Is Your Site Under Attack? A Deep Dive
Is your site under attack? This comprehensive guide explores the various methods attackers use to target websites, from common attack vectors to effective response strategies. We’ll delve into identifying potential threats, assessing website health, analyzing logs, understanding traffic patterns, and implementing security measures. It’s crucial to understand the potential for malicious activity and how to mitigate it.
We’ll analyze common attack methods like DDoS, SQL injection, and malware, outlining their characteristics, symptoms, and potential severity. Then, we’ll equip you with practical steps to assess your website’s health, monitoring traffic patterns, and reviewing logs for suspicious activity. This exploration concludes with a discussion on proactive security measures and strategies for responding to attacks.
Identifying Potential Attacks
Understanding the various ways your website can be targeted is crucial for proactive security. Knowing the methods attackers employ allows you to implement preventative measures and respond effectively should an attack occur. A comprehensive understanding of attack vectors empowers you to safeguard your online presence and protect valuable data.The digital landscape is rife with malicious actors seeking vulnerabilities in websites.
These attackers employ a range of tactics, from sophisticated exploits to brute-force attacks. Proactively identifying potential threats is essential to mitigating risks and maintaining a secure online environment.
Common Website Attack Vectors
Common attack vectors exploit vulnerabilities in web applications or server infrastructure. These methods can compromise data, disrupt service, or even cause financial loss. Understanding these methods allows you to implement preventative measures to avoid falling victim to these attacks.
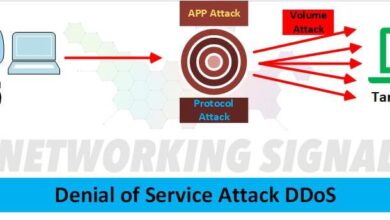
- Distributed Denial-of-Service (DDoS) Attacks: DDoS attacks overwhelm a website with a massive influx of traffic from multiple sources, effectively shutting it down. This flood of requests renders the server unable to handle legitimate traffic, impacting users’ ability to access the website.
- SQL Injection Attacks: SQL injection attacks exploit vulnerabilities in database queries. Attackers insert malicious code into input fields, allowing them to manipulate database information, gain unauthorized access, or even delete data.
- Malware Infections: Malware, such as viruses, worms, or trojans, can infect your website or server. These malicious programs can cause significant damage, leading to system errors, data breaches, and even complete system compromise.
- Cross-Site Scripting (XSS) Attacks: XSS attacks inject malicious scripts into websites viewed by other users. These scripts can steal cookies, redirect users to malicious sites, or deface web pages.
- Cross-Site Request Forgery (CSRF) Attacks: CSRF attacks trick users into performing unwanted actions on a website they are authenticated on. Attackers can manipulate a user’s browser to submit requests to the targeted website without the user’s knowledge or consent.
Types of Malicious Activity
Various forms of malicious activity can indicate a website is under attack. Recognizing these signs is crucial for immediate action. These activities can range from minor annoyances to significant security breaches.
- Unauthorized Access: Unauthorized access to sensitive data or system resources is a clear sign of a security breach. This can involve accessing user accounts, modifying website content, or stealing confidential information.
- Data Manipulation: Malicious actors might manipulate data on your website, including altering product listings, modifying user accounts, or deleting crucial information. This activity often leads to financial losses or reputational damage.
- Service Disruption: Disruptions to website functionality, such as slow loading times, inability to access specific pages, or complete website downtime, can indicate an ongoing attack.
Attack Method Characteristics and Symptoms
This table provides a summary of common attack methods, their characteristics, and typical symptoms. Understanding these patterns is crucial for identifying and responding to attacks. Recognizing the specific patterns of each attack is vital for implementing appropriate countermeasures.
Is your site under attack? Security concerns are constantly evolving, and with the recent news of an e-voting expert and critic urging e-vote hacking, e voting expert and critic urges e vote hacking , it’s more important than ever to stay vigilant. This highlights the critical need for robust security measures, especially for sensitive data, and reinforces the importance of ongoing monitoring for potential threats to your site’s integrity.
| Attack Type | Characteristics | Symptoms | Severity |
|---|---|---|---|
| DDoS | Large-scale, distributed denial-of-service attacks; multiple sources overwhelm the target server. | High traffic volume, slow website response, website becoming unavailable to legitimate users. | High |
| SQL Injection | Exploiting vulnerabilities in database queries; malicious code injected into input fields. | Data breaches, unauthorized access to sensitive data, changes in database content. | High |
| Malware | Malicious software designed to harm systems; can alter website functionality or steal data. | Unexpected changes to website content or functionality, system errors, performance issues, suspicious files or processes. | High |
Assessing Website Health
Maintaining a healthy website is crucial for optimal performance and security. Regular checks for anomalies in traffic patterns, server resources, logs, and security configurations are vital to proactively identify and address potential issues. This proactive approach minimizes downtime, prevents data breaches, and ensures a positive user experience.
