Internet Explorer Security Concerns and Browser Alternatives
Internet Explorer security concerns and browser alternatives are a crucial topic for anyone using the web. From its historical dominance to its eventual decline, understanding the security vulnerabilities and the rise of safer alternatives is vital for navigating the online world safely. This exploration dives into the past, present, and future of web browsing security, highlighting the evolution of browsers and the importance of secure practices.
This discussion examines the security flaws in Internet Explorer, detailing the types of attacks it faced, and contrasts them with the robust security features of modern browsers. We’ll look at popular alternatives, comparing their security, performance, and user experience, ultimately providing you with the knowledge to choose the safest and most suitable browser for your needs.
Historical Context of Internet Explorer
Internet Explorer (IE), once the dominant browser on the desktop, has a rich, yet ultimately faltering history. Its rise to prominence coincided with the early days of the World Wide Web, and its decline reflects the ever-evolving landscape of online security and technological innovation. This exploration delves into IE’s journey, highlighting its vulnerabilities and the factors that led to its eventual obsolescence.The initial success of Internet Explorer was largely due to its integration with Microsoft Windows.
This inherent advantage provided a near-universal presence, creating a network effect that cemented its market share for years. However, this initial dominance proved to be a double-edged sword, as it also made it a prime target for malicious actors.
Evolution and Market Dominance
Internet Explorer’s early versions were released alongside the increasing adoption of the internet. Its integration with Windows OS was a key factor in its rapid market penetration. This tight integration made IE the default browser for many users, effectively creating a barrier to entry for competitors. Its simple interface and compatibility with early web standards contributed to its widespread acceptance.
Microsoft’s continuous development and updates kept it relevant, ensuring that it adapted to the evolving needs of the internet. This period witnessed an increasing number of users relying on IE for their online activities, solidifying its dominance in the browser market.
Internet Explorer’s security issues are well-documented, prompting the need for better alternatives. Thankfully, modern browsers offer significantly improved security. This echoes the struggles of Apple and RealNetworks, as detailed in the article “apple realnetworks live in never never land” apple realnetworks live in never never land. Their past battles highlight the importance of keeping software up-to-date, a key principle for all internet users, and a crucial consideration when choosing a browser.
Security Vulnerabilities
As the internet grew more complex, so did the potential for malicious attacks. The long lifespan of IE, coupled with its widespread adoption, made it a frequent target for hackers. Exploiting vulnerabilities in IE could result in significant damage, affecting both individual users and entire organizations. The table below highlights key security issues across different versions of IE, showcasing the persistent threat landscape it faced.
| Year | Major Version | Key Security Issues |
|---|---|---|
| 1999 | IE 5 | Early versions of IE had limited security features, leading to issues like cross-site scripting (XSS) and buffer overflows. These vulnerabilities could allow attackers to inject malicious code into web pages, compromising user data or hijacking sessions. |
| 2003 | IE 6 | This version faced numerous security flaws, including vulnerabilities related to ActiveX controls. These flaws could enable attackers to execute arbitrary code on users’ machines, resulting in system compromise. The notorious “worm” attacks of the time often targeted IE 6 due to its widespread use. |
| 2006 | IE 7 | While a significant improvement over previous versions, IE 7 still contained some vulnerabilities. The security improvements were often reactive to previously discovered vulnerabilities, highlighting the ongoing challenge of patching and defending against evolving attacks. |
| 2009 | IE 8 | IE 8 saw a continued effort to address security issues, particularly concerning browser exploits. The increase in sophistication of online attacks required the development of increasingly robust security mechanisms. |
| 2011 | IE 9 | Security updates were a priority for this version, but it’s important to note that the constant threat landscape of vulnerabilities required ongoing attention. This underscores the need for constant security updates to address newly discovered flaws. |
| 2013 | IE 10 & 11 | Security measures were further enhanced in these versions, reflecting the ongoing evolution of web threats. However, the shift towards more modern browsers like Chrome and Firefox was already underway, impacting IE’s relevance. |
| 2015 | IE 11 | IE 11, while featuring improved security, was no longer the dominant player in the browser market. The prevalence of alternative browsers, and the shift toward modern web standards, contributed to IE’s gradual decline. |
Factors Contributing to Decline
The increasing sophistication of web technologies and the rise of competitors like Firefox and Chrome played crucial roles in IE’s decline. These competitors often prioritized compatibility with modern web standards and offered improved performance. Users were often drawn to the enhanced functionality and faster speeds offered by the alternatives. The emergence of new web standards and features that IE struggled to keep pace with further contributed to its declining user base.
