Microsoft Issues Record Number of Critical Patches
Microsoft issues record number of critical patches, highlighting the ever-present threat landscape in software security. This flurry of updates signals a significant vulnerability problem across various Microsoft products, from Windows to Office to Azure. Understanding the severity, deployment strategies, and root causes is crucial for users and businesses alike, as these patches could impact everything from home computers to enterprise operations.
The sheer volume of these patches demands attention, prompting a deeper look into the challenges of maintaining software security in today’s digital world.
This in-depth analysis examines the severity and impact of these critical patches, exploring the potential risks to different user groups. We’ll delve into Microsoft’s patch deployment strategies, analyze the root causes behind the surge in vulnerabilities, and evaluate the impact on business operations. Furthermore, we’ll consider the future implications and trends in software security, and discuss the role of user education in preventing attacks.
A crucial aspect of this discussion is understanding the potential financial costs associated with security breaches and the best practices for implementing patch management strategies.
Severity and Impact of Issues
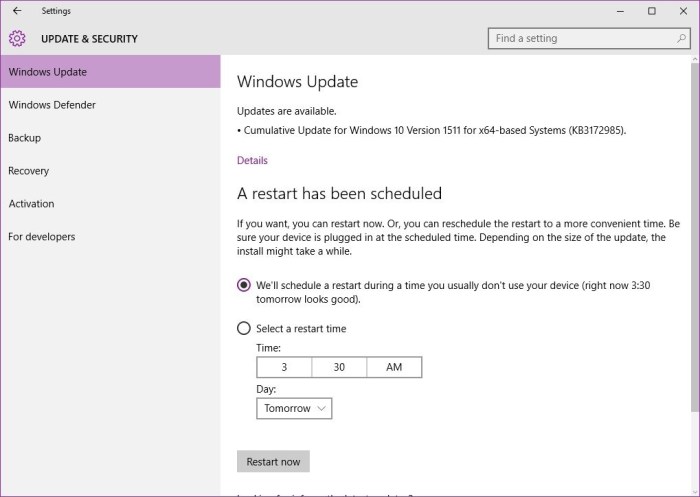
Microsoft has proactively addressed a significant number of critical security vulnerabilities. Understanding the severity and impact of these issues is crucial for users to take appropriate precautions and ensure the protection of their systems. This analysis delves into the specifics of the patched vulnerabilities, their potential consequences, and the varying levels of risk across different user groups.
Criticality Levels and Associated Risks
The patched vulnerabilities vary in their criticality, reflecting the potential harm they pose. High-severity vulnerabilities often allow attackers to gain unauthorized access, execute malicious code, or steal sensitive data. Medium-severity vulnerabilities typically grant attackers limited access or allow them to disrupt specific functionalities. Low-severity vulnerabilities present a minimal risk, usually requiring a specific sequence of events or exploiting existing weaknesses to be truly harmful.
The risk associated with each vulnerability level directly correlates with the potential impact on the affected system and user. For example, a high-severity vulnerability could lead to widespread system compromise, while a low-severity vulnerability might only impact a limited set of users or functionalities.
Impact on Different User Groups
The impact of these patched vulnerabilities varies across user groups. Home users, often relying on personal systems for everyday tasks, face risks such as identity theft, data loss, or system compromise. Businesses, using their systems for crucial operations, face potential financial losses, operational disruptions, and reputational damage from security breaches. Developers, on the other hand, may encounter issues impacting their applications or tools, leading to delays or disruptions in their workflow.
The potential for disruption across these user groups is substantial, and it’s essential to understand the varying levels of exposure.
Types of Vulnerabilities Addressed
The patches address a range of vulnerabilities, including security holes and software bugs. Security holes, which are often exploited by malicious actors, could lead to unauthorized access to sensitive information. Software bugs, though not inherently malicious, could lead to unexpected behavior, system crashes, or data corruption. A combination of both types of vulnerabilities can have significant repercussions.
