Identity Theft Online Debunking the Myths
Identity theft online debunking the myths is crucial in today’s digital age. This exploration delves into the complexities of online identity theft, examining the various forms it takes and separating fact from fiction. We’ll uncover the truth behind common misconceptions, providing actionable steps to protect yourself and understand the evolving landscape of online fraud.
From defining the different types of online identity theft, like phishing and malware, to explaining the psychological drivers behind these crimes, this comprehensive guide provides a clear understanding of the risks and how to mitigate them. We’ll also examine the role of technology in both perpetrating and preventing online identity theft, exploring future trends and strategies.
Defining Online Identity Theft
Online identity theft is a growing threat in the digital age, encompassing various malicious activities that exploit personal information for fraudulent purposes. It’s not simply a modern-day twist on traditional identity theft; it leverages the unique vulnerabilities of online platforms to achieve its goals. Understanding the nuances of online identity theft is crucial for protecting yourself and your sensitive data.Online identity theft differs from traditional identity theft in its primary vector of attack.
While traditional methods often involve physical documents or direct interaction, online identity theft relies heavily on digital channels and sophisticated techniques to gain access to personal information. This shift in tactics has created new challenges for individuals and organizations to safeguard their digital assets.
Online Identity Theft Process
The process of online identity theft often involves a series of steps. First, the perpetrator gathers information about their target, possibly through social media, public records, or other readily available sources. This reconnaissance phase allows them to tailor their attack to exploit specific vulnerabilities. Second, they employ various tactics to gain unauthorized access to accounts or data.
This could range from phishing emails to sophisticated malware infections. Finally, the perpetrator uses the stolen information for fraudulent activities, like making unauthorized purchases, opening new accounts, or committing financial crimes.
Types of Online Identity Theft
Different types of online identity theft exploit diverse vulnerabilities and methods. Understanding these categories helps individuals and organizations recognize and protect themselves against the various threats.
| Type of Online Identity Theft | Characteristics |
|---|---|
| Phishing | Phishing involves the use of deceptive communications, often via email or text messages, to trick individuals into revealing personal information. These messages frequently mimic legitimate organizations or individuals, creating a sense of urgency or trust to encourage the victim to respond. The goal is to obtain sensitive data such as usernames, passwords, credit card numbers, or social security numbers. A common example is an email that appears to be from a bank asking for account details. |
| Malware | Malware encompasses a range of malicious software designed to infiltrate systems and steal data. This includes viruses, Trojans, ransomware, and spyware. Malware can be installed through malicious websites, infected attachments, or compromised software updates. Once installed, malware can capture keystrokes, monitor online activity, or directly steal sensitive information from the victim’s system. |
| Social Engineering | Social engineering exploits human psychology to manipulate individuals into divulging sensitive information. Attackers often use social engineering tactics to gain access to accounts or networks. These methods rely on psychological manipulation and the exploitation of trust. For instance, a perpetrator might pose as a technical support representative to trick a user into revealing their login credentials. |
Common Myths About Online Identity Theft: Identity Theft Online Debunking The Myths
Online identity theft is a serious concern in today’s digital world, and it’s understandable that many misconceptions surround it. Misinformation can lead to a lack of preparedness and make individuals more vulnerable to attacks. Understanding the true risks and debunking the myths is crucial for safeguarding personal information and financial well-being.
Common Misconceptions
Many people hold false beliefs about the ease and prevalence of online identity theft. These myths can lead to unnecessary anxieties or, worse, a lack of proactive measures. Recognizing these misconceptions is the first step toward effective protection.
- Myth: Online identity theft only affects wealthy individuals or large corporations.
- Reality: Anyone with an online presence, regardless of their financial standing, is vulnerable. Hackers target individuals and businesses indiscriminately, aiming for valuable data such as usernames, passwords, and financial information. Small businesses and individuals can be just as susceptible to attacks as large corporations. The motivation behind attacks is often financial gain, and individuals are just as attractive a target as wealthy individuals.
- Myth: Identity theft only happens to people who click on suspicious links or download malicious software.
- Reality: While clicking on phishing links and downloading malware are common methods, identity theft can occur through seemingly legitimate means. Data breaches at major companies, compromised websites, and even simple social engineering tactics can expose personal information. Phishing attempts are more prevalent than ever, and individuals must stay alert to avoid being caught in these traps. Often, people don’t even realize they’ve been targeted.
