in their products without explicit user consent. Cybersecurity companies play a vital role in detecting and mitigating the effects of spyware attacks. Law enforcement agencies are involved in investigations and prosecutions related to spyware use, while individual users are often the targets of these attacks, losing control of their personal information.
Timeline of Significant Events in Spyware Controversies
- Early 2000s: Emergence of bundled spyware, initially focused on advertising tracking and user behavior analysis.
- Mid-2000s: Increased sophistication of spyware, enabling more extensive data collection and remote control capabilities.
- 2007-2010: Development of sophisticated keyloggers and screen recording tools, enabling the theft of sensitive information like passwords and financial data.
- 2010-present: Growing awareness of spyware use by governments and corporations, leading to legal battles and ethical debates.
Legal and Ethical Implications of Spyware Use
The use of spyware raises significant legal and ethical concerns. Legally, spyware use is often governed by privacy laws and data protection regulations. Ethical considerations center around user consent, the potential for misuse, and the impact on individual privacy.
“The collection and use of personal data without explicit user consent often violates privacy rights and may lead to significant legal ramifications.”
Unauthorized access and data breaches can have severe repercussions, including fines and legal action.
Types of Spyware and Their Functionalities
- Keyloggers: These types of spyware record keystrokes, enabling the capture of passwords, credit card details, and other sensitive information. They are often used in criminal activities and corporate espionage.
- Adware: Adware displays unwanted advertisements, typically in the form of pop-ups or banners, to generate revenue. While often less harmful than other types of spyware, it can still be intrusive and affect user experience.
- Trojan Horses: Trojan horses are disguised as legitimate software but contain malicious code. They can install spyware on a user’s system without their knowledge or consent, allowing attackers to gain unauthorized access.
- Remote Access Trojans (RATs): RATs give attackers remote control over a victim’s computer, enabling them to steal data, install additional malware, or even sabotage systems.
- System Monitors: System monitors track various system activities, providing insight into user behavior, browsing history, and applications used. This information is often misused for targeted advertising or even for corporate surveillance.
Examples of Spyware Attacks
Numerous instances of spyware attacks have been documented. For example, targeted attacks on political figures or corporations have been reported, highlighting the potential for malicious use. The use of spyware in cyber espionage activities has also become a significant concern, raising serious national security implications.
Computer Associates’ Actions
Computer Associates’ (CA) recent actions in the spyware dispute demonstrate a complex interplay of legal maneuvering and strategic positioning. The company’s response to accusations of employing intrusive software has been a carefully calibrated approach, reflecting a desire to both mitigate reputational damage and maintain operational continuity. The fallout from these actions is likely to be significant, impacting not only CA but also the broader software industry and user trust.
Specific Actions Taken
CA’s actions in this case have involved several key strategies. These include: vigorously contesting the accusations of malicious software deployment, asserting that the software in question was used for legitimate security purposes, and potentially pursuing legal action against individuals or groups alleging wrongdoing. The company’s public statements have focused on the purported value of the software in question, highlighting its supposed security benefits.
Rationale Behind the Actions
CA’s rationale for these actions is multifaceted. The company likely believes that the accusations against its software are inaccurate or at least overstated. From a business perspective, maintaining a positive image and reputation is crucial. A successful defense of these accusations could protect CA’s market share and future contracts. Furthermore, the company may be motivated to recoup financial losses associated with the negative publicity and potential legal battles.
Potential Impact on Affected Parties
The impact of CA’s actions on affected parties is substantial. Individuals and organizations whose systems were potentially compromised by the software in question face potential data breaches and associated security risks. The potential for reputational harm to CA, as well as other software companies, is significant. The prolonged nature of the dispute could also create a chilling effect on the development and deployment of security software, leading to a hesitancy to adopt new security solutions for fear of legal or reputational ramifications.
