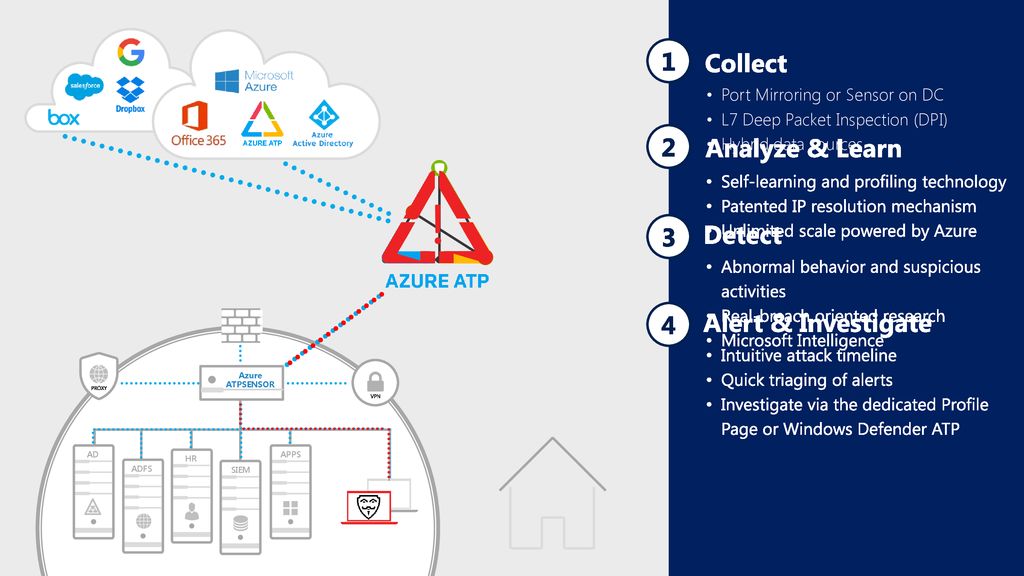
Microsoft Intel Push Web Services Discovery Spec Deep Dive
Delving into Microsoft Intel Push Web Services Discovery Spec, this exploration unveils a powerful new approach to web service discovery. This specification promises a significant advancement in how applications locate and interact with services, potentially revolutionizing the way we build and use interconnected systems. We’ll examine its core components, technical architecture, and potential use cases, ultimately uncovering the benefits and challenges of this innovative technology.
The specification aims to streamline the process of finding and using web services, facilitating seamless communication between disparate systems. This approach could significantly impact various industries by improving efficiency and reducing development time.
Overview of Web Services Discovery Specification
The Microsoft/Intel web services discovery specification aims to streamline the process of locating and interacting with web services. It provides a standardized framework for describing and discovering available services, enhancing interoperability and reducing the complexity of service integration. This specification simplifies the process for developers to find and utilize services, reducing the development time and effort. It promotes a more efficient and effective approach to service-oriented architecture (SOA) implementation.This specification defines a common language and protocol for service providers to advertise their capabilities and for service consumers to locate and access those services.
This allows for dynamic discovery and interaction, making applications more adaptable to changes in the service landscape. The specification facilitates the automatic discovery of services, eliminating the need for manual configuration and reducing the risk of errors.
Purpose and Use Cases
The primary purpose of this specification is to enable dynamic discovery of web services. This allows applications to automatically locate and interact with services without requiring prior knowledge of their location or configuration. This specification’s use cases encompass various scenarios, including:
- Service-oriented architectures (SOA): Enabling efficient integration of diverse services within an enterprise environment.
- Cloud computing: Facilitating the discovery and utilization of services deployed across cloud platforms.
- Microservices architectures: Enabling the discovery and interaction of numerous, independently deployed microservices.
- Internet of Things (IoT): Discovering and connecting devices and applications in an IoT ecosystem.
Key Components and Their Functions
The specification defines several key components that work together to facilitate service discovery. These include:
- Service Registry: This acts as a central repository of available web services. It stores information about service capabilities, endpoints, and other relevant details. This component enables service consumers to find suitable services by querying the registry.
