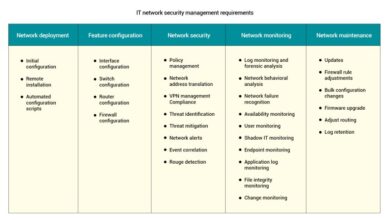
Managing IM and Email Threats in the Workplace
Managing im and e mail threats in the workplace – Managing IM and email threats in the workplace is crucial for any organization. From phishing scams to malware, the threat landscape is constantly evolving. This comprehensive guide delves into the specifics of recognizing, preventing, and mitigating these dangers, ensuring a secure environment for all employees and data.
We’ll explore various types of threats, robust security measures, essential tools, and data protection strategies. Understanding how to implement an incident response plan and conduct regular employee training is also key. Finally, we’ll discuss the importance of staying updated on the latest threats and trends in the ever-changing digital landscape.
Defining the Threat Landscape: Managing Im And E Mail Threats In The Workplace
Protecting your workplace from email and instant messaging (IM) threats requires a clear understanding of the diverse and evolving threat landscape. Cybercriminals constantly adapt their tactics, employing increasingly sophisticated methods to compromise systems and steal sensitive information. This article provides a comprehensive overview of the various threats, including malware types, social engineering, and insider risks, highlighting the importance of proactive defense mechanisms.The modern workplace relies heavily on email and IM for communication and collaboration.
Unfortunately, this reliance also exposes organizations to a range of malicious attacks. Recognizing these threats and understanding their characteristics is crucial for implementing effective security measures.
Email and IM Threat Types
Email and instant messaging platforms are common vectors for a variety of malicious activities. Phishing, malware delivery, and social engineering are prominent examples. Insider threats, though often underestimated, also pose a significant risk.
- Phishing: Phishing attacks aim to trick users into revealing sensitive information, such as usernames, passwords, or credit card details. These attacks often involve creating fraudulent emails or IM messages that mimic legitimate communications from trusted sources. Examples include spoofed bank emails or messages requesting account verification.
- Malware: Malicious software, or malware, can be delivered through infected attachments, malicious links, or compromised websites accessed through email or IM. Various types of malware exist, each with unique functionalities. Common types include viruses, worms, Trojans, ransomware, and spyware.
- Social Engineering: Social engineering exploits human psychology to manipulate individuals into performing actions that compromise security. This can involve manipulating users into clicking malicious links, opening attachments, or divulging sensitive information. For example, a threat actor might impersonate a senior executive to pressure an employee into making a financial transfer. Criminals often leverage urgency or authority to bypass critical thinking.
- Insider Threats: Employees, either malicious or negligent, can pose significant risks. Malicious insiders may deliberately sabotage systems or leak confidential data, while negligent insiders might unintentionally expose sensitive information due to a lack of security awareness. A disgruntled employee, for example, could intentionally delete critical data or send sensitive information to an external party.
Malware Types
Malicious software (malware) can take many forms, each designed to achieve different malicious objectives. Understanding the various types is critical for effective threat detection and mitigation.
- Viruses: Viruses replicate themselves and spread to other files or systems. They can damage data, disrupt operations, and potentially cause system crashes.
- Worms: Worms autonomously propagate through networks, often exploiting security vulnerabilities to spread rapidly. They can overload networks and consume resources, leading to operational disruptions.
- Trojans: Trojans disguise themselves as legitimate software, but contain malicious code. They can provide unauthorized access to systems or steal sensitive information.
- Ransomware: Ransomware encrypts data and demands a ransom for its release. This type of malware can cause significant financial and operational losses if not handled properly.
- Spyware: Spyware monitors user activity and collects sensitive information, such as browsing history, keystrokes, and personal data. This information can be used for identity theft or other malicious purposes.
Social Engineering Tactics
Social engineering attacks leverage psychological manipulation to exploit human vulnerabilities. Understanding these tactics is vital for recognizing and preventing such attacks.
