Mimail Email Worm Rapid Spread Explained
With mimail e mail worm spreads quickly, understanding how these malicious programs exploit email systems is crucial. This worm, capable of rapid proliferation, leverages the very infrastructure we use for communication. It can infiltrate our inboxes, often disguised as legitimate messages, and wreak havoc on individual computers and entire networks.
This exploration dives deep into the anatomy of this email worm, examining its methods of propagation, the vulnerabilities it exploits, and the potential impact on various targets. We’ll also discuss preventative measures and strategies for mitigating the damage.
Defining the Email Worm
An email worm is a self-replicating malware program that spreads through email systems. It exploits vulnerabilities in email clients and servers to automatically forward copies of itself to other email addresses in the recipient’s address book or other email lists. These automated actions often overwhelm email infrastructure and can cause significant disruption.Email worms are a serious threat to both individuals and organizations, as they can quickly compromise large numbers of systems, leading to data breaches, financial losses, and reputational damage.
Understanding their characteristics, methods of propagation, and disguises is crucial for effective prevention and mitigation.
Characteristics of an Email Worm
Email worms are characterized by their ability to autonomously replicate and spread through email systems. They often have intricate code designed to evade detection and remain hidden until they have infected a significant number of machines. Their rapid proliferation makes them particularly dangerous. The core feature is their ability to exploit email systems for their propagation.
Methods of Propagation
Email worms typically spread by attaching themselves to email messages as files or by embedding malicious code within the message body. They often masquerade as legitimate messages, exploiting the trust recipients place in their contacts. The worm then attempts to execute the malicious code when the recipient opens the infected file or clicks on a link. The worm then proceeds to send copies of itself to other addresses, often through the recipient’s address book or mailing lists.
Disguises and Hiding Techniques
Email worms often employ sophisticated techniques to disguise themselves as legitimate email messages. They may use spoofing to make the sender’s address appear to be from a trusted source. The message body itself might contain misleading subject lines, or be crafted to appear like a harmless notification or important announcement. This is a common technique to trick users into opening the malicious attachment or clicking a harmful link.
These tactics are crucial for the worm to evade detection and spread undetected.
Technical Aspects of Infection
The infection process typically begins when a user opens an infected email attachment or clicks a malicious link within the message. The worm then uses various techniques to gain access to the recipient’s system. These can include exploiting vulnerabilities in email clients or operating systems, or using social engineering tactics to trick the user into executing malicious code.
Once inside, the worm can then replicate itself and send copies to other addresses, often utilizing the victim’s email address book or other mailing lists.
Example of Email Worm Behavior
Imagine a worm disguised as a shipping confirmation email. The worm’s payload could be designed to steal user credentials or encrypt files. The worm will spread by sending copies to recipients in the victim’s email address book. This highlights the insidious nature of email worms. Their ability to mimic legitimate communications makes them exceptionally difficult to detect.
Email Worm Taxonomy
| Worm Name | Infection Vector | Payload Type | Propagation Method |
|---|---|---|---|
| MyDoom | Email attachment | Denial-of-service | Address book, spam |
| Sobig | Email attachment | Denial-of-service, data theft | Address book, spam |
| Melissa | Email attachment | Mass mailing | Address book |
| I Love You | Email attachment | File deletion | Address book |
This table provides a glimpse into the diverse nature of email worms. Different worms employ different infection vectors, payloads, and propagation methods. Understanding these variations is crucial for developing effective countermeasures.
Dissemination and Impact
Email worms exploit the inherent interconnectedness of digital networks to spread rapidly. Their ability to automatically propagate through email systems makes them a potent threat, potentially impacting a wide range of users and organizations. Understanding the channels they use and the damage they can inflict is crucial for effective defense.
