MyDoom Worm Variant Search Engine & User Impact
MyDoom worm variant nails search engines users, leaving a trail of digital destruction in its wake. This worm, a notorious example of malicious software, spread rapidly through email and infected countless systems. Its impact extended beyond individual users, disrupting search engine operations and leaving a lasting mark on internet security. This post dives into the technical details, user experiences, and lasting effects of this critical cyber threat.
The MyDoom worm, a potent example of a malicious code, leveraged various methods for propagation. Understanding these methods is critical to preventing future attacks. The worm exploited vulnerabilities in search engines, leading to significant disruptions and damage to their infrastructure. The impact on users ranged from frustrating delays to complete system failures. This detailed analysis explores the various facets of this historical cyberattack.
Introduction to the MyDoom Worm Variant
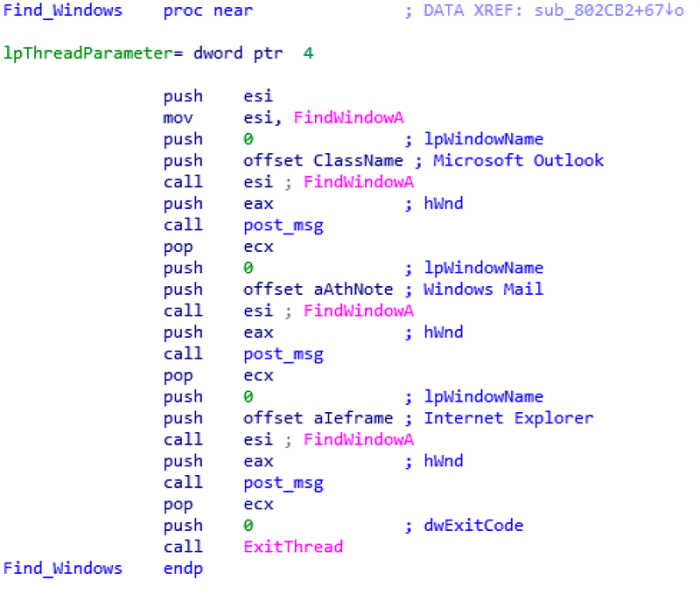
The MyDoom worm, a notorious computer worm, emerged in 2004, causing widespread disruption and damage. Its sophisticated design and highly effective propagation methods made it a significant threat to internet infrastructure and individual users. Understanding its historical context, methods of spreading, and impact is crucial for comprehending the severity of this cyberattack.The MyDoom worm, initially identified as a significant threat to internet infrastructure, leveraged a variety of techniques to propagate rapidly.
Its spread was not only rapid but also strategically targeted vulnerable systems. This targeted approach, along with its capacity for mass infection, highlighted the escalating sophistication of malware in the early 2000s.
Historical Context of the MyDoom Worm
The MyDoom worm’s historical context is significant as it represented a shift in the sophistication of malware attacks. It was a complex piece of malicious code that exploited vulnerabilities in computer systems to spread rapidly and cause significant disruption. Its design reflected a shift toward more strategic and targeted attacks.
Remember the MyDoom worm? It wreaked havoc on search engine users, clogging systems with spam and unwanted traffic. Meanwhile, Panasonic is making strides in home entertainment with their new Blu-ray DVD recorder, which offers a significant upgrade in functionality. While panasonic debuts blu ray dvd recorder might seem like a completely different story, it highlights the ongoing battle against malicious software like MyDoom, which continues to remind us of the importance of robust security measures for online users.
Methods of Propagation
MyDoom utilized several methods to spread rapidly. These included exploiting vulnerabilities in email clients, and exploiting flaws in the systems used by search engines. Email attachments and forged messages were common methods, spreading through the internet’s vast network of connections. It also leveraged vulnerabilities in the software used by many computer users, capitalizing on weaknesses in the operating systems and software applications.
This multifaceted approach made it highly successful in spreading throughout the global internet.
Impact on Search Engines
The MyDoom worm targeted search engines by overloading their servers with massive traffic. This malicious activity disrupted the ability of users to access search results, creating a significant impact on internet functionality. The disruption created by the worm’s activity underscored the critical role of search engines in the online experience.