Is your website under attack? Sometimes, subtle signs can be hard to spot, like a sudden spike in traffic or unusual error messages. Think about Mount St. Helens, a telemetric volcano – its activity is closely monitored using sensors to predict eruptions. Similarly, proactive monitoring for your site can help identify and mitigate potential attacks before they cause significant damage.
Understanding the signals and patterns, like a telemetric volcano, can help you respond quickly if your site is under attack. mount st helens a telemetric volcano
Monitoring Website Traffic Patterns
Website traffic patterns offer valuable insights into the health of your site. Significant deviations from normal behavior can signal issues, from a surge in legitimate traffic to malicious activity. Regular monitoring allows for quick identification of unusual patterns, enabling timely intervention.
- Identify typical traffic patterns: Analyze historical data to establish baseline metrics for daily, weekly, and monthly traffic. Consider factors like time of day, day of the week, and seasonal trends.
- Detect sudden spikes or drops: Implement tools to monitor real-time traffic. A sudden increase in traffic might indicate a surge in legitimate user interest, a successful marketing campaign, or potentially a distributed denial-of-service (DDoS) attack. A sharp decline might point to a problem with your website or service outages.
- Track traffic sources: Analyze where your traffic is coming from. Significant shifts in traffic sources might reveal new marketing opportunities or potential threats. For example, a sudden increase in traffic from unusual or unknown locations warrants investigation.
Monitoring Server Resources
Server resources, including CPU, memory, and bandwidth, are critical indicators of website health. Surges or unusual activity in these areas can be early warning signs of issues like resource exhaustion or attacks. Proactive monitoring ensures the website remains responsive and available.
Is your website under attack? If you’re still using Internet Explorer, you might want to take a closer look at your security posture. Outdated browsers like Internet Explorer pose significant risks, leaving your site vulnerable to attacks. Consider switching to more secure alternatives like Google Chrome or Firefox to fortify your online defenses. Learn more about internet explorer security concerns and browser alternatives here.
Ultimately, a strong security strategy is key to protecting your site from malicious actors.
- Establish baseline resource usage: Collect data on typical CPU, memory, and bandwidth usage. This baseline will be essential for comparison when unusual activity is detected.
- Identify resource spikes: Implement monitoring tools to track server resource usage in real-time. Tools should be able to alert you when CPU usage exceeds a certain threshold or memory usage approaches saturation. Unexpected spikes should be investigated immediately.
- Analyze bandwidth usage: Keep a close eye on bandwidth consumption. Abnormally high bandwidth usage could indicate a denial-of-service attack, excessive data transfer, or other issues. For example, high bandwidth usage coupled with unusual traffic patterns might suggest a malicious actor attempting to overwhelm the server.
Examining Website Logs
Website logs are valuable records of activity on your site. They provide a detailed history of user interactions, requests, and errors. Regular review allows you to identify suspicious activity and potential vulnerabilities.
- Regular log file analysis: Implement a scheduled process to review website logs for unusual activity. This could include looking for error messages, unusual access patterns, or suspicious user agent strings.
- Identify unusual access patterns: Analyze log files for unusual access patterns, such as unusually high login attempts, unusual user agents, or access from unusual IP addresses.
- Look for error messages: Analyze log files for recurring error messages, which may indicate underlying technical issues. These issues could include database problems or server configuration errors.
Reviewing Website Security Configurations
Regularly reviewing your website’s security configurations is essential for maintaining a secure environment. Outdated or improperly configured settings can create vulnerabilities that attackers can exploit.
- Regular security configuration checks: Conduct regular checks on the security configurations of your website. This includes firewalls, intrusion detection systems, and other security measures.
- Identify outdated security measures: Ensure that your website uses the latest security patches and updates. Outdated software can contain vulnerabilities that attackers can exploit. Example: A server running an outdated version of Apache might have known vulnerabilities.