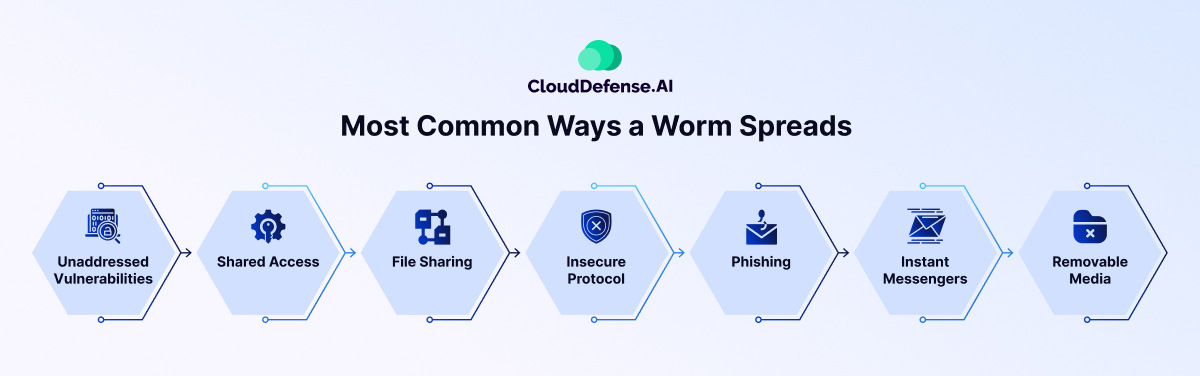
Typical Dissemination Channels
Email worms leverage various channels to spread quickly. A common tactic is exploiting vulnerabilities in email clients or servers. This allows the worm to automatically attach itself to outgoing emails, propagating to new recipients. Phishing campaigns, disguised as legitimate communications, also play a key role. Malicious links or attachments within these deceptive emails are often used to deliver the worm.
Social engineering tactics, manipulating users into clicking on infected links or opening malicious attachments, are another effective means of propagation. The worm often spreads via compromised accounts or servers, using these as launchpads to target a larger pool of users.
Common Targets
Email worms target a broad spectrum of individuals and organizations. Personal accounts, especially those with compromised passwords, are vulnerable to the propagation of these malicious programs. Small businesses, often lacking robust security measures, are frequently targeted due to their susceptibility. Large corporations, despite their security investments, can be impacted by these attacks, especially if they experience vulnerabilities in their email systems.
The worms’ impact on various targets varies greatly based on the specific worm’s capabilities and the targets’ security postures.
Potential Damage to Individuals and Organizations
The damage inflicted by email worms can range from minor inconveniences to significant disruptions. Individuals might experience spam overload, compromised personal information, or system crashes. Small businesses can face disruptions in operations, lost productivity, and financial losses due to downtime. Large corporations can experience significant financial losses, reputational damage, and legal repercussions due to data breaches and regulatory penalties.
The impact is directly related to the nature of the worm’s payload, the number of systems affected, and the severity of the breach.
Impact on Various Targets
| Target | Potential Impact | Data Breached | Recovery Time |
|---|---|---|---|
| Individuals | Spam overload, compromised personal information, system crashes, identity theft | Emails, contacts, personal files, financial information | Days to weeks, depending on the extent of the damage |
| Small Businesses | Disruptions in operations, lost productivity, financial losses due to downtime, potential loss of customer trust | Customer data, financial records, internal documents | Weeks to months, depending on the complexity of the business |
| Large Corporations | Significant financial losses, reputational damage, legal repercussions, regulatory penalties, potential loss of critical data, disruption of supply chains | Confidential data, intellectual property, financial data, customer information, employee records | Months to years, depending on the scope of the breach and the corporation’s resources |
Prevention and Mitigation
Email worms, with their ability to spread rapidly and disrupt systems, demand proactive measures for prevention and mitigation. Effective strategies involve user education, robust organizational security policies, and swift incident response protocols. A layered approach combining these elements is crucial for minimizing the impact of such threats.
The mimail email worm is spreading like wildfire, and that’s incredibly concerning. Recent reports suggest a potential link to the latest Windows flaws, which foretell a new wave of worm threats. This article highlights the vulnerabilities and how they could be exploited. Clearly, the rapid spread of the mimail worm underscores the importance of staying vigilant and implementing robust security measures.
Recognizing Suspicious Email Messages
Users are the first line of defense against email worm infections. Developing the ability to identify suspicious emails is paramount. Look for messages with poor grammar, unusual sender addresses, or requests for sensitive information. Phishing attempts often masquerade as legitimate communications, using familiar brands or urgent tones. Hovering over links before clicking can reveal the true destination, and scrutinizing attachments is essential.
Always verify the sender and the content before opening any attachments or clicking on links, especially those related to financial transactions or personal information.
The MiMail email worm is spreading like wildfire, clogging inboxes faster than you can say “system overload.” Thankfully, companies like Transmeta are working on innovative solutions. For instance, Transmeta readies a new astro chip here to potentially bolster security measures, which could be crucial in mitigating the worm’s rapid spread. This rapid worm infection highlights the importance of proactive security measures.