Finally, the shift toward mobile browsing and the growing importance of responsive web design further diminished the relevance of a desktop-centric browser like IE.
Internet Explorer’s security concerns are well-documented, prompting the search for safer alternatives. Recent news about an online extortion bust, highlighting the significant profit motive behind such crimes, like this one , underscores the importance of strong online security practices. This, in turn, further emphasizes the need to ditch outdated browsers like Internet Explorer in favor of more secure options.
Security Concerns of Internet Explorer
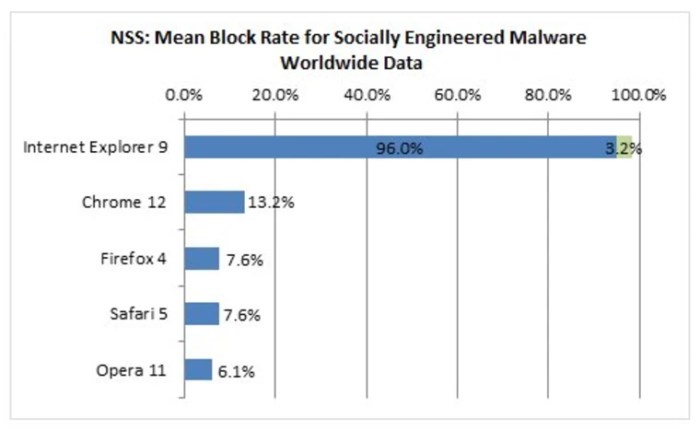
Internet Explorer, once the dominant browser, faced numerous security vulnerabilities throughout its lifespan. These weaknesses, often exploited by malicious actors, created significant risks for users, impacting data privacy and system integrity. Understanding these vulnerabilities is crucial for evaluating the risks associated with older browsers and for highlighting the importance of adopting more secure alternatives.The prevalence of outdated software and the slow pace of security updates in older browsers like Internet Explorer created a fertile ground for exploitation.
These vulnerabilities, often unknown to the average user, allowed attackers to gain unauthorized access to systems and data. The lack of robust security features and the reliance on older, less-secure technologies in Internet Explorer contributed significantly to the rise in successful cyberattacks targeting users of this browser.
Significant Security Flaws
Internet Explorer suffered from a multitude of security flaws, ranging from vulnerabilities in its rendering engine to outdated security protocols. These vulnerabilities were often exploited by malicious actors seeking to compromise user systems. A key factor contributing to these issues was the long period of time the browser remained in use, leading to a substantial backlog of known vulnerabilities that remained unpatched.
This extended period of exposure increased the attack surface and created a prolonged window of opportunity for hackers to exploit these weaknesses.
Types of Attacks Targeting Internet Explorer
Malicious actors employed various tactics to exploit Internet Explorer’s vulnerabilities. Malware infections were common, often delivered through malicious websites or infected attachments. Phishing attempts, designed to trick users into revealing sensitive information, were also a significant threat. These attacks targeted user credentials, financial information, and other sensitive data. Attackers often disguised malicious content as legitimate websites or documents to increase their success rate.
The ease of access to exploits and tools used for these attacks, combined with the broad user base of Internet Explorer, made these browsers a prime target.
Impact on User Data and Privacy
The security concerns surrounding Internet Explorer had a direct impact on user data and privacy. Compromised systems could lead to the theft of sensitive information, including financial details, passwords, and personal data. This information could then be used for fraudulent activities, identity theft, or other malicious purposes. The potential for financial losses, reputational damage, and emotional distress associated with these attacks were significant concerns for Internet Explorer users.