- Review firewall rules: Review firewall rules to ensure they are appropriately configured and block known malicious traffic. Firewall rules should be reviewed regularly to ensure they are up-to-date.
Analyzing Website Logs: Is Your Site Under Attack
Website logs are invaluable records of activity on your site. They provide a detailed history of user interactions, requests, and server responses. Understanding the data within these logs is crucial for identifying potential security threats and maintaining a healthy website. By carefully examining these records, you can uncover patterns and anomalies that might signal an attack.Analyzing website logs is like deciphering a complex code, but one that holds the key to your site’s security.
Each entry in the log represents an event, from a simple page view to a more intricate database query. By identifying unusual patterns, unusual IP addresses, and excessive requests, you can potentially catch malicious activity early.
Typical Website Access Log Data
Website access logs record various details about every request made to your server. These logs typically include the date and time of the request, the client’s IP address, the requested URL, the HTTP method used (e.g., GET, POST), the status code returned by the server, and the size of the response. This wealth of information can be crucial in identifying unusual behavior.
Potential Indicators of Attacks in Access Logs
Certain patterns in access logs can strongly suggest malicious activity. Careful observation of these anomalies can help prevent significant damage.
- Unusual IP Addresses: A sudden surge of requests from an IP address range unfamiliar to your site’s traffic patterns warrants investigation. This could indicate a botnet or automated attack. For example, if your site typically sees traffic from the US and Europe, a sudden influx of requests from countries in Asia or Africa might be suspicious. These unusual IP addresses might originate from compromised devices or malicious actors attempting to overload your server.
- High Volume of Requests from a Single IP: While legitimate users might make multiple requests, a single IP address generating an exceptionally high volume of requests (often referred to as “flooding”) could be a denial-of-service (DoS) attack. This is an attempt to overwhelm your server and render it unavailable to legitimate users. A single user making hundreds of requests per second could indicate malicious activity, while a single user making a dozen or so requests is likely a normal user.
- Unusual Request Patterns: Unusual request patterns, such as repeated attempts to access sensitive files or directories, or requests for files that do not exist, could indicate unauthorized access attempts. This includes trying to access files with specific extensions like .php, .cgi, or .jsp, which are common targets of attacks.
- Unusual User-Agent Strings: The user-agent string identifies the software and browser used by the client. Unusual or fabricated user-agent strings can signal a bot or automated attack. For instance, an attacker might try to mask their activity by using a fake user-agent string, making it harder to identify their origin.
Organizing Website Log Data for Attack Detection
To effectively identify attacks, organizing your website log data is essential. Using log analysis tools, you can filter and sort requests based on various criteria to uncover anomalies.
| Log Entry | Description | Potential Attack Indicator |
|---|---|---|
| 2024-10-27 10:00:00 | IP Address: 192.168.1.100; URL: /admin/config.php; Method: GET | Potentially suspicious, access to sensitive area |
| 2024-10-27 10:01:00 | IP Address: 192.168.1.100; URL: /admin/config.php; Method: GET | Suspicious, repeated attempts from same IP |
| 2024-10-27 10:02:00 | IP Address: 192.168.1.101; URL: /admin/config.php; Method: POST | Potential attempt at unauthorized modification |
Using log analysis tools, you can filter requests by IP address, time period, and HTTP status codes to pinpoint suspicious activities. For example, a high number of 404 errors from a single IP could suggest a brute-force attack or a scan. This systematic approach allows you to effectively detect potential security threats.
Understanding Traffic Patterns
Monitoring website traffic is crucial for detecting potential attacks. Unusual spikes or dips in traffic, combined with other indicators, can signal malicious activity. Understanding typical traffic patterns allows you to quickly identify anomalies and react appropriately. This proactive approach can prevent significant damage to your site’s performance and reputation.Analyzing traffic patterns is like reading a complex story. Each data point contributes to the narrative, revealing trends, seasonality, and, critically, deviations from the norm.
By tracking key metrics and visualizing the data, you can quickly identify suspicious activity and take appropriate measures.
Monitoring Website Traffic Data
Monitoring website traffic data involves systematically tracking various metrics that describe visitor behavior. This includes not just the volume of visitors but also their source, geographic location, and the pages they interact with. By analyzing these metrics over time, you can spot sudden surges or unusual behavior that could indicate a cyberattack. This proactive approach helps you anticipate problems and respond effectively.