For example, a security hole in a web server combined with a software bug in a related application could enable attackers to gain complete control of the system.
Vulnerability Severity Comparison Across Product Lines
| Product Line | High Severity | Medium Severity | Low Severity |
|---|---|---|---|
| Windows | Remote code execution vulnerabilities in the kernel, critical for system integrity. | Compromised authentication protocols, impacting user accounts and access control. | Minor issues in specific components, unlikely to impact majority of users. |
| Office | Exploitable vulnerabilities in document handling components, potentially allowing malicious code execution. | Vulnerabilities in macro processing, allowing attackers to execute harmful code when documents are opened. | Minor bugs in specific features, requiring a targeted attack to exploit. |
| Azure | Vulnerabilities in cloud services, impacting data security and availability. | Vulnerabilities in APIs, potentially allowing unauthorized access to data or resources. | Issues in specific components of Azure, impacting a small portion of users. |
This table illustrates a comparison of the severity levels of vulnerabilities patched across different product lines. The criticality of vulnerabilities differs across these product lines due to the varying levels of trust and importance associated with each.
Patch Deployment Strategies
Microsoft’s commitment to security necessitates a robust patch deployment strategy. The sheer volume of devices and users necessitates a sophisticated approach, ranging from automatic updates to carefully managed phased rollouts. This intricate process involves considerable planning, testing, and meticulous execution. The successful implementation of these strategies directly impacts the security posture of the entire ecosystem.Microsoft’s approach to patch deployment is multifaceted, employing various strategies tailored to different scenarios and priorities.
The aim is to minimize disruption while maximizing security. This involves understanding the potential impact of each patch, considering the varying levels of user experience, and carefully calibrating the deployment timelines.
Microsoft’s Patch Deployment Approach
Microsoft typically employs a combination of automatic updates and manual installations, often with phased rollouts. Automatic updates are designed for widespread adoption, ensuring users receive security enhancements promptly. Manual installations are reserved for situations where automatic updates are impractical or undesirable. Phased rollouts allow for controlled testing in select environments before wider dissemination. This approach helps identify and address potential issues in a contained manner.
Challenges in Large-Scale Patch Deployment
Deploying patches on a massive scale presents significant challenges. The sheer number of devices—from desktops to servers to mobile devices—requires careful consideration of potential conflicts, compatibility issues, and the potential for widespread disruption. Furthermore, different user environments and varying levels of technical expertise necessitate adaptable deployment strategies. Addressing these challenges requires proactive monitoring, extensive testing, and a deep understanding of potential risks.
Comparison of Patch Deployment Strategies, Microsoft issues record number of critical patches
Different patch deployment strategies offer varying trade-offs between speed, security, and user experience. Automatic updates are rapid and ensure broad coverage, but they may cause unintended conflicts with existing applications. Manual installations allow for careful testing and control, but they can introduce delays and require significant administrative overhead. Phased rollouts represent a balance between speed and control, offering a controlled release in manageable increments.
The optimal strategy depends heavily on the specific circumstances and potential impact on users.
Patch Installation Process for Different Operating Systems
The patch installation process varies slightly across operating systems like Windows and macOS. For Windows, the process typically involves downloading the patch, prompting the user for confirmation, and applying the update. For macOS, the process often involves a similar sequence, with the OS handling much of the update process in the background. Understanding these differences is critical for effective patch management.
Steps Involved in the Patch Installation Process
- Windows: Download the patch, initiate the installation, confirm user consent, and apply the update.
- macOS: Download the patch, initiate the installation, and potentially restart the system to apply the update.
Patch Release Cycles for Microsoft Products
The patch release cycles for Microsoft products vary depending on the product type and the nature of the update. Some updates are critical security fixes, while others address functional improvements or compatibility issues. The table below illustrates the differences in patch release cycles for various Microsoft products.
