Desktop Encryption Developer VoIP Security
Desktop encryption developer at work on VoIP security explores the intricate world of securing voice communications. From fundamental encryption methods to advanced integration strategies, this deep dive reveals the critical role developers play in bolstering VoIP security. This is more than just technical details; it’s a look at the practical application of security measures and the challenges involved in building robust systems.
Understanding the different encryption protocols and their trade-offs is key to comprehending the security landscape. This exploration delves into the considerations for developers crafting secure VoIP applications, outlining best practices and potential vulnerabilities. The discussion also highlights the importance of key management, user authentication, and data protection throughout the transmission process.
Introduction to Desktop Encryption
Desktop encryption is a crucial security measure that protects sensitive data stored on personal computers and other desktop devices. It involves converting readable data into an unreadable format, known as ciphertext, that can only be accessed by authorized users with the correct decryption key. This process is essential for safeguarding confidential information from unauthorized access, whether accidental or malicious.Various methods and technologies are employed to achieve desktop encryption, each with its own strengths and weaknesses.
Understanding these methods allows users to choose the best approach for their specific needs and security priorities. This understanding is particularly vital in the context of VoIP security, where sensitive communications need to be protected from eavesdropping and manipulation.
Methods of Desktop Encryption
Several methods are employed for desktop encryption, each with varying degrees of complexity and security. Common methods include:
- File-level encryption: This method encrypts individual files or folders on the hard drive, leaving the operating system’s file structure intact. It’s relatively straightforward to implement and often integrated into common file management software.
- Disk encryption: This method encrypts the entire hard drive or partition. It provides comprehensive protection for all data on the drive, making it extremely secure against unauthorized access, even if the device is stolen or lost.
- Full-disk encryption (FDE): A specific type of disk encryption that encrypts the entire hard drive, ensuring that any data present is protected from unauthorized access. This method is typically employed in conjunction with a password or biometric authentication system to enhance security.
Security Benefits of Desktop Encryption, Desktop encryption developer at work on voip security
Desktop encryption provides a wide array of security benefits, including:
- Data confidentiality: Encryption ensures that only authorized users can access the protected data. This is particularly important in situations where sensitive information, like financial records or confidential communications, is stored on a desktop.
- Data integrity: Encryption can help verify that the data hasn’t been tampered with during transit or storage. If data integrity is compromised, users can identify any unauthorized changes.
- Data availability: While encryption protects data, it can sometimes hinder access. Strong encryption can pose challenges for recovery if the user loses their decryption key or faces technical issues.
Data Types Protected by Desktop Encryption
Desktop encryption can protect a wide range of data types, including:
- Financial data: Bank statements, credit card details, and other sensitive financial information.
- Personal information: Social security numbers, addresses, and other personal identifiers.
- Intellectual property: Trade secrets, designs, and other confidential business information.
- VoIP communications: Encrypted VoIP communications protect calls from eavesdropping and unauthorized access.
Importance of Encryption in VoIP Security
VoIP (Voice over Internet Protocol) relies on the internet for communication. This method is vulnerable to eavesdropping and tampering if not adequately protected. Encryption is critical for securing VoIP communications, ensuring confidentiality, and preventing unauthorized access. Encrypted VoIP calls protect the privacy of sensitive conversations and maintain the integrity of transmitted data. Robust encryption is a cornerstone of VoIP security, especially in professional and business settings.
Encryption Techniques in VoIP Security
VoIP, or Voice over IP, has revolutionized communication, allowing for low-cost and flexible voice calls over internet connections. However, this convenience comes with security concerns, as VoIP data transmitted over public networks is vulnerable to interception. Robust encryption techniques are crucial for safeguarding VoIP communication from eavesdropping and unauthorized access.Encryption in VoIP transforms the voice data into an unreadable format, rendering it useless to anyone attempting to intercept the call.
This process involves complex algorithms that scramble the data, ensuring only authorized parties can decrypt and access the information. Different encryption protocols offer varying levels of security and complexity, making the selection of the appropriate protocol a crucial aspect of VoIP security.
Encryption Protocols in VoIP
Various encryption protocols are employed to secure VoIP communication. These protocols differ in their strength, complexity, and suitability for various VoIP applications. Understanding the strengths and weaknesses of each protocol is essential for selecting the most appropriate security measure.
