FTC Endorses Bounty on Spammers A New Approach
FTC endorses bounty on spammers, a novel approach to combatting the pervasive issue of online spam. This new initiative incentivizes individuals to report spam by offering rewards, potentially revolutionizing how the FTC tackles this digital menace. The program promises a more proactive and collaborative approach, shifting from solely reactive enforcement to a system that actively engages the public in identifying and reporting spam.
The FTC’s history with spam enforcement, past enforcement strategies, and the evolution of spam techniques will be examined. The bounty system’s potential benefits and drawbacks will be discussed, along with a look at potential impacts on the spam landscape. Public perception, potential concerns, and future implications, including potential partnerships, will also be explored.
Background of the FTC’s Action
The Federal Trade Commission (FTC) has a long history of addressing deceptive and unfair business practices, including the insidious problem of spam. This aggressive stance stems from a recognition that unsolicited commercial emails, or spam, can cause significant harm to consumers and businesses alike. The FTC’s efforts to combat spam have evolved over time, adapting to the changing tactics of spammers.The FTC’s approach to spam is not static; it has been shaped by the evolution of spam techniques, from early, easily identifiable mass mailings to the sophisticated, often disguised, phishing attempts prevalent today.
The FTC’s endorsement of a bounty on spammers is a significant step, but it’s worth noting the ongoing efforts in tracking cybercriminals. Recent news of the feds nabbing a Blaster suspect and continuing to track the SoBig F writer, as detailed in this article feds nab blaster suspect continue tracking sobig f writer , highlights the broader fight against malicious actors.
This reinforces the importance of the FTC’s initiative to deter spam, as it directly addresses a crucial component of online security.
This evolution necessitates a dynamic approach from the FTC, constantly updating its strategies to keep pace with spammers’ innovations.
Historical Approach to Spam
Initially, the FTC focused on using existing laws to address spam, targeting deceptive or misleading practices often associated with it. This involved complaints from consumers and businesses about fraudulent schemes, misleading representations in spam messages, and violation of CAN-SPAM Act provisions. The FTC’s enforcement actions early on were primarily focused on addressing specific harms caused by spam, such as identity theft or fraudulent schemes.
Types of Penalties and Enforcement Actions
The FTC has employed a range of enforcement actions against spammers, including cease-and-desist orders, civil penalties, and restitution for consumers harmed by spam. Cease-and-desist orders prohibit further violations, while civil penalties financially punish the perpetrators. Restitution remedies address the direct financial harm caused by spam to individual consumers.
Legislative Frameworks Underpinning FTC Authority
The FTC’s authority to pursue spam cases is rooted in various legislative frameworks, including the Federal Trade Commission Act (FTC Act) and the CAN-SPAM Act. The FTC Act empowers the commission to address unfair or deceptive acts or practices, while the CAN-SPAM Act provides specific regulations governing commercial email.
Evolution of Spam Techniques and Influence on FTC Strategy
Spam techniques have significantly evolved over time. Early spam relied on simple mass mailings. Modern spam is often more sophisticated, employing techniques such as spoofing to appear legitimate, disguising links, and using social engineering tactics to trick recipients into revealing sensitive information. The FTC’s strategies have adapted accordingly. For example, initial actions were focused on identifying spam by obvious characteristics.
The FTC’s endorsement of a bounty on spammers is a smart move, but what if, instead of reacting to the problem, we proactively prevented it? Imagine a world where companies like Microsoft prioritized security, not just as a feature, but as a fundamental design principle. That’s what I explore in my article, “what if microsoft got security right” what if microsoft got security right.
Ultimately, though, the FTC’s approach, while potentially effective, still hinges on reactive measures. Perhaps this bounty will be a stepping stone towards a more preventative, holistic approach to online security.
Later strategies incorporated more sophisticated detection and analysis methods.