Organizational Strategies for Prevention
Implementing robust security measures at an organizational level is crucial. Email gateways should be configured with filters that scan for known malicious patterns and block potentially harmful attachments. Security awareness training for employees is essential to educate them on identifying phishing attempts and suspicious emails. Regular software updates, including operating systems and antivirus software, patch known vulnerabilities, thereby reducing the attack surface.
The MiMail email worm was spreading like wildfire, clogging inboxes across the globe. Meanwhile, tech giants like SGI were pushing the boundaries of computing with innovations like their quad processor workstation , highlighting the ever-increasing need for robust defenses against such digital threats. This rapid spread of the MiMail worm was a stark reminder of the vulnerability of our digital infrastructure.
Implementing a multi-layered approach with various security measures, such as intrusion detection systems, strengthens the overall security posture.
Isolating Infected Systems Quickly
Swift isolation of infected systems is critical to prevent further spread. Immediately disconnect infected systems from the network, and quarantine them to prevent further transmission. This should be a coordinated effort involving IT staff and potentially security professionals. Once the infected system is isolated, a thorough investigation is necessary to determine the extent of the damage and implement appropriate remediation steps.
Logging and monitoring network traffic can provide valuable insights into the infection source and the affected systems. Properly documenting the incident response procedures is vital for future reference and improvement.
Common Security Measures
| Security Measure | Description | Implementation | Effectiveness |
|---|---|---|---|
| Email Filtering | Filtering emails based on predefined criteria (e.g., sender, s, attachments) to block potentially malicious messages. | Configure email gateways with anti-spam and anti-virus filters. Regularly update filters to detect new threats. | High, if properly configured and updated. |
| Security Awareness Training | Educating users on recognizing phishing attempts, identifying suspicious emails, and handling potentially harmful attachments. | Conduct regular training sessions, provide readily accessible resources, and encourage feedback. | Moderate to High, depending on the level of engagement and reinforcement. |
| Regular Software Updates | Keeping operating systems, applications, and security software up-to-date to address known vulnerabilities. | Implement automated update systems and ensure timely patching. | High, as updates often include critical security fixes. |
| Intrusion Detection Systems (IDS) | Monitoring network traffic for malicious activity and alerting administrators of potential threats. | Deploy IDS systems strategically to monitor network traffic and log suspicious events. | High, when configured and monitored properly. |
| Network Segmentation | Dividing the network into smaller, isolated segments to limit the impact of a security breach. | Establish firewalls and access controls to restrict communication between segments. | High, if implemented correctly. |
Examples and Case Studies
Email worms have consistently posed a significant threat to computer systems, causing widespread disruptions and financial losses. Understanding past outbreaks provides crucial insights into the mechanisms of these malicious programs and helps in developing effective prevention strategies. Analyzing successful attacks, and how they were executed, is key to staying ahead of future threats.
Notable Email Worm Outbreaks
Email worms exploit vulnerabilities in email clients and server software, leveraging the inherent trust associated with email communication to spread rapidly. They often utilize social engineering tactics, disguising themselves as legitimate messages to trick users into opening attachments or clicking on malicious links. This reliance on human interaction makes email worms particularly effective in bypassing traditional security measures.
Specific Vulnerabilities Exploited
Many email worms target vulnerabilities in Microsoft Outlook and other email clients. These vulnerabilities often involve buffer overflows, which allow the worm to overwrite memory and execute malicious code. Another common method involves exploiting flaws in email server software, allowing the worm to propagate to other systems without user intervention. Security researchers have also observed email worms exploiting vulnerabilities in the transport layer protocols used for email delivery, such as SMTP.
Case Study Table, Mimail e mail worm spreads quickly
| Worm Name | Date of Outbreak | Number of Systems Affected | Financial Loss (USD) |
|---|---|---|---|
| MyDoom | 2004 | Estimated 2.5 Million | Billions (estimated) |
| Sobig | 2003 | Estimated 50 Million | Billions (estimated) |
| Blaster | 2003 | Estimated 500,000 | Hundreds of millions (estimated) |
| Nimda | 2001 | Estimated 1 Million | Billions (estimated) |
Dissemination Methods
Email worms spread by attaching themselves to legitimate emails, often masquerading as important messages or updates. They can also exploit vulnerabilities in email server software, allowing the worm to propagate automatically to other systems. In some cases, worms can also use spoofing techniques to send emails that appear to originate from trusted sources.
