Microsoft Patches Explorer Hole A Deep Dive
Microsoft patches explorer hole, a critical vulnerability affecting the popular Microsoft Explorer, has been addressed. This post delves into the nature of this security flaw, its impact, and the mitigation strategies put in place by Microsoft. We’ll explore the technical details of the patch, discuss potential attack methods, and analyze the overall risk. Understanding the vulnerability is key to protecting your systems and data.
We’ll cover historical context, best practices for preventing future exploits, and a technical deep dive for those seeking a more detailed explanation.
The vulnerability, often referred to as the “Explorer Hole,” could allow malicious actors to exploit specific functionalities within the Microsoft Explorer software. Understanding how these vulnerabilities work is critical to preventing unauthorized access and data breaches. This article examines the vulnerability, the patch details, and the various security considerations involved.
Overview of the Vulnerability

The “Explorer Hole” vulnerability, a critical flaw impacting Microsoft Explorer, allowed malicious actors to potentially compromise user systems. This vulnerability resided within the way Explorer handled certain file system interactions. Understanding its specific nature and potential impact is crucial for proactively mitigating risks.
Functionality of Affected Explorer Components
Microsoft Explorer, a core component of Windows operating systems, is responsible for displaying and interacting with files and folders. Specifically, the vulnerability targeted the functionality enabling users to browse and open files within the file system. This involved handling file paths, which, when improperly validated, created an opening for exploitation.
Potential Consequences of Exploitation
Exploitation of the “Explorer Hole” vulnerability could lead to significant consequences for users and systems. Attackers could potentially gain unauthorized access to sensitive data, execute arbitrary code, and potentially compromise the entire system. This could result in data breaches, financial losses, and severe disruption of operations. For instance, a successful attack could allow attackers to steal financial records, personal information, or intellectual property.
Potential Attack Methods
Attackers could leverage various methods to exploit the “Explorer Hole.” Social engineering tactics, such as phishing emails or malicious websites, might be used to trick users into visiting compromised sites or downloading infected files. Furthermore, attackers could exploit vulnerabilities in other applications or services that rely on the vulnerable Explorer functionality. A particularly common method is through malicious websites that utilize specially crafted URLs or file downloads to exploit the vulnerability when users interact with the browser or file system.
