Critical IE Flaws Bug Reporting Debate
Critical IE flaws invoke debate on bug reporting, highlighting the complexities of identifying and addressing severe software issues. This discussion delves into defining critical flaws, examining their impact on software systems, and exploring the controversies surrounding bug reporting practices. Different perspectives on prioritization, classification, and communication will be examined, along with methods for improvement and tools for effective management.
Understanding the varying severity levels of bug reports, from minor to critical, is crucial. Critical flaws pose significant risks, impacting user experience, security, and system stability. Analyzing past failures and examining the factors that contribute to a bug being considered critical are essential for developing robust bug reporting procedures.
Defining Critical Flaws in Bug Reporting
A critical flaw in a bug report signifies a severe issue that can have a profound impact on the functionality and stability of a software application. Identifying and addressing these critical flaws is paramount to ensuring a positive user experience and preventing potential system failures. This section will delve into the specifics of what constitutes a critical flaw, distinguishing it from other severity levels, and highlighting crucial elements for effective reporting.Critical flaws represent significant problems that can lead to substantial disruptions in a software application’s intended operation.
They are fundamentally different from minor or major bugs, as they pose a substantial risk to the application’s overall integrity and user experience. Understanding the criteria for a critical flaw is essential for both developers and testers to prioritize and address these issues effectively.
Characteristics of a Critical Flaw
Critical flaws are bugs that have a significant impact on the application’s usability, security, or stability. They often manifest as complete system failures, data corruption, security vulnerabilities, or severe performance degradation. The severity is not merely subjective; it is based on the potential impact on the application and the user.
Factors Contributing to Critical Severity
Several factors contribute to a bug being classified as critical. These include:
- System Instability: A critical flaw may lead to system crashes, freezes, or unexpected terminations. For instance, a bug that consistently causes a web application to crash when a specific button is clicked warrants critical classification.
- Data Loss or Corruption: Bugs that result in the loss or corruption of critical data are unequivocally critical. An example is a database query bug that deletes all user records.
- Security Risks: Flaws that expose the system to security breaches or unauthorized access are critical. A vulnerability that allows remote code execution is a prime example.
- Severe Performance Degradation: A bug that significantly slows down or halts the performance of a critical system component, impacting user experience, is critical. For example, a bug in a transaction processing system that drastically increases transaction times.
- Violation of Design Principles: If a bug violates fundamental design principles or security best practices, leading to a significant risk, it should be categorized as critical. A bug that bypasses security measures designed to prevent unauthorized access is an example.
Elements of a Well-Written Critical Bug Report
A comprehensive bug report is crucial for addressing critical flaws effectively. The report should clearly describe the issue, steps to reproduce it, expected versus actual results, and any relevant system information.
- Clear and Concise Description: A concise and detailed description of the problem is essential, including the specific actions taken and the observed consequences. For instance, “After clicking ‘Save,’ the application crashes with an error message ‘System Error 101’.”
- Reproducible Steps: The report should Artikel the precise steps required to reproduce the critical flaw. This allows developers to quickly replicate the problem and understand the context.
- Expected and Actual Results: A comparison of the expected behavior versus the observed behavior is crucial. For example, “Expected: The user profile is saved. Actual: The application crashes.”
- System Information: Details about the operating system, browser, version of the application, and other relevant system configurations should be included.
- Screenshots or Videos (if applicable): Visual aids can greatly enhance the report, allowing developers to visualize the issue directly.
Severity Levels Comparison
The following table illustrates the differences between various severity levels of bug reports, highlighting the characteristics of critical flaws.
