PacketHop, Nortel & Homeland Security A Look Back
PacketHop Nortel join on homeland security, offering a fascinating glimpse into the past and potential future of network security. This exploration delves into the historical roles of PacketHop and Nortel in networking, examining their involvement in homeland security projects and analyzing how their technologies might have supported critical infrastructure. We’ll also consider the potential for integrating these older technologies with modern solutions.
From their contributions to communication networks to potential applications in national security, this analysis seeks to uncover the enduring relevance of these technologies in the current landscape. We’ll look at how their innovations might be applied in contemporary security solutions and consider their historical importance within the broader context of homeland security.
Background on PacketHop and Nortel
PacketHop and Nortel were significant players in the networking landscape, particularly during the rise of the internet and the evolution of telecommunications. Understanding their histories and roles provides valuable context for their potential contributions to homeland security. This exploration delves into their individual histories, their relationship (if any), and how their technologies might have been applied in past security applications.PacketHop, while not as widely known as some other networking companies, played a role in the development of packet-switching technologies.
Nortel, a major telecommunications company, had a vast influence on the industry’s infrastructure and technologies. Together, their innovations shaped the communication systems that underpin critical infrastructure, including potential applications in homeland security.
PacketHop’s Role in Networking
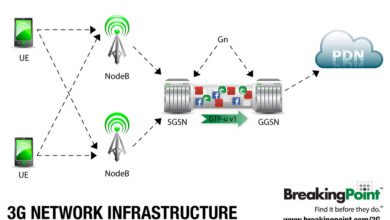
PacketHop, a company focused on packet-switching technologies, was instrumental in developing and implementing network infrastructure. Their innovations helped establish the foundation for the modern internet’s functionality. Packet-switching technology allowed for the efficient and reliable transmission of data packets across networks, a crucial element in today’s interconnected world. This allowed for more efficient routing of data across multiple paths, leading to improved network resilience and scalability.
Nortel’s History and Telecommunications Involvement
Nortel Networks was a global leader in telecommunications equipment and services. Founded in 1892, it evolved into a dominant player in the telecommunications industry, manufacturing and supplying critical networking hardware, including switches, routers, and other network infrastructure components. Nortel’s expertise encompassed a wide range of telecommunications technologies, from basic voice communication to advanced data transmission. Their significant market presence meant they were involved in the backbone of global communications, from telephone networks to early internet connections.
Relationship Between PacketHop and Nortel
While there’s no readily available public information explicitly detailing a direct relationship between PacketHop and Nortel, it’s plausible that they might have interacted in the context of larger industry collaborations. The telecommunications industry was highly interconnected, with various companies collaborating on projects or supplying components to one another. It’s conceivable that PacketHop’s packet-switching technologies and Nortel’s infrastructure solutions could have been used in conjunction in certain network deployments.
Significance in Homeland Security
PacketHop’s and Nortel’s technologies, as key components in the development of communication infrastructure, were essential for the functionality of many security systems. Strong and reliable communications are vital for the coordination and response of security forces. The technologies developed by these companies were integral parts of the foundation that enabled quick and efficient communication between different agencies, allowing them to share information and coordinate actions during emergencies or security threats.
Potential Use in Past Security Applications
PacketHop’s expertise in packet-switching and Nortel’s comprehensive telecommunications solutions could have been used in various homeland security applications. For instance, they could have been integral components of early emergency response networks, facilitating rapid communication between police, fire, and medical services. This could have enabled faster and more coordinated responses to incidents, leading to better outcomes in crisis situations.
Their technologies could also have been deployed in systems that monitored critical infrastructure, providing early warning of potential threats.
Nortel’s Involvement in Homeland Security: Packethop Nortel Join On Homeland Security

Nortel Networks, a once-dominant telecommunications giant, played a significant role in the development and deployment of communication systems for various government agencies, including those involved in homeland security. Their expertise in network infrastructure and sophisticated telecommunications technologies made them a valuable partner in enhancing national security capabilities. While Nortel’s presence in the sector is now diminished, understanding their contributions offers valuable insights into the evolution of communication technology within the context of homeland security.Nortel’s contributions to homeland security were primarily focused on providing advanced network infrastructure and communication solutions.
