DRM vs ERM Your Datas Fight for Control
Drm vs erm the battle for control of your data – DRM vs ERM: the battle for control of your data. In today’s digital landscape, data is king, but who controls it? This deep dive explores the intricacies of Data Rights Management (DRM) and Enterprise Resource Management (ERM), dissecting how these systems shape your data’s destiny. We’ll examine the fundamental differences in ownership, security protocols, access management, and compliance implications, ultimately helping you understand how these powerful tools interact and impact your organization.
From defining the core concepts to exploring future trends, we’ll unpack the complexities of DRM and ERM. We’ll analyze the challenges and benefits of implementing these systems, drawing on real-world examples and highlighting the critical role data governance plays in ensuring your organization’s data security and compliance.
Defining Data Control
Data control, a critical aspect of modern information management, encompasses the policies, procedures, and technologies used to govern how data is accessed, used, and protected. Two key players in this arena are Data Rights Management (DRM) and Enterprise Resource Management (ERM). Understanding their individual roles and their interplay is crucial for organizations seeking to maintain data integrity and compliance.Data control, in essence, is about establishing clear lines of responsibility and authority over data assets.
This involves defining who can access specific data, what they can do with it, and how it should be secured. Different approaches to data control, such as DRM and ERM, address these issues from unique perspectives.
Data Rights Management (DRM)
Data Rights Management (DRM) focuses on controlling access and use of specific digital content. It is primarily concerned with intellectual property protection and preventing unauthorized copying or distribution. DRM systems often employ encryption, digital signatures, and watermarks to restrict access and track usage. This ensures the rightful owner maintains control over their data.
Enterprise Resource Management (ERM)
Enterprise Resource Management (ERM) is a broader system for managing an organization’s resources, including data. It integrates various departments and processes, such as finance, human resources, and supply chain management. ERM systems aim to improve operational efficiency, enhance decision-making, and streamline data flows within an organization. While DRM is focused on protecting specific digital assets, ERM manages the overall data flow within the enterprise.
Differences in Data Ownership and Access
DRM and ERM differ fundamentally in their approach to data ownership and access. DRM focuses on the rights of the data owner to control how their specific data is used. ERM, on the other hand, focuses on the overall flow of data within the organization. DRM emphasizes granular control over specific data items, while ERM aims for smooth integration and flow of data across various departments.
Interaction and Influence
DRM and ERM systems interact and influence each other in several ways. ERM systems can leverage DRM technologies to protect sensitive data within the overall enterprise resource management framework. For instance, sensitive financial data can be protected by DRM measures within an ERM system. Similarly, DRM systems can benefit from ERM systems by ensuring that the data used to control access is accurate and readily available.
Comparison of DRM and ERM
| Feature | Data Rights Management (DRM) | Enterprise Resource Management (ERM) |
|---|---|---|
| Primary Focus | Protecting specific digital assets and controlling their use. | Managing the overall flow of data and resources within an enterprise. |
| Scope | Specific digital content (e.g., documents, videos, software). | Entire organization’s data and resources. |
| Access Control | Granular control over access based on specific rights. | Broader access control based on roles and responsibilities within the organization. |
| Integration | Often integrated with specific applications. | Integrated with multiple enterprise systems. |
| Example Use Cases | Protecting copyrighted material, controlling access to sensitive documents. | Managing inventory, tracking customer relationships, handling financial transactions. |
Data Ownership and Security: Drm Vs Erm The Battle For Control Of Your Data
Data ownership and security are paramount in the ongoing battle between DRM and ERM. Understanding how data is owned and protected is crucial for navigating the complex landscape of digital rights and access. Effective strategies for managing data rights, combined with robust security measures, are essential for mitigating risks and ensuring the responsible use of information.Data ownership models, ranging from centralized to decentralized approaches, significantly impact the security and control of information.
This is further complicated by the varying needs of different stakeholders and the potential for conflicting interests. Implementing robust security protocols is a critical aspect of any data management strategy, regardless of the specific ownership model.