| Severity Level | Description | Impact | Example |
|---|---|---|---|
| Critical | Significant impact on application functionality, stability, or security. | System crashes, data loss, security breaches, major performance degradation. | Application crashes upon login, leading to data loss. |
| Major | Significant impact on application functionality. | Partial loss of functionality, user interface errors. | Missing features in the user interface. |
| Minor | Minor impact on application functionality. | Minor user interface errors, cosmetic issues. | Minor layout issues on the web page. |
The Impact of Critical Flaws
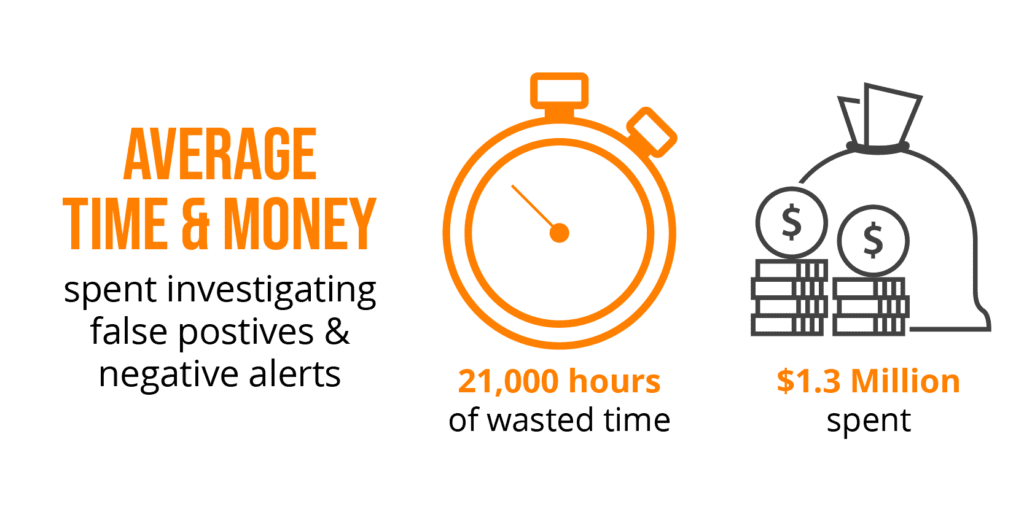
Ignoring or mishandling critical flaws in software can have devastating consequences, ranging from minor inconveniences to catastrophic system failures. The potential for harm escalates rapidly as these flaws remain unaddressed, impacting not only the software’s functionality but also user trust, financial stability, and even public safety. Understanding the potential ramifications of these vulnerabilities is crucial for software developers, security professionals, and end-users alike.Software vulnerabilities, especially critical ones, can lead to a wide array of negative consequences.
The ongoing debate around critical IE flaws and how to best report bugs is intense. A recent example, like the mimail variant posing as a legitimate PayPal email , highlights the urgent need for clear guidelines. These types of phishing scams, while distinct from the IE vulnerabilities themselves, underscore the importance of effective bug reporting mechanisms to prevent similar security breaches.
So, the discussion about critical IE flaws and bug reporting remains crucial in today’s digital landscape.
These range from compromised data security to complete system instability, affecting everything from user experience to the integrity of sensitive information. The severity of the impact is directly proportional to the criticality of the flaw and the context in which it’s exploited.
Consequences of Unresolved Critical Flaws
Critical flaws, if left unpatched, can manifest in numerous ways, jeopardizing the integrity and reliability of software systems. These vulnerabilities can be exploited by malicious actors, leading to data breaches, unauthorized access, and financial losses. In addition, these flaws can introduce instability into software systems, potentially causing unexpected crashes, performance degradation, or even complete system failure.
Risks Associated with Unresolved Critical Flaws
Unresolved critical flaws pose a significant risk to both the software’s users and the organization responsible for its development and deployment. These risks can include financial losses due to data breaches or downtime, reputational damage from compromised user trust, legal liabilities stemming from data breaches or system failures, and even loss of life in cases where critical software is responsible for safety-critical systems.
Examples of Critical Flaws and their Impact
Numerous historical examples illustrate the devastating consequences of ignoring critical flaws. The infamous Heartbleed bug, for instance, exposed sensitive user data on millions of websites. The WannaCry ransomware attack, exploiting a critical vulnerability in Windows systems, crippled organizations globally, demonstrating the potential for widespread disruption. These instances underscore the urgent need for proactive vulnerability management and prompt patching.
Impact on User Experience, Security, and System Stability
Critical flaws can severely affect user experience by introducing unexpected crashes, performance issues, or system instability. From a security perspective, unresolved critical flaws expose users to malicious attacks, data breaches, and identity theft. The overall system stability is compromised, potentially leading to widespread disruption or even complete system failure.
Real-World Case Studies of Software Failures
The following table presents some real-world case studies highlighting the impact of critical flaws. These examples illustrate the potential for significant negative consequences, from financial losses to loss of user trust and reputational damage.
| Case Study | Critical Flaw | Impact |
|---|---|---|
| Heartbleed (2014) | Vulnerability in OpenSSL | Exposed sensitive user data on millions of websites; significant financial and reputational damage for affected organizations. |
| WannaCry ransomware (2017) | Vulnerability in Windows systems | Crippled organizations globally, leading to widespread disruption and financial losses; demonstrated the potential for catastrophic disruption. |
| Equifax data breach (2017) | Vulnerability in Equifax’s systems | Exposed personal data of millions of individuals; resulted in significant financial losses and reputational damage for Equifax. |
Debate Surrounding Bug Reporting: Critical Ie Flaws Invoke Debate On Bug Reporting
The process of bug reporting, while seemingly straightforward, often sparks heated debates within development teams and organizations. Different stakeholders have varying perspectives on what constitutes a critical flaw, how it should be reported, and the subsequent actions needed to address it. These disagreements can significantly impact the efficiency and effectiveness of software development lifecycle.The debate around bug reporting often centers on the balance between thoroughness and efficiency.