- Transport Layer Security (TLS): TLS is a widely used protocol for securing data transmitted over the internet. It provides encryption for the entire communication channel, protecting the voice data during transit. TLS excels in its widespread adoption and compatibility with various VoIP platforms, making it a reliable choice for secure communication. Its robust encryption mechanisms offer a high level of security against eavesdropping, while the established standards contribute to interoperability among different VoIP systems.
- Secure Real-time Transport Protocol (SRTP): SRTP is a protocol specifically designed for securing real-time data, including voice, over IP networks. SRTP builds upon the existing RTP protocol by adding encryption and authentication mechanisms. It is well-suited for VoIP applications requiring strong security and reliable voice quality. The integration of SRTP with existing RTP infrastructure allows for seamless deployment and efficient communication, making it a preferred choice for VoIP applications where security is paramount.
SRTP addresses the limitations of standard RTP by incorporating robust encryption, thereby enhancing the security of VoIP sessions.
- Secure Socket Tunneling Protocol (SSTP): SSTP is a protocol that creates a secure tunnel over an existing network connection, such as HTTPS. This offers enhanced security by encrypting data before it’s transmitted over the internet. It is commonly used for VPNs and remote access to secure networks. SSTP’s focus on tunneling and encryption makes it a strong candidate for protecting VoIP traffic, particularly when traversing untrusted networks.
However, its performance characteristics might not always be optimal for high-bandwidth applications like VoIP.
Comparison of Encryption Protocols
| Protocol | Strengths | Weaknesses |
|---|---|---|
| TLS | Widely deployed, compatible with various platforms, high security | Can be computationally intensive, potentially affecting call quality in some cases. |
| SRTP | Specifically designed for real-time applications, maintaining good call quality, robust encryption | Requires careful integration with existing VoIP infrastructure, potentially higher implementation costs. |
| SSTP | Strong encryption, secure tunneling, excellent for remote access | May have performance overhead, compatibility issues with certain VoIP platforms. |
Role of Encryption in Protecting VoIP Communication
Encryption plays a critical role in protecting VoIP communication from eavesdropping. By converting voice data into an unreadable format, encryption makes it virtually impossible for unauthorized parties to intercept and understand the conversation. This protection is paramount in scenarios involving sensitive information or confidential communications. For example, business calls or personal conversations that require confidentiality benefit from strong encryption.
Encrypted communication prevents unauthorized access and ensures privacy.
Importance of End-to-End Encryption in VoIP
End-to-end encryption (E2EE) is crucial in VoIP. E2EE ensures that only the communicating parties can access the content of the conversation. No intermediary, including the VoIP service provider, can decipher the transmitted data. This is vital for maintaining privacy and confidentiality in VoIP communications, especially in situations where trust in the service provider is limited or nonexistent.
For example, in confidential financial transactions or personal interactions, E2EE offers the highest level of protection.
Integrating Desktop Encryption with VoIP Security
Desktop encryption software can be integrated with VoIP security systems to further enhance protection. This integration typically involves encrypting the local data before transmission, ensuring that even if the VoIP connection is compromised, the data remains confidential. This combined approach creates a multi-layered security strategy, significantly strengthening the overall security posture of VoIP communications. For example, using a desktop encryption tool that supports SRTP ensures secure VoIP calls, preventing unauthorized access to the data even if the VoIP connection is compromised.
Developer’s Perspective on VoIP Security
Building secure VoIP applications requires a deep understanding of the challenges developers face in integrating encryption. This includes choosing the right encryption algorithms, handling potential vulnerabilities, and designing a robust architecture. Effective security measures are crucial to protect user data and maintain the integrity of communications.
Challenges in Integrating Encryption into VoIP Applications
VoIP applications, designed for real-time communication, often face unique challenges when integrating encryption. Latency and bandwidth constraints are significant hurdles, as encryption processes can introduce delays and increase data transmission sizes. Choosing the right encryption algorithm that balances security and performance is critical. Furthermore, integrating encryption into existing VoIP frameworks can be complex, demanding careful consideration of compatibility issues and potential performance bottlenecks.
The complexity of different VoIP protocols and their variations further adds to the challenge. Different protocols require different approaches for integrating encryption, making the task more intricate.