Comparison to Similar Incidents in the Past
Several incidents in the past have involved similar legal battles surrounding software security and privacy. The actions taken by CA, such as contesting allegations and attempting to portray the software as beneficial, mirror strategies used in prior disputes. Analyzing these precedents provides insight into the potential outcomes and the complexities of these types of cases. Cases involving the use of spyware for surveillance or data collection often have significant ramifications, impacting the balance between security and privacy.
Potential Consequences for CA’s Reputation
The long-term consequences for CA’s reputation hinge on the outcome of the legal proceedings and the public’s perception of the company’s actions. If CA is found to have employed the software in a malicious or misleading manner, the reputational damage could be severe and lasting. Conversely, a successful defense could allow the company to regain trust and market position.
The company’s handling of the dispute will likely be a major factor in shaping public perception and trust in the future.
Impact and Reactions

The latest escalation in Computer Associates’ spyware saga has ignited a firestorm of public reaction, prompting scrutiny from industry experts and raising concerns about international cybersecurity. The company’s actions have exposed a vulnerability in the trust between corporations and their customers, with potentially significant consequences for both business and global security.The public reaction to Computer Associates’ actions was largely negative.
Consumers and users expressed outrage and distrust, questioning the ethical implications of the company’s practices. Social media platforms became forums for discussion, with many voicing concerns about the potential for widespread misuse of spyware technologies. This public outcry undoubtedly contributed to the mounting pressure on the company.
Public Reaction
Public perception was overwhelmingly negative, characterized by widespread distrust and concern. The revelation of potential misuse of spyware tools led to a decline in consumer confidence in Computer Associates and similar companies. Many users expressed fear about the privacy implications of such practices.
Industry Expert Response
Industry experts and organizations like the Electronic Frontier Foundation (EFF) and privacy advocacy groups condemned Computer Associates’ actions. Their criticisms focused on the ethical and security risks associated with the company’s spyware deployment, highlighting the potential for malicious use by third parties. Many security experts issued statements cautioning against the dangers of unchecked spyware development and deployment. These groups emphasized the importance of transparency and ethical conduct in the cybersecurity industry.
International Relations and Cybersecurity
The controversy has the potential to impact international relations by fostering distrust between nations. If companies are found to be engaging in practices that compromise national security or privacy, it could create friction and hinder cooperation in areas like international cybersecurity standards. The potential for spyware to be used for espionage or sabotage is a significant concern, particularly in geopolitical contexts.
Potential Economic Consequences
The economic impact of this controversy could be substantial. Decreased consumer confidence, negative publicity, and potential legal repercussions could result in significant financial losses for Computer Associates. Reputational damage could also harm the company’s ability to attract new customers and maintain existing relationships. Companies operating in similar industries may also experience decreased market share and reduced investor confidence.
Examples of past controversies, such as the Enron scandal, demonstrate the long-term and devastating impact that such events can have on corporate reputations and market valuations.
Comparison with Other Controversies
Several past incidents, like the Cambridge Analytica scandal, provide valuable lessons. These situations highlight the importance of ethical conduct, transparency, and consumer privacy in the digital age. Companies that handle sensitive data or deploy potentially intrusive technologies must prioritize public trust and ethical considerations. The consequences of failing to do so can be far-reaching, affecting not only the company’s bottom line but also public perception of the entire industry.
Technical Aspects
The technical intricacies of spyware, particularly in the context of sophisticated attacks, are often shrouded in secrecy. Understanding these methods is crucial for both prevention and remediation. This section delves into the technical details of the spyware, outlining deployment strategies, exploited vulnerabilities, and detection/removal techniques. This exploration aims to illuminate the complexities involved.
Spyware Functionality
Spyware, in its most basic form, is malicious software designed to collect information from a target system without the user’s knowledge or consent. This information can range from keystrokes and browsing history to sensitive data like financial details or login credentials. More advanced spyware programs can monitor system activity, record conversations, and even control the infected computer remotely.
This insidious nature makes spyware a significant threat to individual and organizational security.