Comparison of Enforcement Strategies, Ftc endorses bounty on spammers
| Year | Enforcement Strategy | Success Rate | Impact on Spam |
|---|---|---|---|
| Early 2000s | Focusing on deceptive and misleading practices, primarily relying on consumer complaints. | Moderate | Limited impact on overall spam volume, but effective in specific cases. |
| Mid-2000s | Increased emphasis on cease-and-desist orders and civil penalties. More proactive investigation of spam networks. | Mixed results; some high-profile cases with significant impact, but overall volume remained high. | Reduced some spam volume, but spam evolved to be more sophisticated. |
| Present | Combination of proactive investigations, data analysis to identify patterns, and collaborative efforts with other agencies and industry groups. Stronger emphasis on preventative measures. | Ongoing assessment; success is hard to quantify due to the dynamic nature of spam. | Ongoing reduction in spam, though spammers are continuously developing new methods. |
Understanding the “Bounty” Mechanism
A bounty system, often used in cybersecurity and other fields, can be a powerful tool for consumer protection. The FTC’s proposed bounty on spam reports leverages this principle to incentivize individuals to actively participate in combating unwanted messages. This approach aims to supplement existing enforcement mechanisms and potentially reduce the volume of spam reaching consumers.The core concept of a bounty system involves offering rewards for specific actions.
In this case, the action is reporting spam emails, websites, or other forms of unwanted digital communication. The hope is that by providing financial incentives, individuals will be more motivated to identify and report these problematic communications, ultimately strengthening the FTC’s ability to combat these violations of consumer protection.
The FTC’s endorsement of a bounty on spammers is a smart move, tackling a persistent problem. Meanwhile, it’s interesting to see that Intel is reportedly moving to new chip names, potentially signifying a major shift in their branding strategy, as seen in intel reportedly moving to new chip names. This likely won’t directly impact the effectiveness of the bounty program, but it does highlight the ongoing tech landscape and the need for continuous innovation in fighting online annoyances.
Potential Benefits of Incentivizing Reports
Incentivizing individuals to report spam offers several potential benefits. Firstly, it can increase the volume of reports received by the FTC, providing a more comprehensive picture of spam activity. Secondly, it could lead to faster identification and resolution of spam campaigns, potentially saving consumers time and resources. Thirdly, by encouraging citizen participation, the bounty system might foster a sense of collective responsibility for protecting consumers from online scams and harassment.
Finally, a well-structured bounty program can act as a deterrent, discouraging spammers and potentially reducing the overall volume of spam.
Potential Drawbacks or Challenges
Implementing a bounty program for spam reporting also presents some potential challenges. One concern is the potential for fraud or abuse. Ensuring the legitimacy of reports and preventing malicious actors from exploiting the system is crucial. Another concern is the need for a clear and transparent system for awarding bounties, to avoid accusations of bias or unfairness.
Determining appropriate reward levels and the overall budget for the program is also a key consideration. Finally, there might be difficulty in accurately measuring the effectiveness of the program and ensuring it’s not simply adding to existing bureaucratic processes without significantly impacting the problem.
Types of Rewards
Several types of rewards could be offered to individuals who report spam. These could include:
- Cash payments: A straightforward and easily understood reward system.
- Gift cards: Providing a flexible reward option for recipients.
- Points redeemable for goods or services: Allowing individuals to choose rewards based on their preferences.
- Recognition and publicity: Recognizing the contributions of those who report spam, fostering community engagement.
Careful consideration of the target audience and the desired impact will help in choosing the most effective reward type.
Criteria for Awarding Bounties
The success of a bounty program hinges on a transparent and objective system for evaluating and awarding rewards. The criteria must be clearly defined and communicated to encourage responsible reporting and discourage abuse.
| Criteria | Description | Points Awarded |
|---|---|---|
| Report Validity | Accuracy and completeness of the reported spam information. | 1-5 points (based on quality of detail) |
| Impact | The potential impact of the report on preventing future spam activity (e.g., identifying a new spam campaign, blocking a known spammer). | 1-3 points (based on assessed impact) |
| Timeliness | How quickly the report is submitted and the response from the system. | 1-2 points (prioritizing swift action) |
| Completeness of information | Providing necessary details about the spam, including links, contact information, and descriptions of the content. | 1-3 points (ensuring full data is provided) |
Impact on the Spam Landscape

The FTC’s endorsement of a bounty program for reporting spam represents a significant shift in the fight against unwanted email and online messages. This approach, leveraging financial incentives, is expected to create a new dynamic in the spam landscape, potentially prompting changes in spammer tactics and influencing the effectiveness of existing anti-spam measures. By rewarding individuals for identifying and reporting spam, the FTC aims to empower users and increase the overall cost of engaging in such malicious activity.