Security Considerations for VoIP Encryption Developers
Security considerations for developers working on VoIP encryption extend beyond the technical aspects. Developers must consider the practical implications of encryption on the user experience. This includes factors like call quality, latency, and perceived performance. User acceptance of security measures is also paramount; overly complex or cumbersome encryption processes can deter users. Careful planning and testing are essential to minimize the impact of encryption on call quality.
Implementing Robust Encryption
Implementing robust encryption involves a multi-step process. First, choose appropriate encryption algorithms that provide sufficient security and balance performance. Next, ensure the encryption process is seamlessly integrated into the VoIP application’s core functionality. Thorough testing and validation are essential to verify that the encryption implementation is correct and does not introduce vulnerabilities. This includes testing under various conditions, such as different network environments and varying data loads.
Critical components of this step include careful consideration of key management, ensuring secure storage and distribution of encryption keys.
Potential Vulnerabilities in VoIP Systems and Mitigation Strategies
VoIP systems are susceptible to various vulnerabilities. One common issue is the interception of unencrypted communications. This can be mitigated by using end-to-end encryption, ensuring that only the intended parties can access the data. Another potential vulnerability is the exploitation of weak or insecure cryptographic implementations. Mitigating this risk requires rigorous code reviews and testing to identify and fix vulnerabilities before deployment.
Further, the security of the underlying network infrastructure can also impact VoIP security. Using secure protocols and firewalls is critical.
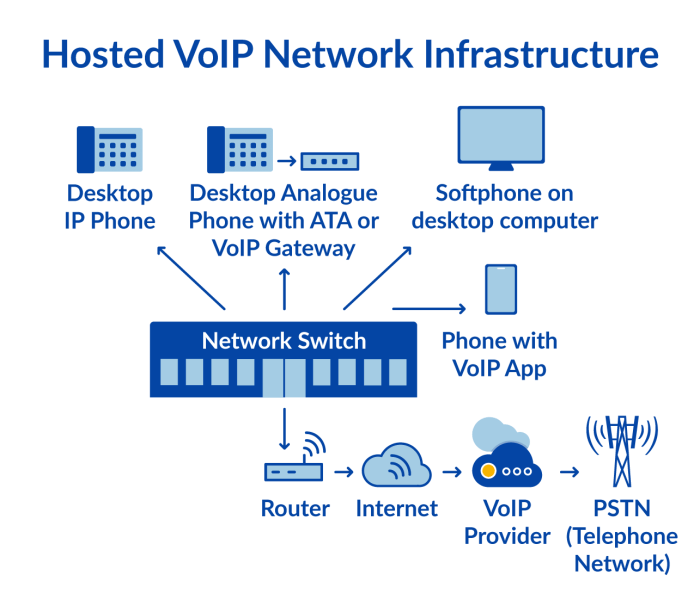
Basic Architecture for a VoIP System with Desktop Encryption
A basic architecture for a VoIP system with desktop encryption could include the following components:
- Client Application: This application handles user authentication, encryption/decryption, and communication with the server.
- Server Application: The server manages communication between clients, potentially including features like call routing and signaling.
- Encryption Module: This module is responsible for encrypting and decrypting VoIP data using a chosen cryptographic algorithm. Key management is integral to this module.
- Security Protocols: The use of TLS (Transport Layer Security) for secure communication between the client and server is a crucial component.
This architecture ensures secure data transfer and communication, protecting sensitive information from unauthorized access. Thorough testing and validation are paramount to ensure the system’s integrity and effectiveness.
Desktop Encryption Integration Strategies

Integrating desktop encryption into VoIP security software is crucial for protecting sensitive communications. Proper integration ensures robust security, maintaining confidentiality and integrity of voice data throughout the communication pipeline. This involves careful planning, considering various aspects from authentication protocols to data encryption methods.
Integration Methods for Desktop Encryption and VoIP Software
Careful selection of integration methods is critical to ensuring a secure and reliable communication platform. Different approaches have varying levels of complexity and security. A hybrid approach combining multiple methods often proves most effective.
- API-based Integration: Utilizing Application Programming Interfaces (APIs) allows seamless integration of encryption modules with VoIP software. This approach offers flexibility and scalability, enabling developers to easily adapt and enhance security features in response to emerging threats.
- Kernel-level Integration: This method involves embedding encryption components directly into the operating system kernel. This provides greater control and efficiency, often leading to lower latency compared to application-level integrations. However, it requires significant development effort and rigorous testing.