- Myth: Robust security software is enough to prevent online identity theft.
- Reality: Strong security software is a crucial part of a comprehensive security strategy, but it’s not a foolproof solution. Cybercriminals are constantly evolving their tactics, and security software needs to be regularly updated to stay ahead of threats. Strong passwords and vigilance are also important factors. Software alone is not sufficient to prevent all attacks.
- Myth: My personal information is safe if I only use secure websites.
- Reality: While using secure websites is essential, hackers can still access personal information through various means, including data breaches at companies handling that data. Even secure websites can be compromised. Data breaches at companies handling sensitive information can expose personal data, and secure websites don’t automatically guarantee complete safety. It’s important to recognize that security is a layered process.
- Myth: It’s impossible to recover from online identity theft.
- Reality: While recovering from online identity theft can be challenging, it’s not impossible. Taking swift action, reporting the theft to relevant authorities, and monitoring financial accounts can help mitigate the damage. Recovery often involves a combination of reporting, financial monitoring, and legal intervention.
Ease of Online Identity Theft
The misconception that online identity theft is easily perpetrated stems from the relative ease of accessing and exploiting personal information online. This ease can be misleading; while the methods are often subtle and sophisticated, they aren’t inherently simple. It’s crucial to understand the methods used and the importance of vigilance.
Comparing Risks and Assumptions
| False Assumption | Real Risk |
|---|---|
| Identity theft is only a concern for tech-savvy individuals. | Anyone with an online presence is at risk. |
| Security software is a guaranteed solution. | Security software needs constant updates and vigilance. |
| Only malicious links pose a threat. | Data breaches and social engineering tactics are also significant risks. |
| Identity theft recovery is hopeless. | Recovery is possible with swift action and reporting. |
| Only large corporations are vulnerable to data breaches. | Small businesses and individuals are equally susceptible. |
Protecting Yourself from Online Identity Theft
Online identity theft is a serious crime that can have devastating consequences. It’s crucial to understand the methods criminals use and to take proactive steps to protect yourself. By understanding the risks and implementing effective security measures, you can significantly reduce your vulnerability to this growing threat.
Crucial Steps to Safeguard Personal Information
Protecting your personal information online requires a multi-faceted approach. Taking these crucial steps can make a substantial difference in your online security.
- Be cautious about what you share online. Avoid posting sensitive information like your social security number, bank account details, or full addresses on public platforms. Be mindful of the information you share on social media and other online forums, as this data can be used to piece together a complete picture of your identity. Limit the information you provide on public websites and online forms to only what is absolutely necessary.
- Use strong passwords and enable two-factor authentication. Use a unique and complex password for each online account. Strong passwords are essential for preventing unauthorized access to your accounts. Two-factor authentication adds an extra layer of security, requiring a second verification method (like a code sent to your phone) in addition to your password. This makes it much harder for attackers to gain access even if they have your password.
- Regularly monitor your accounts for suspicious activity. Check your bank statements, credit reports, and other account activity frequently. Look for any unusual transactions or login attempts. Early detection of suspicious activity allows you to take immediate action and mitigate potential damage.
- Keep your software updated. Regularly update your operating system, web browsers, and other software applications. Updates often include crucial security patches that address vulnerabilities exploited by cybercriminals.
- Be wary of phishing scams. Phishing scams are fraudulent attempts to obtain your personal information. Phishing emails and websites often mimic legitimate organizations. Be cautious of emails or messages asking for personal information, and never click on suspicious links or attachments.
Importance of Strong Passwords and Two-Factor Authentication
Strong passwords and two-factor authentication are essential layers of defense against online identity theft. They make it significantly harder for attackers to access your accounts.
Strong passwords should be unique, complex, and long, incorporating a mix of uppercase and lowercase letters, numbers, and symbols. Never reuse passwords across different accounts. Two-factor authentication adds an extra layer of security, requiring a second verification method in addition to your password. This significantly reduces the risk of unauthorized access even if your password is compromised.
Debunking online identity theft myths is crucial. While scary stories abound, many fears are overblown. Take, for example, the recent news about the MSN Messenger worm wreaking havoc in the new year, msn messenger worm wriggles in new year. While such incidents highlight security vulnerabilities, they don’t automatically translate into personal identity theft. Understanding these nuances is key to staying safe online and not falling prey to misinformation.