Predicting Spammer Behavior
Spammers, driven by profit, are likely to adapt to the bounty program. Some may shift towards more sophisticated techniques to avoid detection, while others might abandon spam altogether, given the increased risk. Those who remain may focus on targeting vulnerabilities in the systems used for bounty payouts, or attempt to exploit loopholes in the program’s design. The potential for increased sophistication in spam filtering technology and detection will likely also occur as a direct response to the bounty.
Comparing Effectiveness with Existing Measures
The effectiveness of the bounty program will likely be measured against existing anti-spam measures. Methods like email filters, sender reputation databases, and user education campaigns have proven valuable, but their impact has been limited in certain areas. The bounty program can be considered a complementary measure, adding a layer of user-driven enforcement. Its effectiveness will depend on the program’s design, the size of the rewards, and the level of public participation.
Success will also depend on how well the program is integrated with existing anti-spam technologies, potentially creating a more holistic and proactive approach to spam control.
Potential for Anti-Spam Innovation
The bounty program may inspire innovation in anti-spam technology. This could lead to the development of more sophisticated spam detection algorithms, new approaches to classifying spam, or improved techniques for verifying sender identities. The incentive for innovation may also create a market for new tools that can help users identify and report spam more effectively. Companies specializing in anti-spam software may be motivated to develop new solutions.
Examples of Similar Bounty Programs
Bounty programs have proven successful in other sectors. For instance, bug bounty programs in software development incentivize the discovery and reporting of vulnerabilities, leading to improved security. Similarly, in the cybersecurity arena, programs rewarding the reporting of malicious activity have yielded positive results, leading to quicker identification and mitigation of threats. These programs, when well-designed, can be effective tools for bolstering security and encouraging responsible reporting.
Potential Impacts on Different Types of Spam
| Spam Type | Potential Impact | Reason |
|---|---|---|
| Phishing Emails | Significant reduction in volume and sophistication | High potential rewards for reporting successful phishing attempts. |
| Malicious Links | Moderate reduction in volume, potential for increased sophistication in disguise. | Rewards for identifying malicious links could prompt more advanced cloaking and obfuscation techniques. |
| Spam Advertisements | Likely to see a decrease in volume and some change in tactics. | The high volume of spam advertisements might make the bounty program less profitable for spammers, driving them to adjust their methods. |
| Social Media Spam | Potential impact on volume and tactics, likely to adapt to the new environment. | The reward structure may incentivize more sophisticated strategies for targeting users on social media platforms. |
Public Perception and Potential Concerns
The FTC’s bounty program, while aiming to combat online spam, presents a complex set of potential public reactions and concerns. Public perception hinges on trust, fairness, and transparency in the program’s design and execution. Misunderstandings or perceived unfairness could erode public support for the initiative, potentially undermining its effectiveness.The bounty program, while intended to incentivize reporting and reduce spam, requires careful consideration of potential negative impacts.
Concerns about fairness, transparency, administration, and potential legal challenges must be addressed to ensure the program’s success and public acceptance. A robust public relations strategy and proactive communication will be vital to managing these potential concerns.
Potential Public Reaction
Public reaction to the program is multifaceted and unpredictable. Some individuals may view the bounty program positively, recognizing its potential to curb spam and protect consumers. Conversely, others may perceive the program as overly complex, potentially leading to skepticism or cynicism. Misinformation or lack of clear communication could exacerbate these concerns. The program’s success depends on effective communication to build trust and understanding among the public.
Fairness and Transparency Concerns
Concerns about fairness revolve around the criteria for awarding bounties. Uneven application or perceived bias in the evaluation process could lead to public dissatisfaction. The program needs clear, publicly accessible criteria for identifying and rewarding reports of spam activity. Transparency in the program’s administration is paramount to maintain public trust. This includes outlining the process for reviewing submissions, the qualifications of evaluators, and the criteria for determining a valid claim.