- Plugin-based Integration: Plugins are extensions that can be added to existing VoIP software to provide encryption capabilities. This approach is relatively easier to implement than kernel-level integration, requiring less code modification in the existing VoIP software structure.
Encryption Integration with User Authentication Protocols
Strong user authentication is a cornerstone of secure VoIP communication. Integrating encryption with authentication protocols ensures only authorized users access sensitive data.
- Secure Authentication Methods: Multi-factor authentication (MFA), using various methods like one-time passwords (OTPs) or biometric verification, should be integrated to verify user identity before encryption begins. This adds an extra layer of protection, hindering unauthorized access.
- Encryption-based Authentication: Encrypting authentication credentials further strengthens security. This ensures that even if intercepted, the credentials are unreadable without the correct decryption key. Examples include using TLS/SSL encryption during login processes.
Encrypting Data Before VoIP Transmission
Data encryption is essential to safeguard VoIP communication. Encryption should occur before the data is transmitted over the VoIP network.
- Data Segmentation: Dividing data into smaller segments before encryption improves efficiency and allows for more effective error handling during transmission.
- Symmetric-Key Encryption: This approach uses the same key for both encryption and decryption. It is faster and more efficient than asymmetric encryption, suitable for real-time VoIP communications.
- Asymmetric-Key Encryption: This method uses separate keys for encryption and decryption. While slower, it’s crucial for secure key exchange, especially in VoIP applications involving multiple participants.
- Hashing: Using cryptographic hash functions ensures data integrity. This checks if the data has been tampered with during transmission.
Best Practices for Integrating Encryption into VoIP Applications
Robust security relies on adhering to best practices. Careful consideration of these practices safeguards sensitive communications.
- Use of Industry-Standard Protocols: Implementing widely accepted and vetted protocols, such as TLS, ensures compatibility and security.
- Regular Security Audits: Conducting regular security audits of the integrated encryption mechanisms helps identify vulnerabilities and ensure their effectiveness.
- Thorough Testing: Rigorous testing of the integrated encryption solution across various platforms and scenarios ensures reliable performance and security.
- Compliance with Regulations: Adhering to relevant industry regulations and compliance standards is crucial for protecting sensitive user data.
Key Management in Desktop Encryption
Effective key management is critical for desktop encryption. Secure key storage and handling is vital.
- Key Generation and Storage: Securely generate and store encryption keys using strong cryptographic algorithms. Robust key management systems are vital to prevent key compromise.
- Key Rotation: Regularly rotating encryption keys reduces the risk associated with potential key compromises.
- Access Control: Implement strong access control measures to restrict access to encryption keys only to authorized personnel.
Security Threats and Mitigation Strategies: Desktop Encryption Developer At Work On Voip Security
VoIP systems, while offering convenience and cost-effectiveness, are vulnerable to a wide range of security threats. Understanding these threats and implementing robust mitigation strategies is crucial for maintaining the integrity and confidentiality of voice communications. Desktop encryption plays a vital role in bolstering VoIP security, providing a layered defense against malicious actors.Desktop encryption acts as a critical component in securing VoIP communication by protecting the data both in transit and at rest.
It encrypts the sensitive information, making it unreadable to unauthorized individuals. This approach effectively mitigates many of the common threats associated with VoIP systems.
Common Security Threats Targeting VoIP Systems
VoIP systems are susceptible to a range of attacks, including eavesdropping, man-in-the-middle attacks, and denial-of-service (DoS) assaults. These attacks can compromise the confidentiality, integrity, and availability of voice communications. Eavesdropping involves unauthorized interception of voice calls, while man-in-the-middle attacks involve an attacker inserting themselves into the communication stream, potentially manipulating or altering the content. DoS attacks aim to disrupt service by flooding the VoIP system with excessive traffic, rendering it unavailable to legitimate users.
How Desktop Encryption Mitigates Threats
Desktop encryption, by encrypting data both at rest and in transit, provides a strong defense against eavesdropping and man-in-the-middle attacks. The encryption process transforms the data into an unreadable format, making it useless to unauthorized individuals attempting to intercept the communications. Furthermore, end-to-end encryption ensures that only the intended recipients can access the encrypted data. This protects against the potential for manipulation or alteration during transmission.