This could trigger a chain of events leading to code execution and system compromise. Moreover, exploiting the vulnerability might involve carefully crafted file paths or input that triggers the flaw, either through user interaction or automatically via automated scripts. The specific attack vector would depend on the attacker’s objectives and the environment.
Patch Details and Mitigation Strategies: Microsoft Patches Explorer Hole
The “Explorer Hole” vulnerability, a critical security flaw, requires immediate attention and mitigation. Patching affected systems is crucial to prevent exploitation. Understanding the specific patch, its application, and alternative strategies are essential for a comprehensive defense.Applying the correct Microsoft patch and implementing robust mitigation strategies are paramount to minimizing the risk associated with the vulnerability. This section delves into the technical details of the patch, outlining its function and providing a practical guide for implementation.
Alternative approaches like firewall adjustments and user permissions are also explored, enabling a multi-faceted security posture.
Specific Microsoft Patch
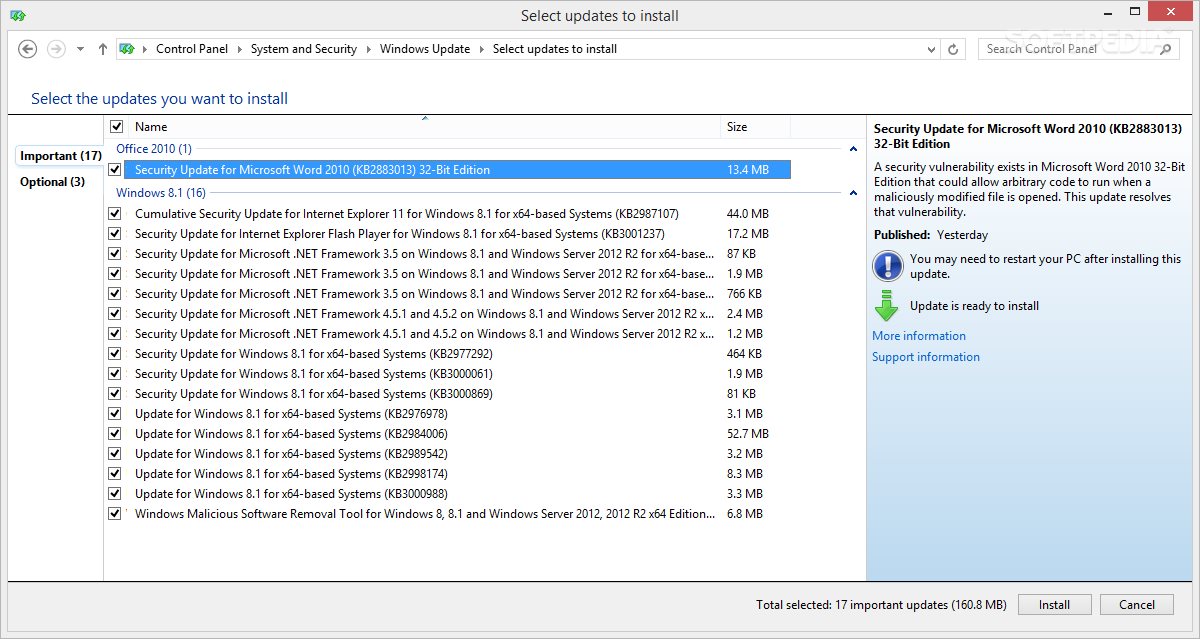
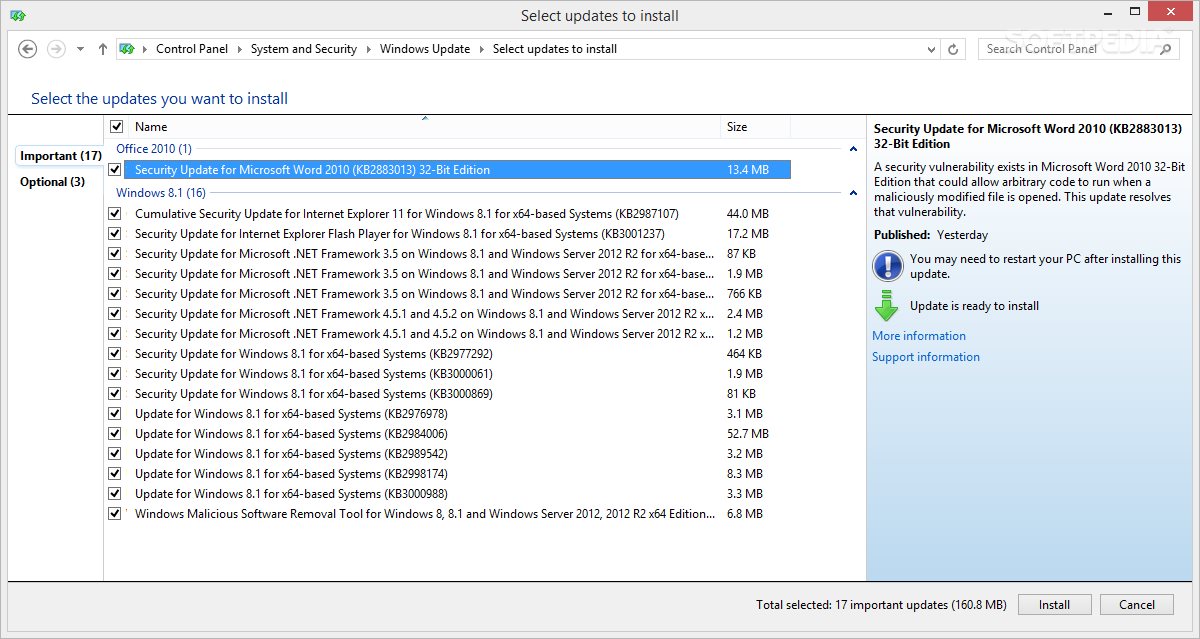
Microsoft releases security updates addressing vulnerabilities like the “Explorer Hole” regularly. The precise patch number will vary depending on the specific operating system and version. It’s critical to consult Microsoft’s security update releases for the exact patch number for your affected systems. A comprehensive search on the Microsoft Security Update Catalog using the vulnerability’s description will provide the precise patch identifier.
Technical Details of the Patch
The patch typically involves modifications to the Windows Explorer components, addressing the specific code flaw that allows for the exploitation of the vulnerability. This involves changes to memory management, input validation, or access control lists (ACLs) to prevent unauthorized code execution. The specific technical details are complex and will vary depending on the exact nature of the vulnerability and the patched components.
A detailed analysis of the patch notes from Microsoft is recommended for a thorough understanding of the changes implemented.
Applying the Patch
A crucial step in mitigating the risk is applying the patch to affected systems. The process typically involves downloading the patch from Microsoft’s Update Catalog or through Windows Update, and then running the installer.