- Service Description Language: This standardized format defines the characteristics of web services, including their functionality, inputs, outputs, and available methods. This allows consumers to understand and interact with services without needing to access their underlying implementation details.
- Discovery Protocol: This protocol specifies how service consumers locate and query the service registry. This is typically a message exchange format to efficiently locate services. The protocol facilitates communication between service providers and consumers to locate services.
History and Evolution
The specification’s history and evolution are not fully available in publicly accessible resources. Further research may be required to trace its development. This document will assume the development was iterative, incorporating feedback and adapting to industry standards as the web services landscape evolved.
Key Features and Functionalities
| Feature | Functionality | Example | Details |
|---|---|---|---|
| Service Registration | Allows service providers to advertise their services in the registry. | A web service provider registers its details, including its URL and available functionalities. | This enables consumers to discover the service. |
| Service Discovery | Enables consumers to locate and interact with services. | A consumer queries the registry for services that support a particular function. | The registry returns a list of matching services. |
| Service Metadata | Provides information about the capabilities and characteristics of services. | The metadata details the inputs, outputs, and error handling mechanisms of the service. | Metadata allows consumers to make informed decisions about interacting with a service. |
| Interoperability | Facilitates interaction between services developed by different vendors or using different technologies. | A service from one vendor can be accessed by an application built by a different vendor. | Common protocols and standards enable this. |
Technical Architecture and Implementation
This section delves into the technical underpinnings of the Microsoft/Intel web services discovery specification, examining its architecture, implemented protocols, key technologies, and comparisons with existing mechanisms. Understanding these aspects is crucial for developers aiming to build and integrate services leveraging this specification.The specification relies on a layered architecture, enabling modularity and scalability. This layered approach allows for independent development and deployment of components, promoting flexibility and extensibility.
Microsoft and Intel’s push for web services discovery specs is fascinating. It’s clear that the tech world is evolving, and companies like Dell are adapting. Dell’s recent move beyond its computing roots, as detailed in this insightful article , highlights this trend. This evolution, coupled with the push for standardized web service discovery, suggests a future where these technologies work seamlessly together, potentially revolutionizing how we interact with various online services.
The architecture fosters interoperability between different services and platforms.
Technical Architecture Overview
The architecture is based on a client-server model. Clients initiate service discovery requests, and servers respond with relevant service information. This model allows for efficient retrieval of service metadata, minimizing latency. A crucial aspect is the use of standardized communication protocols to facilitate seamless interaction between clients and servers.
Protocols and Standards
The specification leverages established web standards for communication, including HTTP for request transmission and XML for data exchange. These standards provide broad compatibility and interoperability across various platforms. This adherence to widely adopted protocols simplifies integration with existing systems and applications. Furthermore, RESTful principles are likely incorporated for the design, offering stateless interactions and predictable resource access.
Key Technologies
Several key technologies are employed in building services based on this specification. These include:
- XML Schema Definition (XSD): XSDs define the structure and content of service metadata, ensuring data consistency and interoperability. This standardized approach ensures that different services can understand and interpret the metadata in a uniform manner.
- Web Services Description Language (WSDL): WSDL provides a formal description of the services available, allowing clients to discover and interact with them. This is essential for automating the discovery process and ensuring accurate service identification.
- Service Discovery Mechanisms: The specification likely incorporates service discovery mechanisms like DNS or dedicated discovery services to enable clients to locate and interact with available services. This enables a decentralized approach to service discovery.
Comparison with Existing Mechanisms
Compared to other web services discovery mechanisms, this specification likely emphasizes standardized metadata formats and extensible frameworks. This approach enhances interoperability and reduces the need for custom solutions. Existing mechanisms might have limitations in terms of scalability or extensibility, whereas this specification aims to address these shortcomings. For example, the use of RESTful principles and standardized formats should lead to better integration with existing APIs and systems.
