HP Girds for War Dell Palmone Targets
HP Girds for War Dell Palmone are targets. This analysis delves into the vulnerabilities of HP Gird systems used in the War Dell Palmone context, examining potential attack vectors, impacts, and critical components. We’ll explore existing security measures, compare them to best practices, and discuss crucial incident response plans, legal compliance, mitigation strategies, and future predictions for these systems.
This comprehensive overview provides a clear picture of the security landscape and actionable steps for enhanced protection.
The analysis examines the specific vulnerabilities of HP Gird systems, highlighting potential weaknesses and their consequences in the War Dell Palmone scenario. It covers the critical components susceptible to attack, presenting a clear table outlining various vulnerabilities, their associated attack vectors, potential impact, and mitigation strategies. The detailed security measures analysis and best practices provide a practical guide for improving security posture and implementing enhanced protection protocols.
Target Vulnerability Assessment

HP Grid systems for War Dell Palmone, while designed for robust operation, are not immune to potential vulnerabilities. Understanding these vulnerabilities is crucial for proactively mitigating risks and safeguarding the integrity of the system. This assessment Artikels potential weaknesses, attack vectors, and impacts, alongside critical components at risk, and suggests mitigation strategies.The intricate nature of HP Grid systems, encompassing diverse hardware and software components, creates potential entry points for malicious actors.
Security breaches can have severe consequences, ranging from data loss and system disruption to financial damage and reputational harm. Identifying and addressing these vulnerabilities is paramount to ensuring the long-term stability and security of the War Dell Palmone operation.
Potential Vulnerabilities in HP Grid Systems
HP Grid systems, due to their complex architecture, present several potential vulnerabilities. These include, but are not limited to, weak authentication mechanisms, insecure communication protocols, and inadequate access controls. Furthermore, outdated software and poorly configured hardware can also expose the system to exploitation.
Attack Vectors Exploiting Vulnerabilities
Various attack vectors can exploit these vulnerabilities. Sophisticated attackers may leverage social engineering tactics to gain unauthorized access to sensitive information or to compromise system accounts. Malicious software, disguised as legitimate applications, can be introduced through phishing campaigns or compromised websites. Exploiting known software vulnerabilities through remote exploits is another common attack vector.
Impact of a Successful Attack
A successful attack on HP Grid systems for War Dell Palmone could have severe consequences. Data breaches could expose sensitive information, potentially leading to financial losses, legal liabilities, and reputational damage. Disruption of service could result in operational downtime and hinder the smooth functioning of the War Dell Palmone operation. In extreme cases, attacks could even compromise the physical security of the infrastructure.
HP’s Grids for War, and Dell’s PalmOne are definitely targets in the current tech landscape. However, IBM’s recent development of a sister supercomputer to its top model, as detailed in this article , might just shift the focus. This new supercomputer’s capabilities could potentially challenge the dominance of the current generation of HP grids, and in turn, impact the future of similar systems from Dell.
So, while HP and Dell are still under the radar, the future of the war in the computing grid market is uncertain.
Critical Components Vulnerable to Attacks
Several critical components within the HP Grid systems are susceptible to attacks. These include the authentication servers, data storage systems, and network infrastructure. The central management console, responsible for overall system control, is also a prime target. Compromising these components could grant attackers significant control over the entire system.
Comparison of Potential Risks
| Vulnerability | Attack Vector | Impact | Mitigation |
|---|---|---|---|
| Weak Authentication | Brute-force attacks, credential stuffing | Unauthorized access, data breaches, system compromise | Strong password policies, multi-factor authentication, regular audits |
| Insecure Communication Protocols | Man-in-the-middle attacks, eavesdropping | Data interception, unauthorized access, manipulation of data | Secure communication channels (HTTPS), encryption, network segmentation |
| Outdated Software | Exploitation of known vulnerabilities | System compromise, data breaches, denial-of-service attacks | Regular software updates, vulnerability scanning, patch management |
| Inadequate Access Controls | Privilege escalation, unauthorized access | Data breaches, system compromise, operational disruption | Principle of least privilege, access controls, role-based access control |
Security Measures & Best Practices
Protecting sensitive data and systems, especially in critical infrastructure like the HP Grid systems for War Dell Palmone, requires a robust security posture. This involves not just implementing measures, but also continually evaluating and adapting to evolving threats. This analysis will delve into existing security measures, compare them to industry best practices, and Artikel strategies for enhancing the HP Grid’s security posture.Existing security measures for the HP Grid systems for War Dell Palmone likely include network firewalls, intrusion detection systems (IDS), and access control mechanisms.