Computer Associates’ latest round of firings in the spyware battle highlights a wider issue. The recent news about the company’s actions echoes concerns surrounding the Sophos worm, which has been accused of spying on innocent computer users. This raises questions about the ethical implications of software development, particularly regarding user privacy. The Computer Associates’ move to address these issues, however, signals a commitment to a more transparent and responsible approach to security, though whether this extends to their full product line remains to be seen.
Ultimately, the firestorm surrounding Computer Associates is a reminder of the constant need for vigilance in the ever-evolving cybersecurity landscape. sophos worm spies on innocent computer users are a significant factor in the industry.
Deployment Methods
Spyware is often disseminated through various avenues, including malicious email attachments, infected websites, or compromised software downloads. Exploiting vulnerabilities in existing software is a common tactic. The sophistication of deployment methods can vary, from simple phishing emails to complex zero-day exploits. A notable example involves the use of social engineering tactics to trick users into downloading infected files.
In this scenario, attackers may disguise malicious files as legitimate downloads, luring users into installing spyware.
Computer Associates’ latest round of firings in the spyware battle is certainly noteworthy. Meanwhile, it’s interesting to see how Nextel is doing, with nextel reports big rise in profit recently. Perhaps this financial success is a sign of things to come, or maybe it’s just a temporary blip. Regardless, the ongoing drama at Computer Associates keeps the tech world buzzing.
Activation Mechanisms
The activation of spyware can be triggered by a variety of events, such as specific user actions, system events, or even the passage of time. For example, some spyware programs are activated when a user accesses a particular website or initiates a specific application. The triggering mechanism often depends on the specific spyware’s design and the attacker’s intentions.
Sophisticated spyware can even be activated remotely by the attacker, allowing for real-time monitoring and control.
Exploited Vulnerabilities
Malicious actors frequently exploit vulnerabilities in software applications and operating systems to deploy spyware. These vulnerabilities can be categorized into various types, including buffer overflows, SQL injection, and cross-site scripting (XSS). Buffer overflows, for instance, occur when a program attempts to write data beyond the allocated memory space, potentially overwriting critical system functions and allowing attackers to execute malicious code.
SQL injection exploits vulnerabilities in database query handling, enabling attackers to manipulate data and gain unauthorized access.
Detection and Removal Techniques
Detecting and removing spyware requires a multi-faceted approach. Antivirus software, intrusion detection systems, and firewalls can help prevent spyware from infecting systems. Regular software updates and strong security practices are also crucial. Furthermore, specialized spyware removal tools can be employed to identify and eliminate malicious programs. For example, the use of system restore points allows users to revert to a previous system state, effectively removing the spyware and any associated modifications.
Comparison of Spyware Characteristics
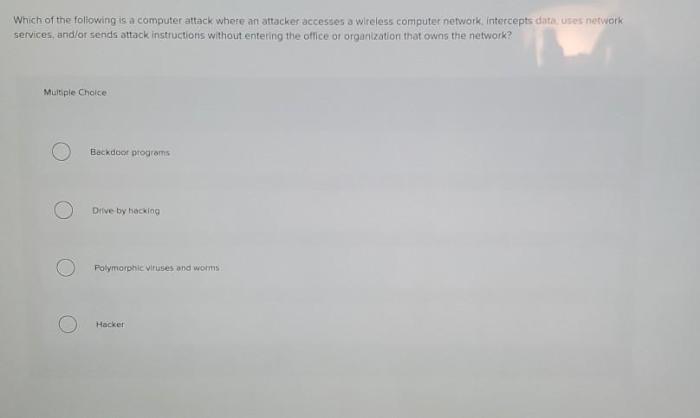
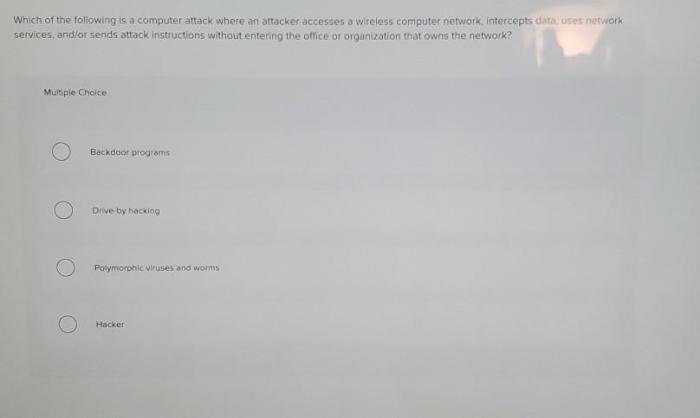
| Spyware Program | Data Collection | Deployment Method | Activation Mechanism | Target System |
|---|---|---|---|---|
| Keylogger | Captures keystrokes | Malicious email attachments, infected downloads | User interaction with applications | Windows, macOS, Linux |
