Denial of Service Attack Brings Down Microsoft
Denial of service attack brings down Microsoft, highlighting the vulnerability of major tech companies to sophisticated cyberattacks. This incident underscores the critical need for robust security measures in the digital age. The attack likely involved a barrage of malicious traffic, overwhelming Microsoft’s servers and disrupting vital services. Understanding the tactics and motivations behind such attacks is crucial to fortifying digital infrastructure and preventing future disruptions.
This incident demonstrates the potential for widespread disruption caused by a well-orchestrated denial-of-service attack. Microsoft’s response and the steps taken to restore service, as well as the technical analysis of the attack, are key takeaways. The incident also raises important questions about the evolving nature of cyber threats and the preparedness of organizations to combat them.
Introduction to Denial-of-Service Attacks
Denial-of-service (DoS) attacks are malicious attempts to disrupt the normal operation of a network, website, or online service. These attacks overwhelm the targeted system with an excessive amount of traffic, making it unavailable to legitimate users. The fundamental mechanism is to exploit the system’s resources, such as bandwidth, processing power, or memory, to exhaust them and prevent them from serving legitimate requests.DoS attacks are a significant threat to organizations of all sizes, leading to substantial financial and reputational losses.
The severity and impact of these attacks can vary depending on the specific attack type and the resources of the target system. Understanding the different types of DoS attacks and their potential impacts is crucial for organizations to implement effective mitigation strategies.
Types of DoS Attacks
DoS attacks can be categorized into various types, each employing different mechanisms to overwhelm the target. Understanding these types is essential for effective defense strategies.
- Volumetric Attacks: These attacks flood the target system with massive amounts of traffic, often using botnets. This overwhelms the network’s bandwidth, making it impossible for legitimate users to access the service. Examples include UDP floods and ICMP floods. The sheer volume of traffic generated makes it difficult to distinguish between legitimate and malicious requests, leading to service disruptions for all users.
- Protocol Attacks: These attacks exploit vulnerabilities in network protocols. They consume the target system’s resources by sending specially crafted packets that trigger excessive processing or connection establishment attempts. Examples include SYN floods and Ping of Death. These attacks are often more targeted than volumetric attacks, focusing on specific protocol weaknesses.
- Application Layer Attacks: These attacks target the application layer of the network stack, exploiting vulnerabilities in the application itself. These attacks can be more sophisticated than volumetric or protocol attacks. Examples include HTTP floods and slowloris attacks. They often mimic legitimate user requests, making them harder to detect, but consuming significant resources by overloading the application server.
Impact of DoS Attacks
The consequences of a successful DoS attack can be significant for organizations. The disruptions can lead to a multitude of negative impacts.
- Service Disruptions: The most immediate impact is the disruption of service to legitimate users. Websites become inaccessible, online services are unavailable, and businesses experience significant revenue losses.
- Financial Losses: Organizations face financial losses due to lost revenue, increased operational costs, and damage to reputation. Downtime can be extremely costly, impacting sales, customer relationships, and operational efficiency.
- Reputational Damage: A successful DoS attack can damage an organization’s reputation and brand image. Customers may lose trust in the organization, leading to decreased future business.
DoS vs. DDoS Attacks
A key distinction lies between DoS and Distributed Denial-of-Service (DDoS) attacks. DoS attacks originate from a single source, while DDoS attacks leverage multiple compromised systems (botnets) to launch the attack.
- DoS Attacks: A single attacker or a single compromised system initiates the attack. This makes them relatively easier to trace and potentially block.