A transparent process will increase public confidence in the program’s fairness and reliability.
Administration and Management Issues
Efficient administration and management are crucial for the program’s success. Potential issues include the volume of submissions, the need for dedicated personnel, and the risk of fraudulent claims. A robust system for managing submissions, verifying claims, and processing payments is essential. Implementing effective filters to identify and triage spam reports could also streamline the process and prevent overwhelming the system.
Clear guidelines and a well-defined procedure for handling disputes or appeals are necessary to ensure the program’s integrity and maintain fairness.
Potential Legal Challenges
Legal challenges are always a possibility with any new program. Concerns may arise about the program’s scope, the potential for abuse, or the constitutionality of certain provisions. The program should be carefully drafted to minimize the potential for legal disputes. Consulting legal experts to identify and mitigate potential legal risks is crucial to avoid costly and time-consuming litigation.
The program must comply with existing laws and regulations to ensure its legality and effectiveness.
Summary of Potential Concerns and Proposed Solutions
| Concern | Potential Solution |
|---|---|
| Uneven application of criteria for awarding bounties | Publish clear, publicly accessible criteria for evaluating spam reports, ensuring transparency and consistent application. |
| Lack of transparency in the program’s administration | Provide detailed information on the submission process, evaluation criteria, and payment procedures. |
| High volume of submissions overwhelming the system | Implement a system for managing and prioritizing submissions, using automated filters and prioritization strategies. |
| Potential for fraudulent claims | Implement robust verification procedures to ensure the legitimacy of submissions, and establish a clear process for handling fraudulent claims. |
| Potential legal challenges to the program | Consult legal experts to ensure compliance with existing laws and regulations, and anticipate potential challenges. |
Future Implications and Strategies

The FTC’s bounty program for spammers represents a significant shift in consumer protection strategies. Its success hinges not only on immediate impact but also on long-term adaptability and integration with broader consumer protection efforts. This section explores potential future extensions, integrations, and sustainability strategies, as well as a crucial public communication plan.The bounty program, while promising, requires ongoing refinement to maximize its effectiveness and long-term impact.
Understanding the evolving nature of spam and its tactics is crucial for adjusting the program’s parameters and ensuring continued success in the face of emerging threats.
Potential Future Extensions and Modifications
The bounty program can be further enhanced by incorporating dynamic adjustments based on spam trends. For example, if a particular type of spam targeting specific demographics becomes prevalent, the program could allocate a higher reward for identifying and reporting it. This proactive adaptation would ensure the program remains relevant and effective against emerging threats. Another potential extension involves incorporating automated tools to expedite the reporting and verification process.
This could include utilizing AI-powered systems to analyze spam reports, identify patterns, and automatically flag suspicious activity. This automation would significantly increase the program’s efficiency and allow for faster payouts to legitimate reporters.
Integration with Other Consumer Protection Efforts
The bounty program can be synergistically integrated with other consumer protection initiatives. For instance, it could be linked with existing fraud reporting mechanisms, allowing users to report fraudulent activities and receive rewards simultaneously. This would broaden the scope of consumer protection, encompassing a wider range of harmful online practices. Additionally, the program can be integrated with educational campaigns to raise awareness about various online scams and the importance of reporting suspicious activities.
This approach fosters a proactive approach to consumer protection, empowering users with knowledge and incentives to report issues.
Strategies for Long-Term Sustainability
Ensuring the long-term sustainability of the bounty program requires a multifaceted approach. One key strategy involves establishing a transparent and well-defined process for managing and evaluating program performance. This includes regular performance reports and feedback mechanisms for both reporters and the FTC. This transparency builds trust and demonstrates accountability. Another crucial strategy is establishing a dedicated budget and funding mechanism to ensure consistent funding and prevent future budget constraints.
This would allow for the program’s ongoing maintenance and expansion without relying on temporary funding.
Effective Public Communication Strategy
A well-structured communication strategy is essential for educating the public about the program and encouraging participation. This involves a multi-channel approach encompassing social media campaigns, educational websites, and partnerships with consumer advocacy groups. Clear and concise information regarding the program’s eligibility criteria, reporting process, and reward structure must be readily available to the public. This information should be disseminated across various platforms, ensuring accessibility and understanding among all stakeholders.