Recognizing and Avoiding Phishing Scams
Phishing scams are a common method used by cybercriminals to trick you into revealing your personal information. Recognizing the signs of a phishing scam is crucial for protecting yourself.
Phishing attempts often involve emails or messages that appear to be from legitimate organizations like banks or social media platforms. These messages may contain urgent requests for personal information or threats of account closure. Always be cautious of emails or messages asking for sensitive information, and verify the sender’s authenticity before responding. Do not click on suspicious links or download attachments from unknown sources.
Verify the website’s authenticity before entering any personal information.
Role of Antivirus Software and Firewalls
Antivirus software and firewalls play a crucial role in protecting your computer and network from malicious software and unauthorized access.
Antivirus software detects and removes viruses, malware, and other harmful programs that can compromise your system. Firewalls monitor and control network traffic, blocking unauthorized access attempts. These security tools act as a first line of defense against online threats, preventing malicious software from gaining access to your computer or network and potentially stealing your sensitive data.
Password Management Strategies
Effective password management is essential for protecting your online accounts. Different strategies offer varying levels of security and convenience.
| Strategy | Description | Effectiveness |
|---|---|---|
| Password Manager | Uses a software program to generate and store strong, unique passwords for each account. | High – Provides strong passwords, prevents password reuse, and often includes two-factor authentication. |
| Password Notebook | Manually writing down passwords in a secure location. | Low – Susceptible to loss or theft. |
| Simple Passwords | Using easy-to-remember passwords (e.g., “password123”). | Very Low – Easily guessed by attackers. |
Reporting and Recovery from Identity Theft
Navigating the aftermath of suspected online identity theft can feel overwhelming. Knowing the steps to take, and the resources available, can significantly ease the burden and potentially prevent further damage. This section will detail the crucial steps for reporting and recovery, emphasizing the importance of prompt action.The recovery process from online identity theft requires a multi-faceted approach. It’s essential to act swiftly, documenting every step and contacting the relevant authorities and financial institutions promptly.
By taking proactive measures, you can minimize the impact of the theft and safeguard your future financial well-being.
Unmasking the myths surrounding online identity theft is crucial. While some folks might think that only tech-savvy criminals can pull off identity theft, recent news about a seemingly “helpful hacker” like Adrian Lamo facing federal charges ( helpful hacker Adrian Lamo faces federal charges ) shows that anyone, regardless of their apparent technical skills, can be a target or even a perpetrator.
It’s all about understanding the real risks and taking proactive steps to protect yourself online.
Steps to Take if You Suspect Identity Theft
Understanding the immediate steps is crucial in mitigating the damage from online identity theft. Swift action can limit the negative consequences and prevent further financial loss. This includes promptly reporting suspected fraud to all relevant institutions.
- Document Everything: Keep meticulous records of all fraudulent activity. Note down dates, times, amounts, transaction details, and any communications with fraudulent entities. Take screenshots of suspicious emails, messages, or website interactions. This documentation is critical evidence during the recovery process.
- Contact Financial Institutions Immediately: Notify all affected financial institutions (banks, credit card companies, loan providers) about the suspected identity theft. Explain the situation clearly and request a fraud alert or freeze on your accounts. Each institution will have its own reporting procedures; familiarize yourself with these.
- File a Police Report: Contact your local law enforcement agency and file a police report. This official record serves as crucial documentation for your case and can be instrumental in future investigations.
- Contact Credit Bureaus: Immediately place a fraud alert on your credit reports with the major credit bureaus (Equifax, Experian, and TransUnion). This alert will help to flag any suspicious activity and prevent further unauthorized access.
Contacting Relevant Authorities and Financial Institutions
Understanding the specific procedures for reporting to different authorities and financial institutions is vital. This process involves detailed communication and meticulous record-keeping.
- Financial Institutions: Follow the specific reporting procedures of each financial institution. Most institutions have online portals, dedicated phone lines, or specific email addresses for reporting fraudulent activities. Be prepared to provide supporting documentation, such as transaction details or copies of your identification.
- Law Enforcement: Your local police department is responsible for investigating potential criminal activity related to identity theft. Filing a police report is a crucial step in the recovery process. It helps establish a record of the crime and can be helpful for future investigations or legal proceedings.
- Credit Bureaus: Each credit bureau has its own process for placing a fraud alert or freeze on your credit reports. This process typically involves providing personal information and confirming your identity.
