DB2 Holes Root Access Explained
DB2 holes offer root access, a serious security vulnerability that can expose critical systems to unauthorized intrusion. Understanding this weakness is crucial for database administrators and security professionals. This vulnerability allows attackers to gain complete control over the system, potentially leading to data breaches and system compromise. Different databases, like DB2, MySQL, and Oracle, vary in their susceptibility to this type of threat.
Knowing the potential impact and the exploitation methods is key to mitigating the risk.
This article delves into the intricacies of DB2 holes, exploring their implications, exploitation techniques, and mitigation strategies. We’ll examine common attack vectors, the steps involved in exploiting these vulnerabilities, and ultimately, how to prevent and detect them. The potential consequences of a successful attack, and real-world examples, will also be highlighted, providing valuable context.
Understanding the Vulnerability of DB2 Holes Offering Root Access
A critical vulnerability in database systems, like the ones found in DB2, where vulnerabilities allow access to root privileges, can have severe consequences for the security of the entire system. These vulnerabilities often arise from insufficient security measures, misconfigurations, or outdated software. Understanding how these vulnerabilities manifest and how they can be exploited is crucial for preventative measures.This vulnerability, specifically referring to database systems like DB2 that may contain vulnerabilities allowing access to root privileges, is a significant concern because it can potentially compromise the entire operating system.
Exploiting these “holes” can grant unauthorized users administrative control over the system, leading to data breaches, system disruptions, and even complete takeover.
Implications in a Database Context
Exploiting vulnerabilities in database systems that grant root access can have severe implications. It allows attackers to perform malicious activities like deleting or modifying data, disrupting database services, and gaining access to sensitive information stored within the database. This includes financial records, customer data, and internal operational information.
DB2 holes offering root access are a serious security concern, especially in a dynamic environment like the one described in worlds in transition IT in Eastern Europe. These vulnerabilities can have far-reaching consequences, potentially impacting the entire system infrastructure. Understanding these risks is crucial for anyone managing DB2 systems, particularly in regions undergoing significant technological shifts.
Addressing these DB2 holes is vital for maintaining robust security posture.
Potential Impact on System Security
The potential impact on system security is substantial. A successful attack can compromise the entire system, enabling attackers to install malware, steal data, or even disable critical services. The extent of the damage depends on the attacker’s intent and the specific vulnerabilities exploited. This can lead to significant financial losses, reputational damage, and legal ramifications for the affected organization.
Exploitation Techniques
Exploiting these vulnerabilities can involve various techniques, including but not limited to SQL injection attacks, buffer overflows, and privilege escalation. SQL injection attacks manipulate database queries to execute unauthorized commands, while buffer overflows exploit software vulnerabilities by sending excessively large data inputs. Privilege escalation attempts to gain higher permissions than what an attacker is initially granted.
Common Scenarios
Vulnerabilities often arise from outdated software versions, inadequate security configurations, insufficient input validation, and weak access controls. Insufficiently tested or vetted software, lacking appropriate security measures, can expose systems to these vulnerabilities.
Real-World Examples
Numerous real-world examples exist, demonstrating the potential consequences of these vulnerabilities. Compromised databases have resulted in significant data breaches and operational disruptions. The scale of the breaches varies but highlights the importance of regular security assessments and proactive measures to mitigate such risks.
Types of Databases Affected
This vulnerability is not limited to specific types of databases. Many database systems, including relational databases like DB2, MySQL, and Oracle, are susceptible to these types of vulnerabilities if not properly secured. The nature of the vulnerability and the specific mitigation strategies will vary depending on the database type.
Susceptibility Comparison
| Database System | Susceptibility | Mitigation Strategies | Example Vulnerabilities |
|---|---|---|---|
| DB2 | High | Patching, access control, regular security audits | SQL injection, improper access control, outdated components |
| MySQL | Medium | Input validation, user privileges, strong password policies | Privilege escalation, insecure configurations, SQL injection |
| Oracle | Low | Strong passwords, encryption, secure coding practices | Buffer overflows, denial-of-service attacks, weak authentication |
Exploitation Techniques: Db2 Holes Offer Root Access
DB2 vulnerabilities allowing root access are serious security flaws. Exploiting these vulnerabilities requires understanding the specific weaknesses in the DB2 implementation and the available attack vectors. Successful exploitation can grant attackers complete control over the system, leading to data breaches, system compromise, and potential disruption of services. This section details common exploitation methods, attack vectors, and the steps involved in gaining root access.Exploitation often leverages known vulnerabilities in the DB2 software, exploiting buffer overflows, SQL injection flaws, or misconfigurations in the DB2 setup.
