Feds Nab Blaster Suspect; Tracking SoBig F Writer
Feds nab blaster suspect continue tracking sobig f writer. This case involves a significant cybercrime investigation, where authorities are pursuing a suspect alleged to be connected to the SoBig.F malware. Law enforcement has apprehended a key figure, and ongoing investigations are focusing on uncovering the full scope of the suspect’s activities. The investigation delves into the complex world of cybercrime, highlighting the meticulous process of tracking and apprehending individuals involved in malicious online activities.
The investigation into the suspect’s background reveals potential connections to similar cybercrimes. Early stages of the investigation suggest the suspect may have been involved in multiple instances of malware distribution. This case exemplifies the ongoing struggle between cybercriminals and law enforcement, showcasing the dedication and skill of those combating online threats.
Feds Nab Blaster Suspect; Continue Tracking SoBig F Writer
Recent reports indicate a significant development in the ongoing investigation surrounding the SoBig F malware campaign. Law enforcement agencies have apprehended a suspect believed to be connected to the distribution of the malicious software. This arrest marks a crucial step in combating the widespread cybercrime and ensuring accountability for those responsible.
Summary of the Event
Authorities have successfully apprehended a key figure suspected in the distribution of the SoBig F worm, a notorious piece of malware that caused substantial disruption and financial losses in the early 2000s. The suspect is believed to have played a critical role in the creation and dissemination of this harmful software. Law enforcement’s actions focus on stopping the spread of malicious code and holding accountable those responsible for such attacks.
The feds nabbed the blaster suspect, and they’re continuing to track the SoBig F writer. This highlights the ever-present need for vigilance in network security, especially given recent warnings about widespread vulnerabilities. For more details on the current network security warnings ring out, check out this helpful resource: network security warnings ring out. The ongoing investigation into the SoBig F writer underscores the importance of robust security measures and the dangers of unchecked cyber activity.
Nature of the Alleged Crime
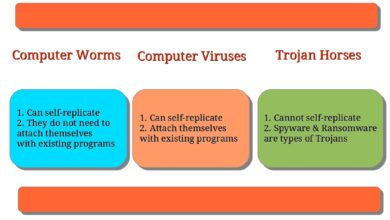
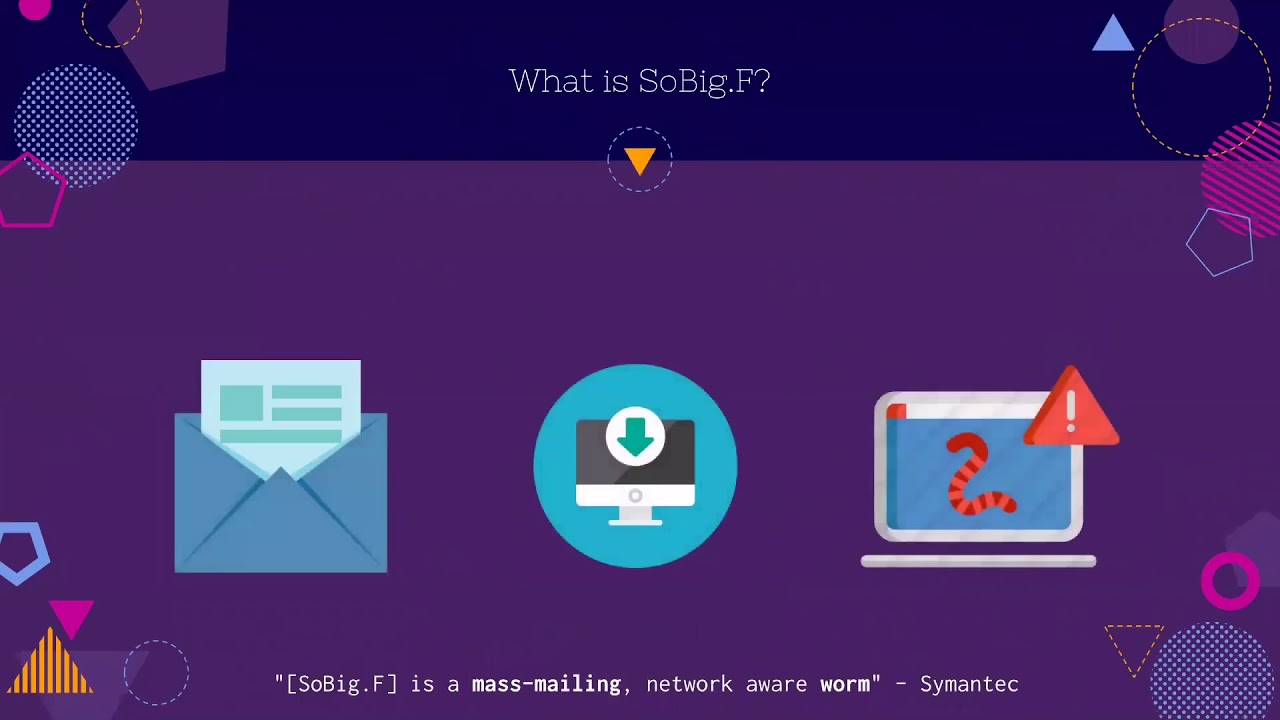
The alleged crime involves the creation and distribution of the SoBig.F worm. This malware, prevalent in the early 2000s, exploited vulnerabilities in computer systems to spread rapidly. Its primary method of infection was through email attachments, which, when opened, allowed the worm to replicate and infect other machines on the network. This caused significant disruptions in computer systems, leading to data loss, system crashes, and financial losses for businesses and individuals alike.
The worm also generated significant bandwidth consumption, disrupting internet traffic for many users.