- Impersonation: Attackers often impersonate trusted individuals or organizations to gain access to sensitive information or to trick victims into performing actions that compromise security.
- Urgency: Creating a sense of urgency, such as a threat of account suspension or immediate action, can manipulate individuals into making hasty decisions without proper verification.
- Authority: Presenting oneself as an authority figure, such as a manager or a law enforcement official, can instill trust and encourage compliance with requests that might be suspicious.
Comparison of Email and IM Threats, Managing im and e mail threats in the workplace
The following table summarizes common email and IM threats, highlighting their characteristics.
| Threat Type | Description | Detection Methods | Mitigation Strategies |
|---|---|---|---|
| Phishing | Attempts to trick users into revealing sensitive information. | Suspicious sender addresses, grammatical errors, urgent requests, unusual links. | Strong authentication, security awareness training, email filtering. |
| Malware | Malicious software delivered through attachments, links, or compromised websites. | Unusual file types, suspicious attachments, unknown senders, system performance issues. | Antivirus software, secure browsing practices, regular system updates. |
| Social Engineering | Exploits human psychology to manipulate users. | Suspicious requests, unusual tone, urgent demands, pressure to act quickly. | Security awareness training, verification procedures, reporting suspicious activities. |
| Insider Threats | Employees who deliberately or unintentionally compromise security. | Unusual access patterns, unauthorized data transfers, suspicious emails or IMs. | Strong access controls, regular security audits, employee training. |
Implementing Robust Security Measures
Protecting against email and instant message (IM) threats requires a multi-layered approach encompassing strong protocols, employee training, and incident response procedures. A proactive security posture is crucial for mitigating risks and maintaining a secure digital environment within the workplace. Failure to implement these measures can lead to significant financial losses, reputational damage, and legal repercussions.Implementing robust security measures is not just about installing software; it’s about fostering a security-conscious culture throughout the organization.
This involves equipping employees with the knowledge and tools to identify and respond to potential threats, ensuring that every individual plays a part in safeguarding sensitive information.
Keeping workplace IM and email secure is crucial, especially with the rise in phishing attempts. Fortunately, a flat rate wifi package, like the one ipass recently announced, ipass tees up flat rate wifi package , can help improve network security by potentially reducing the number of vulnerable devices connected. This, in turn, can make it harder for malicious actors to gain access, ultimately strengthening your overall IM and email threat management strategy.
Essential Security Protocols and Procedures
Implementing a comprehensive set of security protocols and procedures is paramount in mitigating risks associated with email and IM threats. These protocols should encompass all communication channels to ensure a consistent and secure approach. This includes establishing clear guidelines for acceptable use, regularly reviewing and updating these guidelines, and implementing systems that track and monitor employee activity. Robust protocols and procedures are crucial to prevent unauthorized access and misuse of company resources.
- Strong Password Policies: Enforcing strong password policies is critical. These policies should mandate complex passwords, a minimum length, and regular password changes. Employees should be educated on the importance of using unique passwords for each account, and password managers can be a helpful tool to manage complex passwords securely.
- Multi-Factor Authentication (MFA): Implementing MFA for all accounts accessing sensitive data significantly enhances security. This adds an extra layer of protection, requiring users to provide multiple forms of verification before accessing accounts. MFA makes it significantly more difficult for attackers to gain unauthorized access even if they obtain a user’s password.
- Regular Software Updates: Keeping software up-to-date is essential to patch vulnerabilities. Cybercriminals frequently exploit known vulnerabilities, so timely updates are crucial to maintain a strong defense. Organizations should implement automated update systems where possible, and establish clear procedures for deploying security patches.
Importance of Strong Passwords and MFA
Strong passwords and MFA are fundamental to protecting against unauthorized access. Weak passwords are easily guessed or cracked, allowing attackers to gain entry to accounts and systems. MFA, by requiring additional verification steps, significantly reduces the risk of unauthorized access even if a password is compromised.