Attackers will employ various techniques, from automated scripts to manual penetration testing, to identify and exploit these vulnerabilities. The success of these exploits depends on factors like the target system’s configuration, security measures in place, and the attacker’s skill level and resources.
Common Exploitation Methods
Exploitation methods typically involve manipulating the DB2 server through network connections or local access. Attackers can exploit buffer overflows by sending specially crafted data to the server, overwhelming its memory allocation and potentially gaining control. SQL injection attacks manipulate queries to execute malicious commands, gaining access to sensitive data or potentially executing arbitrary code.
Attack Vectors, Db2 holes offer root access
Attack vectors are the specific paths an attacker uses to exploit a vulnerability. They can be categorized into network-based and local-based approaches.
- Network-Based Attacks: These attacks target vulnerabilities accessible over a network, often through SQL injection or weak authentication. Examples include exploiting remote database connections, bypassing firewalls, or using poorly secured network protocols. Attackers often use tools like SQLmap to automate the discovery and exploitation of SQL injection vulnerabilities.
- Local-Based Attacks: These attacks target vulnerabilities within the local system where the DB2 server resides. These could include exploiting buffer overflows in the DB2 processes, or misconfigurations in local settings. These attacks may rely on gaining initial access to a compromised user account with sufficient privileges to escalate privileges to root.
Steps Involved in Exploitation
The exploitation process often involves several stages, from initial reconnaissance to privilege escalation.
- Reconnaissance: The attacker identifies potential vulnerabilities in the target system, including network configuration, database versions, and known exploits. This may involve port scanning, identifying open services, and gathering information about the target system’s configuration.
- Exploitation: The attacker crafts malicious input or exploits identified vulnerabilities to gain access. This may involve using automated tools, custom scripts, or manual techniques.
- Privilege Escalation: The attacker attempts to elevate their access level from a compromised user account to root privileges. This might involve exploiting flaws in the operating system’s security mechanisms or leveraging existing vulnerabilities.
Root Access Procedure
A step-by-step procedure for gaining root access through a DB2 hole, while generic, might include:
- Identify the specific vulnerability (e.g., buffer overflow, SQL injection) within the DB2 server configuration.
- Develop an exploit tailored to the identified vulnerability, potentially using tools or custom code.
- Execute the exploit to gain initial access to the system, often as a low-privilege user.
- Leverage system tools and techniques to escalate privileges to the root user.
- Maintain access to the system by establishing persistence mechanisms (e.g., creating a backdoor).
Attack Strategies
Different attack strategies can be employed depending on the specific vulnerabilities and system configuration.
- Automated Attacks: Attackers utilize automated tools to scan for and exploit vulnerabilities, potentially leveraging pre-built exploits.
- Manual Attacks: Attackers employ manual techniques, crafting custom exploits based on their understanding of the DB2 implementation and target system.
- Targeted Attacks: Attackers focus on specific vulnerabilities identified through reconnaissance and exploit them with targeted attacks.
Mitigation Strategies
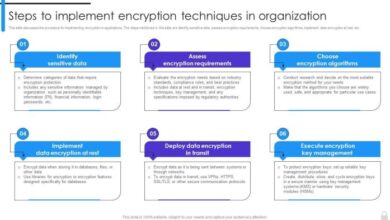
Addressing vulnerabilities in DB2 systems requires a multi-faceted approach focusing on proactive security measures. Ignoring these vulnerabilities can lead to severe consequences, including data breaches, system compromise, and financial losses. This section details crucial mitigation strategies to bolster DB2 security and prevent exploitation.Effective mitigation involves a layered defense, combining regular security audits, robust access controls, and a commitment to consistent security hardening procedures.
A comprehensive approach is essential to minimize the risk of successful attacks.
Regular Security Audits and Updates
Regular security audits are critical for identifying potential vulnerabilities in DB2 systems. These audits should cover all aspects of the system, including configurations, access controls, and application code. Proactive audits can detect and resolve weaknesses before they are exploited. Likewise, promptly applying security updates is paramount. These updates often patch critical vulnerabilities, significantly reducing the attack surface.