Teams need to ensure all potential issues are identified and documented accurately, yet they also need to prioritize their resources to address the most critical problems first. This balancing act is where the disagreements often arise.
Common Points of Contention
Different interpretations of severity, varying levels of detail required for effective bug reporting, and differing opinions on the best communication channels all contribute to the debate. This often leads to a lack of consensus, which can hinder the resolution of crucial issues. For instance, a junior developer might perceive a bug as minor, while a senior engineer might view it as a potential security risk.
Perspectives Involved, Critical ie flaws invoke debate on bug reporting
Several key perspectives shape the debate surrounding bug reporting. Developers often focus on the technical aspects, prioritizing the reproducibility and accurate description of the bug. Testers, on the other hand, might emphasize the user experience, highlighting how the bug impacts usability. Product managers, meanwhile, might weigh the bug’s impact on the overall product roadmap and market positioning.
These differing priorities often create friction.
Organizational Approaches to Critical Flaws
Organizations adopt various approaches to handle critical flaws, each with its own strengths and weaknesses. Some prioritize a structured reporting system, with predefined severity levels and standardized templates. Others rely on more ad-hoc methods, with less formal processes but potentially faster response times.
Critical IE flaws often spark heated debates about bug reporting, with different perspectives on severity and impact. This reminds me of the challenges in optimizing system performance, like the frontside bus bottleneck, a crucial component of early computer architecture. Understanding these limitations, as explored in the article breaking the speed barrier the frontside bus bottleneck , helps us appreciate the complexities of software design.
Ultimately, similar meticulous analysis is needed when scrutinizing critical IE flaws to ensure robust and effective bug reporting practices.
Example Prioritization of Critical Flaws
Different teams or individuals may prioritize critical flaws differently. For example, a team focused on financial applications might consider a flaw that could lead to financial loss as exceptionally critical, whereas a team building a game might prioritize a flaw that hinders gameplay. These differing prioritization models are essential to understand in a bug reporting system.
Methods of Classifying Critical Flaws
Various methods exist for classifying critical flaws, each with its own criteria. These include severity levels based on potential impact (e.g., high, medium, low), the potential for security breaches, and the frequency of occurrence. One common method is the use of a matrix that combines impact and probability. This allows for a more comprehensive evaluation of the risk associated with each bug.
| Severity Level | Impact | Probability |
|---|---|---|
| Critical | High | High |
| Major | High | Medium |
| Minor | Low | Low |
This structured approach allows for more objective evaluation and consistent prioritization.
Methods for Improving Bug Reporting
Improving bug reporting is crucial for software development. Effective reporting ensures that critical flaws are identified, documented, and resolved promptly. This directly impacts the stability, security, and overall quality of the software. Thorough reporting empowers developers to address issues efficiently and prevent future occurrences.Comprehensive bug reports are not just a formality; they are a vital communication tool.
They bridge the gap between users experiencing problems and developers tasked with fixing them. Well-structured reports provide the necessary context, enabling developers to understand the issue, reproduce it, and ultimately resolve it.
Strategies for Enhancing the Bug Reporting Process
Effective bug reporting requires a multi-faceted approach. This involves fostering a culture of open communication, providing clear guidelines, and implementing systems that encourage detailed reporting. This will allow the reporting process to be more effective and accurate.
- Establish Clear Reporting Guidelines: Well-defined guidelines ensure consistency and clarity in the reporting process. These guidelines should detail the expected format, required information, and the process for reporting critical flaws. Examples include specific templates or checklists that help the user to organize their reports.
- Encourage Detailed Descriptions: Developers and users should be encouraged to provide detailed descriptions of the issue, including steps to reproduce the bug, expected behavior, actual behavior, and relevant system information. This will help the developers understand the problem and find a solution more efficiently. For instance, instead of simply stating “the program crashed,” a report should specify the steps taken, the specific input data, the error messages displayed, and the environment details.