Tools and Techniques for Tracking Traffic
Several tools and techniques are available for tracking and visualizing website traffic. Web analytics platforms like Google Analytics, StatCounter, and Adobe Analytics provide comprehensive data on visitor behavior, traffic sources, and geographic distribution. These platforms offer visualizations that make it easier to identify patterns and anomalies.Using tools like Google Analytics, you can create custom reports, filter data by specific timeframes, and generate detailed traffic reports that reveal unusual spikes or dips in traffic.
This detailed information can help pinpoint potential attacks.
Comparing and Contrasting Traffic Monitoring Tools, Is your site under attack
Different tools cater to varying needs and budgets. Google Analytics, for example, offers a free tier with significant functionality, making it a popular choice for many websites. Paid tools like Adobe Analytics provide more advanced features, including custom dashboards and deeper insights into user behavior. The choice of tool depends on the specific requirements and resources of the website.Google Analytics is a robust free option that provides a wealth of data for basic analysis.
It allows you to track key metrics, create reports, and understand traffic patterns. Adobe Analytics, on the other hand, offers a comprehensive suite of features, including custom dashboards, advanced segmentation, and in-depth data analysis. This more robust option is suited for large and complex websites that require advanced analytics.
Website Traffic Analysis Metrics During an Attack
| Metric | Description | Normal Value | Attack Value |
|---|---|---|---|
| Unique Visitors | Number of unique visitors | Moderate | Extreme increase or decrease, or a sudden drop from a consistent high number. |
| Page Views | Number of page views | Moderate | Extreme increase or decrease, particularly on specific pages. |
| Traffic Source | Location of visitors | Balanced across regions | High concentration from specific regions, or from unusual sources (e.g., a sudden increase in traffic from countries with low historical traffic). |
Analyzing these metrics is crucial for identifying patterns indicative of an attack. For example, a sudden surge in traffic from a single country might be a sign of a botnet attack. A dramatic decrease in traffic could suggest a denial-of-service (DoS) attack. By meticulously tracking these metrics and recognizing deviations from normal patterns, you can proactively defend your website.
Security Measures
Protecting your website from attacks requires a multi-layered approach. Simply having a website is not enough; proactive security measures are crucial to safeguarding your online presence. This involves understanding potential threats and implementing strategies to mitigate them. A comprehensive security plan is vital to preventing costly downtime, reputational damage, and data breaches.Implementing robust security measures goes beyond simply installing software.
It requires a proactive and ongoing effort to adapt to evolving threats. This includes regularly updating security protocols, monitoring system logs, and staying informed about emerging vulnerabilities. Regular audits and penetration testing are also essential for identifying and addressing weaknesses before they are exploited.
Common Security Protocols
Various security protocols are essential for website protection. These protocols form a layered defense against attacks, each contributing to a comprehensive security posture. Firewalls and intrusion detection systems are key components in this layered approach.
- Firewalls act as a gatekeeper, controlling incoming and outgoing network traffic. They filter out malicious traffic, blocking unauthorized access attempts. Firewalls can be hardware-based or software-based, each with its own strengths and limitations. Hardware firewalls, for example, offer better performance and security for high-traffic websites, while software firewalls are more suitable for smaller or less demanding sites.
- Intrusion Detection Systems (IDS) continuously monitor network traffic for suspicious patterns or activities. They alert administrators to potential intrusions in real-time, allowing for immediate response and mitigation. IDS systems use various techniques to detect threats, including signature-based detection, anomaly-based detection, and behavioral analysis.
Preventative Measures
Implementing proactive measures is critical to reducing the likelihood of a website attack. These measures are designed to address potential vulnerabilities and enhance overall website security.
- Regular Software Updates: Keeping software up-to-date is crucial. Updates often include critical security patches that address known vulnerabilities. Regularly scheduled updates can prevent attackers from exploiting known weaknesses in older versions of software.
- Strong Passwords and Authentication: Robust passwords are essential for all accounts, including administrative accounts. Multi-factor authentication adds an extra layer of security, requiring more than just a password to log in.
- Secure Configuration: Properly configuring web servers, databases, and other software components is vital. Default settings are often insecure, so tailoring configurations to meet specific security needs is critical.
- Regular Backups: Regular backups are essential for data recovery in case of a cyberattack or system failure. Having a recent backup allows for quick restoration of critical data, minimizing downtime and loss.