Impact of Email Worms
The impact of email worms can be significant, causing disruptions to businesses and individuals alike. These disruptions range from decreased productivity due to system outages to substantial financial losses stemming from downtime, data loss, and remediation costs. The sheer volume of affected systems and the rapid spread of these worms highlight the urgent need for robust security measures.
Technical Analysis of Propagation: Mimail E Mail Worm Spreads Quickly
Email worms, those insidious digital parasites, exploit vulnerabilities in email clients and server infrastructure to spread rapidly. Understanding their technical methods is crucial to developing effective countermeasures. This analysis delves into the mechanics of how these worms achieve their swift dissemination, highlighting their tactics and the vulnerabilities they exploit.The swift propagation of email worms relies heavily on automated processes and the inherent structure of email systems.
They leverage the very mechanisms designed for efficient communication to their own nefarious ends, making detection and containment challenging. The worm’s code is intricately designed to exploit weaknesses in email protocols, making it crucial to understand the specific techniques employed.
Email Client Exploitation
Email clients, often perceived as user-facing applications, are integral to the worm’s propagation cycle. They provide a platform for the worm to execute malicious code, often by leveraging features like automatic email forwarding or message preview. This automated execution can lead to widespread infections if not properly secured. Malicious attachments, disguised as legitimate files, can trigger the worm’s execution sequence upon opening, highlighting the importance of cautious file handling.
Server Infrastructure Exploitation
Email servers, the backbone of communication, are frequently targets for worm infiltration. The worm can exploit vulnerabilities in server software, enabling it to automatically send infected messages to numerous recipients. This automated process often leverages the server’s existing infrastructure for sending emails, making it difficult to isolate the source of the infection. Exploiting vulnerabilities in mail transfer agents (MTAs) allows the worm to bypass security measures, enabling rapid dissemination.
Bypassing Security Protocols
Worms employ various strategies to bypass security protocols, often relying on obfuscation techniques to evade detection. These tactics can include encrypting parts of the worm’s code, using polymorphic code to change its appearance, or employing techniques to evade signature-based detection systems. Furthermore, they often exploit weaknesses in the security protocols themselves, including email header manipulation or spoofing sender addresses to evade spam filters.
Comparison of Propagation Techniques
| Technique | Description | Effectiveness | Countermeasures |
|---|---|---|---|
| Attachment-based propagation | Infected emails are sent with malicious attachments. Opening the attachment triggers the worm’s execution. | High, if users are not cautious. | Educate users about phishing emails, implement file scanning and sandbox environments. |
| Embedded code propagation | Malicious code is embedded within the email body, triggering execution when the email is opened or viewed. | High, if users do not have up-to-date email clients. | Utilize email filters and anti-malware software that can detect malicious code. |
| Exploiting server vulnerabilities | Worm leverages weaknesses in email server software to automatically send infected messages to recipients. | Very high, as it leverages the server’s infrastructure. | Regularly update email server software, employ intrusion detection systems, and monitor server logs. |
| Spoofing and header manipulation | The worm disguises its origin and recipient list to evade spam filters and security protocols. | Medium to high, depending on the sophistication of the spoofing technique. | Employ advanced email filtering systems that can detect spoofing attempts, and regularly update spam filters. |
Social Engineering Tactics in Email Worms
Email worms, those insidious digital spreaders, often rely on social engineering tactics to exploit human vulnerabilities and proliferate. This involves manipulating individuals into performing actions that inadvertently contribute to the worm’s propagation, such as opening infected attachments or clicking malicious links. Understanding these tactics is crucial for preventing infection and protecting systems.
Common Social Engineering Tactics
Social engineering tactics used in email worms exploit various psychological principles. These techniques aim to create a sense of urgency, curiosity, or trust, prompting recipients to act without critical thinking. A successful tactic hinges on understanding the target audience’s motivations and fears.
Types of Lures and Bait
Email worms employ a variety of lures to entice recipients. These lures often take advantage of current events, popular figures, or urgent requests. Some examples include:
- Urgent Notifications: Emails mimicking urgent notifications about package deliveries, account issues, or security breaches create a sense of immediate action. The fear of missing out (FOMO) and the desire to resolve the issue quickly can be exploited.
- Phishing for Credentials: These emails attempt to trick users into revealing sensitive information like usernames and passwords. They may impersonate legitimate companies or institutions, creating a sense of trust.
- Financial Incentives: Emails promising large sums of money, lottery winnings, or other financial gains are designed to capitalize on the desire for quick wealth.