- Password Complexity: Passwords should contain a combination of uppercase and lowercase letters, numbers, and symbols. The longer the password, the more difficult it is to crack. Using a password manager can greatly assist in creating and storing complex passwords.
- Regular Password Changes: Implementing a policy requiring regular password changes strengthens security. This ensures that compromised passwords are quickly identified and changed. Establish clear and concise procedures for changing passwords, and provide guidance for creating strong, unique passwords.
- MFA Benefits: MFA adds an extra layer of security, preventing attackers from accessing accounts even if they have a password. MFA is particularly important for accessing sensitive data or systems. Examples include using security tokens, authenticator apps, or biometric verification.
Security Awareness Training for Employees
Security awareness training equips employees with the knowledge and skills to recognize and respond to potential threats. By providing regular training, organizations can cultivate a culture of security awareness and reduce the risk of phishing attacks and other social engineering tactics.
- Phishing Awareness: Training should emphasize the importance of recognizing phishing attempts, which often involve fraudulent emails or messages designed to trick users into revealing sensitive information. Provide examples of common phishing tactics, and emphasize the importance of verifying email and message requests.
- Social Engineering Tactics: Training should cover various social engineering tactics, including impersonation, baiting, and quid pro quo. Employees should be educated on how to recognize these tactics and avoid falling victim to these scams. Discuss realistic scenarios to illustrate how these tactics work in practice.
- Reporting Procedures: Establish clear procedures for reporting suspicious email and IM activity. Employees should understand the channels for reporting and the steps to follow when encountering potential threats.
Identifying and Reporting Suspicious Email and IM Activity
Identifying suspicious email and IM activity is crucial for preventing potential security breaches. By establishing clear criteria and reporting procedures, organizations can effectively respond to potential threats.
- Suspicious Email Criteria: Establish clear criteria for identifying suspicious emails, including unusual sender addresses, grammar errors, urgent requests for sensitive information, and generic greetings. Provide examples of suspicious email patterns to aid in recognition.
- Suspicious IM Criteria: Establish criteria for identifying suspicious IM activity, such as unusual requests, threats, or demands for personal information. Explain how to recognize potential phishing attempts or malware distribution tactics.
- Reporting Channels: Designate clear reporting channels, such as dedicated email addresses, security portals, or designated personnel, for reporting suspicious activity. Provide contact information and clear instructions on how to report incidents.
Handling Suspected Security Incidents
A well-defined process for handling suspected security incidents is crucial for minimizing damage and preventing escalation. A clear incident response plan will guide employees and management on the proper steps to take when a security incident is suspected.
Protecting your workplace from IM and email threats is crucial. Robust security measures are essential, and staying ahead of the curve is key. The UN and ITU are working together to combat spam, a major vector for malicious attacks, as detailed in this article un itu join fight against spam. This global effort highlights the importance of proactive strategies for managing IM and email threats in the modern workplace.
- Incident Detection: Implement systems for detecting potential security incidents, such as intrusion detection systems and email filtering tools. Identify the specific indicators of a potential security incident.
- Initial Response: Establish a clear procedure for initial response to suspected security incidents. This involves containing the incident, preventing further damage, and notifying the appropriate personnel.
- Investigation and Analysis: Initiate a thorough investigation to understand the nature and scope of the incident. Document all actions taken and findings during the investigation. Identify the cause and any potential vulnerabilities.
- Remediation and Recovery: Develop and implement a plan for remediating the incident and recovering from any losses. This may include restoring data, implementing security patches, and conducting system audits.
- Post-Incident Review: Conduct a post-incident review to identify lessons learned and improve future incident response procedures. This is a crucial step in preventing similar incidents in the future.
Email and IM Security Tools
Protecting your workplace from email and instant messaging (IM) threats requires a multi-layered approach. Effective security tools are crucial for preventing malicious activity, safeguarding sensitive data, and maintaining a secure digital environment. This section delves into the available tools and their functionalities, highlighting their importance in today’s interconnected world.Email and instant messaging platforms are commonly targeted by cybercriminals, making robust security measures essential.