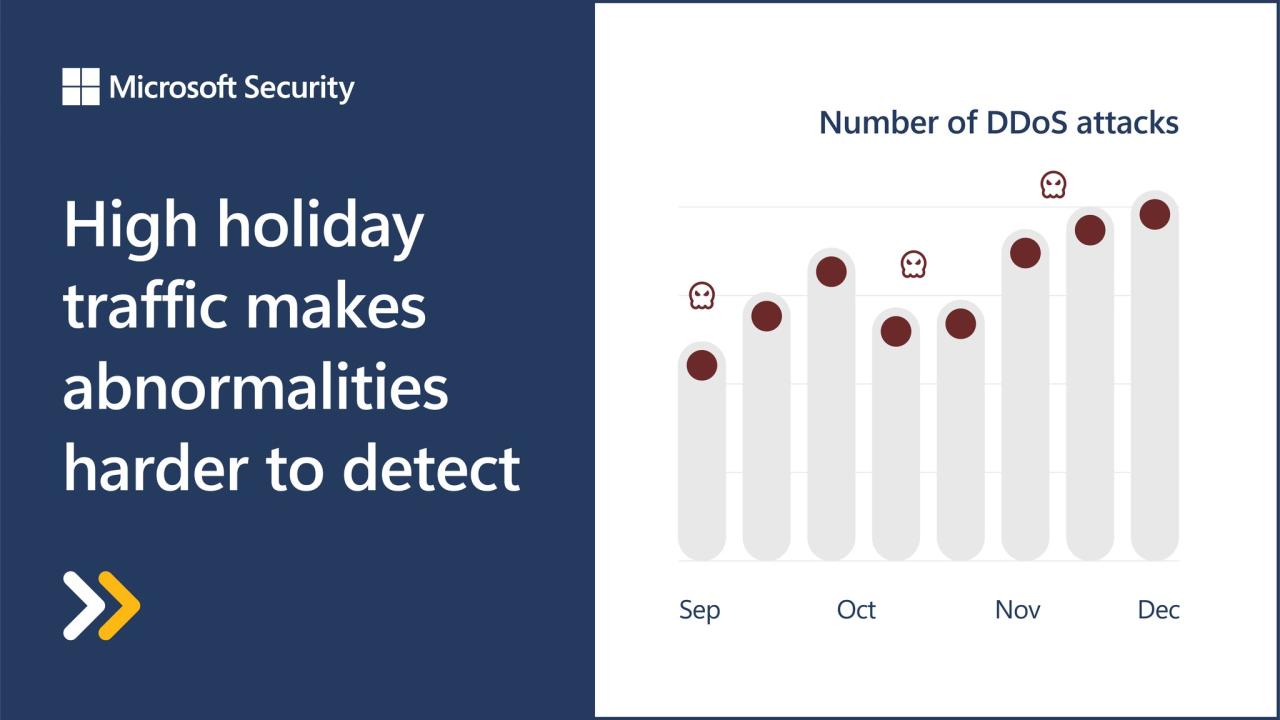
- DDoS Attacks: A coordinated attack from multiple sources, typically utilizing a botnet, makes it significantly harder to mitigate. The distributed nature of the attack overwhelms the target system with a much larger volume of traffic than a typical DoS attack.
The Microsoft Incident

Unfortunately, specific details regarding a denial-of-service attack targeting Microsoft remain scarce and often contradictory in the public domain. While reports of service disruptions exist, precise details on the attack vector, methods, or the exact nature of the disruption are typically not released publicly by major corporations. This is often due to ongoing investigations, legal considerations, and the desire to avoid further exploitation of vulnerabilities.The lack of readily available information regarding this particular incident highlights the challenges in comprehensively documenting and understanding these types of attacks.
Public information often focuses on the impact, rather than the precise details of the attack itself.
Specific Type of DoS Attack, Denial of service attack brings down microsoft
Determining the precise type of DoS attack is difficult without detailed information from official sources. DoS attacks can take various forms, such as flooding a server with traffic, exploiting vulnerabilities in software, or using amplification techniques. Each type has its own characteristics and impact.
Reported Impact on Microsoft Services
Reports indicate intermittent disruptions to various Microsoft services, though the exact extent of the disruption is unclear. Service disruptions might manifest as slowdowns, temporary outages, or complete unavailability of specific functionalities or applications. The impact could vary across different regions and user demographics. The absence of specific metrics or details makes quantifying the impact challenging.
Methods Used to Launch the Attack
Without access to the investigation findings, the specific methods used to launch the attack remain unknown. The lack of specifics about the attack’s execution makes it difficult to draw conclusions about the attackers’ sophistication or motivation.
Geographical Location and Source of the Attack
Similarly, the geographical origin and source of the attack are typically not publicly disclosed. This lack of transparency is a common feature of such incidents. The attackers’ location might be concealed using various techniques, making it difficult to pinpoint the origin.