However, the effectiveness of these measures depends heavily on their configuration, maintenance, and ongoing monitoring. A thorough review and potential upgrades are crucial for maintaining an adequate security level.
Existing Security Measures
The current security measures in place for the HP Grid systems for War Dell Palmone are likely based on a combination of standard industry protocols and possibly tailored configurations for the specific operational requirements of the system. This approach, while potentially adequate, needs continuous evaluation to ensure its effectiveness against modern threats.
Comparison with Industry Best Practices
Industry best practices for critical infrastructure security go beyond basic security measures. They emphasize a layered approach, integrating various security controls. This includes implementing security information and event management (SIEM) systems for real-time threat detection and response, and regular vulnerability assessments to proactively identify and patch potential weaknesses. A robust security architecture for the HP Grid systems should also consider the principle of least privilege, restricting access to only the necessary resources and data.
Furthermore, continuous monitoring and auditing are essential to ensure the ongoing effectiveness of the security measures.
Improving Security Posture
To enhance the security posture of the HP Grid systems, several key improvements are necessary. These include:
- Implementing a comprehensive security awareness program for all users to educate them on potential threats and best practices for avoiding phishing attempts, malware infections, and social engineering attacks.
- Regular penetration testing and vulnerability assessments to identify weaknesses in the system’s architecture and configurations.
- Implementing a robust incident response plan, outlining procedures for detecting, containing, and recovering from security incidents. This should involve clear communication protocols, a dedicated incident response team, and a process for escalating incidents.
These proactive steps are critical for maintaining a strong security posture and preventing potential breaches.
Multi-Factor Authentication
Multi-factor authentication (MFA) is a crucial component of enhanced security. MFA adds an extra layer of verification beyond a simple username and password, making it significantly harder for unauthorized individuals to access sensitive data or systems. This is achieved by requiring users to provide two or more forms of authentication, such as a password, a one-time code from a mobile device, or a biometric scan.Examples of strong MFA implementations include using time-based one-time passwords (TOTP) generated by authenticator apps, or security keys that require physical interaction for verification.
Implementing MFA across all user accounts and administrative access points is a critical step in fortifying the security of the HP Grid systems for War Dell Palmone.
Strong Password Policies
Robust password policies are vital for safeguarding access to the HP Grid systems. These policies should enforce complexity requirements, including a minimum length, the inclusion of uppercase and lowercase letters, numbers, and special characters. Regular password changes and automatic expiration policies further enhance security.Examples of strong password policies include:
- Minimum password length of 12 characters.
- Password complexity requirements, including uppercase letters, lowercase letters, numbers, and special characters.
- Automatic password expiration after a specified period.
- Prohibition of reusing passwords across different accounts.
- Regular password audits and changes for administrative accounts.
By enforcing these policies, the risk of password breaches and unauthorized access is minimized.
Incident Response Plan
Protecting HP Grid systems for War Dell Palmone from cyberattacks requires a robust incident response plan. This plan Artikels the procedures for detecting, containing, and recovering from a security breach, ensuring minimal disruption and swift restoration of operations. A proactive approach is crucial to mitigate potential damage and maintain business continuity.A comprehensive incident response plan acts as a guide for all personnel involved in handling security incidents.
It details the specific actions to be taken, the responsibilities of each team, and the communication channels to be utilized. This proactive approach allows for a structured and efficient response, minimizing the impact of a security breach.
Incident Detection and Initial Response
The first step in responding to a security incident is rapid detection. The security team is responsible for identifying potential breaches through various mechanisms such as intrusion detection systems, security information and event management (SIEM) systems, and user reports. Automated alerts and manual reviews play crucial roles in this process. Immediate actions upon detection include isolating affected systems to contain the incident and notifying relevant personnel.
HP and Dell’s enterprise-grade servers, like the ones in the PalmOne line, are becoming increasingly attractive targets for cybercriminals. This isn’t just a random surge in server theft; it’s a sign of a much larger problem, as highlighted by a recent eBay fraud case, new eBay fraud case highlights growing problem. The tactics used to defraud eBay sellers show a sophisticated approach that could easily be adapted to target these valuable server components.