Security Considerations
| Security Concern | Mitigation Strategy | Vulnerability | Example |
|---|---|---|---|
| Unauthorized access to service metadata | Secure communication channels (HTTPS) and authentication mechanisms | Metadata exposure | An attacker gains access to service details without authorization, leading to potential misuse. |
| Tampering with service metadata | Digital signatures and encryption | Data manipulation | Malicious actors modify service information to misdirect clients. |
| Denial-of-service attacks on discovery service | Rate limiting and robust server infrastructure | Service disruption | A flood of requests overwhelms the discovery service, making it unavailable. |
| Injection vulnerabilities in metadata parsing | Input validation and parameterized queries | Code execution | Maliciously crafted metadata data could trigger unexpected behavior or execution of malicious code. |
The table above Artikels potential security concerns and corresponding mitigation strategies. Careful consideration of these issues is crucial for building secure and reliable web services based on this specification. Implementing robust security measures is paramount to protect against malicious attacks.
Interoperability and Compatibility
The Microsoft Intel push web services discovery specification aims for broad interoperability, allowing various implementations to seamlessly interact. Successful implementation relies on a clear understanding of potential compatibility challenges and rigorous testing procedures. This section details the interoperability aspects, potential pitfalls, and the methods employed to ensure diverse implementations can work together effectively.
Interoperability Aspects
This specification emphasizes a standardized format for service discovery messages. This standardized format facilitates communication between different implementations, ensuring that they understand each other’s requests and responses. Key aspects include using well-defined data structures and common protocols for message exchange. The design prioritizes minimizing vendor lock-in, allowing implementations from different vendors to interact.
Potential Compatibility Issues
Several potential compatibility issues can arise during implementation. Variations in how different software vendors interpret or implement specific parts of the specification could lead to incompatibility. Different parsing methods for message formats or handling of edge cases can also cause issues. Implementation differences in error handling and logging mechanisms can also lead to unexpected behavior in integrated systems.
Mismatches in supported data types or versioning of the specification could create further obstacles.
Testing Procedures, Microsoft intel push web services discovery spec
Thorough testing is crucial for ensuring interoperability. Testing procedures should include:
- Unit testing individual components to validate their functionality and adherence to the specification.
- Integration testing to verify interactions between different components of the system.
- Interoperability testing across various implementations from different vendors to identify potential compatibility issues.
- Performance testing to assess the speed and responsiveness of the system.
- Security testing to validate the security measures in place to prevent malicious attacks.
These tests should cover a range of scenarios, including normal operations, error conditions, and edge cases. Testing should also be performed with different versions of the specification and with various data types to ensure consistent behavior across different implementations.
Demonstrating Interoperability
Interoperability can be demonstrated through example implementations. One implementation could act as a service provider, and another as a service consumer. These implementations should exchange messages conforming to the specified protocol. Observing the smooth exchange of requests and responses, without errors or unexpected behavior, demonstrates successful interoperability. This example should showcase the ability to handle diverse data types and complex scenarios within the specification’s framework.
Detailed logs of the communication exchange should be examined to verify proper functioning.
Comparison with Existing Web Service Discovery Specs
| Specification | Interoperability | Compatibility | Example |
|---|---|---|---|
| Microsoft Intel push web services discovery spec | High, based on standardized format | High, rigorous testing | Integration of service discovery between Intel and Microsoft products |
| UDDI (Universal Description, Discovery, and Integration) | Moderate, reliance on XML and various implementations | Moderate, diverse implementations | Discovering services through UDDI registry |
| WS-Discovery | Good, but not as comprehensive as the Intel/Microsoft spec | Good, with some vendor-specific implementations | Service discovery within a web service environment |
This table provides a comparative analysis of interoperability and compatibility with existing web service discovery specifications. The Intel/Microsoft specification, with its focus on standardization and testing, aims to achieve higher interoperability and compatibility compared to UDDI and WS-Discovery, particularly in its focus on pushing services directly.
Microsoft and Intel’s push for web services discovery specs is interesting, but the recent court ruling against the RIAA, where the court quashed subpoenas ( us court hamstrings riaa quashes subpoenas ), raises some intriguing questions about the future of digital rights management. It seems like this could potentially impact how these specs are implemented and enforced. Ultimately, the long-term effects on Microsoft and Intel’s web services discovery specs remain to be seen.