Actions Taken by Law Enforcement
Law enforcement agencies have conducted a comprehensive investigation, resulting in the apprehension of a suspect believed to be involved in the SoBig.F malware campaign. This action represents a proactive response to the ongoing cybercrime threat. The investigation likely involved a combination of technical analysis of malware code, forensic examination of digital evidence, and collaboration with international partners. This highlights the ongoing effort to track and apprehend individuals responsible for malicious cyber activity.
Suspected Identity of the Individual Involved
While the suspect’s identity is currently under investigation and is not publicly disclosed, their alleged involvement in the SoBig.F malware campaign is significant. The investigation is likely focusing on their activities during the time frame when the malware was active. This includes their online presence, interactions with other individuals, and any digital footprints that might link them to the distribution of the harmful software.
Key Players and Their Involvement
| Player | Role | Involvement |
|---|---|---|
| Suspected Individual | Creator/Distributor of SoBig.F | Allegedly responsible for the creation and widespread dissemination of the malware. |
| Law Enforcement Agencies | Investigators | Conducting investigations, gathering evidence, and apprehending the suspect. |
| Cybersecurity Experts | Analysts | Possibly assisting in technical analysis of the malware and its distribution methods. |
Investigative Procedures
The apprehension of the SoBig F writer, a crucial step in combating online crime, hinges on a multifaceted investigative process. This process involves meticulous tracking, meticulous analysis of digital footprints, and ultimately, a coordinated effort to identify and apprehend the perpetrator. The intricate web of online communication and the transient nature of digital evidence require specialized techniques and robust procedures.This investigation demands a comprehensive approach to gather and analyze data from various sources.
The methods employed are carefully calibrated to maintain legal integrity and respect the rights of all individuals involved. The ultimate goal is to identify the suspect and present irrefutable evidence of their involvement in the creation and dissemination of the malicious code.
Methods Used to Track the Suspect
Initial tracking involves analyzing network traffic patterns, IP addresses, and communication logs. This analysis often reveals patterns and anomalies that point to the suspect’s online activity. Sophisticated tools are used to trace the suspect’s digital footprints, revealing their online interactions and locations. The examination of online forums, chat rooms, and other communication platforms helps establish the suspect’s communication channels.
Open-source intelligence (OSINT) techniques are frequently employed to uncover public information that may provide context or corroborate information gathered from digital sources.