Clearly, businesses need to be more vigilant in protecting their equipment.
Roles and Responsibilities
The incident response plan defines the roles and responsibilities of various teams and individuals. The security team leads the initial investigation and containment, while the IT team handles system restoration. The legal and communications teams support the process with legal counsel and stakeholder updates. Clearly defined roles prevent confusion and ensure efficient coordination during a crisis.
Communication Protocols
Effective communication is essential during a security incident. Internal communication channels, such as email, instant messaging, and dedicated incident response platforms, are established for rapid updates. External communication, such as notification to regulatory bodies and affected customers, follows a pre-defined protocol. Transparency and timely updates are key to managing stakeholder expectations and maintaining trust.
Incident Containment and Eradication
Containing the incident is a critical step to prevent further damage. This involves isolating affected systems, preventing unauthorized access, and securing sensitive data. The plan Artikels the procedures for analyzing the incident to understand the extent of the breach, identify the root cause, and implement remediation measures. These measures include patching vulnerabilities, restoring systems, and implementing security enhancements.
Recovery and Post-Incident Analysis
The recovery phase focuses on restoring systems to normal operation. This involves restoring data, reconfiguring systems, and implementing preventative measures. Post-incident analysis is crucial to identify weaknesses in the security posture and implement necessary improvements. Lessons learned from the incident are documented and used to strengthen future security measures.
Key Elements of the Incident Response Plan
| Stage | Action | Team | Timeline |
|---|---|---|---|
| Detection | Identify the breach, isolate affected systems, notify relevant personnel | Security Team | Within 1 hour |
| Containment | Prevent further compromise, secure sensitive data | Security, IT Teams | Within 2 hours |
| Eradication | Identify and eliminate the root cause, remediate vulnerabilities | Security, IT Teams | Within 24 hours |
| Recovery | Restore systems, data, and services to normal operation | IT, Network Teams | Within 48-72 hours |
| Post-Incident Analysis | Review the incident, identify lessons learned, implement improvements | Security, Management | Within 1 week |
Legal & Regulatory Compliance
Navigating the complex world of data protection and privacy regulations is crucial for any organization handling sensitive information. This section details the legal and regulatory frameworks applicable to HP Grid systems for War Dell Palmone, outlining compliance requirements, potential penalties for non-compliance, and best practices for maintaining a robust legal framework. Understanding these regulations is paramount to ensuring the secure and responsible operation of the systems.The legal and regulatory landscape for data protection and privacy is constantly evolving.
Companies must remain vigilant and proactive in adapting to new standards and requirements. This proactive approach is essential to avoid costly penalties and reputational damage.
Applicable Legal and Regulatory Frameworks
Various legal and regulatory frameworks govern data protection and privacy, particularly within the context of military and government operations. These frameworks differ by jurisdiction, emphasizing the importance of localized compliance strategies. Key regulations include data protection laws, industry-specific standards, and international agreements.
HP’s GRID for war and Dell’s PalmOne devices are apparently prime targets, mirroring the aggressive tactics of the MPAA. This echoes the broader crackdown on peer-to-peer file sharing networks, with the MPAA launching a barrage of lawsuits and arrests against those facilitating illegal downloads. This ongoing campaign highlights the intense pressure on companies producing and distributing technology used in such networks, potentially impacting the development and accessibility of future HP GRID and Dell PalmOne products.
Compliance Requirements for Data Protection and Privacy
Data protection and privacy requirements mandate the implementation of appropriate security measures, including data encryption, access controls, and regular security audits. Compliance requires rigorous adherence to data minimization, storage limitations, and appropriate disposal procedures. The specific requirements vary depending on the applicable regulations and the nature of the processed data.
Penalties for Non-Compliance with Relevant Regulations
Non-compliance with data protection and privacy regulations can result in significant penalties, ranging from substantial fines to legal action and reputational damage. Penalties often escalate with the severity and duration of the violation. The impact on the organization can be far-reaching, affecting operations, finances, and public trust.