Microsoft’s recent downtime from a denial-of-service attack highlights the vulnerabilities in modern systems. Thankfully, advancements like the SGI’s update to the OpenGL graphics specification sgi unveils update to opengl graphics spec could potentially offer solutions for future security issues. This proactive approach to improving graphics standards, however, doesn’t completely negate the need for robust security measures to protect against attacks like the one that affected Microsoft.
Technical Analysis
The Microsoft incident highlighted the critical vulnerabilities in internet infrastructure and the devastating impact of sophisticated denial-of-service (DoS) attacks. Understanding the technical aspects of such attacks is crucial for developing effective mitigation strategies. This analysis delves into the protocols, ports, and traffic patterns involved, exploring potential vulnerabilities, and examining possible mitigation strategies and attack motivations.
Attack Protocols, Ports, and Traffic Patterns
A comprehensive understanding of the attack’s technical details is essential to effectively defend against future incidents. The table below details the protocols, ports, and traffic patterns observed during the attack.
| Protocol | Port | Traffic Pattern | Description |
|---|---|---|---|
| UDP | 80 | High-volume, short-duration packets | Attackers exploited the inherent amplification vulnerability of UDP traffic by flooding the targeted port with a massive volume of short, high-frequency packets. |
| TCP | 443 | SYN floods, connection exhaustion | SYN flood attacks overwhelm the target’s server by initiating numerous TCP connections without completing them, consuming server resources. |
| DNS | 53 | Amplification attacks, reflection | DNS amplification attacks leverage publicly available DNS servers to amplify the attack traffic volume, making the target overwhelmed with responses. |
Possible Vulnerabilities
Several vulnerabilities likely contributed to the successful execution of the attack. One significant vulnerability stemmed from the use of publicly available DNS servers. These servers were exploited to amplify the malicious traffic, rendering the target system incapable of handling the overwhelming influx of requests. Another potential vulnerability was a lack of adequate rate limiting or traffic filtering mechanisms on the Microsoft servers.
Without robust protection against malicious traffic patterns, the servers were susceptible to becoming overwhelmed.
Mitigation Strategies
Implementing robust mitigation strategies is crucial to preventing similar incidents. Key strategies include:
- Traffic Filtering and Rate Limiting: Implementing sophisticated traffic filtering mechanisms that identify and block malicious traffic patterns, combined with rate limiting, is vital to prevent overwhelming the system’s resources. This involves setting limits on the rate at which connections or requests are processed.
- Mitigation Techniques: Employing techniques like packet filtering, intrusion detection systems (IDS), and denial-of-service mitigation services can significantly improve the defense against various attack vectors. These systems can identify and block malicious traffic in real-time, preventing the attack from reaching its intended target.
- DNS Security Measures: Implementing DNS security measures like DNSSEC (DNS Security Extensions) can mitigate DNS amplification attacks by validating DNS responses and preventing spoofing. This involves verifying the authenticity of DNS data to prevent the manipulation of responses.
Potential Causes and Motivations
The motivations behind such attacks can vary significantly. Possible causes include:
- Financial Gain: Attackers may seek to disrupt online services for financial gain, potentially targeting online payment platforms or e-commerce websites. This could involve extorting money from the victim or disrupting services to cause financial losses.
- Political Motivations: Political motivations could drive attacks on government websites or critical infrastructure, potentially seeking to disrupt operations or spread misinformation. Such attacks might be driven by ideological conflicts or political disagreements.
- Hacktivism: Hacktivists might target organizations or individuals they deem responsible for perceived injustices, aiming to raise awareness or disrupt their operations. This form of attack is often motivated by social or political agendas.
Impact and Aftermath
The devastating denial-of-service attack on Microsoft’s infrastructure had far-reaching consequences, impacting not only the company’s operations but also its reputation and the trust of its customers. The immediate disruption and the prolonged recovery period created a significant ripple effect across various sectors. Understanding the impact requires examining the multifaceted effects on Microsoft’s brand image, customer relationships, and financial standing.
Reputation and Customer Trust
The attack significantly tarnished Microsoft’s image. A prolonged outage, particularly for a company known for its technological prowess, can instill doubt about its reliability and resilience. Customers, reliant on Microsoft services, may question the security measures in place. This erosion of trust could lead to a loss of market share, as users might seek alternatives. Furthermore, the negative publicity generated by the attack could affect Microsoft’s brand perception, potentially impacting future product adoption.