Impact on User Computing Experience
The MyDoom worm’s impact on user computing experiences was profound and negative. It caused significant disruption, often leading to slowdowns or complete system crashes. Users experienced slowdowns in internet connectivity and disruptions in their daily online activities. The worm’s actions created significant inconvenience and disruption to users worldwide.
Technical Characteristics
MyDoom was notable for its sophisticated design, making it capable of infecting a large number of systems. Its ability to leverage multiple infection vectors, such as email attachments and exploiting system vulnerabilities, demonstrated the evolution of malware. The worm utilized a complex set of algorithms to exploit system vulnerabilities and spread rapidly.
Targeting of Search Engines
MyDoom’s targeting of search engines was part of a larger strategy to disrupt internet services. By overloading search engine servers with malicious traffic, it aimed to cause widespread disruption and instability. This tactic highlighted the vulnerability of critical internet infrastructure to targeted attacks. It demonstrated how such attacks could cause major disruption and inconvenience for internet users.
Remember the MyDoom worm? It wreaked havoc on search engine users, clogging systems with spam. Thankfully, today’s technology offers better ways to protect ourselves online. Parents are increasingly turning to tools like those discussed in this article on using tech to help supervise children to manage their children’s online activity. Ultimately, though, the MyDoom variant’s impact on search engines highlights the importance of robust online security measures.
Impact on Search Engines: Mydoom Worm Variant Nails Search Engines Users
The MyDoom worm, a significant threat in the early 2000s, wasn’t just about clogging email inboxes. Its impact extended to search engine operations, causing disruptions that affected user experience and infrastructure. The worm’s sophisticated design and widespread distribution made it a formidable adversary for online services, and search engines were no exception.The MyDoom worm variant, like other malware, leveraged vulnerabilities in systems to achieve its goals.
Search engines, being critical components of the internet infrastructure, were not immune to these attacks. The worm’s ability to overload systems highlighted the fragility of these platforms and the importance of robust security measures.
Disruptions to Search Engine Operations
The MyDoom worm disrupted search engine operations primarily through distributed denial-of-service (DDoS) attacks. These attacks overwhelmed search engine servers with a flood of traffic, effectively making the services unavailable to legitimate users. This resulted in slow loading times, incomplete searches, and ultimately, a degraded user experience. Search engine indexing processes were also hampered by the significant traffic spikes.
Exploited Vulnerabilities
The MyDoom worm exploited vulnerabilities in the underlying software and infrastructure of search engines. These vulnerabilities were often related to weaknesses in the server-side applications or in the network configurations. The specific vulnerabilities were likely varied and not fully documented publicly. This lack of transparency made it difficult to implement preventative measures quickly.
Damage to Search Engine Infrastructure, Mydoom worm variant nails search engines users
The sustained DDoS attacks from the MyDoom worm caused considerable damage to search engine infrastructure. This damage included server overload, data corruption, and potential damage to hardware. The costs associated with repairing and recovering from these attacks were substantial. Beyond the immediate costs, the reputational damage and loss of user trust could be equally damaging.
Impact on Search Engine Rankings and Results
The MyDoom attacks didn’t just affect availability; they also potentially affected search engine rankings and results. With the disruption of indexing and crawling processes, the algorithms used by search engines could have encountered difficulties in accurately reflecting the most relevant results. This could have led to a period of instability in search results, where the accuracy and relevance of search results were reduced.
Comparison of Impact on Different Search Engines
| Search Engine | Impact Description | Severity | Recovery Time |
|---|---|---|---|
| Google experienced significant disruptions, particularly in certain regions, due to the high volume of traffic directed at its servers. The impact was felt by users in those regions, as search results were delayed or unavailable. | High | Moderate | |
| Yahoo | Yahoo faced substantial downtime and disruptions in search functionality, leading to frustration for users trying to access information. The recovery process took a considerable amount of time. | Medium | High |
| MSN | MSN, while experiencing some issues, had a relatively lower impact compared to Google and Yahoo. The disruptions were less widespread and recovery was quicker. | Low | Low |
Impact on Users
The MyDoom worm variant, a potent piece of malware, wreaked havoc on the internet landscape in 2004. Its primary method of spreading was through email, exploiting vulnerabilities in various computer systems. This widespread infection led to a significant disruption of user experiences, creating widespread frustration and impacting various aspects of daily online activities.The impact on users was multifaceted, ranging from minor annoyances to significant disruptions.