Potential Future Partnerships
| Partner | Potential Contribution ||—|—|| Cybersecurity Companies | Provide technical expertise and tools to analyze spam reports and identify patterns. || Consumer Protection Organizations | Offer support and resources for outreach and education programs, enhancing public awareness. || Educational Institutions | Conduct research on spam trends and develop educational materials to help users identify and report spam. || Law Enforcement Agencies | Collaborate on investigations and enforcement actions related to spam activities.
|| Online Payment Platforms | Integrate reporting mechanisms into their platforms, making it easier for users to report spam related to payment activities. |
Illustrative Case Studies: Ftc Endorses Bounty On Spammers
The FTC’s ongoing battle against spam is not just about theoretical concepts; it’s about tangible impacts on real people. Understanding past cases helps us grasp the severity and scale of the problem, and how the agency tackles these issues. These examples showcase the types of spam encountered, the harm inflicted, and the FTC’s successful strategies.The FTC’s role in combating spam extends beyond theoretical frameworks.
These cases, while anonymized to protect individuals, provide real-world insight into the tactics employed by spammers and the methods used by the FTC to identify and hold them accountable.
A Case of Phishing Scams Targeting Senior Citizens
Phishing scams, particularly those targeting vulnerable populations like senior citizens, pose a significant threat. These scams often exploit trust and manipulate individuals into revealing sensitive information, leading to financial losses. The FTC’s approach to these cases often involves a multi-pronged strategy that combines enforcement actions, public awareness campaigns, and collaborations with other agencies.
- Type of Spam: Sophisticated phishing emails impersonating legitimate financial institutions. These emails frequently contained urgent requests for account updates or password changes, often using convincing subject lines and logos.
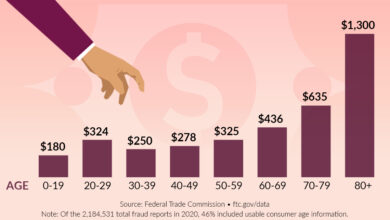
- Impact on Consumers: Many senior citizens, due to a lack of familiarity with online safety or scams, were tricked into providing banking credentials and personal information, leading to substantial financial losses. These losses were not just monetary but also involved emotional distress and a loss of trust in online systems.
- Outcome of FTC Action: The FTC issued cease-and-desist orders against the spammers, halting their operations. Furthermore, the FTC initiated a public awareness campaign targeting senior citizens, providing educational materials on identifying and avoiding phishing scams. The spammers were also held accountable for their fraudulent activities.
- FTC Strategies: The FTC leveraged data analysis to identify patterns in the phishing emails, allowing them to track the spammers’ activities and pinpoint the sources. They collaborated with financial institutions to proactively alert their customers about the scams. A critical component of their strategy was to educate the public on recognizing phishing scams.
- Financial Impact Visualization: Imagine a bar graph with the x-axis representing the number of victims and the y-axis representing the average financial loss per victim. The graph would clearly illustrate the cumulative financial burden on the community. Data from similar cases, compiled by the FTC, would likely show a significant and alarming trend.
- Timeline of Events:
- 2023-Q1: Initial reports of phishing scams targeting senior citizens flood into the FTC.
- 2023-Q2: The FTC conducts data analysis to identify patterns and track the spammers’ activities. Initial public awareness campaigns were launched.
- 2023-Q3: Cease-and-desist orders are issued, and the spammers’ operations are halted. Further collaborations with financial institutions take place to alert their customers.
- 2023-Q4: Ongoing monitoring and follow-up actions are taken by the FTC to ensure the spammers do not resume their activities.
Conclusion
The FTC’s endorsement of a bounty program on spam represents a significant shift in anti-spam strategies. While promising a more proactive and collaborative approach, the program faces potential challenges related to fairness, transparency, and administration. The success of this new initiative hinges on careful consideration of public concerns and the development of robust systems for managing the program effectively.
This marks a crucial moment in the ongoing battle against spam, with potential implications extending beyond the digital realm.