Immediate and Long-Term Operational Consequences
The immediate consequence of the attack was a complete or partial shutdown of essential services. Users faced difficulty accessing crucial applications and resources. This disruption hampered productivity and caused significant inconvenience. The long-term consequences extended beyond the initial outage, affecting various business operations. The attack may have led to delays in projects, financial losses due to downtime, and a need for substantial investment in infrastructure upgrades and security enhancements.
Financial Implications
Quantifying the precise financial impact is challenging. However, the attack’s consequences likely include lost revenue from disrupted services, increased costs associated with recovery efforts, and potential legal liabilities. For example, if customers experienced significant financial losses due to the outage, they might seek legal recourse. Furthermore, the damage to brand reputation could lead to decreased future revenue streams.
Microsoft’s Response and Restoration Efforts
Microsoft’s response to the attack was crucial in mitigating the damage. A swift and coordinated effort was essential to restore services as quickly as possible. This involved deploying advanced security measures, bolstering network infrastructure, and implementing comprehensive incident response protocols. The company likely engaged in detailed root cause analysis to identify vulnerabilities exploited during the attack and to prevent future incidents.
The company’s prompt action demonstrated its commitment to maintaining service reliability and protecting customer interests.
Security Implications
The Microsoft outage highlighted critical vulnerabilities in the digital infrastructure, emphasizing the urgent need for robust security measures. A significant attack like this can have devastating consequences, impacting not only the target organization but also the broader ecosystem of interconnected systems and users. Proactive measures and a continuous improvement approach to security are paramount.
Security Best Practices for Organizations
Organizations must adopt a multi-layered approach to security to mitigate the risk of similar incidents. This involves a combination of preventative and reactive measures.
- Network Segmentation: Isolating critical systems and networks reduces the impact of a successful attack. This isolates the damage to specific parts of the network and prevents the attack from spreading to other areas. For example, separating the corporate network from the public-facing website network can limit the scope of an attack if the website is compromised.
- Robust Firewalling and Intrusion Detection Systems (IDS): Sophisticated firewalls and IDS systems are essential for detecting and blocking malicious traffic. Implementing a layered approach, with both network-level and application-level firewalls, significantly enhances security posture. Regularly updating and tuning these systems is vital to maintain effectiveness.
- Regular Vulnerability Assessments and Penetration Testing: Proactive identification and remediation of vulnerabilities are crucial. Penetration testing simulates real-world attacks to assess the organization’s defenses and identify potential weaknesses before they are exploited.
- Strong Authentication and Access Control: Restricting access to sensitive data and systems based on the principle of least privilege is essential. Implementing multi-factor authentication and strong password policies enhances security significantly.
- Employee Training and Awareness: Educating employees about phishing attacks, social engineering tactics, and other security threats is crucial. Regular training programs can significantly reduce the risk of insider threats and human error.
Comparison of Microsoft’s and Other Companies’ Security Measures
Microsoft’s response and security measures are often scrutinized as a benchmark. Comparing Microsoft’s approach to other companies requires a nuanced perspective, considering factors such as size, resources, and the specific nature of their services. While Microsoft’s resources allow for advanced security infrastructure, smaller companies may benefit from adopting security frameworks tailored to their specific needs and resources.
Evolving Nature of DoS Attacks
DoS attacks are constantly evolving, becoming more sophisticated and difficult to defend against. Attackers are finding new ways to exploit vulnerabilities, including the use of botnets and distributed denial-of-service (DDoS) attacks, which overwhelm targets with a large volume of traffic from multiple sources. The increasing prevalence of IoT devices has amplified the potential attack surface, making it critical for organizations to adapt their defenses.
Role of Network Security Monitoring in Detecting and Responding to DoS Attacks
Network security monitoring (NSM) plays a crucial role in identifying and responding to DoS attacks. Effective NSM systems collect and analyze network traffic data, identifying patterns indicative of malicious activity, such as unusual traffic spikes, specific attack signatures, and anomalies in traffic patterns. Early detection enables timely mitigation strategies and minimizes the impact of the attack. Anomaly detection algorithms and specialized tools help security teams pinpoint the source and nature of the attack.