Resources for Victims of Online Identity Theft
Accessing helpful resources can be a significant aid during the recovery process. Organizations and agencies dedicated to identity theft victims offer guidance, support, and assistance.
- Federal Trade Commission (FTC): The FTC is a leading agency for consumer protection. Their website provides valuable information, resources, and reporting procedures for victims of identity theft.
- IdentityTheft.gov: This official government website is specifically designed to help victims of identity theft navigate the recovery process. It offers step-by-step instructions, reporting guidelines, and access to helpful tools.
- Consumer Financial Protection Bureau (CFPB): The CFPB provides consumer protection in financial matters. Their website offers resources on identity theft and steps to take to safeguard your financial well-being.
Agencies and Organizations That Can Help
This table Artikels the key agencies and organizations that can provide support and guidance during the recovery process.
| Agency/Organization | Role |
|---|---|
| Federal Trade Commission (FTC) | Consumer protection, resources, reporting procedures |
| IdentityTheft.gov | Government resource for identity theft victims |
| Consumer Financial Protection Bureau (CFPB) | Consumer protection in financial matters |
| Local Police Department | Investigating potential criminal activity |
| Credit Bureaus (Equifax, Experian, TransUnion) | Placing fraud alerts or freezes on credit reports |
| Financial Institutions (Banks, Credit Card Companies) | Reporting fraudulent activities, account freezes |
The Role of Technology in Combating Online Identity Theft
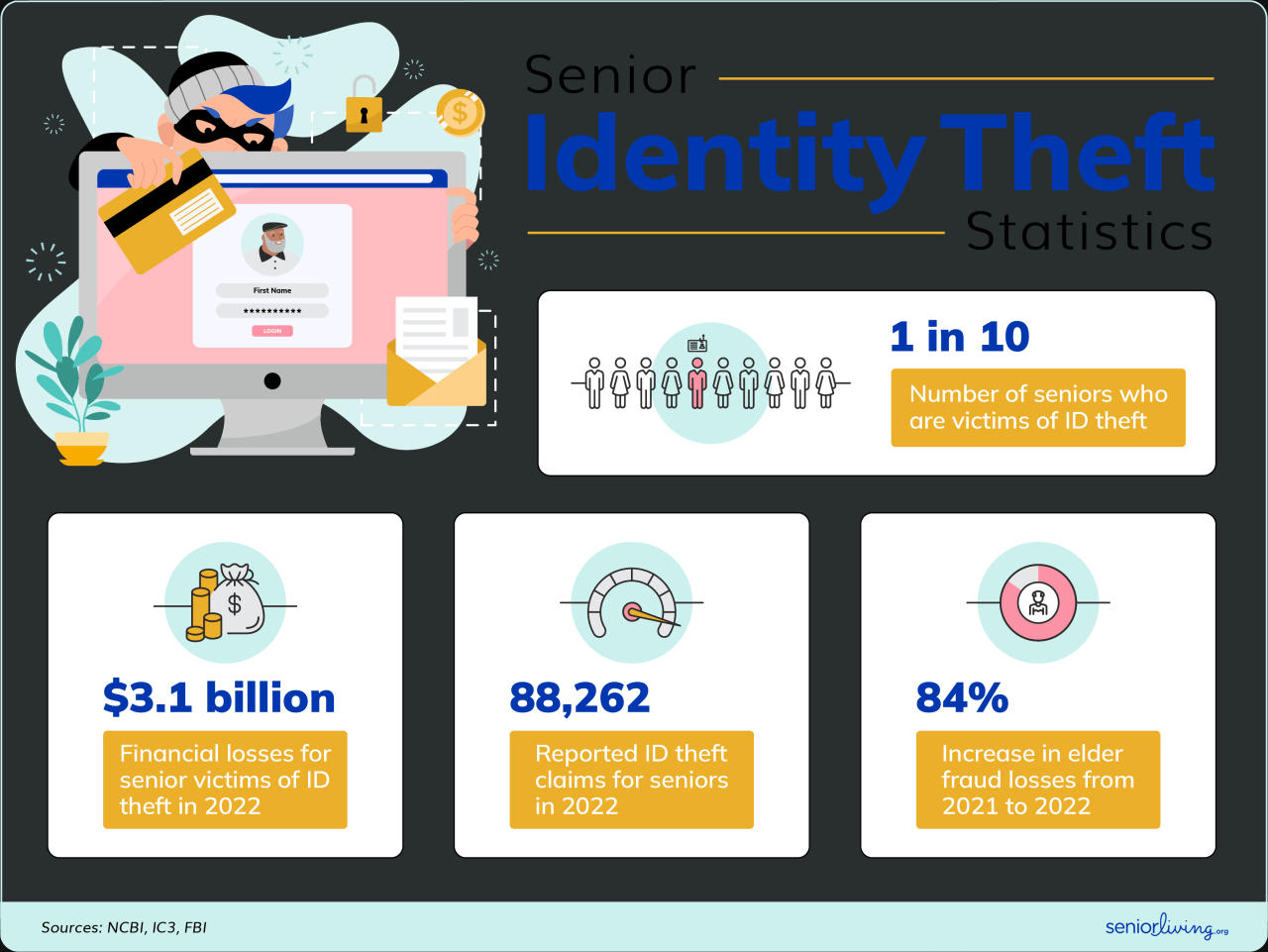
Technology is rapidly evolving, and with it, the tools to combat online identity theft are also becoming more sophisticated. This evolution is crucial as cybercriminals constantly adapt their methods, making it essential for individuals and organizations to stay ahead of the curve. From advanced data analytics to biometric authentication, technology plays a critical role in both preventing and detecting fraudulent activities.