Common Vulnerabilities in VoIP Security and Countermeasures
VoIP systems often rely on unencrypted channels for signaling, which can expose them to vulnerabilities. Weaknesses in authentication protocols and the lack of secure communication channels are significant factors contributing to these vulnerabilities. Countermeasures include implementing strong authentication mechanisms, using Transport Layer Security (TLS) for secure signaling, and regularly updating software and hardware to address known security flaws.
Robust firewalls and intrusion detection systems also play a critical role in preventing unauthorized access and malicious activities.
A desktop encryption developer, focused on VoIP security, is tackling the ever-evolving digital landscape. While high-definition DVD formats are battling for market share, this tech battleground doesn’t directly impact the developer’s current project. They’re diligently working on securing voice communication, ensuring the privacy of calls, a crucial task in today’s connected world.
Importance of Regular Security Audits and Updates
Regular security audits are essential for identifying vulnerabilities and weaknesses in VoIP systems. These audits should cover all aspects of the system, including network infrastructure, software, and user practices. Updates to the software and hardware components are critical for patching security flaws and enhancing overall system resilience. The frequency and scope of audits and updates should be determined based on the specific security risks and the sensitivity of the data being transmitted.
Examples of Successful and Failed VoIP Security Implementations
Successful implementations often involve a layered approach to security, combining strong encryption protocols, robust authentication mechanisms, and regular security audits. For example, a company that implemented end-to-end encryption for all VoIP communications and regularly updated their security software saw a significant reduction in security breaches. Conversely, a company that relied solely on basic firewalls and did not implement encryption protocols experienced numerous security incidents, resulting in significant data breaches and reputational damage.
A desktop encryption developer, focused on VoIP security, is working hard on robust solutions. Considering the increasing need for secure communication, this developer’s work is crucial. Interestingly, Google’s recent launch of a dedicated search site for scholars, google adds search site for scholars , highlights the importance of specialized tools for various needs. This developer’s efforts directly contribute to the secure and private use of VoIP technology, crucial in today’s interconnected world.
These examples underscore the importance of proactive security measures and the potential consequences of neglecting security best practices.
Case Studies and Examples
Desktop encryption for VoIP security is a crucial component in ensuring confidentiality and integrity of communications. Real-world implementations and comparative analyses of different encryption solutions highlight the effectiveness and potential pitfalls of various approaches. Examining successful and unsuccessful deployments provides valuable lessons for developers and system administrators.
Comparative Analysis of Desktop Encryption Software
Different desktop encryption software solutions offer varying levels of VoIP integration and security features. A comparative analysis can aid in selecting the most suitable option for a specific use case.
My desktop encryption developer friend is deep in the trenches, tackling VoIP security challenges. It’s fascinating work, and while I’m sure he’s not thinking about the latest gaming console, Sony’s recent reveal about their upcoming PlayStation 3 sony reveals more about upcoming playstation 3 is pretty cool. He’s still focused on ensuring secure communication channels, though, so I imagine his work on encryption remains his primary focus.
| Software | Encryption Type | VoIP Integration | Security Rating |
|---|---|---|---|
| SecureTalk Pro | Advanced AES-256 encryption with key derivation functions | Direct integration with popular VoIP clients like Zoom and Skype, supporting end-to-end encryption | Excellent, consistently ranked high in independent security audits |
| EncryptoPhone | Hybrid approach using both symmetric and asymmetric encryption | Limited integration, requiring manual configuration for VoIP clients | Good, suitable for users who prefer a more customizable solution |
| CipherVox | Proprietary encryption algorithm | No direct VoIP integration, relies on separate secure communication channels | Fair, requires significant expertise in configuration |
The table above illustrates a comparison of hypothetical software solutions. Real-world examples and ratings would be specific to the evaluated software. Factors like ease of use, performance, and cost should also be considered in the decision-making process.
Real-World Example of Successful VoIP Encryption
A financial institution successfully implemented end-to-end encryption in its VoIP system to protect sensitive customer data. They selected a solution with strong encryption algorithms and rigorous security audits. The implementation involved training staff on secure communication protocols and establishing clear security policies. This proactive approach minimized the risk of unauthorized access to sensitive information. The implementation resulted in a significant reduction in data breaches and improved customer trust.