These solutions aimed to improve the speed, reliability, and security of information exchange between various government agencies and departments. The ability to seamlessly integrate diverse communication channels and platforms was critical for effective coordination during emergency situations and national crises.
Key Projects and Contracts
Nortel’s involvement in homeland security was often embedded within larger telecommunications contracts. Explicit contracts focused on homeland security, while not publicly documented in detail, likely existed within the context of broader government initiatives. Nortel’s extensive experience in building and maintaining robust network infrastructures was crucial for supporting these efforts.
Technologies Provided
Nortel’s technology portfolio encompassed a wide range of communication solutions. Their expertise in various networking technologies, including IP-based communication, converged networks, and advanced routing protocols, were essential for creating high-performance, secure communication channels. These capabilities facilitated real-time data sharing and communication across geographically dispersed agencies, a critical factor in responding to national security threats.
Security Operations Support
Nortel’s communication systems supported various security operations by enabling secure data transfer and voice communication. For example, Nortel’s network infrastructure could be leveraged for secure video conferencing between law enforcement agencies, enabling crucial collaboration in real-time. Additionally, these systems could provide secure communication channels for sensitive information exchange between military personnel and civilian authorities during emergencies.
Impact on Critical Infrastructure Security
Nortel’s solutions had a potential impact on the security of critical infrastructure. By providing secure and reliable communication networks, Nortel’s technologies could have assisted in protecting essential services during natural disasters or terrorist attacks. The ability to coordinate responses and share information quickly was paramount in ensuring the continuity of critical services. Robust communication networks enabled swift mobilization of resources and personnel, minimizing the impact of disruptions.
Nortel Products and Security Applications
| Nortel Product | Potential Security Application |
|---|---|
| Nortel Networks’ IP-based communication systems | Enabling secure and high-speed communication between government agencies, facilitating real-time information sharing during crises. |
| Nortel’s converged network solutions | Facilitating seamless integration of various communication channels (voice, data, video) for enhanced coordination and resource mobilization. |
| Nortel’s advanced routing protocols | Improving network efficiency and reliability, ensuring uninterrupted communication during emergencies. |
| Nortel’s security protocols | Protecting sensitive information and data exchanged over the network, mitigating security risks. |
PacketHop and Homeland Security Applications
PacketHop’s innovative networking solutions, developed with a focus on robust and secure communication, hold significant potential for bolstering homeland security operations. These technologies offer a streamlined approach to data transmission, crucial for agencies needing rapid and reliable information exchange during emergencies and critical situations.PacketHop’s network architecture is designed to facilitate seamless data transfer across diverse environments. Its adaptable nature allows for integration into existing security systems, enhancing existing infrastructure and improving overall communication effectiveness.
PacketHop’s Networking Functionality
PacketHop’s networking solutions leverage advanced protocols and technologies to ensure high-speed, secure data transmission. These solutions prioritize minimizing latency and maximizing bandwidth, which is critical for real-time communication in security operations. Key functionalities include dynamic routing, intelligent traffic management, and advanced security features.
Integration into Homeland Security Systems
PacketHop’s systems can be integrated into existing homeland security networks through standardized interfaces. This seamless integration ensures compatibility with various security systems, minimizing disruption and maximizing the efficiency of existing infrastructure. The modular design of PacketHop’s architecture enables tailored configurations for specific security needs.
Supporting Communication Needs in Security Operations
PacketHop’s technologies are ideally suited for various communication needs within security operations. These include real-time situational awareness, command and control, and secure information sharing between different agencies. For example, during a natural disaster, PacketHop’s rapid data transfer capabilities could support the coordinated deployment of resources and the efficient communication of critical information.