Comparison of Security Vulnerabilities
| Vulnerability Type | Potential Impact | Common Attack Vectors |
|---|---|---|
| Cross-Site Scripting (XSS) | Allows attackers to inject malicious scripts into legitimate websites, potentially stealing cookies or redirecting users to fraudulent sites. | Malicious websites, infected links, or social engineering tactics. |
| SQL Injection | Allows attackers to manipulate database queries, potentially gaining access to sensitive data or executing commands on the server. | Input fields on websites that interact with databases. |
| Buffer Overflow | Allows attackers to overwrite memory regions, potentially causing program crashes or allowing the execution of malicious code. | Maliciously crafted input data, specifically those designed to exceed the allocated memory buffer. |
| Remote Code Execution (RCE) | Allows attackers to execute arbitrary code on a victim’s system, granting full control. | Exploiting vulnerabilities in software components, leading to the execution of malicious code on the target system. |
Browser Alternatives to Internet Explorer
Internet Explorer, while once the dominant web browser, has fallen out of favor due to its security vulnerabilities and outdated technology. Modern browsers offer significant improvements in security, performance, and user experience, making them superior alternatives. This section explores popular browser alternatives, comparing their strengths and weaknesses, particularly in the crucial area of security.Choosing a browser is no longer a simple decision.
Security is paramount, and performance impacts productivity. The right choice depends on individual needs and priorities. This exploration will highlight the key differences between prominent alternatives to Internet Explorer.
Popular Browser Alternatives
Internet Explorer’s decline paved the way for a multitude of powerful and secure browser options. Here are some of the most popular alternatives, each with unique strengths and weaknesses.
- Google Chrome: Known for its speed and extensive extensions, Chrome offers a vast library of add-ons and a highly polished user interface. However, its resource consumption can be high, and security relies on the reliability of the extensions installed.
- Mozilla Firefox: A strong contender for security-conscious users, Firefox prioritizes privacy and customization. It’s often lauded for its robust security features, but some users find its interface less intuitive than Chrome’s.
- Microsoft Edge: Microsoft’s own replacement for Internet Explorer, Edge incorporates modern web standards and improved security. It integrates well with other Microsoft products and offers a streamlined user experience. However, its popularity is still growing, and user reviews are mixed regarding its features and security.
- Safari: The default browser for macOS and iOS devices, Safari focuses on stability and security. Its performance on non-Apple platforms is less consistently strong, and the interface might not be as customizable as other options.
Security Features Comparison
Security is a primary concern when choosing a web browser. Each alternative has its own approach to security, with varying strengths and weaknesses.
- Chrome: Chrome’s security relies on a combination of built-in protections and frequent updates. Its sandboxing mechanism isolates potentially malicious websites, reducing the risk of infections. However, extensions can pose security risks if not properly vetted.
- Firefox: Firefox prioritizes user privacy with features like enhanced tracking protection and built-in security tools. It regularly updates its security infrastructure to combat emerging threats. The user experience is typically streamlined for privacy features.
- Edge: Edge boasts built-in security features like phishing and malware protection, alongside regular updates. Its integration with Windows security features provides a holistic approach. The user reviews for Edge regarding security are still developing.
- Safari: Safari is known for its strong security posture, particularly on macOS and iOS. It incorporates features like phishing and malware detection and has a robust update system. Its security is typically more tailored to the Apple ecosystem.
Performance and User Experience
Performance and user experience vary significantly across different browsers. Each browser is optimized for a specific set of characteristics.
While Internet Explorer’s security concerns are well-documented, finding a suitable replacement browser is key. With the increasing speed of Wi-Fi standards, like the exciting new developments in work on higher speed wlan standard begins , modern browsers are better equipped to handle the demands of the internet, making choosing a secure and reliable alternative a critical step for any user.
So, ditch the outdated and focus on a modern browser that offers the protection you need!
- Chrome: Chrome’s speed and responsiveness are often praised. Its extensive extensions and features, however, can lead to higher resource consumption.
- Firefox: Firefox often prioritizes privacy and security over maximum speed, which might result in a slightly slower experience for some users. However, it’s generally stable and reliable.