- Implement a Structured Reporting System: A dedicated bug tracking system can streamline the process, enabling better organization, prioritization, and follow-up on reported issues. These systems often include features for assigning bugs to developers, tracking progress, and providing updates to reporters.
Techniques for Creating Comprehensive Bug Reports
Comprehensive bug reports are essential for effective issue resolution. The goal is to provide enough detail so that the issue can be reproduced and fixed with minimal effort. This will ensure efficient issue resolution and improve the quality of the software.
- Reproducible Steps: Include precise steps for reproducing the bug, ensuring consistency. This is crucial for developers to understand and replicate the issue. For instance, “1. Open the application. 2.
Click on ‘File.’ 3. Select ‘Open’…” This should lead to a specific and predictable result.
- Clear Description of the Problem: Describe the problem in detail, specifying the expected and actual behavior. Include any error messages, visual anomalies, or unexpected system responses. For example, “Expected: The file opens correctly. Actual: The application crashes with error code 123.” This ensures a clear understanding of the bug.
- Relevant System Information: Include details about the operating system, browser version, hardware specifications, and other relevant system information. For instance, “OS: Windows 11, Version 22H2; Browser: Chrome 112; CPU: Intel Core i5-12400.” This will help developers isolate any potential system-specific issues.
Best Practices for Communication and Collaboration
Effective communication is key to resolving critical flaws efficiently. A collaborative approach ensures all stakeholders are informed and involved in the process. This will also improve the overall quality of the software.
The ongoing debate around critical IE flaws and bug reporting is fascinating. It’s interesting to see how these issues are impacting the tech landscape, especially considering recent announcements like Palm introducing sequels to the Zire and Tungsten line of devices. Palm’s latest moves highlight the need for thorough testing and bug fixes in modern software, and ultimately, this impacts the reliability and security of products.
The critical IE flaws debate will likely continue as technology evolves.
| Aspect | Best Practice |
|---|---|
| Clear Communication Channels | Establish dedicated channels for bug reporting and communication, such as email threads or dedicated forums. |
| Regular Updates | Provide updates to reporters on the progress of bug resolution, including any roadblocks or delays. |
| Prompt Responses | Respond to bug reports promptly and acknowledge receipt. |
| Collaboration between Developers and Users | Encourage active communication and collaboration between developers and users, especially for critical flaws, enabling efficient troubleshooting. |
Encouraging Detailed Bug Reports
Detailed bug reports are essential for effective issue resolution. Clear expectations and incentives can encourage users and developers to provide more comprehensive information.
- Provide Clear Instructions: Clearly Artikel the required information in bug reporting guidelines. This can be done by creating a template for reporting. This can guide users in providing more detailed information.
- Positive Feedback: Acknowledge and appreciate the quality of detailed bug reports. This can motivate users and developers to maintain this level of detail in future reports.
- Reward System: Implement a system to reward users or developers for reporting comprehensive and accurate bugs. This will encourage more detailed reports.
Reviewing and Validating Bug Reports
A structured approach to reviewing and validating bug reports is essential for ensuring accuracy and prioritization. This approach should include checks for reproducibility, severity, and potential impact.
- Verification Process: Implement a process to verify the reported bug, including steps to reproduce the issue and validate the reported behavior. This should involve checking the reproducibility, severity, and impact.
- Prioritization Strategy: Establish a prioritization scheme based on the severity, frequency, and impact of the bug. This will allow the team to focus on the most critical issues first.
- Validation Checklists: Develop checklists to ensure all necessary information is included in each bug report, including steps to reproduce, expected behavior, and actual behavior. This can be used to validate and ensure quality of reports.
Tools and Technologies for Handling Critical Flaws
The identification and resolution of critical flaws are crucial for software security and user safety. Effective tools and technologies are essential for efficiently tracking, managing, and ultimately mitigating these vulnerabilities. Choosing the right tools can significantly impact the speed and accuracy of the process. This section delves into common bug tracking systems, their strengths, weaknesses, and how they facilitate the handling of critical flaws.
Common Bug Tracking Systems
Bug tracking systems are integral to the software development lifecycle. They provide a structured approach to recording, categorizing, and prioritizing bug reports. These systems facilitate communication between developers, testers, and other stakeholders, ensuring transparency and accountability. A well-implemented system streamlines the process from initial reporting to final resolution, minimizing delays and ensuring critical flaws are addressed promptly.
- Jira: A widely used platform, Jira offers robust features for managing various aspects of software development, including bug tracking. Its flexibility allows for custom workflows, enabling teams to tailor the process to their specific needs. Jira’s extensive features, including issue linking, version control integration, and agile project management tools, contribute to its popularity and its ability to manage complex projects and track critical flaws.