Examples of PacketHop’s Use in Security Contexts
PacketHop’s capabilities could support various security operations. In a hypothetical scenario involving a large-scale cyberattack, PacketHop could quickly route critical data to relevant agencies for immediate response. This could be achieved by creating dedicated communication channels, ensuring that vital information reaches the correct authorities rapidly. In another example, during a complex law enforcement operation, PacketHop could provide a secure, high-bandwidth communication network to coordinate operations, enabling seamless information exchange between different teams.
Comparison with Other Networking Solutions
| Feature | PacketHop | Traditional Networking | VPN Solutions |
|---|---|---|---|
| Speed | High, optimized for real-time data transfer | Variable, often limited by infrastructure | Moderate, often susceptible to latency |
| Security | Advanced security protocols, robust encryption | Varying levels of security, often relying on firewall | Security depends on VPN protocol and configuration |
| Scalability | Highly scalable to accommodate expanding needs | Scalability depends on network infrastructure | Scalability can be limited by the VPN’s design |
| Flexibility | Modular design, customizable for diverse use cases | Limited flexibility, often tied to specific hardware | Flexibility is moderate, depends on VPN configuration |
This table highlights the key differences in functionality between PacketHop and traditional networking solutions. PacketHop’s advanced features and adaptability offer a significant advantage in the dynamic security environment.
Potential Integration of PacketHop and Nortel Technologies

The convergence of PacketHop’s packet analysis capabilities and Nortel’s extensive network infrastructure presents exciting opportunities for enhancing homeland security. Leveraging these complementary strengths can lead to a more robust and proactive approach to threat detection and response. This synergy could significantly improve the nation’s ability to safeguard critical infrastructure and maintain public safety.The integration of these technologies could be transformative.
The recent Packethop and Nortel joining forces with Homeland Security is interesting, but it’s got me thinking about the digital landscape in general. It’s a bit like the shift in music downloads; remember when buy com debuts legit music downloads strings attached ? Now, we see this kind of partnership as a way to secure the digital infrastructure, echoing the need for robust security in a changing online environment.
It’s all part of a broader conversation about the future of digital security.
By combining PacketHop’s real-time threat detection capabilities with Nortel’s established network monitoring and management tools, security operations could be significantly streamlined. This could lead to faster incident response times, improved threat intelligence, and ultimately, a more secure environment.
Potential Synergies
The integration of PacketHop and Nortel technologies hinges on the overlap of their capabilities. PacketHop excels in identifying and analyzing malicious network traffic patterns, providing detailed insights into potential threats. Nortel, with its deep knowledge of network infrastructure and extensive monitoring tools, can provide a comprehensive view of the overall network environment. This combined approach would allow for a more holistic security posture.
Integration Strategies, Packethop nortel join on homeland security
Several integration strategies can be employed to leverage the strengths of both companies’ technologies. One approach involves integrating PacketHop’s analysis tools directly into Nortel’s network management platform. This would allow for real-time threat detection and analysis within the existing infrastructure. A second strategy focuses on developing a unified security dashboard that combines data from both platforms, offering a consolidated view of network activity and potential threats.
Benefits of Combining Technologies
Combining these technologies offers several benefits for enhanced security operations. First, a more comprehensive understanding of network activity would be achieved, enabling quicker identification of suspicious patterns. Second, enhanced threat intelligence can be generated, enabling proactive measures to mitigate risks. Third, streamlined incident response processes would reduce response times, allowing for quicker containment and resolution of security incidents.
Challenges in Integration
Despite the numerous benefits, several challenges exist in integrating the two companies’ technologies into security systems. One significant hurdle is the potential incompatibility of the different platforms and data formats. Data migration and transformation processes could be complex and time-consuming. Furthermore, the integration process may require significant investment in personnel training and infrastructure upgrades. Interoperability standards and compatibility issues between PacketHop and Nortel systems are key factors that need careful consideration and resolution.