Implementing appropriate tools helps detect and block malicious content, protecting your organization from potential breaches and data loss.
Email Security Tools Overview
Email security tools are vital for filtering out malicious content, phishing attempts, and other threats that can compromise your network. These tools often employ a combination of techniques to identify and block harmful emails, safeguarding your organization’s sensitive data and preventing potential disruptions. A comprehensive email security solution is critical in today’s digital landscape.
Email Filtering and Antivirus Solutions
Email filtering solutions are designed to identify and filter out unwanted or malicious emails before they reach users’ inboxes. These solutions use various techniques, including content analysis, sender reputation checks, and blacklisting to prevent spam, phishing attempts, and malware. Antivirus solutions for email often work in conjunction with filtering solutions to provide an additional layer of protection. They scan incoming and outgoing emails for known viruses, malware, and other malicious code, thereby preventing infections from spreading through your network.
Different solutions offer varying levels of protection and features, so choosing the right one for your needs is crucial.
Comparison of Email Filtering and Antivirus Solutions
Different email filtering and antivirus solutions vary in their functionalities and capabilities. Some solutions focus primarily on spam and phishing prevention, while others provide a more comprehensive approach that includes malware detection and prevention. A thorough comparison of various solutions is necessary to choose the most suitable one for your organization.
Instant Messaging (IM) Security Features
Instant messaging platforms, while convenient, can be vulnerable to security breaches if not properly secured. Various security features are available to mitigate risks associated with IM communication. These features typically involve encryption, access controls, and user authentication to protect sensitive information shared within the IM platform. The effectiveness of these features varies depending on the specific IM platform and the implementation of the security measures.
Table of Email Security Tools
| Tool Name | Key Feature 1 | Key Feature 2 | Key Feature 3 |
|---|---|---|---|
| SpamTitan | Advanced spam filtering | Phishing protection | Malware scanning |
| Mimecast | Email security gateway | Data loss prevention | Threat intelligence |
| Proofpoint | Security awareness training | Threat detection and response | Archiving and compliance |
Protecting Sensitive Data

Protecting sensitive data exchanged via email and instant messaging (IM) is paramount in today’s digital workplace. A breach can lead to significant financial losses, reputational damage, and legal repercussions. Implementing robust security measures, including encryption and data loss prevention (DLP), is critical to mitigate these risks. This section delves into the importance of secure data handling policies, procedures, and the practical implementation of these measures.Effective data protection strategies are not just about preventing breaches; they are also about establishing a culture of security awareness within the organization.
This requires clear communication of policies, regular training, and a commitment from all employees to adhere to secure data handling practices. Employees need to understand the value of sensitive data and their role in safeguarding it.
Importance of Encryption
Encryption is the process of converting readable data into an unreadable format, known as ciphertext. This scrambled form of data is only accessible with a decryption key. Applying encryption to sensitive data exchanged via email and IM significantly reduces the risk of unauthorized access and disclosure. If an unauthorized party intercepts the communication, they will not be able to understand the contents.
This is especially critical for confidential information like financial data, customer details, and intellectual property.
Keeping workplace IM and email safe from threats is crucial. Recent advancements in cybersecurity, like the joint research initiative between IBM and Nortel, IBM Nortel announce joint research deal , could potentially lead to innovative solutions for these issues. This research could pave the way for better tools and strategies to tackle phishing, malware, and other threats, ultimately improving the security posture of organizations.
Data Loss Prevention (DLP) Measures
Data Loss Prevention (DLP) solutions are software tools designed to identify, monitor, and prevent the unauthorized disclosure of sensitive data. These tools can be deployed to detect sensitive data leaving the organization’s network, either accidentally or intentionally. This can involve identifying s or patterns associated with sensitive information within emails and IM messages. A robust DLP system acts as a proactive defense against data breaches, ensuring that sensitive data remains within the organization’s secure perimeter.