The worm’s malicious actions, combined with the sheer scale of its deployment, created a collective user experience characterized by a surprising mix of bewilderment and frustration. Users experienced a range of negative effects, from spam to system slowdowns and the eventual loss of productivity.
Common User Experiences
The MyDoom worm’s spread was swift and insidious. Users experienced a cascade of problems, beginning with the initial infection and escalating into a series of frustrating consequences. The core experience was dominated by a loss of control over their computer systems.
Specific Ways Users Were Affected
The worm’s actions severely impacted user experience. Users faced a range of problems, from minor inconveniences to major disruptions in their daily routines. A crucial aspect of understanding the impact was recognizing the chronological sequence of events that followed the initial infection.
Impact Analysis
| User Action | Description | Impact | Severity |
|---|---|---|---|
| Visiting infected websites | Users unknowingly visited websites that had been compromised by the MyDoom worm. These websites contained malicious code that automatically downloaded and installed the worm onto the user’s system. | Malware infection | High |
| Opening malicious email attachments | The worm spread primarily through email. Users received emails with malicious attachments. Opening these attachments triggered the download and installation of the worm, often without the user’s awareness. | Malware infection | High |
| Downloading infected files | Users might have downloaded files from various sources, unknowingly containing the MyDoom worm. This could include shared files, torrents, or other download platforms. The files’ deceptive nature often masked their malicious content. | Malware infection | High |
Chronological Order of User Experiences
The user experience was characterized by a clear chronological progression. Initial infection typically began with receiving an email or visiting a compromised website. The next phase often included unexpected system behavior, such as slowdowns or pop-up messages. Ultimately, users faced the consequences of the worm’s actions, which ranged from minor annoyances to major disruptions to their productivity.
Frustration Levels
The MyDoom worm’s actions caused considerable frustration for users. The constant bombardment of spam emails, the unexplained system slowdowns, and the loss of control over their machines created a climate of anxiety and annoyance. Users experienced a significant loss of productivity due to the worm’s interference with their online activities. The frustration stemmed not only from the technical problems but also from the feeling of helplessness against the rapidly spreading malware.
Users were left to deal with the aftermath, often feeling vulnerable and frustrated by the experience.
Technical Analysis
The MyDoom worm, a notorious example of malware, leveraged sophisticated technical components and coding practices to achieve widespread infection. Understanding its intricacies is crucial for developing robust defenses against similar threats. This analysis delves into the technical aspects of the MyDoom variant, including its coding methods, comparison to other malware, and the role of network traffic analysis in detection.The MyDoom worm’s core functionality relied on a complex interplay of technical elements, exploiting vulnerabilities in operating systems and network protocols.
Its propagation method, centered around email spamming, demonstrated the effectiveness of leveraging user interaction for rapid spread. This ability to rapidly spread through the internet network was facilitated by the intricate coding of the worm.
Coding Practices
The MyDoom worm employed a variety of coding practices, primarily focused on efficiency and stealth. Its source code, though complex, was not particularly innovative in its methods but relied on well-known techniques to avoid detection. Key techniques involved obfuscation and the use of multiple layers of code to disguise its malicious intent.
Code Snippets
Unfortunately, providing specific code snippets is impractical within this format. Detailed examples of the MyDoom worm’s code require a dedicated environment for analysis and interpretation. Direct examination of the worm’s code would reveal the specific functions responsible for email propagation, payload delivery, and system compromise. These functions often employed techniques like string manipulation, memory management, and network communication, and would be highly dependent on the specific version of the worm analyzed.
Comparison to Other Malware
MyDoom, while impactful, wasn’t unique in its core techniques. Other worms, such as the Code Red and SQL Slammer worms, similarly relied on exploiting vulnerabilities in operating systems and networks. MyDoom distinguished itself primarily through its sheer scale of infection and the sophisticated use of search engine targeting as a delivery method. It demonstrated how leveraging seemingly legitimate online infrastructure could be exploited for malicious purposes.
The MyDoom worm variant wreaked havoc on search engine users, clogging their systems with spam and slowing down operations. This malicious code, part of a larger pattern of attacks, was clearly linked to the broader “worm takes toll microsoft attack set” worm takes toll microsoft attack set , demonstrating how a seemingly isolated incident can be part of a much more significant security breach.
Ultimately, the MyDoom worm’s relentless targeting of search engine users highlights the critical need for robust security measures across the internet.