Its visual dashboards and reporting capabilities offer insightful data to monitor progress and identify trends. Jira’s popularity and prevalence in enterprise environments suggest its adaptability and effectiveness.
- GitHub Issues: Integrated within the popular version control platform GitHub, this system allows for seamless tracking of issues directly related to code. GitHub Issues is a simple and user-friendly tool, ideal for smaller teams or projects. Its integration with other GitHub tools provides a unified workflow. Its strength lies in its tight integration with code repositories, allowing developers to quickly identify and address the source of the bug within the codebase.
The strength of GitHub Issues lies in its close connection to the codebase and the collaboration capabilities of GitHub itself.
- Bugzilla: A robust, open-source platform, Bugzilla has been a cornerstone of bug tracking for many years. Its versatility and flexibility cater to diverse development needs. Bugzilla supports a wide range of features, including prioritization, categorization, and reporting on the status of issues. Its stability and proven track record make it a reliable choice for projects requiring a stable and reliable system for handling critical flaws.
The extensive documentation and active community support contribute to its enduring popularity and reliability.
Benefits and Drawbacks of Different Tools
Choosing the right bug tracking system depends on several factors, including team size, project complexity, and existing infrastructure. A carefully considered assessment of the benefits and drawbacks of different tools is critical to maximizing efficiency.
| Tool | Benefits | Drawbacks |
|---|---|---|
| Jira | Flexible workflows, robust features, extensive integrations, agile project management tools, detailed reporting. | Steeper learning curve, potentially complex for smaller teams, high cost for enterprise licenses. |
| GitHub Issues | Simple and user-friendly interface, seamless integration with code repositories, strong collaboration features. | Limited customization options, may not be suitable for complex projects, less comprehensive reporting than Jira. |
| Bugzilla | Open-source, versatile, flexible, stable, well-documented. | May require more technical expertise to configure, potentially slower for very large projects, less intuitive for non-technical users. |
Technical Specifications and Features
The technical specifications of these tools vary, affecting their performance and capabilities. Features such as issue linking, customizable workflows, and reporting tools contribute to a smoother and more efficient workflow. The specific functionalities of each tool should be carefully evaluated to ensure alignment with the project’s requirements. Different tools have varying levels of integration with other software development tools, impacting the overall workflow and the handling of critical flaws.
User Involvement and Feedback
User feedback is crucial in identifying critical flaws in software. Active user engagement, beyond simply reporting bugs, provides invaluable insights into the usability and functionality of a product. This engagement often reveals hidden issues and unexpected behaviors that developers might miss during testing. Effective feedback mechanisms can be instrumental in uncovering and addressing critical flaws more efficiently.
The Role of User Feedback in Identifying Critical Flaws
User feedback, when properly collected and analyzed, can expose a wide range of critical flaws. Users, by interacting with the product in various ways, encounter scenarios that might not be anticipated during internal testing. This often leads to the discovery of edge cases, unusual interactions, or poorly designed features that cause severe issues. Users’ real-world usage patterns and their unique perspectives can expose vulnerabilities and limitations that might be overlooked otherwise.
For instance, a user might discover a critical security flaw during normal usage that automated tests would not detect.
Strategies for Gathering User Feedback on Critical Flaws
Effective feedback collection strategies are vital to identifying critical flaws. These strategies should be designed to elicit detailed and specific feedback, allowing for a deep understanding of the issues. A variety of channels should be used, from dedicated feedback forms to in-app reporting tools.
- In-App Reporting Tools: These tools should be readily accessible and intuitive, guiding users through the process of reporting issues. They should also allow for the inclusion of screenshots, videos, or detailed descriptions of the issue, making it easier for developers to reproduce and understand the problem.
- Dedicated Feedback Forms: These forms can be used for more general feedback, including suggestions, ideas, and improvements to the product, potentially revealing critical flaws. They can also serve as a platform for gathering feedback about existing bugs.
- User Forums and Communities: Engaging with user communities allows for a more open and direct discussion about the product. Monitoring these forums and responding promptly to user concerns can reveal patterns of issues and uncover critical flaws.
Methods for Encouraging Users to Report Critical Flaws
Incentivizing user participation in reporting critical flaws is crucial. Users are more likely to report issues if they feel their feedback is valued and that their input can lead to tangible improvements. This can be achieved through transparency and clear communication.