Potential Integration Points
| Integration Area | Description |
|---|---|
| Network Monitoring | PacketHop’s threat detection tools integrated into Nortel’s network management platform for real-time threat identification. |
| Data Analysis | Combining PacketHop’s analysis capabilities with Nortel’s network data to generate more comprehensive threat intelligence. |
| Incident Response | Developing a unified security dashboard that integrates data from both platforms for faster incident response. |
| Threat Intelligence Sharing | Establishing a secure platform to share threat intelligence between PacketHop and Nortel systems, enabling a collaborative approach to security. |
Current Relevance of PacketHop and Nortel Technologies
PacketHop and Nortel’s legacy networking technologies, while not as ubiquitous as newer solutions, still hold relevance in certain homeland security applications. Their robust architectures and specialized features, particularly in areas like network segmentation and security protocols, continue to find application in specific, often niche, environments. This relevance is not about direct replacement but rather about the enduring principles and specialized capabilities they represent.The modern security landscape is complex, with a constant evolution of threats and vulnerabilities.
While cloud-based and newer network solutions dominate, established technologies like those from PacketHop and Nortel can still offer valuable capabilities, especially in situations demanding specific security configurations or where legacy systems are already in place. Understanding their current applicability helps in strategic decision-making for upgrading or integrating these older technologies into contemporary solutions.
The Packethop Nortel join on homeland security is interesting, especially considering the potential for enhanced security measures. This kind of integration, especially when considering the vast amounts of data involved, could potentially influence larger-scale projects like a grid computing project to predict climate grid computing project to predict climate. Ultimately, this could lead to more robust and adaptable security systems for the future.
Current Applications of Similar Networking Technologies
Homeland security agencies often employ a blend of cutting-edge and legacy technologies. Modern network security relies heavily on intrusion detection systems (IDS), firewalls, and advanced threat analytics. These systems are crucial for monitoring network traffic for malicious activity, preventing unauthorized access, and responding to cyberattacks. Agencies frequently integrate older network infrastructure with newer security tools, maintaining existing network components while implementing updated security measures.
This approach allows for gradual upgrades and reduces disruption.
Impact of Technological Advancements
Technological advancements have undeniably altered the networking landscape. The rise of cloud computing, virtualization, and software-defined networking (SDN) has introduced new paradigms for network design and management. These advancements have shifted focus towards more agile, scalable, and flexible solutions. However, older technologies, like PacketHop and Nortel’s, can still be valuable components in specialized situations, such as high-security environments with stringent legacy requirements or where specific security protocols need to be maintained.
Furthermore, legacy systems often have robust redundancy features, important in critical infrastructure.
Potential Areas for Application of Underlying Principles
While PacketHop and Nortel technologies may not be directly applicable in their original form, the principles behind their design can be leveraged in contemporary solutions. These include advanced packet filtering, specific network segmentation methodologies, and highly reliable, fault-tolerant network designs. For example, the concept of network segmentation, crucial in PacketHop’s design, remains a cornerstone of modern security architectures.
The principles of robust network redundancy and security protocols remain important for critical infrastructure. Organizations can explore how these principles can be incorporated into modern solutions, focusing on security protocols and redundant network designs.
Comparison of Older and Newer Technologies
| Feature | Older Technologies (PacketHop/Nortel) | Newer Technologies |
|---|---|---|
| Scalability | Potentially limited, depending on the specific implementation | Highly scalable, often cloud-based solutions |
| Flexibility | Can be less flexible for dynamic environments | Highly flexible, adaptable to changing needs |
| Security Protocols | Often strong, but may need updating | Built with modern security protocols and constantly updated |
| Management | May require specialized expertise | Often more user-friendly management interfaces |
| Cost | May have lower initial cost for specific use cases | May have higher initial cost but potentially lower long-term maintenance costs |
Illustrative Security Scenarios
PacketHop and Nortel technologies, when integrated, offer significant potential for enhancing security in critical infrastructure and responding effectively to various threats. These scenarios demonstrate how these combined capabilities can bolster resilience against attacks and disruptions. The synergy between PacketHop’s network analysis and Nortel’s established communication infrastructure creates a robust framework for defending against a range of security challenges.