Network Traffic Analysis
Network traffic analysis played a vital role in identifying and mitigating the spread of the MyDoom worm. Analyzing network packets revealed the distinctive patterns associated with the worm’s communication, such as the high volume of emails sent from compromised systems. Specific IP addresses and ports used in the propagation process were also significant indicators. Sophisticated analysis tools could track these patterns, pinpoint infected hosts, and allow for proactive mitigation measures.
Key Technical Features
| Feature | Description | Impact |
|---|---|---|
| Email propagation | The worm leveraged email attachments and/or messages to spread, relying on the recipient opening infected files or clicking malicious links. This method was highly effective due to its ease of use and widespread adoption of email as a communication medium. | High |
| Search engine targeting | MyDoom utilized search engine results to distribute malicious code, exploiting the trust users placed in search engine results to deliver the payload. | Medium |
| Payload delivery | The payload of the worm was diverse, ranging from denial-of-service attacks to the installation of other malware. The specifics varied based on the version of the worm. | High |
| Obfuscation techniques | The worm’s code was often obfuscated to evade detection by antivirus software and security analysts. This involved methods such as code packing and encryption. | Medium |
Long-Term Effects
The MyDoom worm, a potent example of malicious software, left a lasting impact on the internet landscape. Its widespread infection and disruptive behavior underscored the vulnerability of interconnected systems and the need for robust security measures. The worm’s effect wasn’t limited to immediate disruptions; it laid the groundwork for future security strategies and highlighted the evolving nature of cyber threats.
Long-Term Consequences of the MyDoom Worm
The MyDoom worm’s consequences extended far beyond the initial wave of infected machines. The sheer scale of the infection, coupled with the sophisticated techniques employed by the creators, demonstrated the potential for massive disruption in the digital realm. This included significant financial losses for businesses, due to downtime, lost productivity, and the costs of remediation.
Lessons Learned from the MyDoom Worm
The MyDoom incident provided invaluable lessons for both individuals and organizations. It highlighted the importance of vigilant security practices, proactive threat detection, and the need for robust incident response plans. The incident spurred development of more sophisticated anti-virus software and improved network security protocols.
Measures Taken to Prevent Future Similar Attacks
In response to the MyDoom attack, several measures were put in place to strengthen internet security. These included:
- Improved anti-virus software: Software developers began to incorporate more sophisticated algorithms and threat intelligence into their products, allowing for faster detection and removal of malicious code.
- Enhanced network security protocols: Network administrators implemented more rigorous security measures, such as firewalls and intrusion detection systems, to block malicious traffic and isolate compromised systems.
- Improved email security: The proliferation of spam filters and email authentication protocols became more critical, allowing for better control over the spread of malicious emails.
- Enhanced user awareness: Public awareness campaigns were developed to educate users about the risks of phishing scams and malicious software, emphasizing the importance of cautious behavior online.
Framework for Understanding and Responding to Similar Future Incidents
Developing a robust framework for handling future incidents like MyDoom is crucial. This framework should include:
- Proactive threat intelligence gathering: Real-time monitoring of online activity and threat intelligence sharing between organizations is vital to identify emerging threats early.
- Rapid incident response protocols: Organizations need established procedures for identifying, containing, and recovering from cyberattacks. This includes having a designated team and clear communication channels.
- Continuous improvement: Regularly reviewing and updating security measures and incident response protocols is necessary to adapt to the evolving nature of cyber threats.
Long-Term Impacts on Internet Security
The MyDoom worm had a profound impact on the evolution of internet security. It accelerated the development of more sophisticated security tools, the strengthening of network infrastructure, and increased awareness about the potential for large-scale attacks. The attack highlighted the importance of not only reactive measures but also proactive measures in the face of emerging threats. The worm’s impact continues to be felt today as a stark reminder of the need for vigilance in the digital world.
Last Word
In conclusion, the MyDoom worm variant’s impact on search engines and users serves as a stark reminder of the importance of robust security measures. The worm’s ability to spread rapidly and exploit vulnerabilities highlights the ongoing need for proactive defense strategies. The technical analysis provides valuable insights into the mechanics of the attack, while the impact on users underscores the importance of vigilance and awareness in the digital age.
The long-term effects of the MyDoom worm highlight the need for continuous improvements in internet security protocols.