DLP also helps comply with regulatory requirements, especially for industries with stringent data protection regulations.
Secure Data Handling Policies and Procedures
A comprehensive data handling policy Artikels the rules and procedures for handling sensitive data within the organization. It should specify the types of data considered sensitive, the protocols for handling such data, and the responsibilities of employees in safeguarding it. This includes procedures for storing, transmitting, and destroying sensitive data. Clear guidelines for handling sensitive information both in email and IM are essential to minimize risks.
- Data Classification: Categorize data based on sensitivity levels (e.g., confidential, restricted, public). This categorization helps tailor security measures to the specific sensitivity of the data.
- Access Control: Implement strict access controls to limit access to sensitive data only to authorized personnel. This can involve user authentication, authorization, and role-based access controls.
- Secure Storage: Store sensitive data in secure locations, using physical and digital security measures. For example, encrypted hard drives and secure file sharing platforms.
Implementing Data Encryption and DLP
Implementing data encryption and DLP requires careful planning and execution. Organizations should conduct a thorough risk assessment to identify potential vulnerabilities and tailor security measures accordingly. This involves evaluating existing systems, assessing the sensitivity of data, and identifying potential threats.
- Assess Existing Infrastructure: Evaluate the current infrastructure to identify weaknesses and gaps in security. Identify the types of sensitive data handled, and where it is stored.
- Choose Appropriate Tools: Select encryption and DLP tools that align with the organization’s specific needs and budget. Consider the size and complexity of the organization, the volume of data handled, and the types of sensitive information.
- Employee Training: Implement comprehensive training programs to educate employees about the importance of data security and the company’s data handling policies. This includes specific training on using the new DLP tools and encryption protocols.
Regulatory Compliance Requirements
Many industries are subject to stringent regulatory requirements for handling sensitive information. These regulations often mandate specific security measures, such as encryption and data loss prevention. Compliance with these regulations is crucial to avoid penalties and maintain trust with stakeholders. Examples include HIPAA for healthcare, GDPR for European Union data, and PCI DSS for payment card information.
“Organizations must adapt their data handling practices to align with the relevant regulatory requirements to maintain compliance and avoid legal issues.”
Incident Response Plan
A robust incident response plan is crucial for mitigating the impact of email and IM threats. This plan provides a structured approach to handling incidents, minimizing damage, and ensuring a swift recovery. A well-defined plan fosters a coordinated response, enabling affected parties to act effectively and efficiently.Having a documented plan allows for consistency and reduces the likelihood of errors or omissions during a crisis.
This systematic approach empowers the organization to quickly assess, contain, and recover from incidents, protecting sensitive data and maintaining operational continuity.
Incident Detection and Reporting
Effective incident detection is the first step in a swift response. Employees must be trained to recognize suspicious emails and IM messages, including phishing attempts, malware distribution, and unauthorized access attempts. Establishing clear reporting procedures is essential. This process ensures prompt escalation to the appropriate personnel, allowing for immediate action. A dedicated incident reporting channel, such as a dedicated email address or a ticketing system, can streamline the process.
This ensures rapid identification and prioritization of potential threats.
Incident Containment and Isolation
Containing the incident is critical to prevent further spread. This involves isolating affected systems, applications, and networks to prevent the infection from spreading. The isolation process may involve disconnecting affected computers from the network, quarantining infected files, and implementing network segmentation. Specific procedures should detail the steps for containing affected systems based on the type of threat encountered.
This prevents the spread of malware or the compromise of additional data.
Data Recovery and Restoration
Data recovery and restoration procedures are vital for minimizing data loss. This involves having a comprehensive backup and recovery plan. Regular backups of critical data, including email and IM communications, are essential. A documented process for restoring data from backups must be available, including clear instructions on the backup locations and the steps to retrieve data. The plan should Artikel the procedures for restoring data to different locations and systems.