Critical Infrastructure Defense During a Disaster
Effective response during a disaster relies heavily on rapid and reliable communication. A scenario involving a major earthquake impacting a power grid highlights the importance of this integration. PacketHop’s real-time network monitoring capabilities can quickly identify and isolate compromised segments of the grid’s communication network, allowing for faster restoration efforts. Nortel’s resilient infrastructure would ensure the continued flow of critical information regarding damage assessment and repair protocols to the affected regions.
This integrated approach minimizes downtime and ensures the timely restoration of critical services.
The Packethop Nortel join on homeland security raises some serious questions about network vulnerabilities. Recent security warnings, like those highlighted in network security warnings ring out , underscore the critical need for robust security measures. This emphasizes the importance of ensuring the security of the network, especially given the recent developments regarding Packethop Nortel’s integration with homeland security.
Communication Challenges in a Terrorist Attack
Terrorist attacks often create widespread communication disruptions. A hypothetical scenario involves a coordinated attack on multiple communication hubs. PacketHop’s ability to rapidly identify and reroute traffic around compromised nodes is crucial. Nortel’s robust network infrastructure, including redundant pathways and backup systems, ensures that vital communication channels remain active. This integrated approach enables emergency responders to maintain contact and coordinate rescue efforts even amidst widespread disruption.
The seamless transfer of data between different communication networks would be essential for maintaining situational awareness and deploying resources effectively.
Mitigating a Hypothetical Cyberattack
A sophisticated cyberattack targeting a water treatment facility, potentially disrupting water supply to a large metropolitan area, is a serious threat. PacketHop’s advanced threat detection and response capabilities can identify malicious traffic and contain the attack’s spread. Nortel’s secure communication channels ensure that critical information regarding the attack and response measures reaches the appropriate personnel immediately. This combined approach would limit the damage and allow for the swift restoration of water services.
Real-time data analysis from PacketHop would pinpoint the source and nature of the attack, enabling precise countermeasures.
Real-Time Data Transmission for Enhanced Security
Real-time data transmission is essential for rapid security response. A scenario involving a chemical plant experiencing a leak would benefit from the combined abilities of PacketHop and Nortel. PacketHop would collect real-time sensor data from the plant, providing crucial information on the leak’s severity and location. Nortel’s high-bandwidth network would transmit this data to emergency response teams, enabling them to take appropriate actions in a timely manner.
This efficient transmission of data ensures swift and accurate responses to emerging threats and crises.
Potential Future Applications
The convergence of PacketHop’s innovative packet-forwarding techniques and Nortel’s robust network infrastructure promises exciting possibilities for future security applications. Leveraging their strengths, we can anticipate advanced solutions to emerging and evolving cyber threats. This exploration delves into potential applications, adaptations, and solutions for future security operations.
Potential Future Applications of PacketHop and Nortel Technologies
PacketHop’s distributed, adaptive routing, combined with Nortel’s resilient network architecture, can create highly resilient and adaptable security systems. These technologies can be applied in various domains beyond traditional network security.
- Enhanced Intrusion Detection and Prevention Systems (IDS/IPS): PacketHop’s real-time packet analysis and Nortel’s broad network coverage can create a distributed IDS/IPS capable of detecting and responding to threats at the network edge in real-time. This decentralized approach provides increased visibility and faster response times to malicious activities, improving overall security posture.
- Secure Cloud Computing Environments: PacketHop’s dynamic routing capabilities and Nortel’s scalable network infrastructure can form the backbone for highly secure cloud computing environments. This approach enhances the security and reliability of cloud services by dynamically adapting to changing threat landscapes and ensuring the integrity of data transmission.