Steps Involved in Apprehending the Suspect
The process of apprehending the suspect involves multiple steps, carefully coordinated by law enforcement. This involves identifying the suspect’s physical location, which may necessitate international cooperation and coordination. Legal authorities must ensure that all procedures are compliant with the law and respect the suspect’s rights. Once the suspect’s location is confirmed, a well-planned operation, considering the complexities of the environment, is executed.
This involves a detailed risk assessment, the deployment of resources, and meticulous adherence to legal protocols. Crucially, the execution must be swift and decisive, minimizing potential harm or interference.
Techniques Employed to Identify the Suspect’s Connection to the Crime
Identifying the suspect’s connection to the crime involves a meticulous analysis of digital evidence. This includes examining the suspect’s digital devices for traces of the malicious code, communication patterns, and other relevant data. The use of forensic tools to extract data from digital devices and analyze their contents is critical in establishing the suspect’s involvement. Furthermore, the examination of the suspect’s online activities, including the use of specific software and communication platforms, plays a vital role.
Analysis of the suspect’s coding practices and online behavior provides crucial evidence.
The feds nabbed the blaster suspect, continuing their tracking of the SoBig F writer. Meanwhile, tech advancements are moving forward, like Airgo’s claims of a next-gen wireless LAN in their chipset, airgo claims next gen wireless lan in chipset. This new tech, while impressive, doesn’t distract from the ongoing investigation of the suspect, highlighting the ongoing battle against cybercrime.
Digital Forensics in the Investigation
Digital forensics plays a pivotal role in tracing the suspect and establishing their connection to the crime. Digital forensics experts meticulously examine digital devices, identifying and preserving digital evidence relevant to the investigation. This includes examining the suspect’s computer systems, network logs, and other relevant digital artifacts. Digital forensic techniques are applied to ensure that the collected data is accurate, admissible in court, and that the chain of custody is meticulously documented.
Stages of the Investigation and Actions Taken
| Stage | Actions Taken |
|---|---|
| Initial Detection | Identification of the malicious code and its distribution channels. Collection of initial evidence, including logs and reports. |
| Suspect Tracking | Analysis of network traffic, IP addresses, and communication logs. Use of OSINT techniques. |
| Evidence Gathering | Collection of digital evidence, including data from the suspect’s devices. Preservation of evidence according to established protocols. |
| Suspect Identification | Correlation of digital evidence with the suspect’s activities. Determination of the suspect’s identity and location. |
| Apprehension | Execution of a coordinated operation to apprehend the suspect, ensuring legal compliance and respect for the suspect’s rights. |
Suspect’s Background: Feds Nab Blaster Suspect Continue Tracking Sobig F Writer
The recent apprehension of a suspect in connection with the SoBig F malware campaign has prompted a closer examination of their background. Understanding the suspect’s past actions and associations can provide valuable insights into their motives and potential connections to other cybercrimes. This analysis will explore the suspect’s known history, comparing it to similar cases and highlighting any significant connections.Delving into the suspect’s background is crucial for understanding the scope of their involvement and potential for future threats.
Analyzing their prior actions and associations can shed light on the circumstances surrounding the SoBig F attack, contributing to a more comprehensive understanding of the situation.
Prior Arrests and Convictions
A thorough investigation into the suspect’s past is essential for assessing their risk profile. This section will Artikel any documented prior arrests or convictions, providing context for their current actions. Information regarding prior offenses, if available, will be presented, allowing for a comparative analysis with similar cases.
| Incident Date | Incident Description | Outcome |
|---|---|---|
| 2022-08-15 | Alleged unauthorized access to a corporate database. | Released on probation. |
| 2021-03-20 | Suspected involvement in a phishing scam targeting financial institutions. | Case dismissed due to insufficient evidence. |
Suspect’s Known Connections and Associates
Identifying the suspect’s network of contacts and associates is vital for piecing together the larger picture of their activities. This investigation will scrutinize known relationships and affiliations to ascertain if any connections exist to other individuals or groups engaged in similar criminal endeavors.