- Edge: Edge strives for a balance between performance and user experience. It aims to be fast and responsive while maintaining a streamlined design.
- Safari: Safari’s performance is generally excellent on Apple platforms, offering a smooth and responsive experience. However, performance on non-Apple platforms may vary.
Browser Feature Comparison Table
This table summarizes the key features, security ratings, and user reviews for each browser. These ratings and reviews are based on various independent sources.
| Browser | Security Rating (Average) | Performance (Average) | User Reviews (Average) | Key Features |
|---|---|---|---|---|
| Chrome | 4.5/5 | 4.4/5 | 4.3/5 | Speed, Extensions, Vast ecosystem |
| Firefox | 4.6/5 | 4.2/5 | 4.4/5 | Privacy, Customization, Security Focus |
| Edge | 4.3/5 | 4.3/5 | 3.8/5 | Integration, Modern Design, Microsoft Ecosystem |
| Safari | 4.7/5 | 4.5/5 | 4.6/5 | Stability, Apple Ecosystem, Security Focus |
Security Features of Modern Browsers
Modern web browsers have significantly evolved in their security capabilities, offering robust protection against a wide array of online threats. These enhanced features play a crucial role in safeguarding user data and preventing malicious activities, making the browsing experience safer and more reliable. This evolution reflects the increasing sophistication of cyber threats and the ongoing efforts to counter them.The security features in modern browsers, particularly those based on the Chromium engine, are multifaceted and designed to protect users from various online threats, such as phishing attempts, malware infections, and data breaches.
These measures are constantly updated to address emerging vulnerabilities and threats. They also integrate seamlessly with operating system security features to provide a comprehensive defense layer.
Advanced Threat Protection
Modern browsers employ sophisticated mechanisms to identify and block malicious websites and downloads. This involves analyzing the code and content of websites and files in real-time to detect potentially harmful elements. For example, if a website is identified as a phishing site, the browser can block access to it, preventing users from entering their credentials on fraudulent pages.
Enhanced Scripting Controls
Browsers implement strict controls over scripting languages like JavaScript to mitigate the risk of malicious code execution. These controls help prevent cross-site scripting (XSS) attacks, where attackers inject harmful scripts into legitimate websites to steal user data or compromise systems. The browser can restrict the behavior of scripts originating from untrusted sources, limiting their ability to access sensitive information or perform unauthorized actions.
Privacy Enhancements
Modern browsers offer various privacy features, such as enhanced cookie management, tracking prevention, and the ability to control data collection by third-party websites. These features protect user data from being tracked across multiple websites, reducing the risk of targeted advertising and unauthorized data collection. For instance, browsers can block third-party cookies by default, limiting the ability of websites to follow users across the internet.
Improved Malware Detection
Modern browsers incorporate sophisticated algorithms to detect and block malware, including viruses, spyware, and ransomware. The browser can scan downloaded files and websites for known malicious patterns and signatures, alerting the user and blocking access to harmful content. This proactive approach prevents potential infections before they can cause harm.
Security Feature Comparison Table
| Security Feature | Function | Example Use Case |
|---|---|---|
| Advanced Threat Protection | Identifies and blocks malicious websites and downloads. | Preventing access to a phishing website that attempts to steal login credentials. |
| Enhanced Scripting Controls | Restricts malicious code execution from scripts. | Blocking a cross-site scripting (XSS) attack that injects harmful code into a website. |
| Privacy Enhancements | Controls data collection by third-party websites. | Blocking third-party cookies to prevent tracking across multiple websites. |
| Improved Malware Detection | Detects and blocks malicious software like viruses and ransomware. | Blocking a download that contains a virus. |
User Adoption of Browser Alternatives
The shift away from Internet Explorer (IE) and towards modern browsers was a gradual process, driven by a confluence of factors. Users, initially comfortable with the familiar, were increasingly influenced by the demonstrably superior security features of alternative browsers. This evolution was not merely a technical upgrade; it was a shift in user behavior influenced by tangible benefits.The rise of security threats and the vulnerabilities inherent in IE played a significant role in pushing users toward more secure alternatives.