Data Ownership Models in DRM and ERM
Different data ownership models have implications for the level of control and access various stakeholders have over data. Centralized models often give a single entity complete control, which can be efficient but may not account for the needs of individuals or smaller groups. Decentralized models, conversely, can give more control to individuals and groups but may require more complex governance structures.
Hybrid models combine elements of both, aiming to balance efficiency with stakeholder needs. The choice of model should be carefully considered based on the specific context and goals.
Security Protocols in DRM and ERM Implementations
Implementing robust security protocols is crucial for both DRM and ERM strategies. These protocols should encompass a range of measures to protect data from unauthorized access, use, disclosure, disruption, modification, or destruction. Strong passwords, multi-factor authentication, encryption, and regular security audits are fundamental components of a comprehensive security strategy. Access controls, determined by data sensitivity and user roles, help regulate access to specific data assets.
The ongoing debate around DRM vs. ERM, the struggle for data control, is fascinating. It’s like a digital arms race, where companies constantly try to secure their data, but also often create convoluted systems. This echoes the problems of legacy systems in the tech world, like those explored in the excellent article “Baby Apples II: The Curse of Xerox” baby apples ii the curse of xerox.
Ultimately, the quest for user control in this DRM vs. ERM battle is still a significant challenge, regardless of how clever the technical solutions are.
Examples of Successful DRM and ERM Strategies
Successful DRM and ERM strategies often involve a combination of technical solutions and organizational policies. For example, a company managing medical records might utilize encryption and access controls combined with strict user access policies. A content creation company might use DRM to protect intellectual property rights while also using ERM principles to enable secure collaboration among team members.
These examples illustrate how different strategies can be tailored to meet specific business needs.
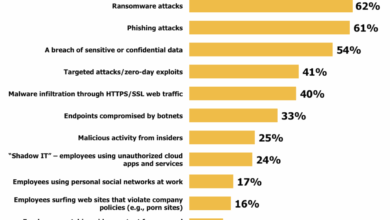
Security Threats to Data in DRM and ERM
Data security is constantly challenged by various threats. A robust security strategy must address these threats proactively.
Ever wondered about DRM vs. ERM, the ongoing battle for data control? It’s a fascinating concept, especially when you consider its parallels in the high-tech world of Formula One racing. Teams are constantly pushing the boundaries of engineering and technology, like those innovative high-tech companies that fuel the sport, and the constant drive for optimization mirrors the complexities of managing and securing data.
Understanding the intricacies of DRM and ERM is crucial in navigating this data-driven landscape, whether you’re a Formula One team or an individual. The intense competition in formula one racing and high tech companies reveals the crucial importance of effective data management strategies. Ultimately, both concepts boil down to controlling your digital assets and safeguarding your data, in a modern world that is increasingly digital.
| Threat Category | Description | DRM Implications | ERM Implications |
|---|---|---|---|
| Unauthorized Access | Gaining access to data without proper authorization. | Preventing unauthorized access to copyrighted content. | Preventing unauthorized access to sensitive company data. |
| Malware Attacks | Infections that compromise data or systems. | Protecting digital content from malicious code. | Protecting company systems and data from ransomware or viruses. |
| Data Breaches | Compromise of data through vulnerabilities or hacking. | Preventing leaks of protected content. | Protecting confidential customer data. |
| Phishing Attacks | Tricking users into revealing sensitive information. | Preventing users from falling victim to phishing attempts. | Training employees to avoid phishing attacks. |
| Insider Threats | Malicious or accidental actions by authorized personnel. | Monitoring access patterns of employees handling protected content. | Restricting access based on roles and responsibilities, ensuring strong access controls. |
Data Access and Usage
Unlocking the potential of your data hinges on carefully controlled access and usage. Effective data management systems, whether DRM or ERM, dictate who can access specific data, what they can do with it, and under what conditions. This crucial aspect ensures data integrity, compliance, and security, ultimately protecting sensitive information. Different approaches in DRM and ERM impact how data is handled, and a thorough understanding of these nuances is paramount for organizations.Data access and usage are critical for both DRM (Digital Rights Management) and ERM (Enterprise Resource Management) systems.