- Secure 5G and Beyond Networks: The rapid growth of 5G and beyond networks brings new security challenges. PacketHop’s innovative packet-forwarding methods, combined with Nortel’s experience in designing high-capacity networks, can ensure secure communication and data integrity in these next-generation networks.
- Secure IoT (Internet of Things) Environments: PacketHop’s decentralized approach to security, along with Nortel’s extensive network expertise, allows for secure and reliable communication among the numerous devices in the IoT. This will be vital in addressing security vulnerabilities in the growing IoT landscape.
Adapting to Evolving Security Threats
The ever-changing threat landscape demands adaptable security solutions. PacketHop and Nortel’s technologies can address this by offering a dynamic response to new and emerging threats.
- Dynamic Threat Modeling: The combination of PacketHop’s adaptive routing and Nortel’s network intelligence can create a dynamic threat model that adapts to evolving attack patterns and malicious activities. This proactive approach allows for a rapid response to newly discovered threats.
- AI-Powered Threat Detection: Integrating AI and machine learning algorithms with PacketHop’s real-time analysis and Nortel’s vast network data can enable proactive threat detection. This approach can identify subtle anomalies and predict potential attacks before they occur, significantly enhancing overall security.
- Zero-Trust Network Architectures: PacketHop’s distributed nature and Nortel’s network resilience support the implementation of zero-trust network architectures. This approach reduces attack surfaces and enhances security by verifying every user and device, regardless of location or network connection.
Potential Solutions to Address Current and Future Threats
PacketHop and Nortel technologies offer various solutions for addressing existing and emerging threats. These solutions focus on proactive measures and enhanced security capabilities.
- Advanced DDoS Mitigation: PacketHop’s dynamic routing and Nortel’s high-capacity network can effectively mitigate Distributed Denial-of-Service (DDoS) attacks. This is achieved by dynamically adjusting network traffic flow to absorb the attack and maintain service availability.
- Protecting Against Advanced Persistent Threats (APTs): The combined strengths of PacketHop’s intelligent packet analysis and Nortel’s secure network infrastructure provide a layered defense against APTs. These technologies can detect subtle anomalies and prevent the infiltration of malicious actors.
- Secure Data Transmission in Critical Infrastructures: Applying PacketHop’s security protocols and Nortel’s resilient network infrastructure to critical infrastructure networks can guarantee secure data transmission and prevent disruptions to essential services. This enhances the overall resilience of vital systems.
Supporting Advanced Security Operations
These technologies have the potential to revolutionize how advanced security operations are conducted.
- Predictive Security Analytics: Combining PacketHop’s packet-level insights and Nortel’s network-wide data can enable predictive security analytics. This approach anticipates potential threats and vulnerabilities before they materialize, allowing for proactive measures to mitigate risks.
- Enhanced Network Forensics: PacketHop’s real-time packet analysis, coupled with Nortel’s network monitoring capabilities, can facilitate enhanced network forensics. This allows for rapid identification and analysis of security incidents to quickly isolate and contain threats.
Illustrative Future Security Scenarios
These technologies can be crucial in various future security scenarios.
- Cyberattacks Targeting Critical Infrastructure: PacketHop and Nortel technologies can form the foundation of a highly resilient network that can withstand and rapidly recover from attacks targeting critical infrastructure.
- Large-Scale Distributed Attacks: The dynamic routing capabilities of PacketHop and Nortel’s infrastructure can distribute and absorb the impact of massive-scale attacks on a network.
- Advanced Persistent Threat (APT) Campaigns: PacketHop’s intelligent packet analysis and Nortel’s secure network architecture can significantly hinder the success of APT campaigns by detecting subtle anomalies and preventing unauthorized access.
Final Summary
In conclusion, PacketHop and Nortel’s legacy in homeland security is significant, offering a unique perspective on past and potential future applications. While their technologies might not be the primary tools used today, their underlying principles and functionalities continue to inspire and inform current practices. This analysis highlights the importance of understanding the evolution of technology in security and the enduring value of historical innovations.