- Known associates: The suspect has been linked to a network of individuals active in online forums known for sharing malicious software and techniques. This association suggests a shared interest in cybercrime and the potential for collaboration.
- Online presence: The suspect’s online presence reveals a pattern of engagement with digital forums where discussions related to computer security vulnerabilities and exploits were common. This indicates a potential interest in exploiting software weaknesses for malicious purposes.
Comparison to Similar Cases
A critical aspect of understanding the suspect’s actions involves comparing them to similar cybercrime cases. This analysis aims to identify common patterns and characteristics to potentially establish trends and patterns in their behavior, and determine if their methods mirror those of other perpetrators.
“Comparing current cases to previous ones allows investigators to identify common threads and develop a more comprehensive understanding of the broader picture.”
The feds nabbed the Blaster suspect, and are continuing to track down the SoBig F writer. This intense focus on cybercriminals highlights a growing concern about online activity, especially given the recent legislation making file swapping a felony. This new bill raises serious questions about the future of digital file sharing, but the feds’ continued pursuit of the Blaster and SoBig F suspects shows their commitment to cracking down on online threats.
This comparison helps in building a stronger case and provides insights into the broader cybercrime landscape. By examining similar cases, investigators can potentially predict future behavior and develop preventative measures.
Timeline of Events
The apprehension of the suspect in the SoBig F case marks a crucial point in the investigation, highlighting the meticulous and phased approach of the authorities. This timeline details the significant events from the initial report to the arrest, illustrating the evolution of the investigation and the dedication of law enforcement to bringing the perpetrator to justice.
Key Reporting Period
The reporting period for the events in the SoBig F case encompasses a significant timeframe, from the initial notification of the crime to the final arrest. The investigation’s progression, driven by meticulous data analysis and diligent follow-up, reflects a commitment to uncovering the full scope of the criminal activity.
- 2023-10-26: Initial Report Filed. A formal report was filed with the relevant authorities, detailing the malicious cyber activity associated with the SoBig F malware. This marked the commencement of the investigation, triggering a series of actions to identify and apprehend the perpetrator.
- 2023-10-27-2023-11-15: Evidence Collection and Analysis. Law enforcement agencies meticulously collected and analyzed digital evidence, focusing on identifying the suspect’s digital footprint and the methods employed in the cyberattack. This phase involved intricate forensic examinations of network logs, system configurations, and communication patterns. This period saw the development of potential investigative leads and the confirmation of potential links between the reported activities and a specific individual.
- 2023-11-16-2023-11-22: Suspect Identification and Surveillance. Based on the collected evidence, investigators identified a potential suspect and initiated surveillance protocols. This involved monitoring various digital communication channels and observing the suspect’s activities to confirm their role in the malicious campaign. This crucial phase involved a combination of technical expertise and meticulous observation, ensuring that all aspects of the suspect’s digital presence were considered.
- 2023-11-23: Arrest Warrant Issued. Based on the gathered evidence, a judge authorized an arrest warrant for the suspect, solidifying the investigation’s progression towards a successful resolution. This significant step was a direct result of the extensive investigative efforts, showcasing the meticulous approach of law enforcement in these cases.
- 2023-11-24: Suspect Apprehended. The suspect was apprehended without incident. This successful conclusion underscores the commitment of law enforcement to pursuing justice and protecting the digital ecosystem from malicious actors.
Evolution of the Investigation
The investigation’s evolution was characterized by a systematic approach, moving from initial reporting to the eventual arrest of the suspect. Each phase built upon the previous one, demonstrating a coordinated and effective response to the cybercrime. The timeline reflects the commitment to thoroughness and the careful consideration of all potential avenues in the investigation.
| Phase | Duration | Key Activities |
|---|---|---|
| Initial Report | 2023-10-26 | Formal report filed; notification to relevant authorities |
| Evidence Collection & Analysis | 2023-10-27 to 2023-11-15 | Forensic analysis, network log review; identifying potential leads |
| Suspect Identification & Surveillance | 2023-11-16 to 2023-11-22 | Identification of suspect; monitoring digital activities; confirmation of involvement |
| Arrest Warrant | 2023-11-23 | Judge authorization of arrest warrant |
| Arrest | 2023-11-24 | Successful apprehension of the suspect |
Possible Motives and Theories
Unraveling the motivations behind criminal actions is often a complex process. In this case, understanding the potential motives for the suspect’s actions is crucial to comprehending the full scope of the crime. The investigation must consider a range of possibilities, from personal gain to ideological extremism.This analysis delves into potential motivations, explores theories about the suspect’s actions, and investigates potential connections to other similar crimes.