Best Practices for Maintaining Compliance
Maintaining compliance with data protection and privacy regulations necessitates a proactive and ongoing approach. This includes regular security assessments, employee training, and a commitment to ongoing improvement. Documentation of compliance procedures and processes is crucial for demonstrating adherence to relevant regulations. Additionally, staying informed about legislative changes is paramount for continuous adaptation.
Table of Legal and Regulatory Compliance Requirements
| Regulation | Requirement | Impact |
|---|---|---|
| General Data Protection Regulation (GDPR) | Ensure data minimization, data security, and user consent for data processing. Provide transparent information about data handling practices. | Non-compliance can lead to substantial fines, impacting the organization’s reputation and operations. Compliance demonstrates a commitment to data protection. |
| California Consumer Privacy Act (CCPA) | Allow consumers to access, delete, and correct their personal data. Provide transparency regarding data collection and use. | Failure to comply can result in fines and legal action. Compliance fosters trust and demonstrates respect for consumer rights. |
| Health Insurance Portability and Accountability Act (HIPAA) | Implement safeguards to protect sensitive patient health information. Ensure compliance with strict confidentiality and security standards. | Non-compliance can result in substantial penalties and legal ramifications. Demonstrates a commitment to protecting sensitive health data. |
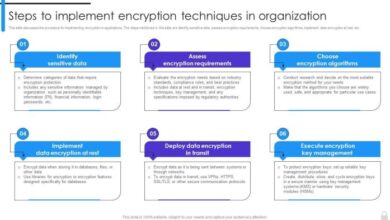
Mitigation Strategies: Hp Girds For War Dell Palmone Are Targets
Protecting critical infrastructure like HP Grid systems for War Dell Palmone requires a multifaceted approach to vulnerability mitigation. A robust strategy considers the interplay of technical solutions, procedural improvements, and ongoing monitoring. This section delves into potential mitigation strategies, comparing their effectiveness, and evaluating the associated costs. Prioritizing these strategies is essential for maintaining operational security and minimizing potential disruptions.
Potential Mitigation Strategies
Various mitigation strategies can be employed to address vulnerabilities in HP Grid systems. These strategies encompass different levels of intervention, from preventative measures to reactive responses. The selection and prioritization of these strategies should be guided by a thorough risk assessment, considering the potential impact of each vulnerability.
Hardware-Based Security Measures
Implementing robust hardware security measures is crucial for protecting the physical integrity of the HP Grid systems. This involves the use of advanced security features within the hardware itself. These measures include employing tamper-proof components, encryption chips, and secure boot processes. Such features help to prevent unauthorized access and modification of critical system components.
- Secure Boot: Enforces a secure boot process by verifying the integrity of the operating system and boot loader. This prevents malicious code from loading during the boot sequence, safeguarding the system from attacks during startup.
- Hardware-Based Encryption: Using encryption chips to protect sensitive data stored on hard drives or other storage devices. This ensures data confidentiality even if the physical device is compromised.
- Tamper-Resistant Components: Employing specialized components that are resistant to physical tampering or modification. This prevents unauthorized physical access and manipulation of critical system components.
Software-Based Security Measures
Implementing robust software-based security measures is equally important for protecting the HP Grid systems. This includes deploying intrusion detection systems, firewalls, and regularly updating software to patch known vulnerabilities.
- Intrusion Detection Systems (IDS): Monitors network traffic for malicious activity and alerts administrators to potential threats. A well-configured IDS can identify and respond to attacks in real-time, mitigating the impact of intrusions.
- Firewalls: Control network traffic by allowing or blocking specific connections based on predefined rules. Implementing firewalls can prevent unauthorized access to the system and limit the spread of malicious activity.
- Regular Software Updates: Ensuring that all software components are updated with the latest security patches. This addresses known vulnerabilities and reduces the attack surface.
Cost Analysis of Mitigation Strategies
Implementing mitigation strategies involves various costs, ranging from the initial investment to ongoing maintenance expenses. Factors such as the complexity of the strategy, the required expertise, and the scale of the deployment significantly influence the overall cost.
- Hardware Costs: Acquiring tamper-resistant components and secure storage devices can be expensive. The cost will vary based on the specific hardware requirements and vendor choices.
- Software Costs: Licensing fees for intrusion detection systems and firewalls can add up. The cost will depend on the features and the number of users.
- Personnel Costs: Implementing and maintaining these strategies may require specialized personnel. Training and expertise in managing these systems will have associated costs.