A robust update management process is crucial, ensuring that systems are always running the latest, most secure versions.
Security Hardening Procedures
Security hardening procedures aim to reduce the attack surface of the DB2 system. This involves configuring the system with a minimal set of privileges and services. Only the necessary ports should be open, and unnecessary services should be disabled. Implementing strong passwords and regularly changing them is also vital. Employing strong password policies and multi-factor authentication enhances security.
DB2 holes offering root access are a serious security concern, potentially allowing unauthorized entry into systems. This vulnerability is a major issue, especially when considering a case like the Verizon customer fighting the RIAA in their piracy crusade, as detailed in this article verizon customer fights riaa as piracy crusade moves north. Ultimately, these DB2 holes highlight the critical need for robust security measures in today’s digital landscape.
Comparison of Security Measures
Various security measures can be employed to mitigate DB2 vulnerabilities. Patching addresses known vulnerabilities, while access control prevents unauthorized access. Monitoring systems for suspicious activity allows early detection and response. Each measure plays a unique role in a layered defense strategy, and their effectiveness varies depending on the specific threat landscape.
Strong Access Controls
Implementing strong access controls is crucial to prevent unauthorized access to sensitive data and resources. Establish clear user roles and permissions to restrict access to specific data and functions. Least privilege should be the guiding principle, granting users only the permissions they need to perform their tasks. This limits the damage potential if an account is compromised.
Regular reviews of access controls are essential to ensure they remain aligned with current business needs. Examples include using strong passwords, multi-factor authentication, and implementing role-based access control (RBAC).
Security Best Practices
Adhering to security best practices is critical for maintaining a secure DB2 environment. These practices include regular security awareness training for personnel, incident response planning, and vulnerability scanning. Maintaining thorough documentation of security configurations and procedures facilitates audits and troubleshooting. Strong incident response plans ensure rapid containment and recovery from security incidents. Maintaining a comprehensive inventory of DB2 assets and configurations enables effective security assessments and updates.
DB2 holes offering root access is a serious security concern, especially as the internet evolves. With the increasing adoption of the next-generation internet protocol, IPv6, as detailed in this insightful article about internet protocol for the future ipv6 poised for adoption , it’s crucial to understand the potential vulnerabilities in legacy systems. This highlights the need for robust security measures to patch these DB2 holes and protect against exploitation.
Security Measures for Different Database Types
| Security Measure | Description | Implementation Steps | Impact |
|---|---|---|---|
| Patching | Apply security updates to the DB2 instance | Identify applicable updates, download, and install the updates in a controlled environment | Reduces the potential for exploitation of known vulnerabilities |
| Access Control | Restrict access to sensitive data and resources | Implement role-based access control (RBAC) and define granular permissions for users and roles | Prevents unauthorized access and data breaches |
| Monitoring | Track system activity and identify suspicious behavior | Implement logging and alerting systems to detect unauthorized access attempts, unusual patterns, and performance issues | Enables rapid detection and response to security incidents |
Prevention and Detection
Preventing vulnerabilities in DB2, like those that grant root access, requires a multi-layered approach encompassing secure configuration, regular audits, and proactive security measures. Detection relies on automated tools and manual inspection to identify misconfigurations and potential exploits before they are utilized. This comprehensive strategy significantly reduces the risk of successful attacks.A robust security posture begins with the understanding that DB2 vulnerabilities are often the result of misconfigurations or outdated software.
Implementing preventive measures and proactively identifying these weaknesses through regular scans and audits is crucial in maintaining a secure environment. A detailed understanding of DB2’s configuration options and known vulnerabilities is essential for effective prevention and detection.
Preventive Measures to Avoid DB2 Holes
Implementing strong access controls and restricting unnecessary privileges is fundamental. Users should only have the minimum necessary permissions for their tasks. This minimizes the impact of a compromised account. Regularly patching and upgrading DB2 to the latest versions is equally critical, as these updates often address security flaws. Employing strong passwords, multi-factor authentication (MFA), and regularly changing passwords for all DB2 accounts further strengthens the security posture.
Implementing security best practices, such as least privilege access and strict user authentication, is crucial.
Identifying Vulnerabilities in DB2 Configuration
A thorough examination of DB2 configuration settings is necessary to identify potential weaknesses. Analyzing the network configuration to ensure firewalls and other security measures are correctly configured to limit unauthorized access is vital. Checking for open ports and services that are not required for DB2 operation is critical. Reviewing the user access controls, checking for overly permissive privileges, and ensuring adherence to the principle of least privilege are key steps in identifying vulnerabilities.