Microsoft’s recent release of a record number of critical patches highlights the ongoing cybersecurity challenges. While this is a major concern, it’s interesting to see how the broader political landscape is also impacting tech discussions, like the intense debate surrounding the Supreme Court. The current battle over the Supreme Court, as seen in the online discourse, battle over supreme court already raging on the net , might subtly influence the urgency of these security patches.
Regardless, Microsoft’s proactive approach to patching is essential to keep systems secure in this constantly evolving digital environment.
| Product | Typical Patch Release Cycle |
|---|---|
| Windows 10 | Monthly, with optional cumulative updates |
| Windows Server | Monthly, with optional cumulative updates |
| Office Suite | Regularly, with updates aligned with feature releases |
| Microsoft 365 | Frequent, with updates delivered based on feature release cycles |
Root Causes and Prevention

The recent surge in critical Microsoft patches highlights a complex interplay of factors contributing to vulnerabilities. Understanding these root causes is crucial for developing effective prevention strategies. This analysis delves into potential causes, Microsoft’s vulnerability prevention strategies, and industry trends, ultimately examining the impact on user trust and adoption.Microsoft’s proactive approach to patching, while essential, necessitates a deeper look at the underlying issues driving the frequency of these critical updates.
Potential Causes of High Patch Frequency
Several factors contribute to the high number of critical patches released by Microsoft. These include the increasing complexity of software, the rapid pace of technological advancements, and the ever-evolving threat landscape. The complexity of modern software systems, encompassing numerous interconnected components and dependencies, can lead to unforeseen vulnerabilities. Furthermore, the constant emergence of new attack vectors and sophisticated cyber threats demands continuous adaptation and proactive patching.
The aggressive innovation cycle, while crucial for progress, can sometimes introduce unforeseen vulnerabilities into the software.
Microsoft’s Vulnerability Prevention Strategies
Microsoft employs a multi-faceted approach to preventing vulnerabilities. This includes rigorous code review processes, security testing throughout the development lifecycle, and the implementation of advanced threat intelligence systems. The company actively collaborates with researchers and security experts to identify and address potential vulnerabilities. Continuous monitoring and analysis of emerging threats form a critical part of Microsoft’s strategy.
Industry Trends in Software Vulnerabilities
The software development industry is facing a confluence of trends impacting vulnerability frequency. The rise of interconnected devices, creating the Internet of Things (IoT), introduces a wider attack surface. The growing reliance on cloud computing, while offering convenience, necessitates robust security measures to protect sensitive data and infrastructure. The escalating sophistication of cyberattacks necessitates continuous adaptation and innovation in security protocols and practices.
Moreover, the rapid pace of software development and deployment cycles can create vulnerabilities if security measures are not integrated into every stage of the process.
Impact on User Trust and Adoption
The frequency of critical patches can impact user trust and adoption. Users may perceive a lack of stability and reliability in software if they are constantly receiving security updates. This can lead to hesitation in adopting new features or technologies. The perception of security risk is a crucial factor influencing adoption rates. Ultimately, maintaining user trust is vital for Microsoft’s continued success.
Comparison of Vulnerability Management Approaches
Different tech companies employ varying strategies for vulnerability management. While Microsoft’s approach focuses on proactive patching and collaboration, other companies may prioritize different aspects of the vulnerability lifecycle. This includes a range of strategies, from penetration testing to vulnerability disclosure programs, depending on the company’s specific risk profile and resources. It’s essential to consider the interplay of these factors in assessing the effectiveness of different approaches.
Comparison requires a nuanced understanding of specific practices and priorities within each company.
Impact on Business Operations: Microsoft Issues Record Number Of Critical Patches
Microsoft’s recent release of critical patches highlights the ongoing struggle businesses face balancing security updates with operational efficiency. These updates, while crucial for maintaining system integrity, can introduce potential downtime and disrupt various business processes. Understanding the potential financial implications and adopting proactive patch management strategies is vital for mitigating risks and ensuring business continuity.