Communication and Escalation Protocols
Effective communication is paramount during an incident. Clear communication channels between affected parties, including IT staff, security personnel, and management, must be established. A well-defined escalation protocol will ensure that incidents are handled promptly and effectively. This protocol defines who to contact and the order of escalation. It should include a system for reporting the status of the incident to all relevant parties, providing regular updates.
Regular updates help keep all stakeholders informed and ensure transparency. For example, an incident involving a suspected phishing campaign should be escalated immediately to the security team.
Employee Training and Awareness
Protecting your organization from email and instant messaging (IM) threats requires a proactive approach. Employee training is a cornerstone of this defense, equipping users with the knowledge and skills to identify and avoid potential dangers. A robust training program empowers employees to act as the first line of defense against sophisticated attacks.A comprehensive training program should cover a broad range of topics, from recognizing phishing attempts to reporting suspicious activity.
Consistent reinforcement of security best practices, through regular training sessions, is crucial for maintaining a strong security posture.
Email Security Training Modules
Regular email security training is essential to protect against phishing scams, malware delivery, and social engineering attacks. Employees must be educated on how to spot these threats and take appropriate action. This training should be tailored to the specific risks and vulnerabilities faced by the organization.
- Recognizing Phishing Attempts: Employees need to learn to identify common characteristics of phishing emails, including suspicious sender addresses, urgent requests, grammatical errors, and requests for sensitive information. Examples include analyzing email subject lines, checking sender email addresses, and scrutinizing embedded links for legitimacy.
- Handling Attachments with Caution: Employees must understand the potential risks associated with opening attachments from unknown or untrusted sources. This module should emphasize the importance of verifying the sender and the legitimacy of the file before opening any attachment. It should also include examples of malicious attachments and their effects on the system.
- Protecting Sensitive Data: Training should cover the importance of protecting sensitive information and following company policies for handling confidential data. This should include guidelines for password management and avoiding sharing sensitive information over unsecured channels. Examples of sensitive data include financial details, employee records, and intellectual property.
- Reporting Suspicious Activity: Employees must know the correct procedures for reporting suspicious emails, including how to escalate the matter to IT security and the appropriate channels to use for reporting. A dedicated reporting mechanism, such as a dedicated email address or a secure online portal, should be clearly communicated.
IM Security Training Modules
Instant messaging (IM) security training should cover similar principles to email security, but with specific attention to the unique characteristics of IM communication.
- Recognizing Malicious IM Messages: Employees should be able to identify suspicious IM messages, including requests for personal information, links to malicious websites, and messages containing attachments. Examples should be provided that demonstrate how to recognize these patterns.
- Protecting Personal Information: Training should emphasize the importance of protecting personal information and not sharing sensitive data through IM. This should include instructions on avoiding disclosing login credentials or financial details through IM. A guide on the dangers of clicking links in IM conversations should be included.
- Avoiding Unverified Contacts: Employees should be cautioned against accepting requests from unknown or untrusted contacts. This should include instructions on verifying contact identities and avoiding engaging in conversations with suspicious contacts.
- Reporting Suspicious IM Activity: Procedures for reporting suspicious IM activity should be clearly defined, including escalation procedures to IT security and the appropriate channels to use for reporting.
Importance of Regular Security Awareness Training
Security threats evolve constantly. Regular security awareness training is crucial to keep employees updated on the latest threats and best practices. Training should be conducted periodically, and the frequency should be determined by the organization’s risk profile and the frequency of new threats. This ensures employees are equipped to deal with emerging threats.
Identifying Phishing and Social Engineering Attempts
Training modules should equip employees with the ability to identify phishing and social engineering attempts. Phishing attacks often use social engineering techniques to manipulate employees into revealing sensitive information.
- Identifying Common Tactics: Training should cover common tactics used in phishing and social engineering attacks, such as urgency, authority, and familiarity. Examples of these tactics, with clear demonstrations of how they are used in attacks, should be provided.