These systems employ distinct strategies for controlling access, based on the nature of the data and the organization’s specific needs. Understanding these differences is essential to choosing the right approach and maintaining control over valuable information.
DRM System Access Control
DRM systems, designed primarily for managing digital content, typically employ granular access control mechanisms. These systems meticulously define who can access specific files, what actions they can perform (e.g., view, download, print), and under what circumstances. The level of access is often tied to specific user roles and their permissions, preventing unauthorized use of copyrighted material or proprietary information.
ERM System Access Control
ERM systems, on the other hand, focus on managing data across the entire organization. Access control in ERM is often more multifaceted, considering not only individual users but also departments, teams, and even specific business processes. This necessitates a more comprehensive approach to data access management, incorporating policies and procedures to ensure data accuracy, consistency, and availability for authorized personnel.
User Roles and Permissions
User roles and permissions are fundamental to both DRM and ERM systems. These systems assign specific roles (e.g., administrator, editor, viewer) to users, granting them corresponding access privileges. This structured approach allows for fine-grained control over data access, preventing unauthorized modifications or deletions.
Data Governance in DRM and ERM
Effective data governance is paramount in both DRM and ERM systems. Clear policies and procedures are needed to define data ownership, access rights, and usage guidelines. This framework ensures that data is managed responsibly and securely throughout its lifecycle, aligning with legal and regulatory requirements. This is crucial for maintaining trust in the data.
Comparison of Data Access Management Approaches
| User Role | DRM Access Privileges | ERM Access Privileges ||—|—|—|| Administrator | Full access to all content, including creation, modification, and deletion; enforcement of policies. | Full access to all data; can manage user roles, permissions, and system configurations. || Editor | Limited access to modify content; typically restricted by permissions and approval workflows. | Ability to modify data within their assigned area; adherence to established procedures.
|| Viewer | Limited access to view content; restricted from making changes or modifications. | Ability to access data for analysis and reporting; typically read-only access. || Guest | Limited access to view specific content or portions of a resource, determined by the content owner. | Limited access to data based on specific requirements, such as temporary access or guest user roles.
|
Compliance and Legal Aspects
Navigating the digital landscape requires a keen understanding of the legal and regulatory frameworks governing data management. This is particularly crucial for organizations employing Digital Rights Management (DRM) and Enterprise Resource Management (ERM) systems, as these systems often hold sensitive information subject to various laws and regulations. Proper compliance ensures not only legal adherence but also builds trust with stakeholders and mitigates potential risks.
Legal and Regulatory Requirements for Data Management
Organizations using DRM and ERM systems must adhere to a complex web of legal and regulatory requirements. These requirements vary by jurisdiction and often overlap, encompassing data protection, privacy, and security laws. Failure to comply can lead to significant penalties, including hefty fines and reputational damage. Understanding these specific requirements is paramount to avoid such issues.
Data Privacy Laws and DRM/ERM
Data privacy laws, such as GDPR in Europe, CCPA in California, and others globally, directly impact how organizations handle data within DRM and ERM systems. These laws often mandate specific data processing practices, including obtaining informed consent, limiting data collection, and ensuring data security. Organizations must implement robust procedures to comply with these requirements, and these procedures must be adaptable and responsive to changing legal landscapes.
Importance of Compliance for Organizations
Compliance with data regulations is vital for organizations employing DRM and ERM systems. It safeguards sensitive data, builds trust with customers and stakeholders, and helps avoid costly legal battles. A robust compliance program ensures the smooth operation of these systems while minimizing risks. It also helps maintain a positive public image and fosters a culture of ethical data handling.
Penalties for Non-Compliance with Data Regulations
Non-compliance with data regulations can result in severe penalties, ranging from substantial fines to legal action and reputational damage. The magnitude of these penalties can be substantial, affecting an organization’s financial stability and operational efficiency. Furthermore, non-compliance can harm customer trust and lead to negative media attention.