Microsoft’s recent release of a record number of critical patches highlights the ongoing need for robust security measures. This flurry of updates likely stems from vulnerabilities, perhaps even those connected to the recent FCC approval of Tivo technology. FCC’s okay for Tivo tech might have exposed new avenues for potential exploits, further emphasizing the urgency of Microsoft’s proactive patch deployment.
Ultimately, the frequency of these critical patches underscores the ever-evolving cyber landscape and the importance of staying vigilant against threats.
Potential Downtime and Business Disruptions
Patching processes, especially for large-scale deployments, can introduce significant downtime. The complexity of modern IT infrastructure, with interconnected systems and dependencies, often leads to cascading effects. A single failed patch application can halt entire workflows, impacting production, customer service, and overall revenue generation. The duration of this downtime, from a few minutes to several hours, can vary based on the scale of the patch deployment and the complexity of the affected systems.
Furthermore, insufficient testing and validation of patches before deployment can exacerbate these issues, leading to unforeseen errors and extending downtime.
Financial Implications Across Industries
The financial impact of critical patches varies greatly across industries. Industries heavily reliant on uninterrupted operations, such as finance, healthcare, and e-commerce, face substantial financial losses from even brief downtime. Revenue loss, decreased productivity, and potential customer churn are all significant financial implications. For example, a major e-commerce platform experiencing prolonged downtime during a peak shopping season could lose millions in potential sales.
Examples of Companies Affected by Security Issues
Several high-profile companies have experienced significant financial and reputational damage due to security breaches. Target, for instance, suffered a massive data breach in 2013, leading to substantial financial losses, customer distrust, and reputational damage. Similarly, Equifax’s 2017 data breach resulted in significant financial settlements and regulatory scrutiny. These examples underscore the importance of robust security measures and proactive patch management to prevent similar incidents.
Best Practices for Patch Management
Effective patch management requires a multi-faceted approach. Regular vulnerability assessments, comprehensive patch testing, and phased deployment strategies are crucial elements. A well-defined patch management policy, encompassing clear procedures and responsibilities, ensures consistent application across the organization. Furthermore, training employees on security best practices and incident response protocols is essential to minimize human error.
Table Illustrating Potential Costs of Security Breaches
| Severity of Vulnerability | Estimated Cost (USD) | Description |
|---|---|---|
| Low | $10,000 – $50,000 | Minor data breaches, limited impact on operations |
| Medium | $50,000 – $500,000 | Significant data breaches, partial disruption of operations, potential reputational damage |
| High | $500,000 – $10,000,000+ | Major data breaches, widespread disruption of operations, severe reputational damage, legal liabilities |
Note: These figures are estimates and may vary based on specific circumstances, such as the industry, the size of the affected organization, and the nature of the security breach.
Future Implications and Trends
Microsoft’s proactive approach to patching critical vulnerabilities underscores a crucial shift in the security landscape. The sheer volume of patches released indicates a heightened awareness of the ever-evolving threat landscape and the increasing sophistication of cyberattacks. This proactive stance is not merely reactive; it reflects a commitment to maintaining a robust security posture in the face of evolving threats.
Microsoft’s recent release of a record number of critical patches highlights the ever-evolving threat landscape. Meanwhile, IBM’s announcement of expanded support for its BladeCenter systems, a significant development in server infrastructure , suggests a proactive approach to security and performance. This ultimately underscores the need for robust security measures in the face of such frequent Microsoft updates.
Long-Term Implications on the Security Landscape
The frequency of critical patch releases signifies a persistent and evolving threat environment. Attackers are continuously developing new exploits and techniques to bypass security measures. This dynamic necessitates a proactive and adaptive approach to security, demanding continuous monitoring and updating of security infrastructure and practices. The long-term implication is a continuous cycle of vulnerability discovery, patch deployment, and adaptation to maintain security.
Future Trends in Software Security
Future trends in software security point towards increased automation in vulnerability detection and patching. Machine learning and AI will play a pivotal role in identifying potential vulnerabilities faster and more effectively. Furthermore, the focus will shift towards proactive security measures, such as code analysis and secure coding practices, implemented during the software development lifecycle. This shift signifies a paradigm shift from primarily reactive to proactive security measures.