- Transparency: Clearly communicating the importance of user feedback and how it is used to improve the product can encourage users to report critical flaws. Sharing updates on how reported issues are being addressed can reinforce this value.
- Reward Systems: Offering incentives, such as exclusive access to features or early access to updates, for reporting critical flaws can incentivize users to actively participate in identifying such issues. This could also include badges or recognition for their contributions.
- User Stories and Case Studies: Demonstrating how user feedback has led to improvements and solutions in the past can encourage further participation. Providing specific examples of how reported issues were addressed can increase user trust and motivate future reporting.
Examples of Successful User Feedback Mechanisms for Identifying Critical Flaws
Several successful examples exist in the software industry. These examples highlight the effectiveness of user feedback in identifying critical flaws.
- Software companies that have actively integrated user feedback into their development processes have consistently reported higher quality products. The ability to quickly respond to user concerns and incorporate their suggestions directly into the product has a profound impact on the overall software quality.
- Social media platforms frequently utilize user feedback to improve features and address critical flaws. These platforms use user comments, posts, and feedback channels to identify trending issues and address them swiftly.
Collecting and Analyzing User Feedback on Bug Reports
Collecting and analyzing user feedback on bug reports is a multi-step process. It requires careful categorization and prioritization of reported issues.
- Categorization: Categorizing bug reports based on severity, functionality, and other relevant criteria enables efficient prioritization and analysis. This ensures that critical issues are addressed promptly.
- Prioritization: Prioritizing bug reports based on factors like severity, frequency, and impact allows development teams to focus on addressing the most significant issues first. A clear prioritization process ensures that critical flaws are addressed before less impactful ones.
- Trend Analysis: Identifying recurring patterns in reported bugs can highlight areas of the software that need further attention or improvement. Trend analysis can reveal hidden vulnerabilities and improve future development.
Internal Processes and Communication
Internal processes for handling critical flaws are crucial for maintaining the integrity and stability of any software system. Effective communication and well-defined procedures ensure swift resolution and minimize potential damage. Prioritization, escalation, and feedback loops all play vital roles in mitigating risks associated with critical flaws. A robust internal framework can significantly impact the overall security and user experience of the software product.
Internal Prioritization and Handling Processes
Establishing a clear hierarchy for handling critical flaws is essential. This prioritization system should consider factors like potential impact on users, the severity of the vulnerability, and the urgency of resolution. A well-defined process ensures that the most critical flaws receive immediate attention, minimizing downtime and potential security breaches.
Importance of Clear Communication Channels
Clear communication channels for reporting and resolving critical flaws are paramount. This includes designated channels for bug reports, escalation procedures, and regular updates to stakeholders. Open communication fosters transparency and allows for a collaborative approach to problem-solving.
Escalation Procedures for Critical Flaws
Defining escalation procedures is vital for critical flaws. These procedures should Artikel specific criteria for escalating issues and the steps involved in the escalation process. A clear chain of command ensures that the appropriate individuals or teams are involved at each stage. This prevents bottlenecks and ensures that the highest levels of expertise and authority address the most serious issues.
Examples of Effective Internal Communication Strategies
Effective communication strategies involve proactive updates to relevant teams and stakeholders. Regular progress reports, status updates, and knowledge sharing through internal forums or wikis can keep everyone informed. Transparent communication builds trust and fosters a collaborative environment. Utilizing project management tools, or even simple email threads with clear subject lines and a defined escalation path, can be beneficial.
Internal Communication Strategy Table
| Stage | Description | Key Activities | Responsible Party |
|---|---|---|---|
| Reporting | Initial identification and documentation of the critical flaw. | Detailed description, reproduction steps, impact assessment. | Developer/Tester |
| Assessment | Evaluation of the flaw’s severity and potential impact. | Risk analysis, prioritization based on criteria. | Security Team/Project Manager |
| Resolution | Implementation of a fix or workaround for the flaw. | Development of a patch, testing, deployment. | Development Team |
| Verification | Confirmation that the flaw has been resolved and no further issues exist. | Regression testing, quality assurance. | QA Team |
| Closure | Formal closure of the flaw, documentation of resolution. | Archiving of reports, communication of resolution. | Project Manager/Security Team |
Last Point
The debate surrounding critical IE flaws in bug reporting underscores the need for clear communication, effective prioritization, and user involvement. By implementing improved reporting methods, utilizing appropriate tools, and fostering collaboration, software development teams can mitigate the risks associated with critical flaws. The key takeaway is that a robust and user-centric approach to bug reporting is essential for building reliable and secure software systems.