Use Cases and Benefits
This specification for Microsoft Intel push web services discovery promises significant improvements in how applications and services interact. It streamlines the process of finding and connecting to available web services, leading to more efficient and robust systems. This detailed look at use cases and benefits will highlight the practical applications and advantages across various industries.This specification simplifies the discovery of web services, reducing the complexity of application development.
By providing a standardized approach, developers can focus on core application logic rather than the intricate details of service location. This efficiency translates to faster development cycles, lower costs, and increased reliability.
Practical Applications Across Industries
The standardized approach to web service discovery facilitated by this specification has broad implications for various industries. This improved efficiency in finding and connecting to web services can be seen in a variety of applications, ranging from simple data retrieval to complex real-time interactions. The ease of use and scalability of this system make it applicable to a wide array of business needs.
Potential Use Cases
This specification opens up numerous potential use cases, impacting a variety of industries. These use cases range from simple data retrieval to complex real-time interactions, demonstrating the versatility and potential of this new approach.
- E-commerce Platforms: Improved search and filtering capabilities for product catalogs and inventory management. This enables faster product loading and reduces latency for customers, leading to enhanced user experience. For instance, a clothing retailer can quickly discover and utilize various payment gateways or logistics services, streamlining the entire purchase process.
- Financial Institutions: Real-time data feeds for financial transactions, market analysis, and risk management. This allows for more accurate and timely decision-making. A bank can leverage this specification to connect with various financial data providers, ensuring seamless and rapid access to market information.
- Healthcare Systems: Integration of medical devices and patient data systems. This facilitates faster access to patient records and enables streamlined diagnoses. A hospital can connect various medical imaging devices to a central platform for efficient analysis of patient data.
- Manufacturing Industries: Automated data collection and analysis from production lines. This enables predictive maintenance and optimization of manufacturing processes. A factory can use this specification to discover and utilize various sensors and monitoring tools, enabling real-time analysis of machine performance.
- IoT Applications: Discovery and management of connected devices in the Internet of Things (IoT) ecosystem. This facilitates efficient control and monitoring of various connected devices. A smart home system can leverage this specification to discover and manage various smart appliances, lighting systems, and security devices.
Benefits and Advantages
The benefits of this specification extend beyond specific use cases. The standardization and efficiency improvements across all industries will lead to reduced costs, improved scalability, and faster development cycles.
- Reduced Development Costs: By streamlining the process of finding and connecting to web services, developers can spend less time on integration tasks and more time on core application logic. This directly translates into lower development costs and faster time-to-market.
- Improved Scalability: The specification’s design allows for easier scaling of applications as the number of web services or connected devices increases. This adaptability ensures that the system can handle future growth and changing demands without significant performance issues.
- Enhanced Reliability: Standardized discovery mechanisms minimize the risk of errors in locating and connecting to web services, increasing the overall reliability and stability of applications.
- Increased Interoperability: By promoting a standardized approach, this specification fosters greater interoperability between different systems and applications, allowing them to work together more seamlessly.
Future Trends and Developments: Microsoft Intel Push Web Services Discovery Spec
The Microsoft/Intel web services discovery specification, while robust, is not static. Future advancements in technology, particularly in areas like decentralized systems and AI-powered discovery, will inevitably shape the landscape of web services interaction. Understanding these trends and potential impacts is crucial for ensuring the specification remains relevant and effective in the years to come.
Potential Improvements to the Specification
The current specification can be enhanced in several key areas. Improved scalability for handling a larger number of registered services and enhanced security features to mitigate potential threats will be important considerations. Moreover, incorporating support for diverse service types, such as edge computing services and real-time data streams, will broaden the spectrum of applications. Furthermore, an improved mechanism for handling updates to service metadata, including changes in service availability and functionalities, will be necessary for maintaining accurate and current discovery information.