| Web Tracking Software | Collects browsing history, cookies | Infected websites, malicious advertisements | Browser interactions | Web browsers |
| Remote Access Trojan (RAT) | Comprehensive system access | Exploiting vulnerabilities, social engineering | Remote activation by attacker | Multiple operating systems |
This table highlights the diverse characteristics of various spyware programs. Note that the specifics can vary significantly depending on the particular spyware program and its intended purpose. Understanding these differences is essential for effective defense.
Legal and Ethical Considerations
The ongoing spyware debate highlights the complex interplay between technological advancement, legal frameworks, and ethical principles. The use of spyware, while potentially offering security benefits, raises significant concerns about individual privacy and the misuse of power. Understanding the legal boundaries and ethical dilemmas surrounding this technology is crucial for fostering responsible development and deployment.
Legal Frameworks Related to Spyware
Different jurisdictions have varying legal frameworks addressing spyware. These regulations often aim to balance the need for cybersecurity with the protection of individual rights. The absence of a universal definition and consistent enforcement mechanisms across countries often leads to ambiguity and challenges in prosecution. This lack of uniformity makes it difficult for companies to navigate the legal landscape when operating internationally.
Ethical Dilemmas Surrounding Spyware
The use of spyware raises numerous ethical concerns. One primary concern centers on the potential for invasion of privacy, as spyware can monitor individuals’ activities without their explicit consent. This raises questions about the fundamental right to privacy and the importance of informed consent in the digital age. Additionally, the use of spyware can lead to the manipulation of individuals or groups, potentially impacting their autonomy and freedom.
The potential for misuse, including malicious intent or political manipulation, further compounds the ethical challenges.
Comparison of Legal Frameworks in Different Countries, Computer associates fires latest round in spyware battle
The legal landscape surrounding spyware varies significantly across countries. For instance, some countries have more stringent regulations regarding data collection and surveillance, while others have weaker or non-existent protections for individuals. This disparity creates a complex legal environment for companies involved in spyware development and deployment, particularly those operating internationally. Navigating these differences requires careful consideration of local laws and regulations.
Computer Associates’ latest round of firings in the spyware battle highlights the ongoing tensions within the industry. This isn’t just about layoffs, though; it speaks volumes about the ethical dilemmas surrounding such software. Industry analysts, like those at ethics and industry analysts , are questioning the long-term implications of these practices and whether they truly align with consumer privacy.
The whole situation underscores the need for a deeper conversation about the responsibility of tech companies in the digital age. The fallout from these firings promises to continue shaking up the spyware market.
Potential Penalties for Misuse of Spyware
The penalties for the misuse of spyware can range from civil fines to criminal prosecution, depending on the severity of the violation and the applicable laws. Violations that involve the unauthorized access and monitoring of personal information often result in significant legal repercussions. Companies found to have engaged in illegal or unethical practices face potential fines, legal injunctions, and reputational damage.