Data Analytics and Machine Learning in Fraud Detection
Data analytics and machine learning are revolutionizing the way online identity theft is detected. Sophisticated algorithms analyze vast amounts of data from various sources, including transaction records, user behavior patterns, and social media activity. By identifying anomalies and unusual patterns, these technologies can flag potential fraudulent activities in real-time. This proactive approach significantly reduces the likelihood of successful identity theft attempts.
For example, a sudden surge in transactions from an unfamiliar location, coupled with unusual login attempts, might trigger an alert, potentially preventing a major financial loss. Machine learning algorithms are continuously learning and improving their ability to detect fraud, adapting to evolving criminal tactics.
Security Software and Services Enhancements
Security software and services are constantly improving their detection capabilities to keep pace with the evolving threat landscape. Sophisticated algorithms and heuristics are embedded within these programs to identify malicious software, phishing attempts, and other online threats. They can also block suspicious websites and emails, protecting users from downloading malware or clicking on malicious links. This ongoing evolution in security software ensures a dynamic defense against the ever-changing tactics of cybercriminals.
Improved algorithms can analyze patterns of user behavior, including unusual login times and locations, to identify and block potential attacks in real-time.
Biometrics for Enhanced Online Security
Biometric authentication methods are emerging as a powerful tool in strengthening online security. Using unique physical characteristics like fingerprints, facial recognition, or voice patterns, these technologies provide a robust layer of security. By requiring a unique biometric input alongside traditional passwords, online platforms can significantly reduce the risk of unauthorized access. This is particularly useful for sensitive financial transactions, where a high level of security is paramount.
This approach effectively prevents unauthorized access by requiring a match between the user’s input and their stored biometric data.
Evolving Technologies in Combating Online Identity Theft, Identity theft online debunking the myths
| Technology | Description | Impact on Identity Theft |
|---|---|---|
| Data Analytics and Machine Learning | Sophisticated algorithms analyze vast datasets to identify unusual patterns and anomalies indicative of fraud. | Proactive detection of fraudulent activities, real-time alerts, and reduced risk of successful attacks. |
| Security Software and Services | Advanced programs and services employing heuristics and algorithms to detect malicious software, phishing attempts, and other threats. | Dynamic defense against evolving cybercriminal tactics, improved protection from malware and phishing attempts. |
| Biometric Authentication | Use of unique physical characteristics like fingerprints, facial recognition, or voice patterns for secure access. | Robust layer of security for sensitive transactions, reduced risk of unauthorized access. |
| Multi-Factor Authentication (MFA) | Requiring multiple forms of verification (e.g., password, code, biometric) for access. | Added layer of security that makes it significantly harder for criminals to gain unauthorized access. |
Illustrative Cases of Online Identity Theft

Online identity theft is a pervasive problem, and understanding real-world examples is crucial to recognizing the risks and vulnerabilities. These cases highlight the devastating impact on victims, demonstrating how seemingly minor online actions can have profound consequences. The following examples illustrate the various tactics used by perpetrators and the importance of vigilance in safeguarding personal information.