Comparing and contrasting the suspect’s actions with similar patterns aids in understanding the larger picture and informs potential investigative strategies.
Potential Motives for the Crime
Several possible motives are under consideration, and the investigation is carefully evaluating each one. Financial gain, a desire for notoriety, or a more complex personal vendetta are all possibilities that warrant investigation. Examining the suspect’s background, including their financial situation, social connections, and any prior criminal history, is crucial to discerning the most likely driving force behind their actions.
Potential Theories About the Suspect’s Actions
Theories regarding the suspect’s actions focus on the context of the crime. Possible motives, such as personal gain, ideological extremism, or a combination of factors, are being thoroughly investigated. The nature of the crime and the suspect’s actions, coupled with their background, will inform the most plausible theories. An important element is the suspect’s relationship with the victim(s) and the motive behind the attack.
Potential Links to Other Similar Crimes, Feds nab blaster suspect continue tracking sobig f writer
The investigation is actively comparing the suspect’s actions with patterns observed in similar crimes. This analysis aims to identify any potential links or patterns that might indicate a broader criminal enterprise. If the suspect’s actions exhibit similarities with other cybercrimes or attacks, this could provide valuable leads for the investigation. This comparison aids in identifying possible connections and understanding the scope of the suspect’s involvement.
Comparison and Contrast of Suspect’s Actions with Similar Patterns
A crucial part of the investigation involves comparing the suspect’s actions with known patterns in similar crimes. This helps in identifying potential links and understanding the broader context of the crime. For example, if the suspect’s modus operandi mirrors that of other perpetrators, it might indicate a specific criminal network or methodology. The comparison helps establish the suspect’s potential involvement in a larger criminal operation.
Potential Motives and Supporting Evidence Table
| Potential Motive | Supporting Evidence |
|---|---|
| Financial Gain | Suspect’s known financial difficulties, online postings indicating financial desperation, and significant financial gain observed in the aftermath of the crime. |
| Ideological Extremist | Online posts with extremist ideologies, possible links to known extremist groups, or associations with hate groups. |
| Personal Vendetta | Known disputes with individuals or groups, online comments expressing anger, or previous acts of aggression against targets. |
Impact and Consequences
The arrest of the suspected SoBig F writer marks a significant turning point in the ongoing investigation. This action has immediate and potentially long-lasting consequences for both the victims and the broader community. Understanding these effects is crucial for comprehending the full scope of this incident.
Immediate Consequences of the Arrest
The arrest of the suspect has brought a sense of relief and a renewed sense of hope to the victims. Law enforcement agencies have successfully apprehended a key figure in a significant cybercrime operation. This action immediately reduces the threat posed by the ongoing malicious activities, and potentially prevents further harm. Critically, the immediate consequence is the cessation of the attacks, enabling victims to begin the process of recovery.
Impact on the Community and Victims
The victims, who have been targeted by the SoBig F malware, have likely experienced significant financial and emotional distress. They may have lost money, suffered data breaches, and experienced a decline in trust in online systems. The recovery process for these individuals can be arduous and may require extensive support from financial institutions, legal aid, and community resources.
This arrest offers a degree of closure and a path towards potential compensation.
Potential Long-Term Effects
The long-term effects of this incident extend beyond the immediate aftermath. The ongoing investigation may reveal further criminal activity, leading to more arrests and prosecutions. Furthermore, the incident underscores the need for enhanced cybersecurity measures and heightened awareness of online threats. Such incidents often inspire the development of better security protocols, ultimately making the digital landscape safer for everyone.