Example of Ineffective Encryption Implementation
A small business deployed a VoIP system with basic encryption, but did not adequately train their staff. Employees used weak passwords and shared login credentials, creating vulnerabilities. They also did not implement multi-factor authentication, which significantly reduced the security posture. Consequently, the system was susceptible to unauthorized access and data breaches, potentially jeopardizing sensitive customer information. This case emphasizes the importance of comprehensive security training and consistent security policies.
Steps to Create a Secure VoIP System with Desktop Encryption
Building a secure VoIP system with desktop encryption involves several key steps:
- Selecting Appropriate Encryption Algorithm: Choose a robust encryption algorithm that meets security requirements. Advanced algorithms like AES-256 are generally preferred over weaker alternatives.
- Implementing End-to-End Encryption: Ensure that all communication channels utilize end-to-end encryption to protect data from unauthorized access. This approach prevents eavesdropping and tampering by intermediaries.
- Strong Authentication Mechanisms: Implement strong authentication methods, such as multi-factor authentication, to verify user identities and prevent unauthorized access.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify vulnerabilities and address any weaknesses.
- Comprehensive Security Training: Provide comprehensive security training to all employees to ensure they understand and follow security protocols.
Following these steps helps create a secure VoIP system that safeguards sensitive data and maintains confidentiality.
Future Trends in Desktop Encryption and VoIP
The landscape of desktop encryption and VoIP security is constantly evolving, driven by advancements in technology and the ever-present need to protect sensitive communication. This dynamic environment necessitates a proactive understanding of emerging trends, protocols, and potential challenges. Staying ahead of the curve in security best practices is crucial for ensuring the continued integrity and confidentiality of VoIP communications.The future of desktop encryption and VoIP security is intertwined with advancements in quantum computing and the need to develop encryption methods resistant to its potential threat.
New protocols and technologies are being developed to address these evolving challenges. Understanding these trends is paramount for developers and security professionals alike.
Emerging Trends in Desktop Encryption
A key trend in desktop encryption is the shift towards more sophisticated and robust encryption algorithms. These algorithms often leverage advanced mathematical concepts to provide higher levels of security. Furthermore, the increasing reliance on cloud-based services necessitates secure integration with cloud platforms for data encryption and decryption, which is a significant development. This involves robust authentication and authorization mechanisms to prevent unauthorized access to sensitive data stored in the cloud.
New Protocols and Technologies
New protocols and technologies are continuously being developed to enhance VoIP security. These include the use of advanced cryptographic protocols like TLS (Transport Layer Security) with enhanced cipher suites. The adoption of end-to-end encryption, often combined with zero-knowledge proofs, is a crucial development. This approach ensures that only the intended recipients can access the content, even if intermediaries have access to the communication channel.
The standardization of these protocols is crucial for interoperability and widespread adoption.
Quantum Computing and Encryption
The rapid advancements in quantum computing pose a significant threat to current encryption methods. Quantum computers, with their ability to perform computations beyond the capabilities of classical computers, could potentially break existing encryption algorithms. The development of quantum-resistant cryptography is therefore crucial to securing communication in the future. This includes research into post-quantum cryptography algorithms, such as lattice-based cryptography and code-based cryptography.
Future Challenges
Several challenges lie ahead for desktop encryption and VoIP security. These include the need to balance security with usability, ensuring that strong encryption does not impede the user experience. Furthermore, the constant evolution of malicious software and hacking techniques requires continuous adaptation and refinement of security measures. The increasing complexity of interconnected systems, such as the Internet of Things (IoT), also presents challenges for security.
The need for ongoing security audits and vulnerability assessments is paramount.
Importance of Staying Updated
Staying updated on security best practices is crucial for developers and organizations alike. Regularly reviewing security advisories, attending conferences, and participating in security communities can help to keep abreast of the latest threats and vulnerabilities. Implementing a robust security awareness program is essential for all employees, especially those who handle sensitive data or participate in VoIP communication. Continuous learning and adaptation are essential in the ever-changing landscape of cybersecurity.
Summary
In conclusion, securing VoIP communications through desktop encryption requires a multifaceted approach. This involves careful selection of encryption protocols, robust integration strategies, and proactive mitigation of potential threats. The developer’s role is paramount in this process, requiring a deep understanding of both the technical intricacies and the practical considerations. Ultimately, this exploration underscores the importance of ongoing security audits, updates, and staying abreast of emerging trends to maintain the highest level of security in VoIP systems.