Potential Rise in Malicious Activities
The potential for a rise in malicious activities is directly correlated with the sophistication of attack methods. Attackers are likely to exploit vulnerabilities in new and innovative ways, leveraging emerging technologies like AI and automation. The rise of ransomware-as-a-service (RaaS) further amplifies the threat, enabling less skilled actors to execute sophisticated attacks. This trend emphasizes the critical need for robust security measures at all levels, from individual users to enterprise systems.
Role of User Education in Preventing Attacks
User education remains a critical component in mitigating the impact of cyberattacks. Educating users about phishing attempts, social engineering tactics, and safe online practices is essential to prevent successful attacks. Training programs should focus on recognizing suspicious emails, websites, and links, as well as the importance of strong passwords and multi-factor authentication. Empowering users with the knowledge and skills to recognize and avoid threats is a key component of a layered security strategy.
“The future of software security demands a proactive, adaptive, and layered approach. Continuous monitoring, automation, user education, and robust security infrastructure are essential to mitigating the ever-evolving threat landscape.”
Technical Details of Vulnerabilities (Optional)
Microsoft’s recent patch releases address a wide range of vulnerabilities, highlighting the ongoing need for robust security measures. Understanding the technical specifics of these vulnerabilities is crucial for effective mitigation and future prevention. This section delves into the types of vulnerabilities patched, providing examples and technical details.
Types of Vulnerabilities Patched
Microsoft’s security updates frequently target various vulnerabilities. These include, but are not limited to, buffer overflows, SQL injection, remote code execution (RCE), and cross-site scripting (XSS). Understanding the nature of these vulnerabilities is critical to effective patching and incident response.
Specific Vulnerabilities Addressed
Several prominent vulnerabilities have been addressed in the recent patches. One example is a vulnerability in the Windows kernel that could allow an attacker to gain unauthorized access. Another example is a flaw in a specific library used in various applications, potentially enabling remote code execution.
Exploitation Techniques
Vulnerabilities can be exploited in diverse ways. Buffer overflows, for instance, can be triggered by carefully crafted input data that overwrites memory locations, leading to arbitrary code execution. SQL injection exploits vulnerabilities in applications that interact with databases. Malicious input can manipulate database queries, allowing attackers to access unauthorized data or execute commands.
Common Software Vulnerabilities
| Vulnerability Type | Description | Example |
|---|---|---|
| Buffer Overflow | Occurs when a program attempts to write data beyond the allocated buffer size, potentially overwriting adjacent memory locations. | A program reads excessively large input data, leading to data overflow into other program areas. |
| SQL Injection | Attackers inject malicious SQL code into input fields, altering legitimate queries to gain unauthorized access or modify data. | Inputting malicious SQL statements into a login form to bypass authentication. |
| Cross-Site Scripting (XSS) | Attackers inject malicious scripts into web pages viewed by other users. | Inserting JavaScript code into a website’s comment section. |
| Remote Code Execution (RCE) | Attackers exploit vulnerabilities to execute arbitrary code on a target system. | Exploiting a vulnerability in a web server to execute malicious commands. |
Attack Vector: Buffer Overflow
Buffer overflows exploit the way data is handled in computer memory. If an attacker provides carefully crafted input exceeding the allocated buffer size, the extra data can overwrite adjacent memory locations. This can lead to arbitrary code execution. 
Final Thoughts
In conclusion, the record number of critical patches from Microsoft underscores the persistent need for robust security measures in software development and deployment. The analysis reveals the multifaceted challenges involved, from the potential for significant downtime in patching to the financial implications for businesses. Looking ahead, the future of software security hinges on continuous vigilance, proactive vulnerability management, and user education.
Microsoft’s response, while reactive, serves as a stark reminder that the fight against vulnerabilities is an ongoing battle, demanding constant adaptation and innovation.