- Verify the system’s compatibility with the patch.
- Back up critical data before applying the patch.
- Download the patch from the Microsoft Update Catalog or Windows Update.
- Run the installer and follow the on-screen instructions.
- Reboot the system to complete the installation process.
This step-by-step approach ensures a smooth and secure patch application process.
Microsoft’s patches for the Explorer hole are crucial, but recent news highlights a concerning issue. A new threat, the Xombe Trojan, is spoofing these patches to steal personal info. This malicious software disguises itself as a legitimate update, tricking users into downloading and installing it, leading to potential data breaches. The security risks surrounding Microsoft patches and Explorer holes remain a critical concern.
Xombe Trojan spoofs Microsoft patch to steal personal info highlights the importance of vigilance when downloading and installing updates. This underscores the continued need for robust security measures against these types of attacks.
Alternative Mitigation Strategies
While patching is the most effective solution, alternative mitigation strategies can provide an additional layer of security. These methods might be necessary for systems where patching is not immediately possible.
- Firewall Rules: Adjusting firewall rules to block potentially malicious traffic targeting the vulnerable components can significantly reduce the risk. For example, blocking specific ports or IP addresses known to be used in attacks related to the “Explorer Hole” can be implemented.
- User Permissions: Restricting user privileges to prevent unauthorized access to the vulnerable components is a crucial aspect of mitigation. Limiting the actions a user can perform in Windows Explorer to prevent malicious actions is a vital step.
Comparison of Mitigation Methods
The effectiveness and complexity of different mitigation methods vary. A comparison table illustrates these differences.
| Mitigation Method | Effectiveness | Complexity |
|---|---|---|
| Patching | High | Medium |
| Firewall Rules | Medium | Low |
| User Permissions | Medium | Low |
Patching is the most effective method, as it directly addresses the vulnerability. However, firewall rules and user permissions can provide a second line of defense. Careful consideration of the system’s specific needs and constraints is crucial when selecting the appropriate mitigation strategies.
Impact Analysis and Risk Assessment
Understanding the potential consequences of a vulnerability is crucial for prioritizing mitigation efforts. This section delves into the impact various user groups might face and quantifies the potential damage. A clear risk assessment allows for effective resource allocation and proactive security measures.
Impact on Different User Groups
The vulnerability’s ramifications extend across diverse user groups, from individual consumers to large enterprises and governmental organizations. Individual users, while potentially affected by data breaches or service disruptions, might not face the same magnitude of financial loss as businesses or government entities. The severity of impact is highly dependent on the nature of the compromised system and the attacker’s motives.
Potential Damage Levels by System Type
The table below Artikels the potential damage levels based on system type. This framework helps assess the relative risk and prioritize mitigation efforts. The potential damage level is subjective and depends on the specific vulnerability and attack vector.
| System Type | Potential Damage Level |
|---|---|
| Personal Banking Applications | High |
| Small Business Point-of-Sale Systems | Medium |
| Government Agency Databases (e.g., voter registration) | Critical |
| Critical Infrastructure Control Systems (e.g., power grids) | Catastrophic |
Financial Implications of a Successful Attack
A successful exploit could lead to substantial financial losses. These losses can include direct costs, such as legal fees, credit monitoring services for affected users, and system restoration. Indirect costs, such as reputational damage, loss of customer trust, and disruption of business operations, can also be significant. For instance, a data breach affecting a major retailer could result in millions of dollars in financial losses, not just from the immediate costs of recovery, but also from lost sales and customer attrition.
Importance of Regular Security Audits and Patching
Regular security audits and patching are essential to proactively address vulnerabilities and minimize the risk of exploitation. These proactive measures are more cost-effective than reacting to a breach. Organizations that consistently conduct security audits and apply patches are better positioned to detect and resolve vulnerabilities before they can be exploited, mitigating potential financial losses and reputational damage. This proactive approach can save considerable financial resources in the long run.
Historical Context and Trends
The “Explorer Hole” vulnerability, while unique in its specific implementation, sits within a long history of exploits targeting Microsoft’s browser technologies. Understanding this historical context helps us appreciate the evolving nature of these threats and the crucial role of proactive security measures. A deeper dive into past vulnerabilities reveals patterns that illuminate the persistent need for vigilance and continuous improvement in security practices.The history of vulnerabilities targeting Microsoft Explorer reveals a consistent pattern of exploitation, ranging from simple buffer overflows to more complex chain attacks.