Table of Relevant Data Privacy Regulations Worldwide
| Regulation | Jurisdiction | Key Aspects |
|---|---|---|
| General Data Protection Regulation (GDPR) | European Union | Comprehensive data protection framework; strong emphasis on data subject rights (e.g., right to access, rectification, erasure); strict requirements for data security and transfer. |
| California Consumer Privacy Act (CCPA) | California, USA | Focuses on consumer rights regarding their personal information; empowers consumers with rights to access, delete, and opt-out of the sale of their data. |
| Personal Information Protection and Electronic Documents Act (PIPEDA) | Canada | Establishes principles for the protection of personal information collected, used, and disclosed in the course of commercial activities; emphasizes consent and accountability. |
| Brazilian General Data Protection Law (LGPD) | Brazil | Promotes the protection of personal data of individuals; mandates data security and establishes obligations for data controllers. |
| Singapore Personal Data Protection Act (PDPA) | Singapore | Provides a framework for the protection of personal data; includes provisions for data security, consent, and accountability. |
Implementing DRM and ERM
Navigating the complexities of data control requires a well-defined implementation strategy for both Digital Rights Management (DRM) and Enterprise Resource Management (ERM) systems. Effective implementation goes beyond simply installing software; it involves meticulous planning, careful data migration, comprehensive training, and seamless integration with existing business processes. A robust implementation strategy ensures that these systems effectively achieve their intended goals of securing data and streamlining business operations.Implementing a DRM or ERM system is a multi-phased process requiring careful consideration of various factors.
The initial phase focuses on defining specific requirements, conducting a thorough risk assessment, and choosing the appropriate technologies. This is followed by the migration of existing data to the new system, employee training, and the final integration with other business systems. This iterative approach ensures a smooth transition and minimizes disruption to existing operations.
Defining System Requirements
Defining the specific requirements for a DRM or ERM system is crucial for a successful implementation. This involves identifying the types of data needing protection, the access levels required, and the compliance standards to be met. Thorough documentation and communication are essential for a clear understanding of the system’s purpose and functionality. A comprehensive list of requirements serves as a blueprint for the entire implementation process.
Data Migration
Migrating existing data to a new DRM or ERM system is a complex process that demands careful planning and execution. The process involves extracting data from the source system, transforming it to meet the new system’s format, and loading it into the target system. This necessitates meticulous testing to ensure data integrity and accuracy throughout the migration process.
Regular data backups and a recovery plan are crucial to mitigate potential risks during the migration.
Employee Training
Effective training programs are essential for ensuring that employees understand and use the new DRM or ERM system correctly. The training should cover the system’s functionalities, security protocols, and compliance requirements. Interactive workshops and hands-on exercises help employees become proficient in utilizing the system. Continuous training and support are essential to maintain employee competency.
Integration with Other Systems
Integrating DRM and ERM systems with other business systems ensures seamless data flow and optimal efficiency. This integration requires careful planning and technical expertise to connect the various systems and ensure data consistency and accuracy. Interface specifications and protocols should be well-defined and thoroughly tested to guarantee smooth interaction between systems. This approach minimizes the risk of data inconsistencies and ensures that data flows seamlessly throughout the organization.
Implementation Flow Chart (DRM System)

This image would illustrate the steps involved in implementing a DRM system, starting from defining requirements, through data migration, training, integration, and testing. It would visually represent the sequential and iterative nature of the process.
Benefits and Challenges
The digital age has brought unprecedented opportunities for data management, but also significant challenges regarding data control, ownership, and security. Effective data management requires robust systems, and Digital Rights Management (DRM) and Enterprise Resource Management (ERM) systems play a critical role in addressing these concerns. Implementing these systems can be complex, but the potential benefits for organizations are substantial.Implementing DRM and ERM systems can enhance data security and streamline data management processes, leading to improved operational efficiency and reduced risks.
However, organizations must carefully consider the potential challenges and develop strategies to overcome them. This section explores the advantages, challenges, and solutions associated with implementing DRM and ERM systems, drawing on real-world examples.