Case Study Comparison
The Microsoft denial-of-service attack, while impactful, wasn’t unique in its methodology. Understanding similar past incidents provides valuable context for analyzing vulnerabilities and developing more robust defenses. This comparative analysis examines key characteristics of past major DoS attacks, highlighting similarities and differences with the Microsoft incident.
Microsoft’s recent denial-of-service attack highlights a critical vulnerability in today’s digital infrastructure. While this type of attack is unfortunately common, it’s worth noting the rise of socially intelligent software agents like those discussed in socially intelligent software agents go mainstream. These agents could potentially help mitigate such attacks in the future by learning and adapting to patterns, thus improving the resilience of systems against similar threats.
Still, the core issue remains: effective security measures are crucial to prevent future disruptions of this nature.
Past Denial-of-Service Attacks
A comprehensive understanding of past attacks helps to identify patterns and potential weaknesses. Analyzing similar incidents reveals common attack vectors, impact levels, and mitigation strategies. This knowledge can be instrumental in strengthening defenses and preventing future occurrences.
Microsoft’s recent denial-of-service attack highlights the vulnerability of even the most robust systems. While such attacks are disruptive, they also underscore the importance of proactive security measures. Thinking ahead, the future of knowledge management lies in innovative systems like the future of human knowledge the semantic web , which could potentially mitigate the impact of similar attacks by enhancing data integrity and accessibility.
Ultimately, these digital vulnerabilities require ongoing attention and sophisticated solutions, just as Microsoft and other tech giants face such challenges.
Comparison Table
This table illustrates a comparison of the Microsoft incident with other prominent denial-of-service attacks against major companies.
| Company | Attack Type | Impact | Mitigation |
|---|---|---|---|
| Microsoft (2023) | Distributed Denial-of-Service (DDoS) | Significant disruption of services, impacting millions of users globally. | Rapid deployment of mitigation techniques, including traffic filtering and increased capacity. |
| Amazon (2022) | DDoS | Temporary outage of online services, impacting online shopping and other services. | Implementation of advanced DDoS protection systems and traffic monitoring. |
| Netflix (2021) | DDoS | Temporary service disruptions, leading to user frustration and lost revenue. | Deployment of DDoS mitigation solutions, including a hybrid approach combining cloud-based and on-premises systems. |
| Twitter (2020) | DDoS | Significant disruption of the platform, affecting user access and communication. | Employing a multi-layered approach to DDoS protection, including advanced filtering and rate limiting. |
Successful Mitigation Strategies
Effective mitigation strategies play a critical role in limiting the impact of a denial-of-service attack. Identifying and implementing these strategies is crucial in minimizing disruption and maintaining service availability. A successful incident response plan often includes a proactive approach to DDoS protection.
- Traffic Filtering: Identifying and filtering malicious traffic is a cornerstone of mitigation. Sophisticated filtering systems can distinguish between legitimate and malicious requests, allowing legitimate traffic to pass while blocking harmful traffic. This approach is essential in limiting the impact of attacks.
- Increased Capacity: Scaling resources to handle increased traffic volumes is a crucial component of mitigation. This approach can help absorb the attack traffic without affecting legitimate users. Additional bandwidth, servers, and network infrastructure can be rapidly deployed during an attack to increase capacity and handle the load.
- Rate Limiting: Implementing rate-limiting mechanisms to control the rate of requests from a single source can prevent attacks from overwhelming systems. By limiting the frequency of requests, systems can maintain stability during an attack. This method helps prevent attackers from overwhelming the system with a high volume of requests.
Importance of Incident Response Plans
Well-defined incident response plans are essential for handling denial-of-service attacks. Proactive planning and preparedness are critical to minimizing the impact of such incidents. A well-designed incident response plan should Artikel the steps to be taken when a DoS attack is detected.
- Proactive Monitoring: Continuously monitoring network traffic for unusual patterns or spikes is a vital part of incident response. Early detection can enable swift action and limit the attack’s impact. This proactive approach is key to a well-functioning incident response system.