- Vulnerability Scanning and Penetration Testing: Regularly scanning for vulnerabilities and performing penetration testing can help identify potential weaknesses before they are exploited. These proactive steps can help pinpoint areas requiring immediate attention.
Security Best Practices
Implementing best practices ensures a higher level of website security. These practices are essential for building a robust and resilient online presence.
- Input Validation: Validating all user inputs prevents malicious code from being executed on your website. This includes preventing SQL injection attacks and cross-site scripting (XSS) attacks.
- Least Privilege Principle: Granting users only the necessary permissions to perform their tasks reduces the impact of a potential compromise. This prevents attackers from gaining unauthorized access to sensitive data.
- Regular Security Audits: Regular security audits help identify and address any weaknesses in your security measures. These audits are vital for maintaining a strong security posture.
- Security Awareness Training: Educating employees about security threats and best practices is essential. A knowledgeable workforce is less likely to fall victim to social engineering attacks or other common vulnerabilities.
Response Strategies
Responding to a suspected website attack requires a swift and organized approach. Proactive measures, like robust security protocols and regular vulnerability assessments, are crucial. However, when an attack does occur, a well-defined response strategy is vital for minimizing damage and restoring functionality quickly. This involves a multi-faceted approach encompassing immediate actions, containment procedures, and communication protocols.A swift and calculated response to a website attack is critical to minimize damage and swiftly restore operations.
This involves several key steps, from isolating the affected areas to contacting the hosting provider or security experts. A documented rapid response plan, readily available to the team, can significantly streamline the process.
Immediate Actions Upon Suspicion
Understanding the warning signs and responding immediately is paramount in mitigating the impact of a cyberattack. Recognizing patterns in website traffic, unusual error messages, or unexpected spikes in resource usage can signal an intrusion. Implementing a monitoring system, which actively tracks and analyzes these metrics, is essential for proactive identification.
- Immediately stop any processes that might be contributing to the attack. For example, if the site is experiencing a denial-of-service attack, halting unnecessary processes will reduce the impact on server resources.
- Implement temporary safeguards, such as blocking access from suspicious IP addresses. This will limit the attack’s scope and prevent further damage.
- Start logging all relevant information. Detailed records of events, errors, and access attempts are vital for investigation and future prevention.
Isolating Affected Areas
Pinpointing the source of the attack and containing its spread is crucial to preventing further damage. Identifying which parts of the website are affected allows for targeted remediation efforts. This isolation process involves temporarily disabling or restricting access to affected areas.
- Identify the specific components or modules of the website that are under attack. For example, a specific form, a particular page, or an entire section might be targeted. Analyzing the error logs and monitoring tools can provide clues.
- Implement temporary restrictions. This might involve blocking access to the affected area through a firewall or temporarily disabling specific plugins or scripts.
- Monitor the affected area closely. Observe the behavior of the website after implementing containment measures. This ensures the attack is effectively contained and allows for informed decisions regarding next steps.
Contacting Support
Reaching out to the hosting provider or security experts is a critical step in addressing a website attack. These specialists often have experience dealing with various attack vectors and can offer tailored support and guidance. Clear and concise communication is vital for effective assistance.
- Document the attack thoroughly. Record the specific time of the attack, the type of attack suspected, and any noticeable changes in website behavior.
- Contact your hosting provider or a cybersecurity expert immediately. Provide them with the documented information about the incident.
- Follow their instructions diligently. Security experts can provide critical guidance on how to safely and effectively respond to the attack and secure your website.
Rapid Response Plan
Having a pre-defined rapid response plan in place can dramatically improve the efficiency and effectiveness of your response to an attack. This plan should Artikel the roles and responsibilities of each team member and the specific steps to take in various situations.
- Establish a dedicated response team. Assign specific individuals to handle different aspects of the response, such as technical analysis, communication, and incident reporting.
- Develop a detailed response protocol. Artikel the specific steps to take, including the tools to use, the procedures to follow, and the communication channels to employ.
- Regularly review and update the plan. Cyber threats are constantly evolving, so your response plan should be reviewed and updated on a regular basis to reflect current security practices and vulnerabilities.
Wrap-Up
Protecting your website from attack requires vigilance and proactive measures. By understanding the potential threats, monitoring your website’s health, and analyzing logs, you can identify and respond to attacks effectively. This guide provides a framework for maintaining website security and ensuring your online presence remains resilient against malicious activity. Staying informed and prepared is key to protecting your digital assets.