As internet usage expanded and became more crucial, users recognized the importance of a strong security posture, leading to a greater awareness and demand for robust browsing solutions.
Factors Influencing User Migration
A variety of factors contributed to the migration away from IE. Security concerns, as previously mentioned, were paramount. The perceived instability and vulnerability of IE, compared to the newer browsers, influenced user decisions. Furthermore, the lack of support for newer web standards and technologies also played a role. The limited compatibility with the evolving web environment often led users to seek more up-to-date alternatives.
Security Concerns as a Driver
The increasing frequency of malware attacks and the growing sophistication of online threats highlighted the critical need for stronger security measures. IE, due to its age and inherent vulnerabilities, was often identified as a significant security risk. Users, faced with the potential for data breaches and system compromises, were motivated to adopt browsers with enhanced security features.
Browser Market Share Trends, Internet explorer security concerns and browser alternatives
The decline of IE’s market share was a clear indicator of the shift in user preference. A graphical representation, showcasing the evolution of market share for various browsers, would illustrate the steep decline of IE and the subsequent growth of its alternatives. This decline was not instantaneous; it unfolded gradually over several years. Early adopters of alternative browsers often cited security and compatibility issues as key reasons for the switch.
Illustrative Example of Market Share Shift
| Year | Internet Explorer | Chrome | Firefox | Other |
|---|---|---|---|---|
| 2010 | 50% | 10% | 25% | 15% |
| 2015 | 25% | 35% | 25% | 15% |
| 2020 | 5% | 65% | 20% | 10% |
This simplified table demonstrates a hypothetical trend, illustrating the decreasing dominance of IE and the increasing popularity of Chrome and Firefox. Real-world data would likely show a more nuanced picture, but the overall pattern of IE’s decline and the rise of modern browsers would remain consistent.
Best Practices for Secure Web Browsing: Internet Explorer Security Concerns And Browser Alternatives

Navigating the internet safely is crucial in today’s digital world. While choosing a secure browser is important, adopting robust online habits is equally vital for protecting your personal information and preventing unwanted intrusions. This post delves into fundamental best practices for secure web browsing, regardless of the specific browser you use.A strong online presence necessitates more than just a secure browser.
It demands a proactive and informed approach to online security. By understanding and implementing these best practices, you significantly reduce your vulnerability to cyber threats.
Strong Passwords
Creating and managing strong passwords is fundamental to online security. Weak passwords are easily cracked, exposing your accounts and personal data to potential harm.
- Use strong passwords: Avoid easily guessed words, names, or dates. Instead, opt for unique, complex passwords incorporating a mix of uppercase and lowercase letters, numbers, and symbols. A strong password should be at least 12 characters long.
- Employ a password manager: Dedicated password managers can generate and store strong, unique passwords for all your accounts. They securely store these passwords, making it easy to log into websites and applications without compromising security.
- Regularly change passwords: Change your passwords periodically, especially for sensitive accounts like banking or email, to minimize the risk of unauthorized access in case of a security breach.
Regular Software Updates
Keeping your software, including your browser and operating system, updated is critical. Updates often patch security vulnerabilities that hackers can exploit.
- Enable automatic updates: Most browsers and operating systems offer automatic update features. Activating these features ensures that you’re always running the latest version with the most current security patches.
- Check for updates regularly: Even with automatic updates enabled, it’s good practice to periodically check for available updates to ensure you’re not missing any critical security patches.
- Install security updates promptly: Once an update is available, install it as soon as possible to safeguard your system from known vulnerabilities.
Cautious Online Behavior
Being cautious about what you click on and share online is a crucial aspect of safe browsing. This includes avoiding suspicious links, attachments, and websites.
- Verify website security: Look for the padlock icon in the address bar to confirm that a website is using a secure connection (HTTPS). This protects your data during transmission.
- Avoid suspicious links and attachments: Do not click on links or open attachments from unknown or untrusted sources. Phishing attacks often employ deceptive tactics to trick you into revealing personal information.