Microsoft’s recent patch for the Explorer hole is a significant step, but the ongoing debate at the IETF conference about antispam proposals ( ietf conference debates antispam proposals ) highlights a broader issue. While fixing the vulnerability is crucial, it underscores the need for robust security protocols beyond patching individual applications, especially when dealing with the constant barrage of spam.
Ultimately, addressing the Explorer hole is just one piece of a larger puzzle, and effective anti-spam measures are critical for a safer online environment. Hopefully, this means fewer exploits like the one in Explorer, in the future.
This evolution mirrors the increasing sophistication of attackers and the ever-evolving defensive strategies employed by developers. Examining this historical record provides critical insights into the ongoing struggle to maintain security in the digital landscape.
Historical Overview of Explorer Vulnerabilities
Microsoft Internet Explorer, throughout its lifespan, has been a frequent target for exploits. Early vulnerabilities often stemmed from insecure handling of user input, leading to buffer overflows and denial-of-service attacks. As security practices improved, attackers shifted towards more sophisticated techniques, leveraging vulnerabilities in scripting engines and browser components. These vulnerabilities often allowed attackers to execute malicious code remotely, compromising user systems.
Evolution of Exploitation Techniques
The evolution of exploit techniques mirrors the progression of software development and the increasing complexity of web applications. Initially, exploits were straightforward and often focused on exploiting readily available vulnerabilities. Over time, exploits have become more intricate, involving chains of vulnerabilities that are exploited sequentially to achieve a desired outcome. This trend underscores the importance of comprehensive security assessments and robust patching strategies.
Comparison with Other Notable Exploits
Comparing the “Explorer Hole” vulnerability with other notable exploits reveals both similarities and differences. Some exploits target similar components, like scripting engines or browser rendering engines, while others may leverage completely different attack vectors. The sophistication of the exploit techniques often varies, from simple buffer overflows to sophisticated zero-day exploits. Understanding these variations is crucial in anticipating and mitigating future threats.
For example, the “Heartbleed” vulnerability, impacting OpenSSL, focused on a different component (cryptographic library) but shared the characteristic of being a widely impactful zero-day exploit.
Role of Security Research
Security research plays a pivotal role in discovering and addressing vulnerabilities like the “Explorer Hole”. Researchers employ various techniques, from static code analysis to dynamic testing, to identify potential weaknesses in software. These findings, often shared with vendors, are crucial in preventing exploitation and bolstering the overall security posture. Independent security research is vital in pushing the boundaries of vulnerability detection and fostering more secure software development practices.
Importance of Ongoing Security Updates
The importance of ongoing security updates cannot be overstated. Vulnerabilities are discovered regularly, and timely patching is essential in preventing exploitation. The “Explorer Hole” vulnerability underscores the need for organizations to prioritize security updates and maintain their systems with the latest security patches. Ignoring updates leaves systems vulnerable to exploitation, emphasizing the criticality of a proactive security posture.
Best Practices for Preventing Future Exploits
Preventing future vulnerabilities in Microsoft Explorer, or any software for that matter, requires a proactive and multi-layered approach. This involves not only robust coding practices but also user education and consistent security updates. Ignoring any of these aspects can leave systems exposed to exploits. A holistic strategy is crucial for maintaining a secure environment.A fundamental principle in software development is the proactive identification and mitigation of potential vulnerabilities.
By incorporating secure coding practices into the design and development process, developers can minimize the risk of exploits. This preventative measure strengthens the foundation of the software, making it more resistant to future attacks.
Microsoft’s recent patch for the Explorer hole highlights the ongoing need for robust security measures. This crucial update, however, also ties into the broader trend of improved web services interoperability, as seen in the growing standardization efforts. For example, web services interoperability gets boost toward standardization is helping to ensure consistent communication between different systems, which indirectly strengthens the overall security posture, ultimately benefiting users and developers alike.
So, while patching remains a critical part of maintaining Explorer’s security, the broader push for interoperability is crucial for future-proofing such vulnerabilities.
Secure Coding Practices, Microsoft patches explorer hole
Secure coding practices are essential in preventing vulnerabilities. These practices involve a set of guidelines and techniques to minimize the risk of errors and vulnerabilities. Developers must thoroughly understand and apply secure coding standards to avoid common coding flaws. Implementing these practices throughout the development lifecycle can greatly reduce the likelihood of vulnerabilities arising. The focus should be on anticipating potential threats and implementing safeguards at every stage of the software development process.