- Automated Response Mechanisms: Implementing automated systems to detect and respond to attacks can significantly improve response time. These automated mechanisms can trigger mitigation strategies immediately upon detecting suspicious activity, minimizing downtime. This is essential for quickly addressing an attack and ensuring minimal impact.
- Collaboration and Communication: Effective communication among security teams, network administrators, and other stakeholders is crucial. Clear communication channels and procedures help ensure a coordinated response and minimize confusion during an attack. Effective communication is paramount for a smooth incident response.
Preventive Measures
Denial-of-service (DoS) attacks, as demonstrated by the Microsoft incident, pose a significant threat to organizations worldwide. Proactive measures are crucial to mitigate the risks and ensure continued service availability. Effective prevention strategies involve a multi-layered approach encompassing network infrastructure, security protocols, and continuous improvement.
Network Infrastructure Hardening
Robust network infrastructure forms the first line of defense against DoS attacks. This involves strategically placing firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) at key points to monitor and filter malicious traffic. Proper configuration and regular maintenance of these systems are essential to maintain their effectiveness. Load balancing techniques distribute traffic across multiple servers, preventing overload on a single point.
- Implementing firewalls effectively involves configuring rules to block known malicious IP addresses, ports, and protocols. Regular updates to firewall rulesets are critical to maintain effectiveness against evolving attack vectors.
- Intrusion detection and prevention systems (IDS/IPS) can monitor network traffic in real-time for suspicious activity. They can identify and block malicious packets before they reach vulnerable systems.
- Load balancing distributes traffic across multiple servers, preventing a single point of failure and reducing the impact of DoS attacks. This can be achieved through hardware load balancers or software solutions.
Security Protocol Enhancements
Strengthening security protocols is another critical aspect of preventing DoS attacks. These protocols are designed to identify and mitigate malicious activity before it causes widespread disruption. Implementing strong authentication and access controls is vital. Regular security audits and penetration testing help identify vulnerabilities and weaknesses in security protocols.
- Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), helps prevent unauthorized access to systems and networks. This significantly reduces the risk of attackers exploiting vulnerabilities to launch DoS attacks.
- Enhancing network segmentation isolates critical systems and data, limiting the impact of a successful attack. This isolates the attack to a specific segment and prevents its spread throughout the network.
- Regular security audits and penetration testing can help identify vulnerabilities in security protocols. This process helps discover weaknesses that malicious actors might exploit.
DDoS Mitigation Strategies
Distributed denial-of-service (DDoS) attacks are a significant concern. Organizations must implement robust mitigation strategies to prevent these attacks from disrupting their services. These strategies often involve a combination of technical and operational approaches.
- Utilizing cloud-based DDoS protection services provides a scalable and cost-effective way to handle large-scale DDoS attacks. These services offer filtering and scrubbing capabilities to identify and mitigate attacks.
- Employing rate limiting and traffic shaping techniques helps manage the volume of incoming traffic. These techniques limit the rate at which packets are processed and can prevent overload situations. This approach can be implemented as a preventative measure, before the attack occurs.
- Working with internet service providers (ISPs) and security providers can provide crucial support during a DDoS attack. Collaboration allows for shared intelligence and resources to effectively counter the attack.
Continuous Security Improvement
A proactive approach to security is essential. Continuous security improvement is crucial to adapting to the evolving threat landscape. This includes regular security awareness training, incident response planning, and maintaining an updated security posture.
- Security awareness training programs educate employees about common security threats, including DoS attacks, and best practices for identifying and reporting suspicious activities.
- Establishing a comprehensive incident response plan Artikels procedures for detecting, containing, and recovering from security incidents, including DoS attacks. This ensures that organizations can respond effectively to these events.
- Regularly updating security software, operating systems, and security protocols ensures that systems are protected against known vulnerabilities. This helps maintain an effective defense against potential attacks.
Closing Summary: Denial Of Service Attack Brings Down Microsoft
In conclusion, the denial-of-service attack on Microsoft serves as a stark reminder of the ever-present threat of cyberattacks. The incident’s technical analysis, impact, and aftermath provide valuable insights into the complexities of such attacks and the measures organizations must take to protect themselves. Ultimately, the need for continuous security improvement and proactive measures is paramount in the face of increasingly sophisticated cyber threats.