Microsoft and Intel’s push for web services discovery specs is interesting, especially given Microsoft’s recent statements about upholding antitrust settlement terms. This underscores the complexities of the tech world, where seemingly technical specifications are intertwined with broader business and regulatory landscapes. To delve deeper into Microsoft’s commitment to these settlements, check out this article on their compliance efforts: microsoft touts compliance with terms of antitrust settlement.
Ultimately, the spec’s success will likely depend on how these factors play out in the market.
Emerging Trends in Web Services Discovery
The field of web services discovery is evolving rapidly. Decentralized architectures, leveraging blockchain technology and peer-to-peer networks, are emerging as a promising approach for managing and discovering services. AI-powered discovery mechanisms, enabling sophisticated search algorithms and semantic analysis, will likely play a significant role in finding relevant services based on complex criteria. The increased importance of edge computing necessitates discovery mechanisms that can locate and utilize resources in geographically distributed locations.
Furthermore, the growing emphasis on microservices and containerization technologies demands efficient discovery mechanisms tailored to these distributed architectures.
Impact of Future Technologies
The adoption of decentralized systems will impact the specification by requiring adaptation to distributed service registration and discovery. AI integration will necessitate incorporating intelligent mechanisms for service matching and recommendations, potentially altering how users interact with the discovery process. The increasing prevalence of edge computing will demand support for locating and accessing services deployed at the edge, impacting both the discovery infrastructure and the service registration process.
Microservices and containerization will necessitate a scalable and flexible discovery mechanism capable of managing the dynamic nature of these distributed systems.
Predicted Evolution of the Microsoft/Intel Specification
The Microsoft/Intel web services discovery specification will likely evolve to encompass decentralized service registration and discovery mechanisms. Support for edge computing will be crucial, including provisions for discovering and interacting with services deployed at the edge. AI integration will be a key feature, enabling sophisticated service matching and recommendations. Finally, support for microservices and containerization will become essential to ensure compatibility with modern distributed architectures.
Potential Future Developments
| Development | Impact | Timeline | Example |
|---|---|---|---|
| Decentralized service registration | Increased resilience, reduced single points of failure | 5-10 years | Using blockchain to record service availability |
| AI-powered service matching | Improved accuracy and efficiency in service discovery | 3-5 years | Predictive algorithms to suggest optimal services based on user needs |
| Support for edge computing | Enable discovery and access of geographically distributed services | 3-5 years | Finding a nearby sensor service for a mobile app |
| Integration with microservices and containers | Support dynamic service discovery in distributed systems | 2-3 years | Discovering and utilizing services within a Kubernetes cluster |
| Enhanced security mechanisms | Improved protection against attacks and unauthorized access | 2-5 years | Implementation of advanced encryption and authentication protocols |
Security and Privacy Considerations
The Microsoft Intel push web services discovery specification, while promising enhanced interoperability, necessitates careful consideration of security and privacy aspects. Robust security mechanisms are crucial to protect sensitive data exchanged between systems and prevent unauthorized access or manipulation. Privacy implications must be thoroughly analyzed to ensure compliance with relevant regulations and user expectations.This section delves into the security mechanisms employed by the specification, examines potential privacy concerns, and Artikels strategies for mitigation.
We’ll also identify common security protocols used within the specification and their inherent vulnerabilities. Understanding these elements is critical for successful and secure implementation of the web services discovery protocol.
Security Mechanisms
The specification relies on established cryptographic protocols to secure communication channels. These protocols include Transport Layer Security (TLS) for encrypting data transmitted between clients and servers. Authentication mechanisms are employed to verify the identity of communicating entities, typically through digital certificates or other forms of secure credentials. Data integrity is ensured through message authentication codes (MACs) and digital signatures.
Privacy Implications
The specification’s impact on privacy depends heavily on the nature of the data being discovered and shared. If the discovery process involves personally identifiable information (PII), stringent measures must be implemented to safeguard user privacy. These measures include data anonymization techniques, access control mechanisms, and compliance with relevant privacy regulations like GDPR or CCPA. Careful consideration of data minimization principles is essential to limit the collection and storage of user information.