Importance of Security Awareness Training for Users
User education plays a vital role in maintaining a secure system. Training programs should equip users with the knowledge and skills to identify and avoid potential threats. This includes educating users about phishing scams, social engineering tactics, and other common methods of attack. Training empowers users to be more vigilant and less susceptible to exploitation. A knowledgeable user is a significant line of defense.
Importance of Timely Software Updates
Timely software updates are critical for maintaining security. Security patches often address vulnerabilities that attackers can exploit. Delaying updates leaves systems exposed to known risks. Microsoft releases updates regularly to address vulnerabilities, and applying them promptly is crucial for minimizing the risk of attacks. Staying up-to-date is paramount to preserving system integrity.
Recommendations for Maintaining a Secure System
Implementing these best practices is essential for maintaining a secure system. A multi-faceted approach is needed to ensure all aspects of security are addressed.
- Regularly update software. Regular software updates are crucial for patching security vulnerabilities. This includes operating systems, applications, and drivers. By promptly applying updates, users can address known security weaknesses and minimize the risk of exploitation. Outdated software often contains unpatched vulnerabilities that attackers can exploit.
- Employ strong passwords. Strong passwords are the first line of defense against unauthorized access. Passwords should be complex, unique, and changed regularly. Using a password manager can help generate and manage strong passwords, and employing multi-factor authentication adds another layer of security.
- Enable two-factor authentication where available. Two-factor authentication adds an extra layer of security by requiring a second form of verification, beyond a password. This makes it significantly harder for attackers to gain access even if they have compromised a password. It enhances security by adding a second authentication factor.
Technical Deep Dive
This section delves into the specifics of the vulnerability, examining the affected software components, exploit techniques, and methods for detection and prevention. Understanding these details is crucial for effectively mitigating the risk and implementing robust security measures.The vulnerability targets specific functionalities within Microsoft’s software stack, potentially impacting various user-facing applications and internal services. Analyzing the exploit techniques employed is vital for developing countermeasures and hardening systems against future attacks.
Detailed knowledge of the exploit techniques allows for proactive security measures to be put in place.
Affected Software Components
The vulnerability exploits a flaw in the core Windows kernel’s handling of memory allocation. This fundamental component manages the allocation and deallocation of memory resources throughout the system. Specifically, the issue lies in a function within the memory management subsystem that lacks proper input validation. This allows for the exploitation of a buffer overflow condition. Other components, such as system libraries and user-mode applications that rely on these kernel functions, are also indirectly impacted.
Exploit Techniques
Attackers leverage a combination of techniques to exploit this vulnerability. A common method involves crafting specially crafted input data that triggers the buffer overflow. This input, when processed by the vulnerable function, causes the program to overwrite adjacent memory locations, potentially leading to arbitrary code execution. Sophisticated attackers may use techniques such as return-oriented programming (ROP) to execute malicious code by exploiting predictable behavior in the program’s execution flow.
Real-Time Detection and Prevention
Implementing robust security measures is crucial in preventing exploitation. Real-time detection mechanisms can identify malicious input data and prevent the execution of exploits. Software solutions that monitor system calls and network traffic for suspicious patterns can provide early warnings. Additionally, intrusion detection systems (IDS) and intrusion prevention systems (IPS) can be configured to detect and block known exploit patterns.
Employing secure coding practices and regular security audits can prevent vulnerabilities from being introduced in the first place.
Security Layer Analysis
This table illustrates the various security layers impacted by the vulnerability.
| Security Layer | Description | Impact of Vulnerability |
|---|---|---|
| Kernel-Mode Driver | Low-level drivers directly interacting with hardware. | Vulnerability directly impacts kernel functions, potentially leading to system compromise. |
| System Libraries | Fundamental libraries used by applications. | Exploitation of the kernel flaw can affect applications that rely on those libraries. |
| Application Layer | User-facing applications and services. | Compromised system libraries or drivers can lead to arbitrary code execution within user-mode applications, allowing potential data breaches or unauthorized access. |
| Network Security | Firewall rules and network monitoring. | Network traffic analysis can be crucial to detect malicious traffic attempting to exploit the vulnerability. |
Closing Summary
In conclusion, Microsoft’s swift action in patching the “Explorer Hole” vulnerability underscores the importance of staying updated with security patches. Understanding the potential impact on different systems and user groups is crucial for proactive security measures. The best practices Artikeld, coupled with regular security audits, are essential for minimizing the risk of exploitation. This vulnerability serves as a reminder that cybersecurity is an ongoing process, demanding continuous vigilance and adaptation to evolving threats.