- Red Flags and Indicators: Employees should be trained to identify red flags and indicators of phishing and social engineering attempts, such as suspicious email addresses, grammar errors, and unusual requests. Real-world examples of successful attacks can be used to illustrate the effectiveness of these tactics.
- Practicing Critical Thinking: Training should emphasize the importance of critical thinking and skepticism when interacting with unfamiliar communications. Employees should be encouraged to question requests for sensitive information and to verify information independently before taking any action.
Monitoring and Auditing

Staying ahead of evolving cyber threats requires proactive monitoring and auditing of email and instant messaging (IM) communications. This proactive approach allows organizations to identify suspicious activity quickly, minimizing potential damage and improving overall security posture. Thorough monitoring and auditing also provide valuable insights into user behavior, helping to identify and address potential vulnerabilities within the system.Effective monitoring and auditing go beyond simply logging activity.
They necessitate a structured approach that combines technical tools with human analysis to recognize patterns indicative of malicious intent. This combination is crucial for preventing sophisticated attacks and ensuring the integrity of sensitive information.
Monitoring Email and IM Traffic for Suspicious Activity
Monitoring email and IM traffic involves scrutinizing communications for unusual patterns, suspicious attachments, or potentially malicious links. Tools and processes for this should be implemented and regularly reviewed. These processes should be adaptable to evolving threats. This vigilance is vital for maintaining a strong security posture.
- Regularly review logs for unusual sender addresses, frequency of communication, and volume of messages.
- Identify unusual or suspicious s, phrases, or attachments that may signal malicious activity.
- Implement filters to flag messages containing known phishing attempts, malware signatures, or malicious URLs.
- Set up alerts for unusual activity, such as large numbers of rejected messages or unusual login attempts.
Log Analysis Techniques for Identifying Potential Threats
Log analysis plays a critical role in identifying potential threats. It provides a historical record of activity that can be reviewed for patterns indicative of malicious behavior. This analysis requires the use of specialized tools and techniques.
- Correlation Analysis: Identify correlations between events, such as a series of failed login attempts from a particular IP address, followed by a large number of outgoing messages. This can suggest a brute-force attack or a compromised account.
- Pattern Recognition: Look for recurring patterns or anomalies in email and IM traffic. Examples include unusual sender addresses, frequent use of specific s, or unexpected changes in communication frequency. This helps to identify and flag unusual behaviors.
- Anomaly Detection: Develop a baseline of normal user activity and flag deviations from that baseline. This is particularly useful for detecting unusual volume of communications or unusual destinations of communications.
- Filtering: Employ filters to detect known phishing attempts, malware commands, or other malicious activity. This should be updated regularly to reflect emerging threats.
Role of SIEM Systems in Threat Detection
Security Information and Event Management (SIEM) systems are powerful tools for aggregating and analyzing security logs from various sources, including email and IM systems. They provide a centralized platform for threat detection and response.
- SIEM systems collect logs from multiple sources, providing a comprehensive view of security events.
- They correlate events to identify potential threats, such as a compromised account leading to unauthorized data access.
- SIEM systems can generate alerts based on predefined rules and anomalies, enabling swift responses to emerging threats.
- Advanced SIEM systems can analyze data for behavioral anomalies and proactively identify suspicious patterns that may indicate malicious activity.
Auditing User Access and Activity
Auditing user access and activity provides insights into user behavior and potential security breaches. This process should be transparent and well-documented. This information is vital for identifying unauthorized access or misuse of resources.
- Track user logins, logouts, and access to sensitive data or systems.
- Review access logs for unauthorized attempts or suspicious activity patterns.
- Monitor user activity to identify potential escalation of privileges.
- Implement robust access control policies to limit access to sensitive information.