- Job Opportunities or Promotions: Emails offering employment opportunities or career advancements can manipulate individuals seeking better prospects. These are designed to trick the user into acting without critical thinking, or providing sensitive data.
- Gossip or Scares: Emails spreading rumors or circulating frightening news stories can create a sense of anxiety and urgency, prompting recipients to forward the email to others. The desire to share information, particularly when concerning a popular figure or important issue, can be leveraged.
Comparative Analysis of Social Engineering Techniques
The table below illustrates various social engineering techniques used in email worms, their descriptions, the target audiences they are aimed at, and their effectiveness. Effectiveness is assessed based on past observed cases and the inherent vulnerabilities they exploit.
| Technique | Description | Target Audience | Effectiveness |
|---|---|---|---|
| Urgent Notifications | Emails mimicking urgent notifications about critical events, like account issues or package delivery. | Individuals who prioritize timely responses to urgent situations. | Medium to High. Creates a sense of urgency and prompts immediate action without critical thinking. |
| Phishing | Emails attempting to trick users into revealing sensitive information like usernames and passwords by impersonating legitimate entities. | Users with weak security awareness and a lack of vigilance. | Medium to High. Leverages trust and exploits the ease of clicking links. |
| Financial Incentives | Emails promising large sums of money, lottery winnings, or other financial gains. | Individuals seeking quick financial gains and those with poor financial literacy. | Low to Medium. Often perceived as too good to be true, especially for high-value promises. |
| Job Opportunities | Emails offering employment opportunities or career advancements. | Job seekers and those actively looking for promotions. | Medium. Appeals to the desire for better prospects, but also requires verification. |
| Gossip or Scares | Emails spreading rumors or circulating frightening news stories to incite fear and urgency. | Individuals seeking information and those easily influenced by fear. | Low to Medium. Effectiveness depends on the believability of the story and the recipients’ trust in the source. |
Illustrative Examples
Email worms, notorious for their rapid proliferation, can wreak havoc on computer networks and systems. Understanding how these malicious programs spread is crucial for prevention and mitigation. This section presents a hypothetical scenario to illustrate the typical infection process and the steps an email worm takes.
Hypothetical Email Worm Scenario
Imagine a newly developed email worm, dubbed “MailStorm,” designed to exploit a vulnerability in popular email clients. MailStorm’s primary objective is to replicate itself and spread across networks, causing significant disruption. The worm accomplishes this through an intricate process of infection and propagation.
Infection Process: Step-by-Step
The MailStorm worm operates in a methodical fashion, infecting systems in a precise sequence. Here’s a detailed look at the steps involved:
- The initial infection occurs when a user opens a malicious email attachment or clicks on a malicious link. The attachment or link contains a specially crafted script that triggers the worm’s activation.
- Upon activation, the worm immediately scans the victim’s system for vulnerable email clients or protocols. The worm identifies the specific targets it can exploit for replication.
- The worm then creates a copy of itself and embeds it into the victim’s email client’s configuration files. This ensures the worm is executed every time the client is used.
- The worm automatically gathers the victim’s email address book and other relevant data. This data is crucial for the worm’s next phase: propagation.
- MailStorm sends identical copies of the malicious email to all contacts in the victim’s address book. Each email contains the malicious attachment or link.
- The recipient opens the malicious attachment or clicks the link. The cycle begins anew, infecting the recipient’s machine, repeating the process of replication, propagation, and infection.
- The worm continues to spread exponentially, infecting more and more machines across the network until it reaches its intended target or the infection is stopped.
Propagation Flow Chart
The following diagram illustrates the propagation process of the MailStorm worm, highlighting the key stages of infection. This visual representation helps in understanding the cyclical nature of the worm’s spread.“`+—————–+ +—————–+ +—————–+| User Receives | –> | Worm Activated | –> | Worm Replicates||Malicious Email | | and Infects | |and Propagates |+—————–+ +—————–+ +—————–+ | | V V+—————–+ +—————–+ +—————–+| Infected Email | –> | Email Sent to | –> | Recipient Opens|| Sent to List | | Contacts List | |Malicious Email |+—————–+ +—————–+ +—————–+ | | V V Repeat Repeat“`
Last Point
In conclusion, the rapid spread of mimail e mail worms underscores the ever-evolving threat landscape in cybersecurity. Protecting ourselves and our organizations requires a multifaceted approach, combining technical safeguards with user awareness and vigilance. By understanding the tactics employed by these worms, we can better equip ourselves to combat them and safeguard our digital assets.