Advantages of DRM and ERM Systems, Drm vs erm the battle for control of your data
Effective DRM and ERM systems offer significant advantages for organizations managing sensitive data. These systems help to secure data, control access, and ensure compliance with regulations. Streamlining processes and improving efficiency are also key benefits.
- Enhanced Data Security: DRM systems restrict unauthorized access and use of data, safeguarding sensitive information. ERM systems can help automate and centralize security policies, minimizing the risk of data breaches and leaks. For example, a financial institution using DRM to protect customer account information can significantly reduce the likelihood of fraudulent activity. This, in turn, improves customer trust and brand reputation.
- Improved Data Access Control: DRM and ERM systems provide granular control over who can access specific data, ensuring that only authorized personnel can view and modify information. This prevents accidental or malicious data disclosure, improving data privacy and compliance. A healthcare organization using ERM to manage patient data can ensure that only authorized doctors and nurses have access to specific patient records, adhering to HIPAA regulations.
- Increased Operational Efficiency: ERM systems can streamline data management processes, reducing manual tasks and improving efficiency. This translates into cost savings and increased productivity. For example, a manufacturing company using ERM to manage inventory and production data can optimize resource allocation and reduce waste, leading to increased profitability.
- Enhanced Regulatory Compliance: Implementing DRM and ERM systems helps organizations comply with data privacy regulations (like GDPR or CCPA) and other relevant laws. This minimizes legal risks and ensures compliance with industry standards, maintaining a positive public image.
Challenges of Implementing DRM and ERM Systems
While the advantages are compelling, implementing DRM and ERM systems can present several challenges. Cost, complexity, and integration issues are common hurdles.
- High Implementation Costs: Developing and implementing DRM and ERM systems can be expensive, requiring significant investment in software, hardware, and personnel training. Organizations must carefully assess the costs against the expected benefits to ensure a positive return on investment (ROI). This is especially true for smaller organizations with limited budgets.
- Complexity and Integration Issues: Integrating DRM and ERM systems with existing infrastructure can be complex and time-consuming. This can involve significant technical expertise and specialized personnel. Issues like compatibility problems with legacy systems can further complicate the process.
- Resistance to Change: Implementing new systems often faces resistance from employees who are accustomed to existing workflows. Effective change management strategies are crucial to ensuring smooth adoption and avoiding disruption. Comprehensive training programs and clear communication are vital to overcome employee resistance.
- Data Security Risks during Transition: The transition period to a new DRM or ERM system can create vulnerabilities if not properly managed. Careful planning and execution are critical to minimizing risks during this period. Regular security audits and monitoring are necessary to ensure the new system’s effectiveness.
Overcoming Implementation Challenges
Several strategies can help organizations overcome the challenges associated with implementing DRM and ERM systems. Careful planning, adequate resources, and clear communication are crucial.
- Phased Implementation: Implementing the system in phases allows organizations to address potential issues gradually and minimize disruptions to existing operations. This approach provides opportunities to refine processes and address any challenges that arise.
- Comprehensive Training Programs: Adequate training for employees on using the new DRM and ERM systems is crucial to ensure successful adoption and minimize resistance. Training should be tailored to different roles and responsibilities to ensure maximum impact.
- Collaboration and Communication: Open communication and collaboration between IT departments, business units, and stakeholders are vital to ensure everyone understands the system’s purpose and benefits. This fosters buy-in and facilitates smooth integration.
- Regular Security Audits: Conducting regular security audits and vulnerability assessments is essential to identify and address any potential issues with the new system, preventing potential breaches and protecting sensitive data.
Real-World Case Studies
Several organizations have successfully implemented DRM and ERM systems, achieving significant improvements in data management and security. For example, a large healthcare provider successfully implemented an ERM system to manage patient data, reducing data breaches and improving regulatory compliance.
Ever wondered about the struggle between DRM and ERM in controlling your data? It’s a constant battle for ownership and access. IBM workshops, like these ones designed to help ISVs sell grids , highlight the need for better data management, and in turn, a more controlled approach to data security. Ultimately, understanding these complex issues is crucial for ensuring your data remains safe and usable, making the DRM vs ERM debate more than just a theoretical exercise.