Sample Report for Monitoring and Auditing Email and IM Communications
| Date | Time | User | Event | Details | Severity |
|---|---|---|---|---|---|
| 2024-10-27 | 10:00 AM | John Smith | Login | Successful login from internal network | Low |
| 2024-10-27 | 10:05 AM | Jane Doe | Email Sent | Sent email to external address with suspicious attachment | Medium |
| 2024-10-27 | 10:10 AM | John Smith | File Access | Accessed confidential financial report | Low |
This sample report illustrates the format for recording monitoring and auditing activities. The severity column provides a quick way to prioritize potential threats. The report is a template and needs to be adapted to the specific needs of the organization.
Staying Updated with Emerging Threats
Staying ahead of evolving email and IM threats requires a proactive approach. The digital landscape is constantly shifting, with new vulnerabilities and attack vectors emerging regularly. This necessitates a commitment to continuous learning and adaptation in our security strategies.Cybercriminals are adept at exploiting weaknesses in existing systems and policies. Therefore, simply implementing security measures isn’t enough; organizations must adapt their defenses to match the ever-changing tactics employed by threat actors.
Regular updates and vigilance are crucial to maintaining a robust security posture.
Staying Informed on Security Trends
Staying informed about the latest security trends is vital for proactive threat management. This involves actively monitoring industry publications, security blogs, and reputable news sources. Understanding the motivations and techniques of threat actors is equally important.
- Follow cybersecurity news outlets: Keeping abreast of breaking news, advisories, and security reports from reputable sources like SANS Institute, KrebsOnSecurity, and well-known industry publications provides valuable insights into emerging threats.
- Engage in online communities: Participating in cybersecurity forums and groups allows for direct interaction with experts and peers, enabling the exchange of knowledge and the sharing of threat intelligence.
- Attend industry conferences and webinars: Attending relevant cybersecurity conferences and webinars allows for in-depth learning about the latest threats, security best practices, and the latest tools and techniques in a structured environment.
Identifying and Responding to Emerging Threats
Proactive identification and response to emerging threats are crucial for minimizing damage. This requires a systematic approach to threat detection, analysis, and mitigation.
- Threat intelligence feeds: Implementing threat intelligence feeds provides real-time information on emerging threats, enabling organizations to quickly adapt security measures.
- Security Information and Event Management (SIEM) systems: These systems collect and analyze security logs from various sources, aiding in the identification of suspicious activities and potential threats. For instance, an unusual spike in failed login attempts or unusual network traffic patterns could signal a potential breach.
- Regular security assessments: Conducting regular security assessments helps identify vulnerabilities in systems and policies. These assessments should cover email and IM protocols, network configurations, and user access controls. For example, a vulnerability assessment might reveal a missing patch in an email server, which is a known entry point for malware.
Regularly Updating Security Software and Policies
Regularly updating security software and policies is essential for maintaining a robust security posture. Software updates often include crucial security patches to address newly discovered vulnerabilities. Policies should be reviewed and updated to reflect the latest threat landscape.
- Software updates: Implementing automatic updates for operating systems, applications, and security software is crucial to ensure the most current security protections.
- Policy reviews: Regular reviews of security policies, especially those concerning email and IM use, should be performed to reflect the latest best practices and to identify any outdated or inadequate procedures.
Evaluating and Implementing New Security Solutions
Evaluating and implementing new security solutions requires careful consideration and a systematic approach. Organizations should thoroughly research new solutions, assess their suitability, and consider the potential impact on existing systems and processes.
- Thorough research: Before adopting any new security solution, thorough research should be conducted to determine its effectiveness, compatibility, and cost-effectiveness. Consider independent reviews and testimonials from other organizations.
- Pilot programs: Implementing pilot programs can allow organizations to test new security solutions in a controlled environment before widespread deployment. This will allow for evaluation of the effectiveness of the new solutions, and identification of any unforeseen issues.
Last Recap
In conclusion, safeguarding your workplace from email and instant messaging threats requires a multi-faceted approach. Implementing strong security protocols, educating employees, and utilizing the right tools are essential. This comprehensive guide has provided a framework for establishing a secure environment, protecting sensitive data, and effectively responding to incidents. By proactively addressing these threats, organizations can maintain a productive and secure work environment.