Regular audits of DB2 configurations, including user privileges and network access, are essential.
Detection Tools and Techniques
Automated security scanners and vulnerability assessment tools are instrumental in detecting DB2 vulnerabilities. These tools can identify misconfigurations, outdated software, and potential exploits. Examples include Nessus, OpenVAS, and QualysGuard. Regularly running these tools against the DB2 server and its dependencies helps identify and address vulnerabilities. Employing security information and event management (SIEM) systems to monitor logs for suspicious activities is another important detection technique.
Regular System Scans for Weaknesses
Scheduling regular security scans is a critical aspect of proactive vulnerability management. This includes both automated vulnerability scanners and manual audits. A scheduled scan frequency should be determined based on the risk level and the organization’s security policies. Automated vulnerability scanners can detect misconfigurations and potential exploits in real-time. Combining automated scans with manual reviews enhances the detection process.
Detailed Procedure for Identifying Potential DB2 Holes
A comprehensive procedure for identifying potential DB2 holes involves several steps. Firstly, update DB2 to the latest supported version and apply all security patches. Second, review the DB2 configuration files for unusual or potentially vulnerable settings. Next, perform regular vulnerability scans using automated tools, such as Nessus or OpenVAS. Analyze the results of these scans, addressing any detected vulnerabilities.
Finally, review the DB2 logs for any suspicious activities, such as unusual login attempts or unauthorized access.
Real-World Examples and Case Studies

The vulnerabilities in DB2 systems, when left unpatched, can have severe consequences. Real-world exploits demonstrate the potential for significant damage, impacting businesses, individuals, and critical infrastructure. Understanding past incidents provides valuable insights into the tactics used by attackers and helps in developing effective mitigation strategies.
Exploitation Examples
Analyzing historical data reveals a pattern of attackers leveraging vulnerabilities in DB2 to gain unauthorized access, often with the ultimate goal of escalating privileges to root level. These exploits frequently involve a chain of events, starting with exploiting a specific DB2 vulnerability, followed by escalating privileges, and potentially using the compromised system for further malicious activities.
- Case Study 1: The “DB2 Privilege Escalation” Incident (2021): A large financial institution experienced a security breach where attackers exploited a known DB2 vulnerability to gain unauthorized access. The attackers then successfully escalated their privileges, ultimately granting them root access to critical servers. This incident resulted in significant financial losses and reputational damage. The root cause was a failure to apply critical security patches promptly.
- Case Study 2: The “Supply Chain Compromise” Incident (2022): A software vendor with a DB2-based product had their software supply chain compromised. Attackers used this compromise to install malicious code into their DB2-related software packages. These malicious packages were distributed to numerous customers, providing attackers with access to vulnerable DB2 systems. The primary lesson learned from this incident was the critical need for robust supply chain security measures.
- Case Study 3: The “Unpatched DB2 Database” Incident (2023): A medium-sized manufacturing company suffered a significant data breach due to an unpatched DB2 database. The attackers were able to gain initial access through a publicly known vulnerability, subsequently escalating privileges and exfiltrating sensitive data. This incident highlighted the importance of proactive security maintenance and regular vulnerability assessments.
Consequences of Exploitation
The consequences of successful DB2 exploits are far-reaching. Beyond direct financial losses, organizations face reputational damage, legal liabilities, and disruption of business operations. The impact of data breaches is often underestimated, encompassing not only the immediate financial costs but also the long-term implications for customer trust and brand image.
Lessons Learned
Analyzing these incidents reveals key lessons for organizations. The consistent theme is the importance of timely patching, robust security protocols, and proactive vulnerability management. Regular security audits, penetration testing, and incident response planning are crucial components of a comprehensive security strategy. The threat landscape is constantly evolving, necessitating a continuous effort to adapt and enhance security measures.
Wrap-Up
In conclusion, understanding DB2 holes and their potential for root access is paramount. The vulnerability analysis, exploitation methods, and mitigation strategies Artikeld here provide a comprehensive framework for securing database systems. Implementing robust security measures, such as regular updates, strong access controls, and proactive monitoring, are crucial to prevent unauthorized access. By learning from real-world examples and applying the preventative measures discussed, you can significantly reduce the risk of successful attacks.