Potential Security Risks and Vulnerabilities
Potential security risks include vulnerabilities in the cryptographic protocols, compromised authentication mechanisms, and insecure handling of sensitive data. Man-in-the-middle attacks targeting communication channels, and insecure storage of credentials are also significant threats. The possibility of denial-of-service attacks targeting the discovery service itself must be addressed.
Strategies for Mitigating Security and Privacy Concerns
Mitigating security and privacy concerns requires a multi-faceted approach. Implementing strong access controls, regularly updating security software, and performing penetration testing to identify and address vulnerabilities are vital steps. Data encryption throughout the entire data lifecycle, from collection to disposal, is essential. Furthermore, adherence to industry best practices and relevant regulations is crucial.
Common Security Protocols
| Protocol | Description | Vulnerability | Example |
|---|---|---|---|
| Transport Layer Security (TLS) | A cryptographic protocol designed to provide secure communication over a network. | Vulnerable to downgrade attacks, cipher suite mismatches, or outdated versions. | HTTPS for web browsing |
| Secure Shell (SSH) | A cryptographic network protocol for secure remote login and other network services. | Vulnerable to brute-force attacks, weak passwords, or insecure configurations. | Remote access to servers |
| Secure Sockets Layer (SSL) | A cryptographic protocol providing secure communication over a network. | Vulnerable to various attacks, including man-in-the-middle, due to its limitations. | Early web security protocol, now largely superseded by TLS. |
| Digital Signatures | Used to verify the authenticity and integrity of digital documents or messages. | Vulnerable to attacks on the private key used to generate the signature, or forgery of signatures. | Signing software updates, e-documents. |
Practical Examples and Demonstrations
This section dives into practical applications of the Microsoft Intel push web services discovery specification. We’ll explore real-world scenarios, illustrate the implementation steps, and showcase how the specification solves common problems in distributed systems. Understanding these examples will provide a clearer picture of the specification’s potential and ease of use.Implementing a simple web service utilizing the specification involves several key steps.
A crucial element is the standardized metadata exchange for service discovery. This enables clients to automatically locate and interact with relevant web services, improving efficiency and reducing manual configuration.
Simple Web Service Implementation
The specification facilitates the creation of a discoverable web service. The process begins with defining the service’s metadata, including endpoints, functionalities, and required parameters. This metadata is then published using the specification’s protocols, making it accessible to potential clients. Clients can then query the discovery service to identify available services matching their needs.The core elements of this implementation are:* Metadata Definition: Defining the service’s characteristics (endpoints, functions, data types, etc.) in a standardized format.
This metadata becomes the blueprint for interaction.
Metadata Publication
Publishing the defined metadata to the discovery service, ensuring accessibility to potential clients. This is typically achieved via a designated registry or directory.
Client Discovery
Clients use the specification’s discovery mechanisms to locate services matching their requirements. This is often facilitated by querying the discovery service using the standardized query language.
Service Interaction
Once a service is located, clients can interact with it via the identified endpoints, following the defined protocols and data formats.
Scenario Demonstrating Problem Solving
Imagine a scenario where a company has multiple internal web services. Each service provides a specific function, and applications need to access these services dynamically. Without a standardized discovery mechanism, developers need to hardcode the service URLs, which is cumbersome and error-prone. Using the specification, the services register themselves in a central discovery service. Applications can query the discovery service to find the available services.
This eliminates the need for hardcoding URLs and allows the system to adapt to changes in service availability and location.
A retail application needs to access various backend services (inventory, order processing, payment gateway). Without a discovery mechanism, the application would need to know the precise URLs of each service, making updates and maintenance difficult. Using the specification, the backend services register themselves with a central registry. The application queries the registry for the available services and dynamically connects to the appropriate service. This solution allows the application to easily adapt to changes in the backend services’ locations or functionalities.
Conclusive Thoughts
In conclusion, the Microsoft Intel Push Web Services Discovery Spec presents a compelling solution for enhancing web service discovery. While challenges related to interoperability and security exist, the potential benefits and use cases across diverse industries are substantial. This specification holds promise for a more interconnected and efficient future of web services.