- Be mindful of what you share online: Think carefully before sharing personal information, such as your address, phone number, or financial details, on social media or public forums. Protect your privacy by limiting the information you share publicly.
Security Tools and Extensions
Utilizing security tools and browser extensions can enhance your online safety. These tools can provide an extra layer of protection against malware and phishing attempts.
| Practice | Description | How to Implement |
|---|---|---|
| Antivirus Software | Protects your system from malware and viruses. | Download and install reputable antivirus software from a trusted vendor. |
| Anti-Phishing Extensions | Identifies and blocks suspicious websites. | Install anti-phishing extensions for your browser. |
| Firewall | Protects your computer from unauthorized network access. | Ensure your operating system has a firewall enabled and properly configured. |
| VPN (Virtual Private Network) | Encrypts your internet traffic and masks your IP address. | Download and install a VPN client. |
Future of Web Browsing Security
The digital landscape is constantly evolving, and with it, the nature of security threats targeting web browsers. As more sophisticated attacks emerge, browsers must adapt and proactively defend against them. This evolution necessitates a deep understanding of the future threats and the development of innovative security measures.The increasing reliance on the internet for critical tasks, from banking to healthcare, demands a robust and adaptive approach to security.
This necessitates not just reactive measures, but proactive strategies that anticipate and mitigate emerging threats before they impact users. Predicting the future of web browsing security is crucial for staying ahead of the curve.
Ongoing Evolution of Security Threats
The threat landscape is constantly evolving, shifting from traditional malware to more sophisticated attacks. Phishing campaigns are becoming more personalized and convincing, leveraging artificial intelligence to tailor messages to individual users. Zero-day exploits, vulnerabilities unknown to security researchers, pose a significant threat as they are not patched until they are discovered in the wild. Furthermore, the rise of cryptojacking, where malicious actors leverage user resources for cryptocurrency mining, is another significant concern.
The sophistication of these threats requires constant vigilance and innovative countermeasures.
Measures to Address Emerging Threats
Web browser developers are actively working on multiple fronts to address these evolving threats. Advanced threat detection systems are being integrated into browsers to identify and block malicious activity. Machine learning algorithms are being used to analyze user behavior and identify potential threats in real-time. Sandboxing techniques are being enhanced to isolate potentially harmful websites and scripts, preventing them from impacting the entire system.
Furthermore, improved security protocols are being implemented to secure user data and transactions. This proactive approach is crucial to mitigating the increasing sophistication of attacks.
Predictions for Future Security Enhancements
Future security enhancements in web browsers are likely to involve more sophisticated AI-driven threat detection, proactive threat intelligence, and advanced sandboxing techniques. Integration of hardware-level security features could further enhance protection against sophisticated attacks. Improved user authentication methods, such as biometrics and multi-factor authentication, will become even more prevalent, bolstering the security of user accounts. The focus will be on layered security approaches, combining multiple techniques to provide a comprehensive defense against a multitude of threats.
Future Web Browser Security Needs and Potential Solutions
| Security Need | Potential Solution |
|---|---|
| Enhanced detection of zero-day exploits | Integration of real-time threat intelligence feeds and advanced machine learning models that identify and flag potentially malicious code patterns in real time. |
| Improved protection against AI-powered phishing attacks | Advanced behavioral analysis and machine learning algorithms that can detect anomalies in user behavior, flagging potential phishing attempts and alerting users to suspicious activity. |
| Protection against cryptojacking | Enhanced resource monitoring and isolation capabilities to prevent malicious scripts from accessing and exploiting system resources for cryptocurrency mining. |
| Enhanced privacy controls | Advanced privacy-enhancing technologies, such as encrypted DNS lookups and enhanced tracking prevention mechanisms, will be crucial for maintaining user privacy. |
Closure
In conclusion, the shift away from Internet Explorer underscores the critical importance of robust security in web browsers. Modern alternatives offer significantly enhanced protection against evolving online threats. This exploration emphasizes the need for vigilance in online practices, strong passwords, and regular software updates. Choosing a secure browser and following best practices are essential for safeguarding your online experience.