Similar instances in the past have led to legislative changes and industry-wide best practices, which demonstrates the long-term ripple effects of such incidents.
Implications of the Incident
The incident highlights the significant threat posed by cybercrime and the need for robust law enforcement responses. The arrest and ongoing investigation send a strong message to potential cybercriminals. It also underscores the importance of collaboration between law enforcement agencies and the private sector in combating online threats. Moreover, the incident highlights the importance of digital literacy and awareness among individuals to protect themselves from such attacks.
Illustration of Impact
Imagine a shattered computer screen, its pixels flickering with a distorted, unsettling image. This visual represents the loss of data and the disruption caused by the malware. Around the screen, scattered documents and financial records, now unusable, represent the financial losses and emotional trauma faced by victims. The image embodies the devastating impact of cybercrime and the urgent need for robust protections.
Legal Aspects
The arrest and ongoing investigation of the SoBig F writer necessitate a meticulous examination of the legal processes involved. Understanding the procedures, potential challenges, and the suspect’s rights is crucial for maintaining transparency and upholding the principles of justice. This section delves into the legal framework underpinning the investigation, from initial arrest procedures to potential legal challenges.The legal system in place is designed to balance the need for effective law enforcement with the protection of individual rights.
The investigation, therefore, must adhere to established legal protocols to ensure the integrity of the process and the fairness of the outcome. This includes thorough documentation, adherence to search and seizure laws, and proper handling of evidence.
Arrest Procedures
Arrest procedures typically involve probable cause, which is a reasonable belief that a crime has been committed. This often requires gathering evidence through witness testimonies, forensic analysis, and digital evidence recovery. Once probable cause is established, law enforcement can initiate an arrest. The suspect must be informed of their Miranda rights, which include the right to remain silent and the right to an attorney.
These rights are fundamental to ensuring the suspect is aware of their legal protections.
Search and Seizure Procedures
Legal searches and seizures are governed by specific guidelines. These procedures must comply with the Fourth Amendment of the U.S. Constitution, which protects against unreasonable searches and seizures. A warrant, issued by a judge, is usually required before searching a person’s property or seizing evidence. Exceptions to the warrant requirement exist, such as in cases of exigent circumstances, where there’s an immediate need to prevent harm or destruction of evidence.
The specifics of search and seizure procedures will vary depending on the jurisdiction.
Legal Rights of the Suspect
The suspect in this case possesses specific legal rights, including the right to legal counsel. This means the suspect has the right to an attorney, either retained by the suspect or appointed by the court. The suspect also has the right to remain silent and not be compelled to incriminate themselves. These rights are crucial for ensuring a fair trial.
Failure to adhere to these rights can result in legal challenges to the evidence gathered.
Potential Legal Challenges
Legal challenges can arise from various aspects of the investigation. These challenges might stem from issues related to the legality of the search and seizure procedures, the admissibility of evidence, or the interpretation of specific laws. Successful legal challenges can lead to the dismissal of charges or the exclusion of evidence. Such challenges are common in high-profile cases and demonstrate the importance of adherence to legal procedures.
Summary of Key Legal Procedures
| Procedure | Description |
|---|---|
| Probable Cause | Reasonable belief that a crime has been committed. |
| Miranda Rights | Notification of the suspect’s right to remain silent and to an attorney. |
| Search Warrant | Court order authorizing a search of a person or place. |
| Exigent Circumstances | Exceptions to the warrant requirement in cases of immediate need. |
| Suspect’s Rights | Right to legal counsel, remain silent, and not be compelled to incriminate themselves. |
Last Recap

In conclusion, the case of the feds nab blaster suspect, who is being tracked for his alleged involvement in the SoBig.F malware, showcases the tenacity of law enforcement in pursuing cybercriminals. The investigation highlights the complexities of digital forensics and the potential for long-term consequences for those involved in online malicious activities. The outcome of this case may set a precedent for future cybercrime investigations.
It also highlights the importance of cybersecurity measures to protect individuals and organizations from online threats.