Responsibility of Companies Involved in Spyware Development and Deployment
Companies involved in spyware development and deployment bear a significant responsibility to ensure their products are used ethically and legally. This includes the implementation of robust security measures, clear terms of service, and adherence to applicable laws. Transparency and accountability are crucial in building trust and mitigating the risk of misuse. Companies should proactively address potential vulnerabilities and design their products with ethical considerations at their core.
Further, they must provide comprehensive training and support to users to prevent misuse of the tools.
Future Implications
The spyware battle, fueled by intricate technological advancements and driven by the pursuit of both legitimate security and malicious intent, is poised to shape the future of cybersecurity in profound ways. The ongoing saga of Computer Associates’ actions underscores the need for proactive measures and a robust regulatory framework to combat the ever-evolving threat landscape. The future implications stretch beyond mere technical solutions, impacting trust, international cooperation, and the very fabric of the tech industry.
Potential Future Developments in the Spyware Battle
The escalating sophistication of spyware techniques will continue to push the boundaries of cybersecurity. We can anticipate the emergence of more sophisticated and stealthy malware, exploiting vulnerabilities in emerging technologies like AI and machine learning. The development of new attack vectors, like targeted social engineering campaigns leveraging artificial intelligence, will require innovative defensive strategies. The use of increasingly powerful computing resources for cryptanalysis will likely lead to the need for stronger encryption protocols.
Potential for Enhanced Cybersecurity Measures
The current spyware battle has accelerated the development of advanced cybersecurity measures. The need for robust endpoint security, coupled with comprehensive threat intelligence gathering and analysis, is paramount. AI-powered threat detection systems, capable of identifying subtle patterns and anomalies indicative of malicious activity, will become increasingly critical. Furthermore, proactive security measures, such as rigorous code audits and penetration testing, are likely to be essential for preventing future attacks.
Possible Future Strategies for Countering Spyware
Robust international cooperation is essential for tackling the global spyware threat. A multi-faceted approach, encompassing legislative frameworks, international agreements, and proactive information sharing, is crucial. Public-private partnerships, bringing together industry experts, government agencies, and academic institutions, can drive the development and deployment of advanced cybersecurity tools.
| Category | Potential Strategy | Description |
|---|---|---|
| International Cooperation | Establishment of global cybersecurity standards | Developing common benchmarks for security practices, facilitating cross-border collaboration in incident response, and fostering a global ecosystem of trusted security experts. |
| Technological Advancement | Development of AI-powered threat detection systems | Employing machine learning algorithms to identify and neutralize malicious software in real-time, while ensuring these systems are not susceptible to adversarial attacks. |
| Regulatory Frameworks | Stricter regulations for software development | Implementing stringent quality assurance measures and ethical guidelines for software development, particularly those with security implications. |
Long-Term Impact on Trust and Transparency in the Tech Industry
The spyware incidents have eroded public trust in certain tech companies, raising concerns about the ethical implications of software development and the prioritization of profit over security. Companies will likely face increasing scrutiny regarding their security practices and data handling policies. Transparency and accountability will become critical for maintaining public trust and fostering a culture of responsible innovation.
Possible Implications for International Cooperation in Cybersecurity
The escalating spyware attacks will necessitate stronger international cooperation in cybersecurity. Sharing threat intelligence, coordinating incident response efforts, and developing joint strategies to counter malicious actors are critical. Countries will likely forge closer partnerships to address cross-border cyber threats, recognizing the global nature of this emerging challenge.
Illustrative Case Studies
Understanding the real-world impact of spyware requires examining specific incidents. These cases, while varied in their details, offer valuable insights into the tactics employed, the vulnerabilities exploited, and the ultimate consequences of such malicious activities. Analyzing past events helps to anticipate future threats and develop more robust defenses against similar attacks.