Case Study 1: The Phishing Scam
A common tactic involves phishing, where criminals attempt to trick individuals into revealing personal information by mimicking legitimate websites or organizations. This often involves emails, text messages, or fake websites designed to look like trusted platforms. These scams can lead to a variety of fraudulent activities.
Debunking online identity theft myths is crucial. It’s easy to get caught up in the scary stories, but often the reality is less dramatic. For example, a complex grid computing project to predict climate, like the one at grid computing project to predict climate , relies on robust security measures. Ultimately, understanding the true nature of online risks, rather than just the hype, is key to staying safe.
“I received an email that appeared to be from my bank. It asked for my login credentials, and I foolishly provided them. Within days, my account was drained. It was a devastating blow to my financial security, and I had to spend weeks recovering.”
Sarah Miller, fictional victim.
This case illustrates the vulnerability of trusting seemingly legitimate communications. Sarah’s experience underscores the importance of scrutinizing email addresses, website URLs, and the overall design of communications before providing personal information. Phishing attempts often rely on urgency or a sense of authority to pressure individuals into acting quickly.
Case Study 2: The Compromised Account
Hackers often exploit vulnerabilities in online accounts to gain unauthorized access. This can be through weak passwords, compromised websites, or malware. Once inside, perpetrators can steal sensitive information, make unauthorized purchases, or even damage the victim’s reputation.
“My social media account was compromised. The perpetrators posted inappropriate content, and my friends were concerned. The impact on my personal and professional life was considerable. I had to spend time repairing the damage and regaining trust.”
David Chen, fictional victim.
This case highlights the reputational damage and emotional toll that online account compromises can inflict. David’s experience underscores the importance of strong passwords, enabling two-factor authentication, and regularly reviewing account security settings. The impact extended beyond financial loss, affecting his personal and professional standing.
Case Study 3: The Stolen Credit Card
Stolen credit card information is a significant concern in online identity theft. Criminals can use this information to make unauthorized purchases, open new accounts, or apply for loans in the victim’s name. This can lead to substantial financial losses and a lengthy process to clear the victim’s name.
“My credit card information was compromised during an online purchase. I discovered fraudulent charges on my statement, and it took months to resolve the issue. The financial burden was significant, and I had to monitor my credit reports diligently to ensure my identity was protected.”
Emily Rodriguez, fictional victim.
This case demonstrates the devastating financial consequences of stolen credit card information. Emily’s experience emphasizes the importance of monitoring credit reports, disputing fraudulent charges promptly, and utilizing security measures like strong passwords and secure payment methods.
The Psychology of Online Identity Theft
Understanding the motivations behind online identity theft is crucial for developing effective prevention strategies. Beyond the obvious financial gain, a complex interplay of psychological factors drives individuals to commit these crimes. These motivations can range from a desire for power and control to a need for validation or even a misguided sense of entitlement. Examining these underlying psychological factors is key to crafting targeted solutions.The motivations behind online identity theft are varied and complex.
The act is not always driven solely by monetary gain; other factors, such as the thrill of deception, the desire to inflict harm, or a sense of superiority, can also play a significant role. Understanding the nuanced motivations allows for more comprehensive prevention measures that address the root causes rather than just the symptoms.
Motivations for Online Identity Theft
A range of motivations fuels online identity theft, often overlapping and intertwining. Financial gain is a prominent motivator, but not the only one. Some individuals might be driven by a desire to inflict harm or damage on others, perhaps to exact revenge or simply to feel powerful. A sense of superiority or a desire for social status can also lead individuals to commit such crimes, sometimes for recognition or to prove themselves to others.
- Financial Gain: This is a primary driver, but the motivation is often more than just immediate profit. Perpetrators might seek to build credit lines, access loans, or engage in large-scale fraud for significant financial gain.
- Power and Control: The act of deception and manipulation can be intoxicating for some. Gaining access to another person’s identity allows perpetrators to exert a sense of control and power, sometimes over a significant period.
- Revenge or Harm: In certain cases, identity theft is a form of retaliation. Perpetrators might target individuals or groups they perceive as adversaries, aiming to cause distress and disruption.
- Social Status or Recognition: Some perpetrators might engage in identity theft to gain recognition, attention, or a sense of belonging within online communities or criminal networks. This motivation can be driven by a desire to prove themselves or impress others.