Effectiveness Comparison
The effectiveness of each mitigation strategy depends on the specific context of the HP Grid systems and the nature of the potential threats. A comprehensive approach combining various strategies will typically provide a more robust defense compared to relying on a single strategy.
Structured Overview of Solutions
A structured overview of solutions to address identified vulnerabilities should include a detailed risk assessment, a prioritized list of mitigation strategies, and a comprehensive implementation plan. The plan should Artikel timelines, responsibilities, and required resources. It should also incorporate regular security audits and penetration testing to assess the effectiveness of the implemented measures.
Future Trends & Predictions

The security landscape for HP Grid systems for War Dell Palmone is constantly evolving, demanding proactive measures to address emerging threats. Understanding future trends and anticipating vulnerabilities is crucial for maintaining a robust security posture. This section explores potential future threats, the evolving nature of security measures, and the impact of emerging technologies on these systems.The future of security for HP Grid systems will involve a complex interplay of technological advancements, evolving threat actors, and the need for adaptable security strategies.
Predicting the precise form of future attacks is impossible, but identifying likely trends and adapting to them is vital for preparedness.
Emerging Threats and Vulnerabilities
The increasing sophistication of cyberattacks necessitates a focus on advanced persistent threats (APTs) and zero-day exploits. Traditional security measures may prove insufficient against these novel attacks, demanding a shift towards proactive and adaptive defenses. Moreover, the rise of AI-powered attacks, including automated phishing campaigns and sophisticated malware, presents a significant concern. These attacks are capable of bypassing traditional security filters and targeting specific vulnerabilities within the HP Grid system.
A key consideration is the potential for attacks leveraging vulnerabilities in interconnected systems and components. The expanding attack surface due to increasing interconnectivity makes targeted attacks more probable.
Future Direction of Security Measures and Best Practices, Hp girds for war dell palmone are targets
Security measures must evolve to address the growing complexity of threats. This necessitates a shift from reactive to proactive security strategies, emphasizing continuous monitoring, threat intelligence gathering, and automated response systems. A focus on zero trust architecture, incorporating micro-segmentation and identity-based access controls, is crucial for limiting the impact of potential breaches. Furthermore, the use of AI and machine learning for threat detection and response is becoming increasingly important.
The ability to learn from past incidents and adapt security protocols in real-time will be critical.
Predictions About the Evolving Threat Landscape
The threat landscape is projected to become more complex and dynamic. Attacks will likely leverage vulnerabilities in emerging technologies, such as the Internet of Things (IoT) and cloud computing. The potential for insider threats will also continue to be a concern, necessitating strong access controls and user awareness training. A growing trend is the use of social engineering tactics to exploit human weaknesses, highlighting the importance of employee training and awareness programs.
The potential for supply chain attacks also remains a significant concern. A well-defined and tested incident response plan is vital for swift and effective mitigation of these potential issues.
Potential Impact of Emerging Technologies on the Security of HP Grid Systems
Emerging technologies, such as cloud computing, IoT devices, and AI, while offering benefits, also introduce new security challenges. Cloud-based services, for example, may expose the HP Grid system to vulnerabilities in the cloud infrastructure itself. The increasing integration of IoT devices can introduce new entry points for attackers. The rise of AI in both offensive and defensive capabilities necessitates a constant adaptation of security strategies.
How to Adapt to Emerging Threats
Proactive adaptation is paramount to mitigating the impact of emerging threats. This involves continuously updating security protocols, implementing advanced threat detection systems, and investing in security training programs for personnel. Furthermore, maintaining open communication channels with relevant stakeholders, such as the vendor, is essential for a coordinated and effective response. Regular vulnerability assessments and penetration testing are critical to identifying and addressing weaknesses before they are exploited.
The implementation of a robust incident response plan, thoroughly tested and regularly updated, is also a key factor.
Last Recap
In conclusion, the security of HP Gird systems in the War Dell Palmone context requires a multi-faceted approach. Understanding the potential vulnerabilities, implementing strong security measures, and developing a robust incident response plan are crucial. Adhering to legal and regulatory compliance is paramount, and adapting to emerging threats is essential. By implementing the mitigation strategies discussed, organizations can significantly reduce the risk of successful attacks and maintain the integrity of these critical systems.