- Financial Institution Example: A major bank successfully implemented a DRM system to protect sensitive financial data. This led to a substantial reduction in fraud and improved compliance with regulatory requirements.
- Healthcare Provider Example: A leading healthcare organization successfully implemented an ERM system to manage patient records, improving efficiency and compliance with HIPAA regulations.
Summary Table
| Factor | Advantages | Disadvantages |
|---|---|---|
| Data Security | Enhanced protection against breaches and unauthorized access. | Potential for increased complexity in security protocols. |
| Compliance | Improved adherence to regulations and standards. | Potential for high implementation costs and lengthy transition periods. |
| Efficiency | Streamlined processes and reduced manual tasks. | Resistance to change from employees used to existing workflows. |
| Cost | Potential for long-term cost savings through efficiency gains. | High initial investment in software, hardware, and training. |
Future Trends in Data Control
The landscape of data control is rapidly evolving, driven by technological advancements and increasing regulatory pressures. Understanding the future direction of data management technologies is crucial for organizations to adapt and thrive in this dynamic environment. This section explores the emerging trends shaping the future of data control, focusing on the pivotal roles of AI, cloud computing, and emerging technologies.
AI and Machine Learning in DRM and ERM
Artificial intelligence (AI) and machine learning (ML) are poised to revolutionize data control mechanisms. AI-powered systems can analyze vast datasets to identify patterns, anomalies, and potential threats, enabling proactive security measures. This predictive capability enhances the effectiveness of both DRM and ERM. For instance, AI algorithms can detect unusual access patterns, flag suspicious data modifications, and even predict potential data breaches.
This proactive approach significantly strengthens the overall security posture. ML models can also automate tasks like data classification and access control, freeing up human resources for more strategic initiatives.
Cloud Computing’s Impact on Data Control
Cloud computing is fundamentally altering how data is stored, managed, and accessed. The decentralized nature of cloud environments presents both opportunities and challenges for data control. The centralized management and security protocols offered by cloud providers can streamline data access and compliance processes. However, data sovereignty and security in multi-tenant cloud environments require robust governance and security measures.
This includes implementing strong access controls, encryption protocols, and secure data transfer mechanisms. Organizations need to carefully assess the security measures and compliance standards of the cloud provider to ensure their data is adequately protected.
Emerging Technologies Shaping the Future of Data Control
Emerging technologies, including blockchain and quantum computing, are impacting the data control landscape. Blockchain technology, with its decentralized and immutable nature, can enhance data integrity and transparency. This capability can help establish trust in data provenance and reduce the risk of tampering. Quantum computing, while still in its early stages, has the potential to significantly impact data encryption and decryption.
However, this also raises concerns about the potential vulnerability of current encryption methods to future quantum attacks. Organizations must prepare for these advancements and adjust their strategies accordingly.
Timeline of Data Control Technology Evolution
| Year | Technology | Description | Impact ||—|—|—|—|| 1970s | Relational Databases | Structured data storage | Improved data organization and access || 1990s | Data Warehousing | Centralized data storage | Enhanced data analysis and reporting || 2000s | Cloud Computing | Decentralized data storage | Increased scalability and accessibility || 2010s | Big Data Analytics | Handling large datasets | Deeper insights and improved decision-making || 2020s | AI and Machine Learning | Automated data analysis and control | Proactive security and enhanced efficiency || 2030s | Quantum Computing | Potential to impact encryption | Significant security implications |
Ultimate Conclusion

In conclusion, the battle for control of your data through DRM and ERM is multifaceted and demanding. Understanding the nuances of these systems, from ownership models to compliance, is crucial for navigating the digital age. This discussion highlighted the importance of careful planning, robust security measures, and a commitment to data governance for organizations seeking to leverage the power of their data effectively.
The future of data control promises exciting advancements, particularly with AI and cloud integration, requiring continuous adaptation and vigilance.