Social and Economic Factors Contributing to Online Identity Theft
The social and economic conditions that surround individuals can significantly influence their likelihood of engaging in online identity theft. Economic hardship, lack of opportunities, and social isolation can create a breeding ground for criminal behavior. Exposure to criminal networks and the normalization of unethical practices within certain social circles also contribute to the problem.
- Economic Hardship: Financial pressures can make some individuals more susceptible to criminal opportunities, including online identity theft. The lure of quick wealth or a perceived easy solution to financial problems can outweigh the risks.
- Lack of Opportunities: Individuals who lack access to legitimate opportunities or resources may be more likely to resort to criminal activity. A lack of educational or employment prospects can increase the risk.
- Social Isolation and Marginalization: Social isolation or a feeling of marginalization can create a sense of vulnerability and resentment, potentially leading some individuals to seek power and validation through criminal actions, including online identity theft.
- Exposure to Criminal Networks: Exposure to criminal networks and the normalization of unethical behavior within those circles can significantly increase the likelihood of individuals participating in identity theft.
Developing Prevention Strategies
Understanding the psychological factors driving online identity theft is critical for developing effective prevention strategies. Prevention efforts must consider the multifaceted nature of the motivations and address the underlying social and economic factors. Public awareness campaigns, educational programs, and support systems for vulnerable individuals can all play a role in mitigating the problem.
| Psychological Factor | Influence on Identity Theft |
|---|---|
| Financial Gain | Motivated by immediate or long-term financial gain, potentially through fraudulent activities |
| Power and Control | Driven by a desire to manipulate and control others through deception |
| Revenge or Harm | Motivated by a desire to inflict pain or distress on others |
| Social Status or Recognition | Seek recognition, validation, or belonging within online communities or criminal networks |
Future Trends in Online Identity Theft
The digital landscape is constantly evolving, and so too are the methods employed by cybercriminals to exploit vulnerabilities. Predicting the future of online identity theft requires understanding the ongoing technological advancements and the adaptability of malicious actors. This involves recognizing not only the emergence of new technologies but also the creative ways existing technologies are being weaponized.The evolution of online identity theft is a complex interplay between technological innovation and criminal ingenuity.
The future will likely see a rise in sophisticated and targeted attacks, often leveraging vulnerabilities in emerging technologies. This dynamic environment necessitates a proactive and adaptable approach to safeguarding personal information.
Emerging Technologies and Their Impact
The rise of artificial intelligence (AI) and machine learning (ML) presents both opportunities and threats. AI can be used to automate the process of identifying and exploiting vulnerabilities, allowing criminals to launch highly targeted attacks at scale. For instance, AI-powered phishing campaigns can be personalized to exploit specific individual characteristics and vulnerabilities. Machine learning algorithms can analyze vast datasets to identify patterns and predict future behaviors, enabling more accurate targeting of victims.
Evolution of Tactics and Strategies
Criminals are continuously adapting their tactics and strategies to exploit emerging vulnerabilities. The rise of social engineering and deepfakes is likely to intensify, creating a more sophisticated and challenging environment for individuals and organizations. For example, a deepfake video of a CEO requesting a transfer of funds might be highly convincing and difficult to distinguish from reality. This type of deception can bypass traditional security measures and manipulate individuals into performing actions that compromise their accounts.
Leveraging New Technologies for Protection
Advancements in technology also offer opportunities to combat online identity theft. Biometric authentication, such as facial recognition or fingerprint scanning, can provide a more secure way to verify identities online. Blockchain technology can be used to create secure and transparent records of transactions, making it more difficult to forge or manipulate identities. For instance, blockchain-based solutions can be implemented for secure voting or document verification, potentially mitigating fraud risks.
Shaping the Future of Online Identity Theft
The future of online identity theft is being shaped by a combination of technological developments and criminal motivations. The increasing interconnectedness of devices and systems creates more entry points for attackers, and the sheer volume of data collected and stored online presents a tempting target. The focus on privacy and data security will be crucial in mitigating these risks and safeguarding personal information.
Furthermore, proactive measures by individuals and organizations to enhance security awareness and implement robust security protocols will be essential to mitigate the impact of future threats.
Concluding Remarks
In conclusion, understanding online identity theft requires a multifaceted approach. By debunking the myths and recognizing the real threats, we can equip ourselves with the knowledge to safeguard our digital identities. This guide offers a clear path forward, arming you with practical steps for protection, reporting, and recovery. The future of online security relies on our collective vigilance and understanding of these evolving challenges.