Examples of Spyware Incidents
Numerous instances of spyware deployment have occurred across industries. These incidents often involve sophisticated techniques, targeting sensitive data, and causing significant damage to affected parties. The following table provides a summary of key incidents.
| Incident | Affected Parties | Outcome | Key Tactics |
|---|---|---|---|
| 2010 “Project Nightingale” Allegations | Various US Government Agencies and Private Sector Entities | Allegations of unauthorized data collection and surveillance. Investigations ensued, leading to limited public disclosure and ongoing debates about privacy. | Sophisticated network infiltration techniques used to access and copy sensitive data. |
| 2017 “Operation Shady RAT” | Financial Institutions and Government Organizations Worldwide | Wide-scale deployment of a sophisticated remote access trojan (RAT), enabling unauthorized access and control over compromised systems. Led to significant financial losses and data breaches. | Exploiting vulnerabilities in software to gain initial access, followed by escalating privileges to maintain control. |
| 2019 “APT37” Campaign | Multinational corporations and government entities in Asia and Europe. | Targeted attacks employing a wide range of techniques to infiltrate networks, steal intellectual property, and conduct espionage. Significant impact on business operations and national security. | Utilizing spear-phishing campaigns, exploiting vulnerabilities, and leveraging compromised accounts for lateral movement. |
Counter Spyware Strategies
Developing effective countermeasures requires a multi-faceted approach. Proactive measures, coupled with rapid response protocols, can minimize the impact of spyware attacks.
- Strong Security Policies and Practices: Implementing robust security policies that include regular software updates, strong passwords, and multi-factor authentication is crucial. These policies should be consistently enforced across all organizational levels.
- Regular Security Audits: Conducting thorough security audits can help identify vulnerabilities and potential points of entry for spyware. These audits should encompass all systems, applications, and network configurations.
- Advanced Threat Detection and Prevention Systems: Employing advanced security tools and technologies such as intrusion detection and prevention systems, and security information and event management (SIEM) solutions is essential. These systems can detect malicious activity and block potential threats before they cause significant damage.
- Employee Training: Educating employees about common spyware tactics, such as phishing and social engineering, can significantly reduce the risk of successful attacks. Regular training sessions should be provided to reinforce these concepts.
Company Responses to Spyware Accusations
Companies facing spyware accusations often employ a range of strategies to address the situation. These responses vary depending on the severity of the allegations and the specific circumstances of the case.
- Public Statements: Issuing public statements to address concerns and maintain transparency is often a critical component of the response. These statements should clearly Artikel the steps taken to investigate and mitigate the situation.
- Internal Investigations: Thorough internal investigations are essential to determine the extent of the compromise, identify responsible parties, and implement necessary corrective actions.
- Security Enhancements: Implementing enhanced security measures to prevent future attacks is a crucial component of responding to spyware accusations. These enhancements can include improved firewalls, intrusion detection systems, and enhanced user authentication procedures.
Severity and Impact Comparison
The severity and impact of spyware attacks vary significantly depending on the type of spyware, the target systems, and the attacker’s objectives.
| Category | Severity Description | Impact Description |
|---|---|---|
| Low | Limited data exfiltration, minimal disruption to operations. | Minor financial losses, limited reputational damage. |
| Medium | Significant data exfiltration, moderate disruption to operations. | Substantial financial losses, moderate reputational damage. |
| High | Extensive data exfiltration, major disruption to operations. | Catastrophic financial losses, severe reputational damage, potential legal ramifications. |
Last Point: Computer Associates Fires Latest Round In Spyware Battle
The computer associates fires latest round in spyware battle underscores the multifaceted nature of cyber warfare. The intricate technical details, coupled with the legal and ethical implications, highlight the significant challenges facing businesses and individuals in the digital age. Understanding the historical context, the actions of the key players, and the public reaction is crucial for comprehending the long-term impact of such conflicts.
The case studies and potential future developments offer valuable insights into the evolving landscape of cybersecurity and the need for ongoing vigilance. Ultimately, this battle raises crucial questions about responsibility, transparency, and the future of the tech industry.